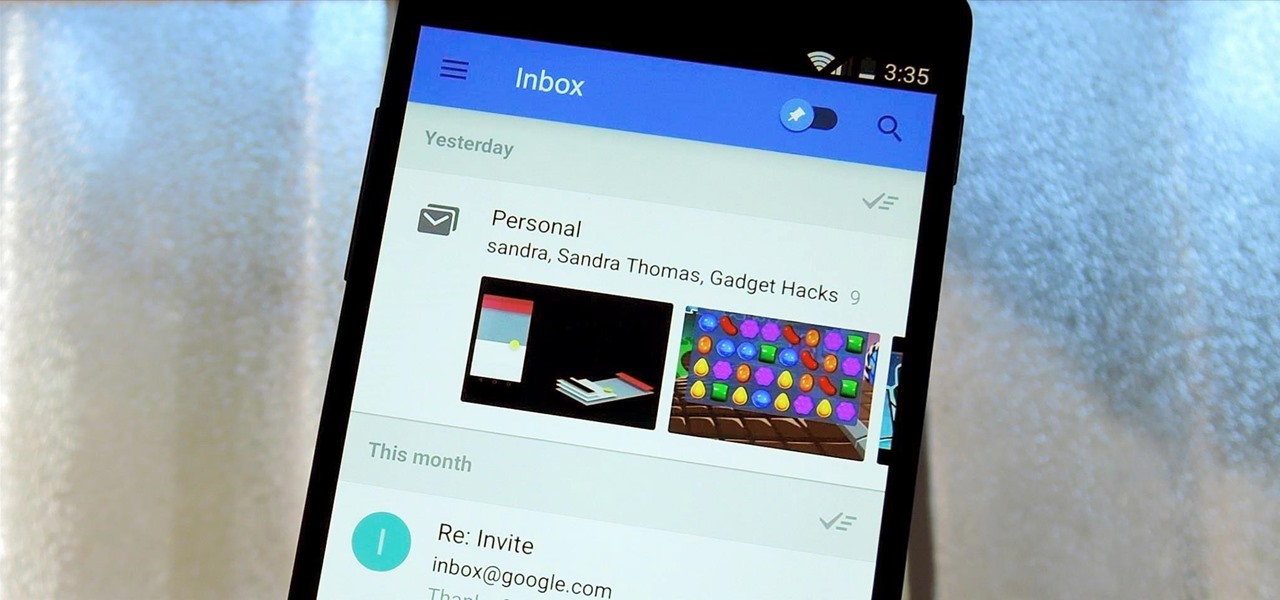
Google's new Inbox by Gmail service wants to fundamentally change the way you handle email, so a bit of a learning curve is to be expected when you're first using the utility. As of right now, the service is invite-only, but if you were lucky enough to get in on the ground floor, you're probably wondering, "How the heck do I use this thing?"

I hate to break it to you, but you're probably here because you were trolled. Thanks to a Photoshopped image making rounds across Twitter, Apple fans were tricked into believing that iOS 8 allowed them to lock individual apps, accessible only through a passcode or fingerprint ID. While that's not technically true, we've got the solution for you.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?
Bees are the key to pollination and healthy vegetation, and wasps may help by assisting in pest control, but despite their benefits in the world, they're still a real pain in the ass if they're in your face.

Recently, Sprint announced a partnership with Harman Kardon to deliver exclusive sound FX technology to their variant of the HTC One M8. The joint effort between the two companies is both to entice customers to switch to Sprint as well as improve the overall audio quality coming from the already extraordinary BoomSound speakers. But while this is great for new and existing Sprint customers, it does leave the rest of us out in the cold.

When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Dropbox lets you store anywhere from 2 GB to 18 GB of data for free, but if you want more cloud storage you're going to have to pay. Even if you do, Dropbox only gives you 500 GB for a pro membership. So how do you get more cloud storage without paying a dime? Start using Flickr.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

Forum member Luciano posted a terrific guide on adding hacks to our phone by editing build.prop. The article was great, but one of best things I saw in it was the "What You'll Need" section:

With the recent announcement of our server shutting down, it's time to get in and save the things you've made. However, this will work on any CraftBukkit server as well, and gives no extra strain to the server as the work is all done on your local computer.

The startup JigSpace, which was among the first apps to support ARKit and LiDAR for iPhone augmented reality apps, has capitalized on its early mover status by innovating within the space.

Imagine tilting the top of your phone away from you — it becomes a bit of a trapezoid, right? The top will appear smaller since it's further away, and the bottom will appear larger since it's closer to you — in other words, the perspective is all off. The same can be said of the pictures you take with an awkwardly-positioned phone.

Although the Galaxy Note 9 is an amazing phone, many members of the Android community won't even look at it. This isn't just because of the Samsung Experience skin, but the large amount of bloatware that comes with this device. However, with a little work, you can remove all of it.

All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Now that the Magic Leap One is officially out in the wild, users are already beginning to find out exactly how it works and what it might be useful for in the augmented reality space. But there are still other, more unique questions that remain unanswered.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

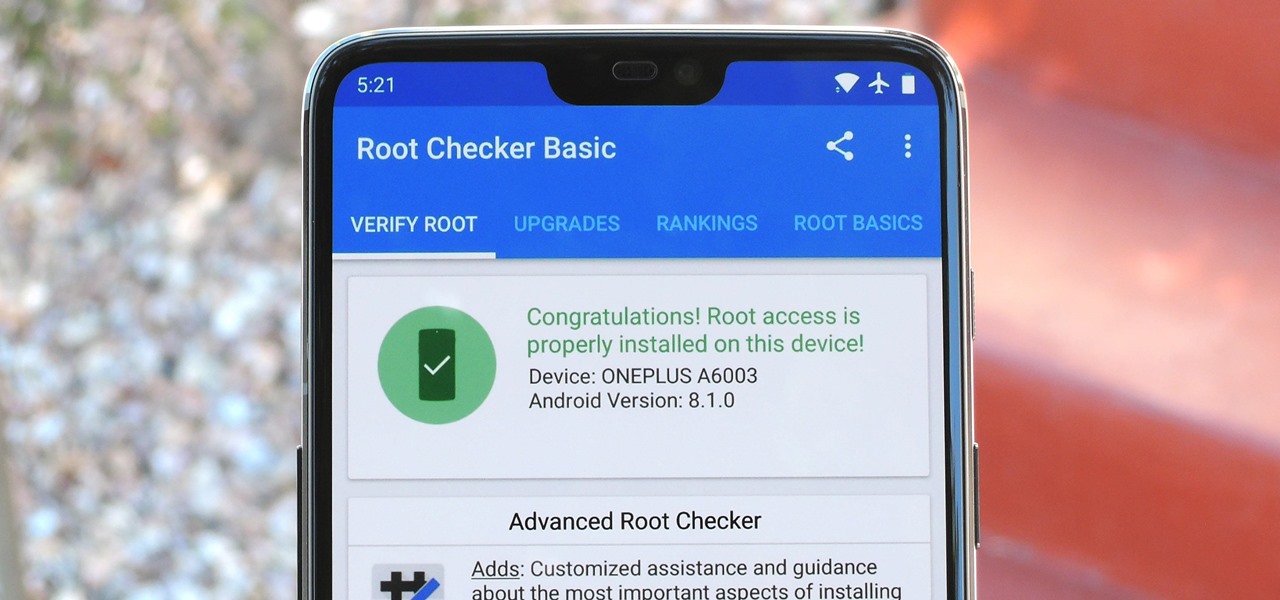
Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

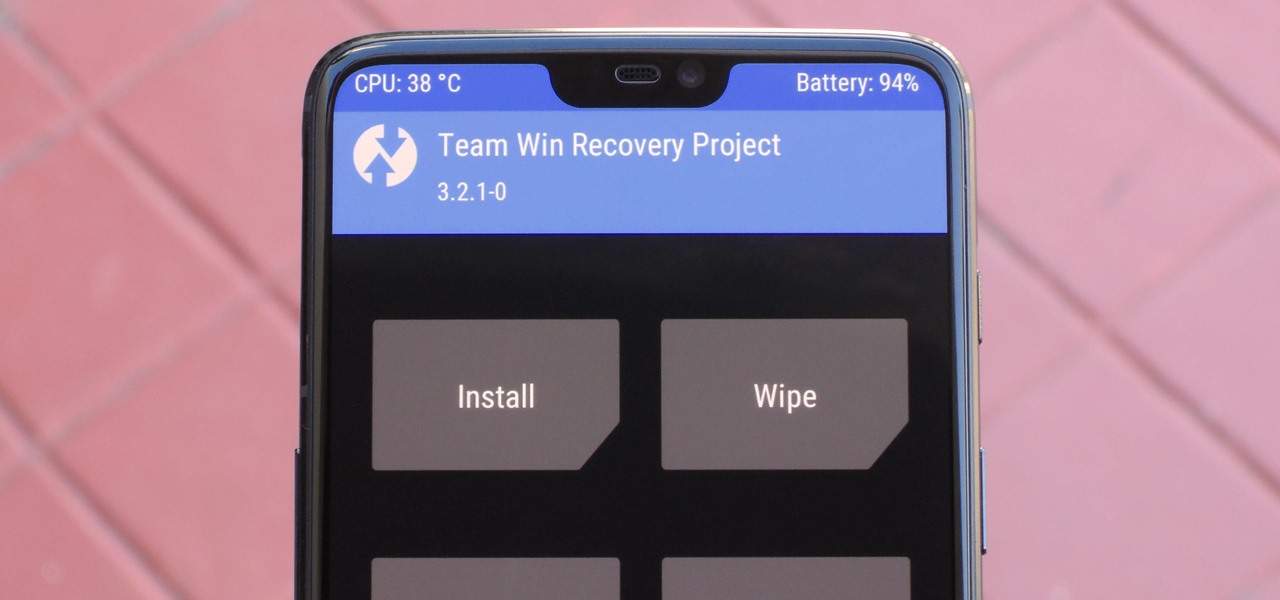
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

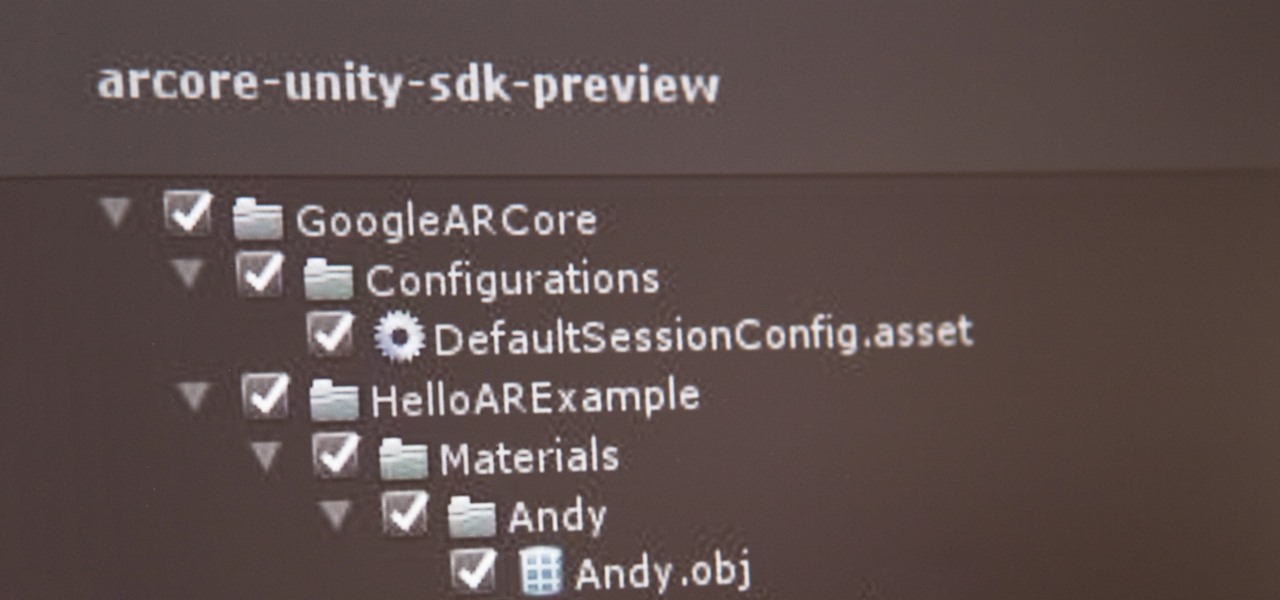
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

When it comes to streaming services, Google Play Music is one of the best options for both Android and iOS. Perhaps its single greatest feature is the fact that you can upload as many as 50,000 of your own songs to Google's servers, then stream your library to any device without ever paying a dime.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

The OnePlus 5 had been in the hands of the public for a meager twenty hours before developers on XDA released a custom recovery image for it, and the 5T had a similar trajectory. The installation process is simple enough, but it can be somewhat confusing if you're new to modding Android.

The next time you suffer a cut or abrasion, think twice before you reach for the Neosporin. It's time, and mom, tested — you get a cut, you wash it carefully, then apply some triple-threat antimicrobial ointment. You may or may not slap on a band-aid. We won't cover it here, but so that you know, covering the wound with a sterile dressing or band-aid is a good idea.

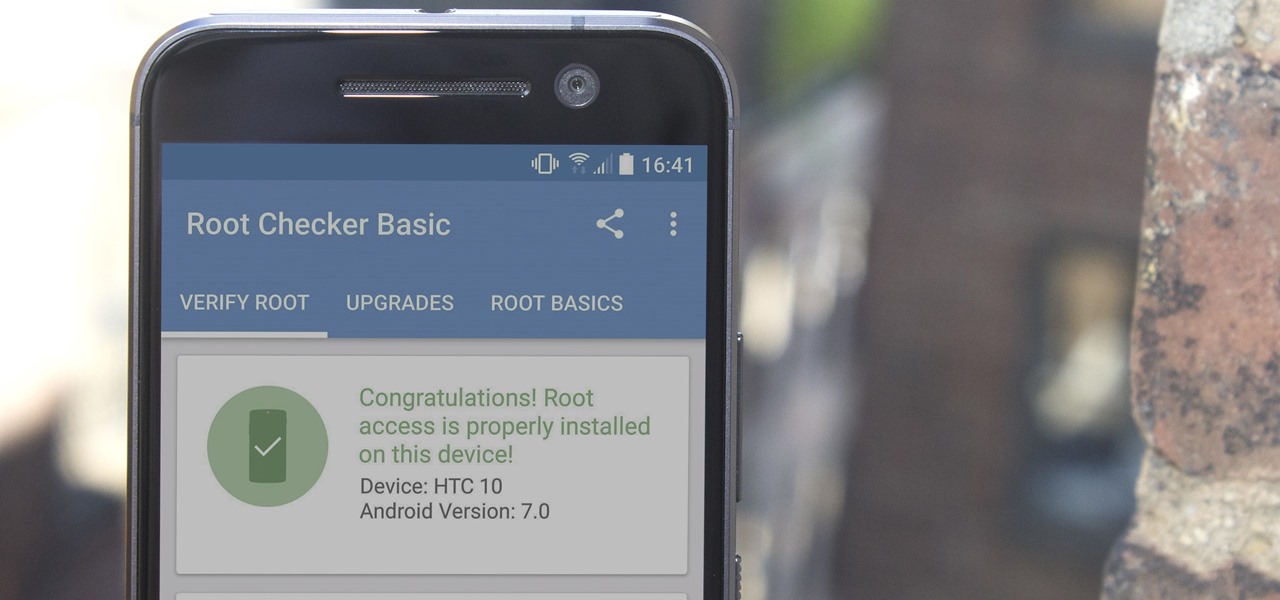
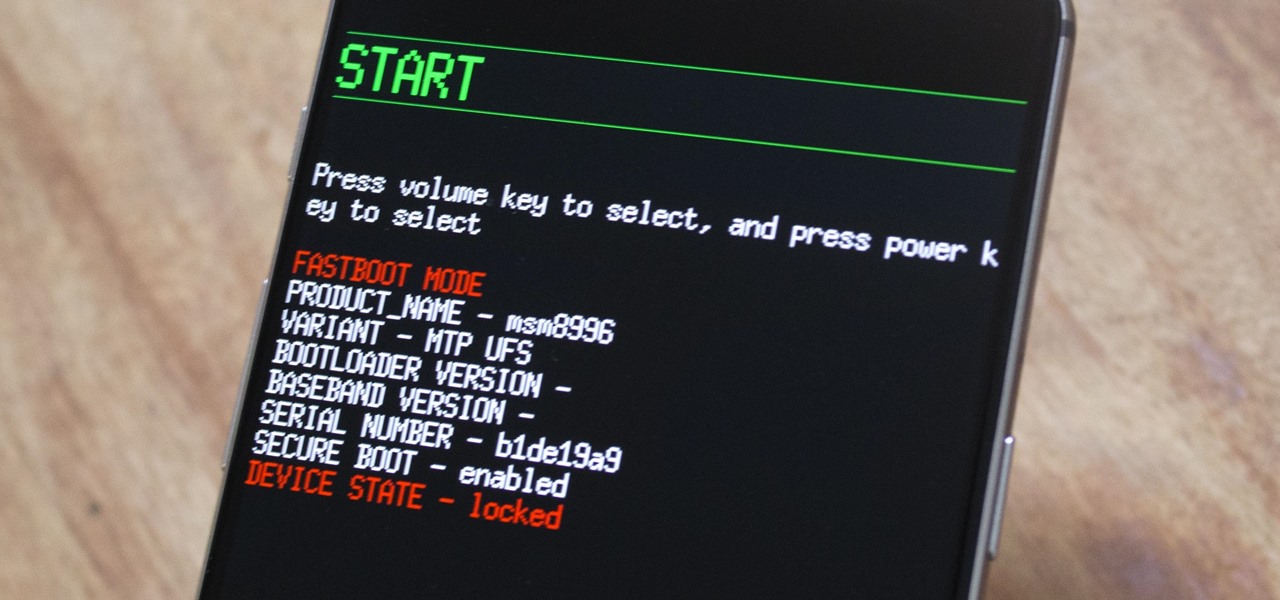
There are many great reasons to root your phone, but if you're not experienced with tools like ADB and Fastboot, it can seem like a daunting task. Fret not, because if you want to root your HTC 10, we're here to walk you through the process.

There is an Indian story called the Legend of Paal Paysam, and while it doesn't seem like it at first, it has a lot to say about what motivated Paul Travers in the augmented reality space.

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

The OnePlus 3 and 3T are two of the most modder-friendly devices to be released in 2016. Not only that, but they're both extremely solid phones which happen to sport a very reasonable price tag. Among the things that make these devices such a joy for tinkerers is the fact that they have an unlockable bootloader, receive timely kernel source releases, and are actually quite easy to root.

Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

As we reported first here on Gadget Hacks, the Google Pixel and Pixel XL have unlockable bootloaders, with the exception of models purchased from Verizon. This means that once the TWRP custom recovery is installed, you can flash ZIPs and even root your device in a few taps—as long as you unlock the bootloader beforehand.

Google has already issued a few updates to Android 7.0 Nougat. There aren't many headlining features, as these minor updates are mostly bug fixes and performance improvements. But there's a few security enhancements as well, so staying up-to-date with the latest patches is important for a number of reasons.

No matter how far technology advances, battery life continues to be an issue. Powerful new hardware is introduced each year, but smartphone batteries only get a few extra milliamp-hours to compensate.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.