In this Home & Garden video tutorial you will learn how to wash exterior windows. Get your window bucket with Dawn dish soap and water. Use your house brooms to remove cobwebs and dust from the windows. You will also need the utility belt with window applicator and squeegee. Couple of cloth pieces, plastic scrapper, steel wool and razor blades will also be needed for removing paint and other hard, sticky stuff. Dust off with the broom. Apply the solution with the applicator. Wipe off near the...
Wartex8 demonstrates how to use remote desktop in Windows XP. Remote Desktop is a useful utility that you can use to control another computer and its applications.The necessary steps that are adopted to activate remote desktop are:1) Right click on my computer icon (either the icon on the desktop or the one on the start menu list) and select properties, and a new dialog box called system properties will pop up on the window.2) In the System Properties, select the computer name tab and write d...

Need some extra space on your computer? Grab those folders and zip 'em! Watch this tutorial and learn how to consolidate your folders into a single zip file, saving you space and keeping you organized.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

When a new jailbreak method comes out, Apple is quick to patch the vulnerability it exploits by issuing a new iOS update. If you were to accept such an update, you'd no longer be able to jailbreak your iPad, iPhone, or iPod touch unless you could roll back your firmware to a version that could be jailbroken. But Apple even takes things a step further and stops signing older iOS firmware versions, which makes downgrading next to impossible. This is where your SHSH2 blobs come into play.

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

For those of you who've already gotten Beta Preview or Developer Preview access to Mac OS X 10.10 Yosemite, I highly recommend installing it on a separate partition on your hard drive.

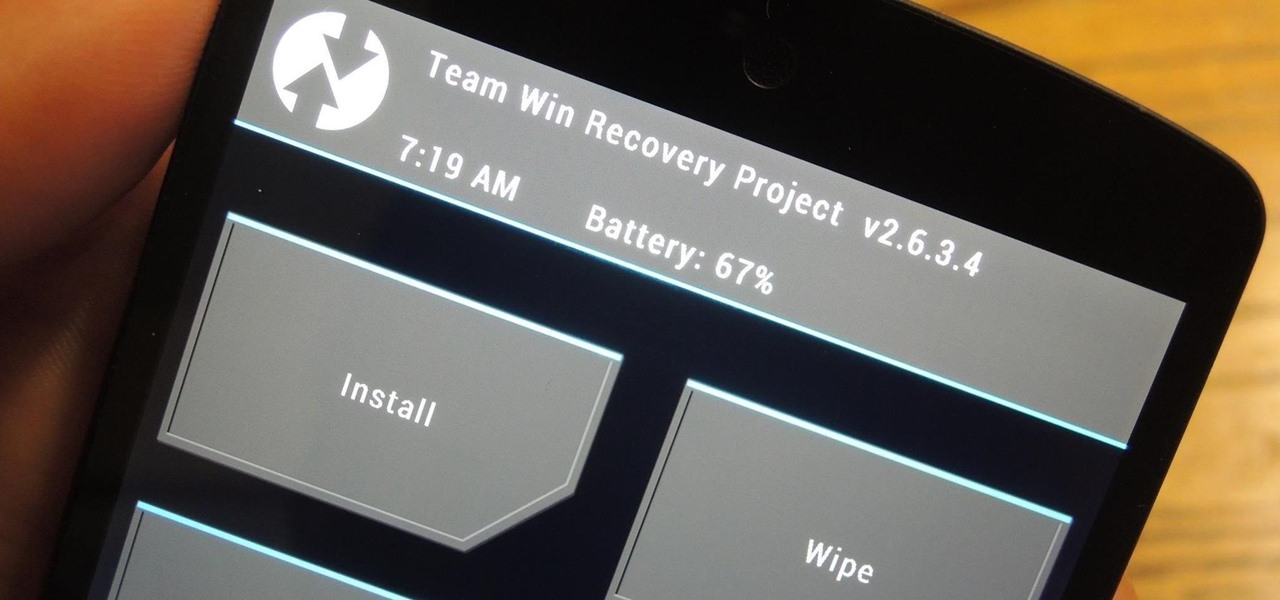
A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

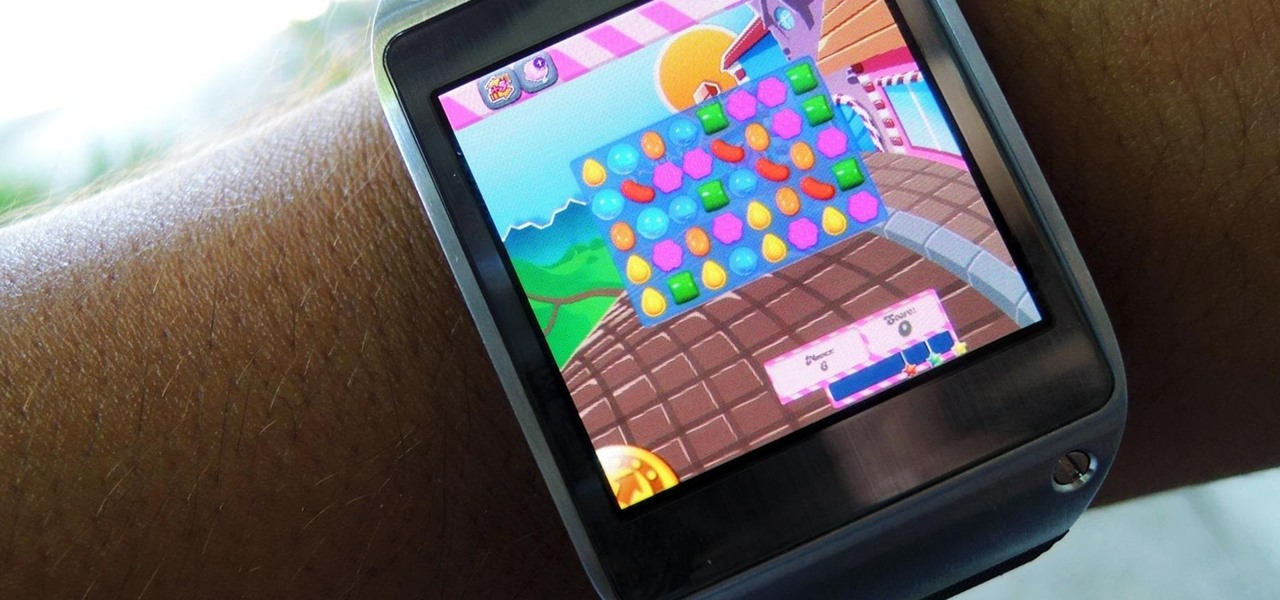
With the Samsung Galaxy Gear smartwatch only several weeks old, the extent as to what you can do with it is limited since there are only about 70 apps in the Gear Store right now, and a lot of those need the full app installed on your Samsung Galaxy Note 3 in order to function properly.

How to patch a hole in drywall / plasterboard / Sheetrock. Everyone at some stage in their life will need to patch a hole in drywall / plasterboard / sheetrock. Instead of doing some dodgy patchwork, watch this video to see how simple the job is. The steps are as follow in point form. This method is particularly suitable for holes that are larger than about 100mm or 4 inch's in size.

Automator is a built-in Mac utility found in Mac 10.4+ and can be used to convert a PDF file to text format.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

On Tuesday, the smartglasses startup known as North finally took the wraps off its Focals product, but in a very unique way: The team simply opened a couple of stores and invited the public in.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

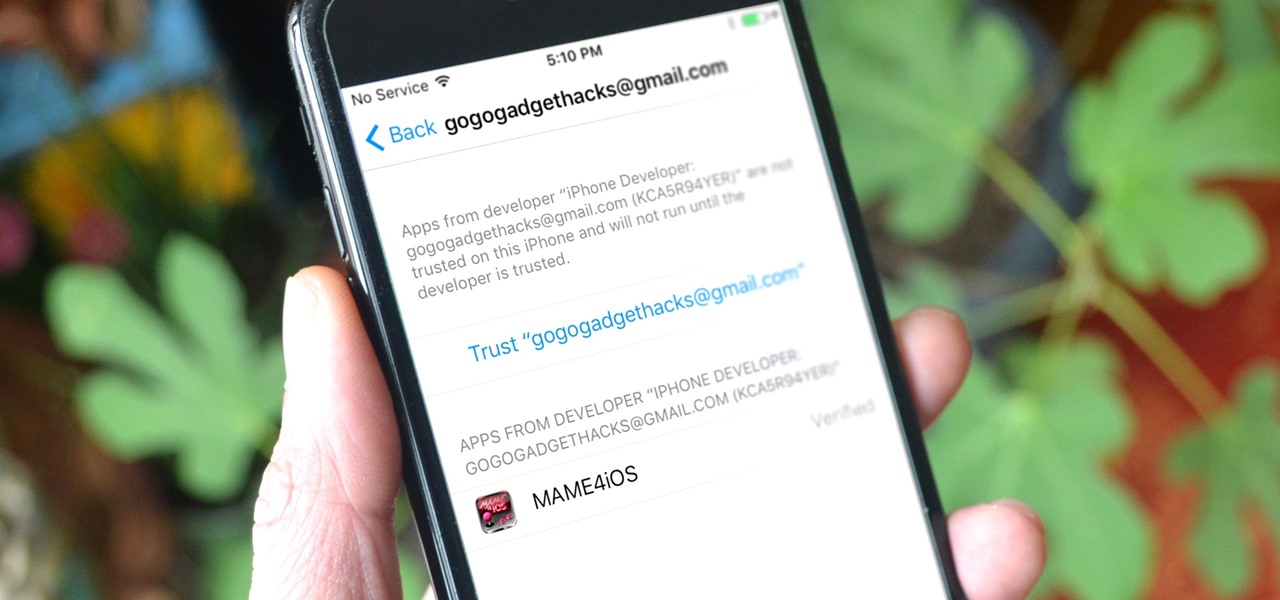
Jailbreaking gives iPhone users almost unfettered access to their devices, offering a slew of customizations, new features, and improved apps that you just can't get elsewise. Unfortunately, Apple has clamped down hard on the latest iterations of iOS, making jailbreaking extremely unstable at best. Hope is not lost, however, as there's still a way to install modded and unofficial apps on your iPhone, iPad, or iPod touch without any jailbreak.

I was on our new #nullbyte IRC channel when someone told me how tedious it is to install an OSX Virtual Machine on Virtual Box (I think it was wawa). We all know Linux rocks (gets acknowledgement from the crowd), but there are morons out there, multiplying at a never before seen rate, who use OSX. We at nullbyte should be prepared for anything and everything. So, in this guide I take you step by step to creating your OSX Yogemite VM.

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.

New York-based virtual content startup Sketchfab is usually at the forefront of the latest developments in augmented reality, so it's no surprise that the company has locked in yet another major platform.

With the latest software updates for its Focals smartglasses, North has essentially deputized its customers as marketing evangelists to friends and family.

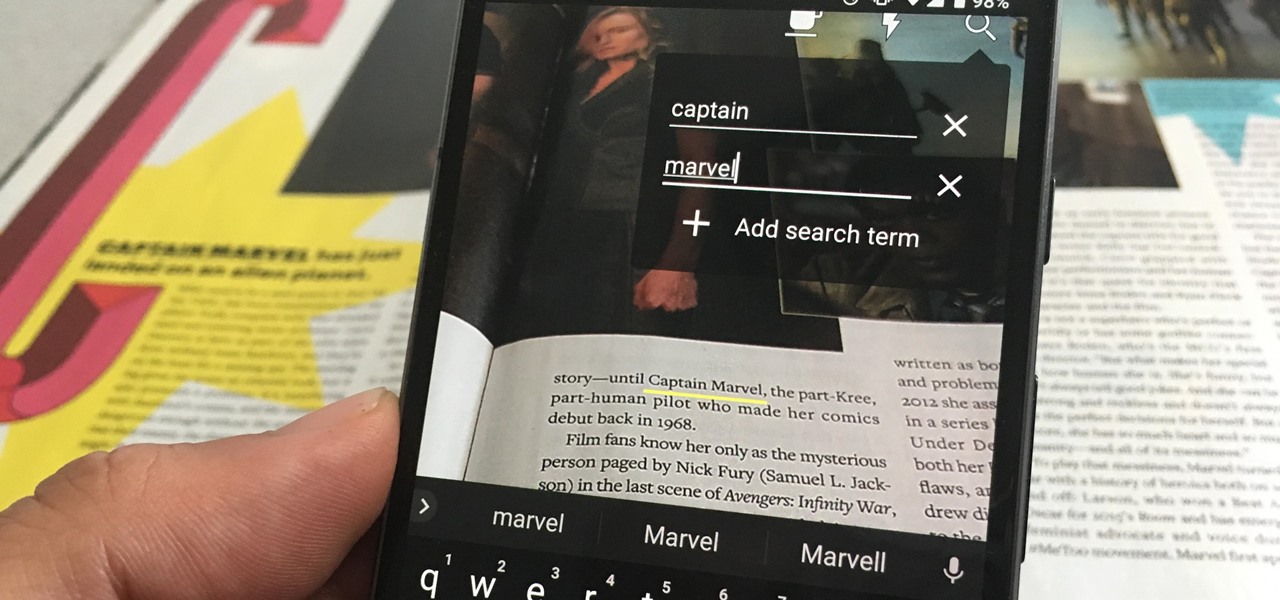
One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

On Friday, at IFA 2018 in Berlin, Samsung invited attendees into the residence of Family Guy's Griffin family to learn all about its "smart home" products via augmented reality.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Do you see a red door and wonder if it might be a good idea to paint it black? You could "ask Ask Sherwin-Williams," or, better yet, you could just ask the new augmented reality features in the retailer's mobile app.

As a long-distance runner off and on for the past, I absolutely detests hills. While there are many apps that can measure elevation and slope for certain routes, understanding spatial data on a line graph or even an elevation map can be difficult.

The rumors have been confirmed by Samsung themselves: Samsung has developed a virtual assistant of their own, named Bixby.

For some strange reason, Google Now is unavailable in several countries across the globe. Users from Albania, China, Cyprus, Malta, Nepal, Puerto Rico, Tunisia, and many more big countries have reported for years that the service doesn't work in their area, mostly likely because Location Reporting is not available in their region. This is really a shame, because Google Now has some great features.

When you want to leave someone a quick message, you often write it down on a sticky note and paste it to the relevant location. Alternatively, you call to leave a voicemail. Holo Voice Memo lets you do both at the same time by leaving an audio clip on a physical object in the room so anyone with a HoloLens and the app can play it back.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Although they're often times the primary source of income for websites, on-site advertisements can annoy even the most tolerable reader. That's why ad blockers have been some of the most popular downloads on Firefox and Chrome for some time now, demonstrating that when it comes down to it, most people just want nothing to do with ads shoved in their face.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

Ant-Man isn't one of the most famous Marvel superheroes. In fact, with the news of his individual movie came great doubt that the comic book legends could succeed in telling the tiny story of an oddball hero on the big screen. Yet with its humor and unique story, Ant-Man has become a hit movie in its own right—and the hero will most certainly make a hit Halloween costume.

Most of us only see our screen savers in passing, as some sort of slide show or animation as we glance up at the screen or walk by the computer. Usually, anything is better than a boring blank screen—even the classic Pipes screensaver is better than nothing.

Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).