There is nothing better than topping off a cardio workout with a little strength training. In this fitness how-to video SELF Magazine shows you how to utilize weights and strength training to really tone body. Watch and learn how easy it is to do the following moves with a few light weights: high pull, figure eight, swing back, Turkish get up, skater's leap, push presses, teapot tip, high five squat, bent over row, starfish reach, side press and a Russian twist. You will love the results from...

When you wan to get your body into shape you don't need any fancy equipment. In this fitness how to video SELF Magazine demonstrates how to utilize an elastic band for toning specific muscle groups. Watch and learn how easy it is to use the resistance band to do the following exercises: Bent-over cobra, power plunge, triceps crossover, recline row, curl whirl, side bend, hot 100, torso twist and deltoid raises. This simple elastic band moves are sure to tone and sculpt your arms, abs and lowe...
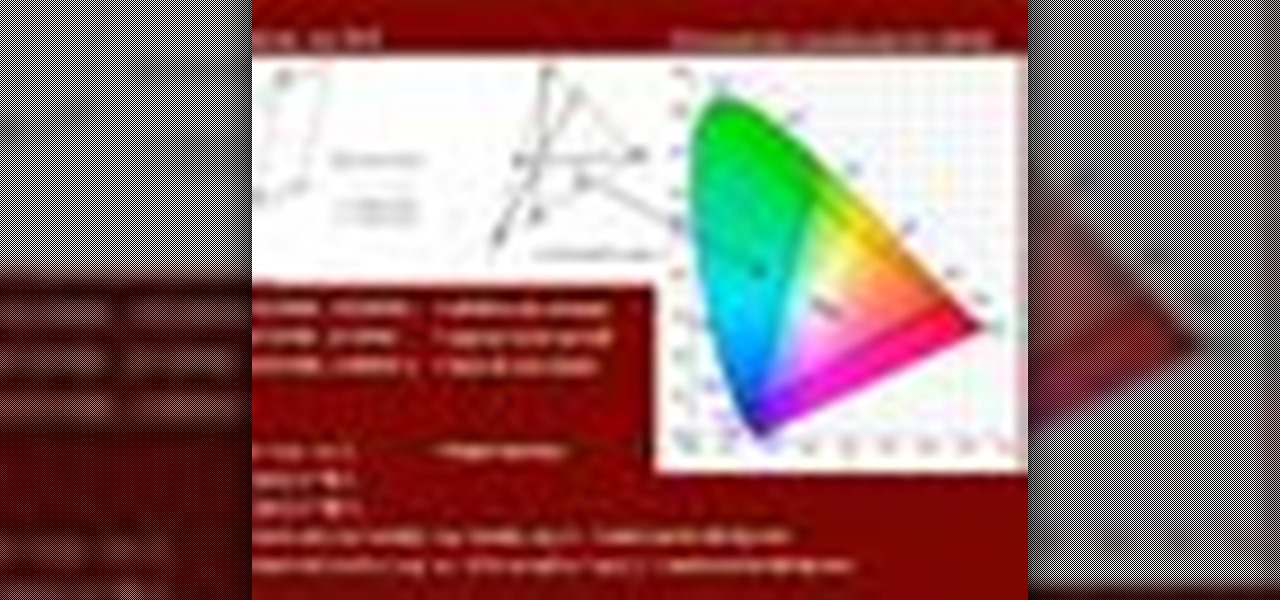
Watch shader writer, Mario Marengo, explain spectral wavelength and how to utilize it within Houdini. This presentation was recorded at a Toronto Technical Evening hosted by Side Effects Software.
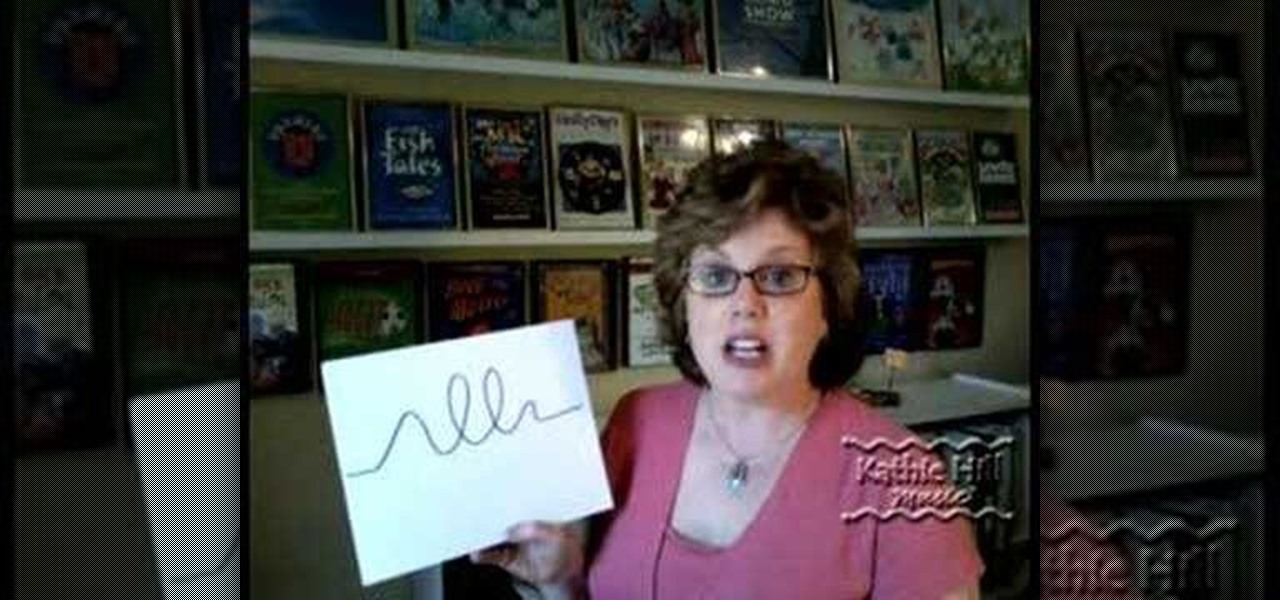
In this how to video, Kathie talks about using the diaphragm and shows some tools she's used to help kids with vocal exploration. These are great tips to utilize if you are teaching a music class or a children's choir. You'll be able to teach kids to sing in no time at all with this tutorial.

A speedrun tutorial for the classic game Metroid. Note: The door glitch is not being utilized, nor is the restart tactic with the second controller. This is also a no-death tutorial. These factors make this path acceptable for most speed-run sites.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

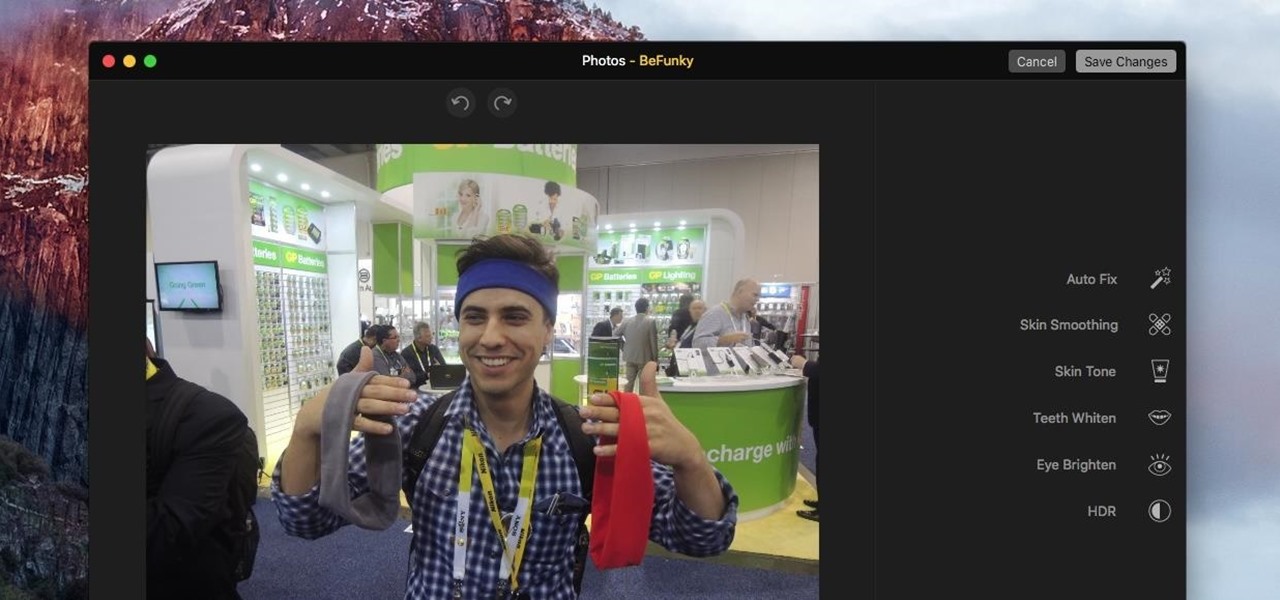
For minor adjustments and color-correction, the Photos app is extremely useful, but its capabilities are limited to just the basics. Now, with Mac OS X El Capitan, Apple is opening the door for third-party extensions, meaning we can utilize additional, unique tools when editing pictures in Photos.

The hardware running your One is nothing short of powerful, but the people at OnePlus can't control how developers choose to utilize that power—or rather, not utilize it. Most popular developers have removed all signs of lag from their apps, but others still have archaic lines of code that can make your shiny, new device feel like a first-generation smartphone.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

In order to draw a meerkat, you will need the following: a pen, an eraser, and a pencil.

Kung fu is an ancient Chinese martial art that requires balance, stability and strength. Learn several kung fu blocking techniques from a kung fu instructor in this free martial arts video series.

This video features an image from Squizzlefly. The card is Spring suite 2. Use a regular A2 size card. Cut 8 1/2 x 5 1/2. Score in the middle. Go down another 1/2 inch and score. Take a ruler across the top of the fold. Make a pencil mark at every 1/4 inch. Should be 21 small hash marks. Measure down 1/4 inch on both sides. Go 1/2 inch in and make a dot every 1/2 inch. Go down 1/2 inch from the fold and make a dot every 1/2 inch. Make long-short, long-short cuts with the dots along the whole ...

Prepare this wonderful easy vegan meal for six. It only requires a 10 minute prep time and it cooks in 35-40 minutes.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

Actions allow you to control your movie timeline and buttons in various ways. This tutorial starts with a basic image and shows you how to utilize the different actions available to you when creating an animation in Adobe Flash CS3.

Isometric exercises are strength training exercises that don't let the joint angle and muscle length contract during the movement. This means that the exercise is done in a static position with the muscular intensity coming from the weights and your own body.

Need some assistance figuring out how to utilize the Selection tool in Adobe Illustrator CS4 or CS5? This clip will teach you what you need to know. Whether you're new to Adobe's popular vector graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

In this tutorial, we learn how to improve your FICO credit score. Everyone will want to use your credit score to decide what kind of person you are. The FICO is the most commonly used credit score used today. To improve your credit score you will want to make all payments on time. Catch up on past due accounts and utilize 50% and less of your credit limit. Your balance should be under half of what your limit is. Don't close your account, because this can drop your credit score as well. Revolv...

In this video tutorial, viewers learn how to draw a cartoon bird. Using the gray pencil tool, draw an oval shape for the body of the bird. Then create the lines for the wing and tail. Now add the details with black outlines. Then use transparent colors to fill the body, tail and wing with different shades of color. Add details to the wing by drawing some lines. The beak should be short and sharp, and the eyes should be highlighted in white. Color the branch with the brown paint tool and the l...

In this video tutorial, viewers learn how to draw a formal dress. Begin by sketching the body of the figure. A formal dress is usually loose, so make the figure's body look thin and slender. The add some glamorous looking hair on the figure to make her look formal. Then add details to the dress by drawing the straps of the dress and cleavage on the chest. For the bottom of the dress, draw vertically curved lines to represent the fold of the dress. Make the dress look long and loose at the bot...

This video shows various exercises to define your abs. These exercises involve breathing techniques. They utilize the breath to reduce your waist and develop perfect abs. The video starts with easy exercises like sucking your belly in. This exercise has to be done for five seconds in the beginning, and later increasing it to a full minute when you are comfortable with it. The video then goes through variations of this exercise. The video is very simple to understand.

Frozen shoulder is a common problem that men and women get between ages of 40 to 60. It is also known as adhesive capsulitis. A frozen shoulder is when the shoulder joint is clamped down. Learn how to diagnose and treat a frozen shoulder in this medical how-to video.

Scosche Industries offers this instructional users guide for its TA07 radio replacement interface in a 2007 Toyota Tundra. The TA07 will work with select 2004 and up Toyota vehicles equipped with JBL and JBL Synthesis systems. The TA07SR radio replacement interface was designed to make installation of any brand name aftermarket head-unit simple. The TA07SR allows the customer to replace the factory head unit with an aftermarket head unit and utilize their factory amplifier without having to "...

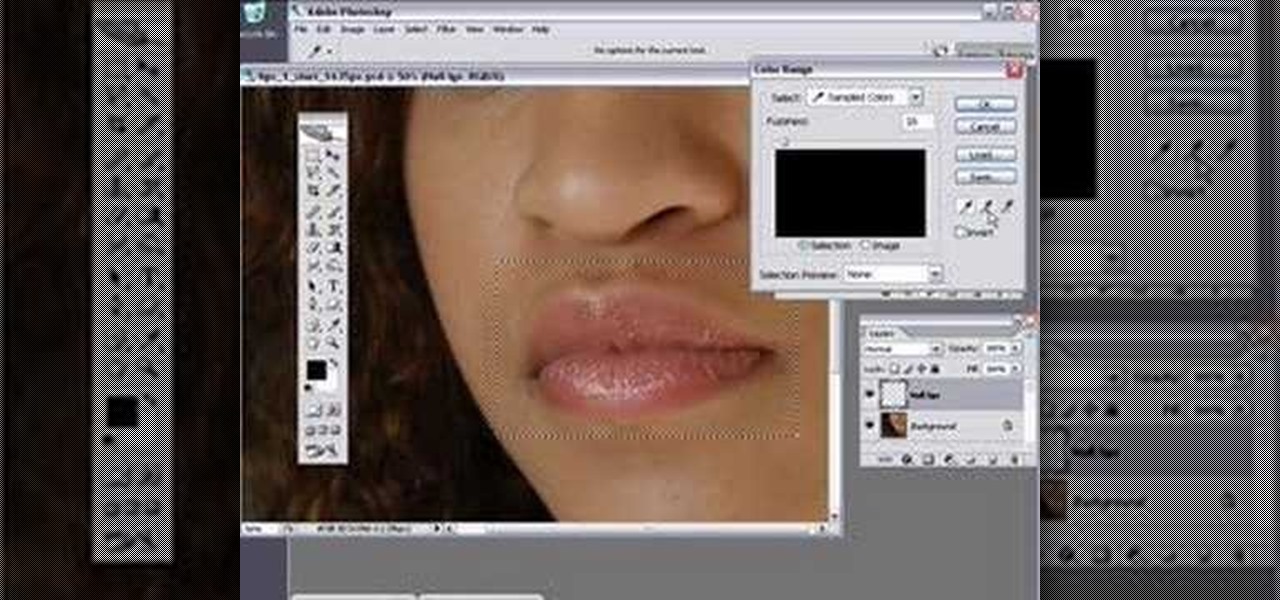
A demonstration of how to utilize a Photoshop Action Mama created to optimize the natural highlights in the lips to produce a very glossy lip effect. NOTE: You will need to buy the Action from Photoshop Mama to follow this tutorial.

If you've ever wanted to live in the Matrix—or at least the iconic digital rain data visualization that Neo saw when realizing he was, indeed, the "one"—you can now do that with the Microsoft HoloLens. Just download The Red Pill.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

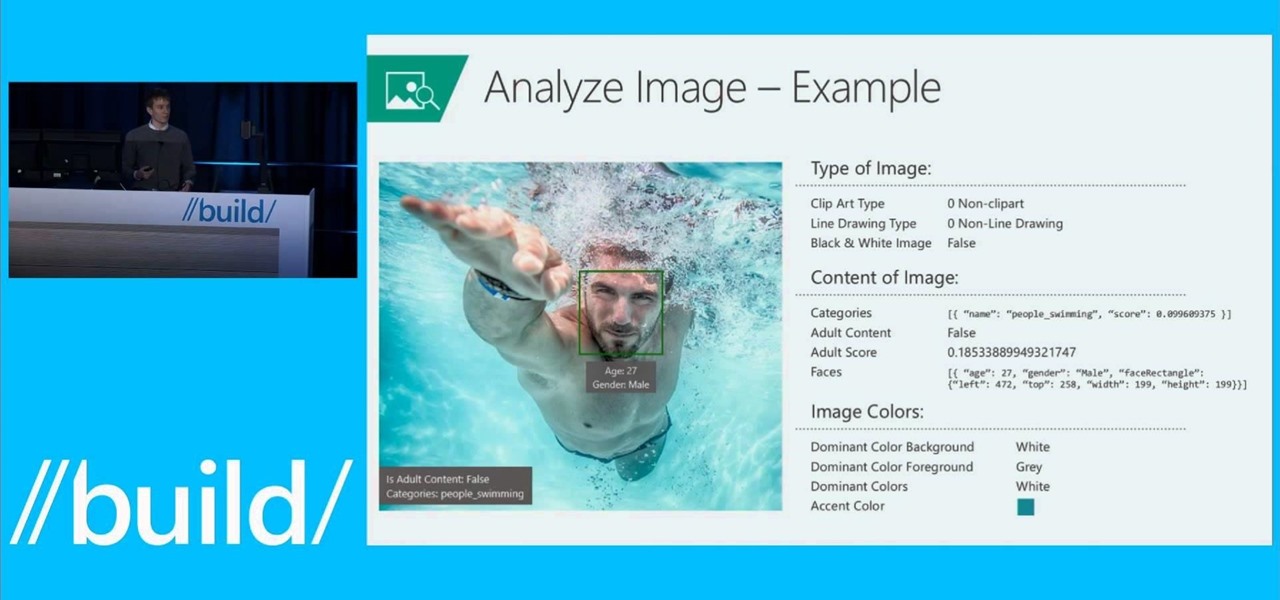
Microsoft is developing a new API project called poject "Oxford," and it includes face, speech, and more "smart" API technology. Despite being Microsoft, I actually found this to be very useful. ;)

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

While Android devices made by HTC, Samsung, and others have long utilized IR (infrared) blasters to offer remote control functionality, Apple has still yet to embrace it on iPhones.

This is for people who are already proficient at doing basic pull-ups and chin-ups and want to take their training to the next level. It's also pretty funny for anyone who enjoys a bit of gym humor.

This is a cool little trap that me and some friends came up with while messing around with TNT and redstone on a big platform in the sky. The reason we called it the 'Roof Lever Trap' is because it utilizes the ability to place levers on the bottom side of blocks, which was introduced in Minecraft 1.3.1.

A lot of people like to trash stand mixers for being overpriced and rarely used kitchen appliances. As an avid bread baker I certainly don't agree with that assessment, but I understand where people are coming from. A good Kitchen Aid stand mixer costs a few hundred dollars, and if you only occasionally bake, you probably don't use it much, and therefore aren't getting your money's worth. But what most people don't know is that stand mixers are one of the most versatile appliances in the kitc...

Next to map data overlays, one of the most often discussed concepts for apps that could propel augmented reality smartglasses into the mainstream is a real-time language translation app.

The company that brought us a BB-8 droid controlled with the Force — okay, just a high-tech wristband — is releasing its take on Spider-Man. Toymaker Sphero collaborated with Marvel to release an app-enabled Spider-Man toy equipped with numerous features, as well as games for your smartphone.

Most popular virtual reality headsets, like the HTC Vive and Oculus Rift, require a tethered connection to the computer and that imposes some obvious restrictions on how much we can move in our space. We'd all prefer a simpler, untethered option, and Intel wants to provide just that.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?