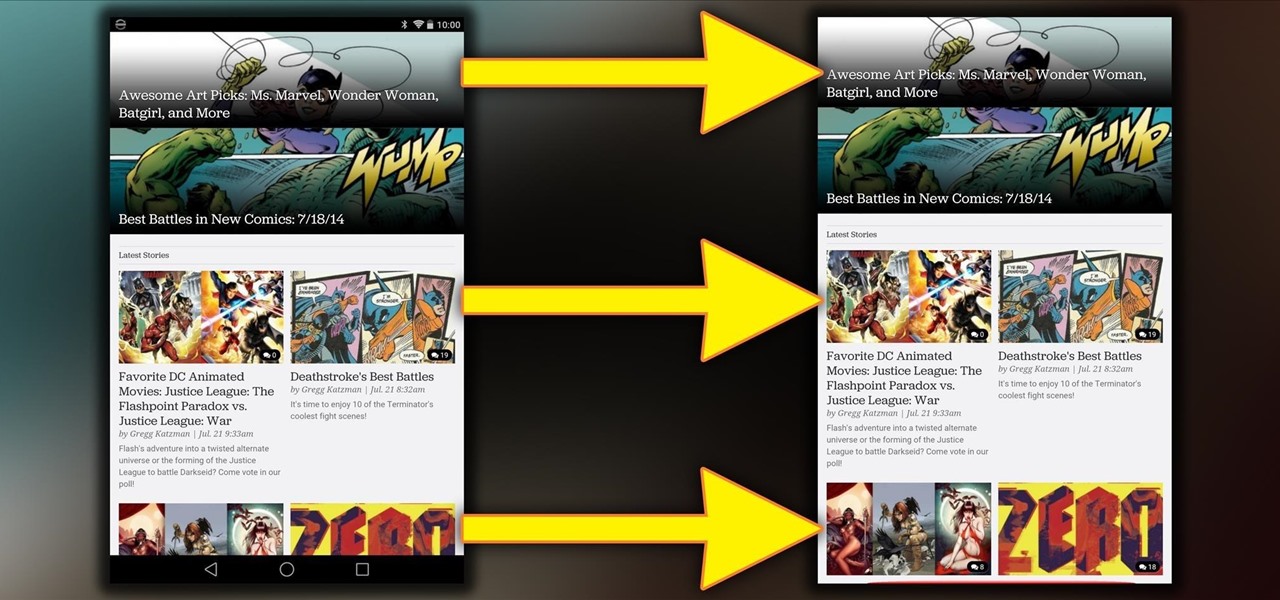
Rooting is a great way to unleash your device's full potential, but not everyone's comfortable with it. Rooting can void a warranty, cause issues with certain apps, and the process itself can be tricky for older devices. Alas, most of the great apps or mods out there require root access, like the ability to utilize a built-in KitKat feature known as Immersive Mode.
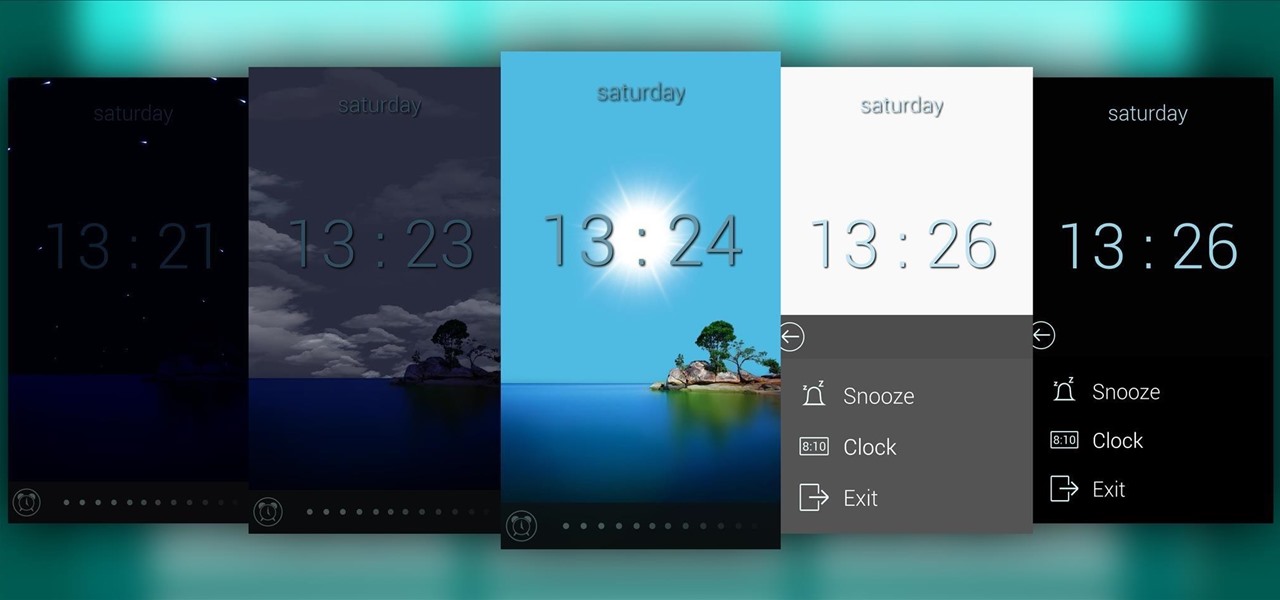
Most alarms just make noise to wake you up, and it can be a bit jarring coming off of a deep sleep to suddenly being woken up by a blaring sound. On the flip side, if you're a heavy sleeper, this might not even be enough stimuli to snap you out of your 8-hour coma.

It's not enough for me to just listen to a mindless EDM song that can be retooled as a torturing method for Guantanamo Bay. As an actual fan of music, I yearn for substance and depth. Artists like Morrissey, Kurt Cobain, and John Lennon impacted lives with not only their music, but the subject matter of their songs.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.
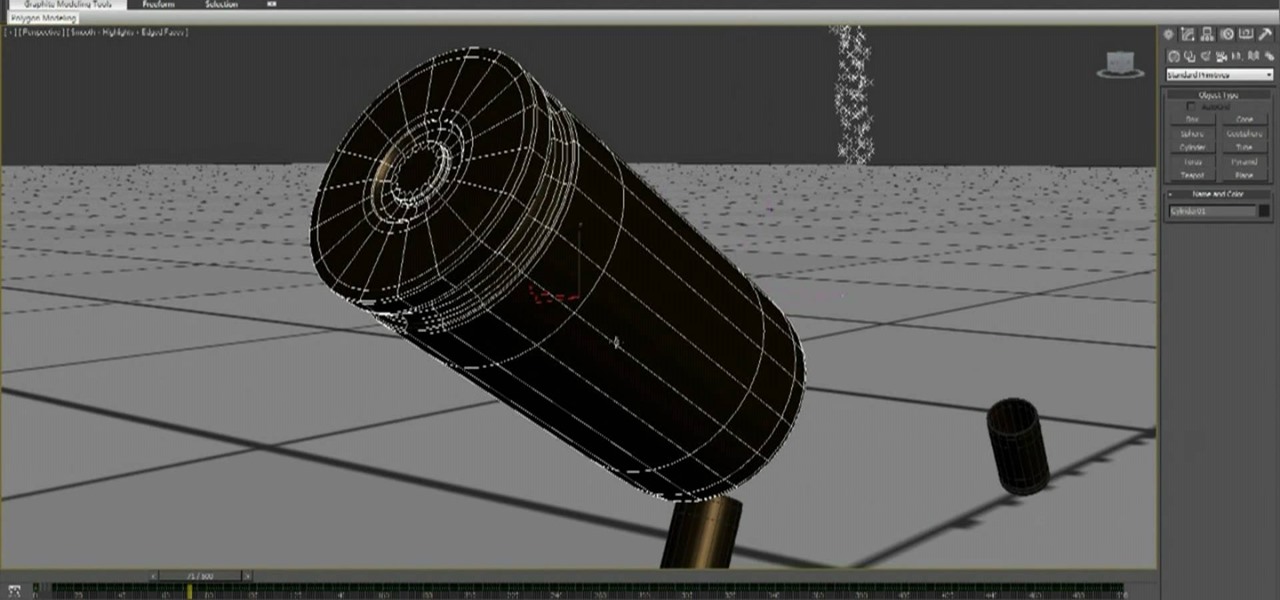
When people fire weapons in movies, there is often a shot of the shell-casings leaving the gun and flying through the air. Sometimes we get to follow them all the way to the ground, leaving us with a sense of loss at the firing of the weapon. This video will show you how to model and animate some shell casings falling to the ground and smoke trailing them in 3D Studio MAX and Photoshop, utilizing Reactor physics, particle flow, space warps, and all sorts of other fun 3DS MAX tools.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

Check out this video from Berkleemusic.com and watch as Berklee professor Paul Schmeling explains how to master the toughest jazz standard with ease and improve your left hand technique by utilizing shell voicings to represent chords in the left hand.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

I recently wrote about fast food fakeouts you can make at home, but people cannot live off fast food alone. Sometimes you need to step up your game a little and enjoy the fare at a popular chain restaurant with a bit more variety to its menu.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

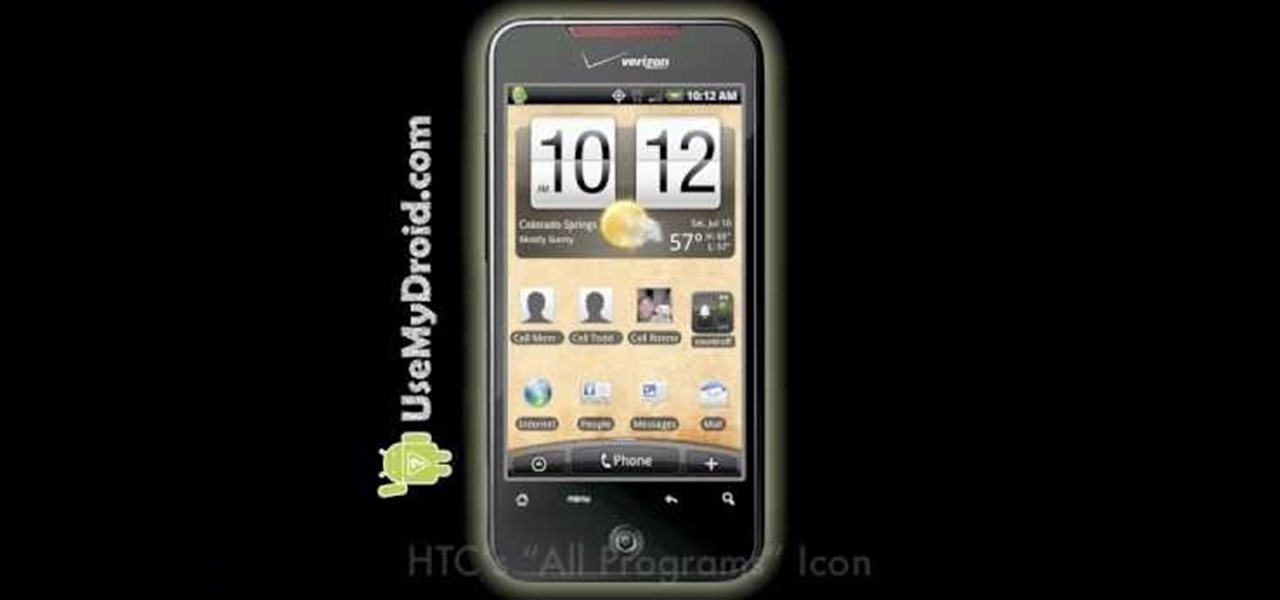
In this video tutorial, anyone who owns a Droid smartphone can learn how to better navigate their home screen. With this Droid phone tips, you'll be able to maximize your time and create shortcuts to your most used applications. The Droid's home screen in much like a computer's desktop; putting an icon on one of your Droid home screens allows you quick access to a program or app. There are numerous Android phones, but this video focuses on the "Droid" versions, but you may need to play around...

In this video tutorial series, DJ James Zabiela shows how to use effects to enhance your DJ set, utilize a feedback loop, and discover new music. In the second half of the series he shows how to alter live vocals, incorporate a few of his signature moves, and edit digital scratches into your DJ set.

Leigh Ramsdell and Hal Brindley with The Environmentals discuss how to build a worm composting bin. To build a worm composting bin, you will need a plastic tub or a box with a lid. Calculate one square foot of surface area per pound of worms. A pound of worms can process a half a pound of food per day. Worms need air so put holes in your bin on the top and sides. Also put holes on the bottom for drainage so your worms don't drown and die. Add screens to cover the holes. Put bricks on the bott...

Enthusiastic, young David Yzhaki teaches you how to play the piano with a damper (sustain) pedal. Get to know the pedals on an upright piano. The right pedal, which is the primary focus of the video, is the sustain pedal, which creates a sustaining note when pressed. The left pedal is called the "una corda," which modifies the tone quality by softening the note when pressed. The middle pedal is called the sostenuto pedal, which enables the piano player to hold a note longer than usual. To use...

Tango teachers perform a didactic demo to highlight and integrate some concepts in this video. It is about refining the rock step in tango.

Check out this overclocking tutorial from HotHardware.com! Intel's Core i7 processor offers a significant performance increase over previous generation Core 2 processors. In addition, like the legacy Core 2 architecture, the new Core i7 also has a bunch more headroom for wringing upside performance out of the chip, maximizing value, power and return on your investment with overclocking. In fact, Intel actually built-in a predefined overclocking feature called "Turbo Mode". We explain how not ...

Josh Copp and Madeline Donahue show us how to build a light table from pine wood and plywood utilizing two fluorescent light fixtures as the light source inside the box. The frame of the box is fashioned out of two 1X8 planks cut into four pieces so that two sides are 30 inches and two sides are 22 3/8 inches. The base of the box is made of plywood or OSB and is 30X22 3/8. Once the pieces are cut and assembled using a pocket hole jig and wood screws, the inside of the box is painted with whit...

This tutorial covers some of the basics of dramatic filmmaking. A drama is a film that is character-driven, using the characters' emotional responses to situations to move the story along. Epic and historical dramas put their characters in historical events. Crime dramas are set within the rules and boundaries of reality, but do not have to be linked with any historical event. These films utilize suspense and action to push the characters through the story. Biopics are motion picture biograph...

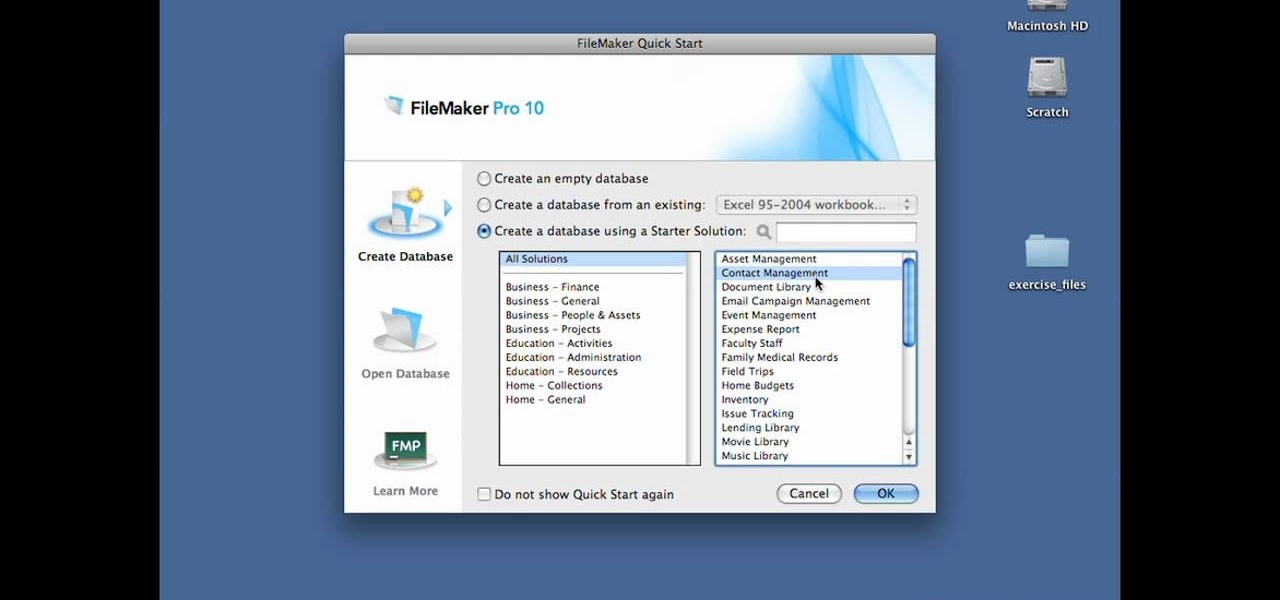
In this Lynda video tutorial, learn how to use FileMaker Pro 10 software to create databases with pre-made templates. FileMaker offers these templates in a package called Starter Solutions. To access these options, click open FileMaker. Then, go to New Database under the File menu. Click the option "Create a database using a Starter Solution." The templates are grouped according to the nature of their use. Some are for the home, while some are for business. All you do is open the template you...

A cow is enormous... Hence why this video on how to butcher a beef carcass (from start to finish) had to be broken up into 13 parts. This butchering process is designed to not waste an ounce of meat and utilize every part of the carcass. Warning! These videos are not for queezy stomachs!

Learn about circuit bending in this video series that will help you understand how and when to utilize this unique way of making music.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

The new Samsung Galaxy S8 and Galaxy S8+ phones were announced on March 29 at the Samsung UNPACKED 2017 event. Preorders start on March 30 for the Korean tech giant's latest flagships, and sales officially begin in the US on April 21. Samsung will need a smooth release to win back consumer trust after the Note7 mess, and it's already looking like the S8 won't disappoint.

Home cooks are often quite intimidated when trying to reproduce the delicious ethnic dishes they enjoy at various restaurants. Thankfully, there are definite flavor profiles and spice/seasoning/herb combos that are very specific to various regional cuisines and cultures; with a little guidance, you can create dishes that are tasty homages to the cuisines you love to eat. In this two-part article (second part here), I'll cover both categories and sub-categories of some of the most popular ethn...

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

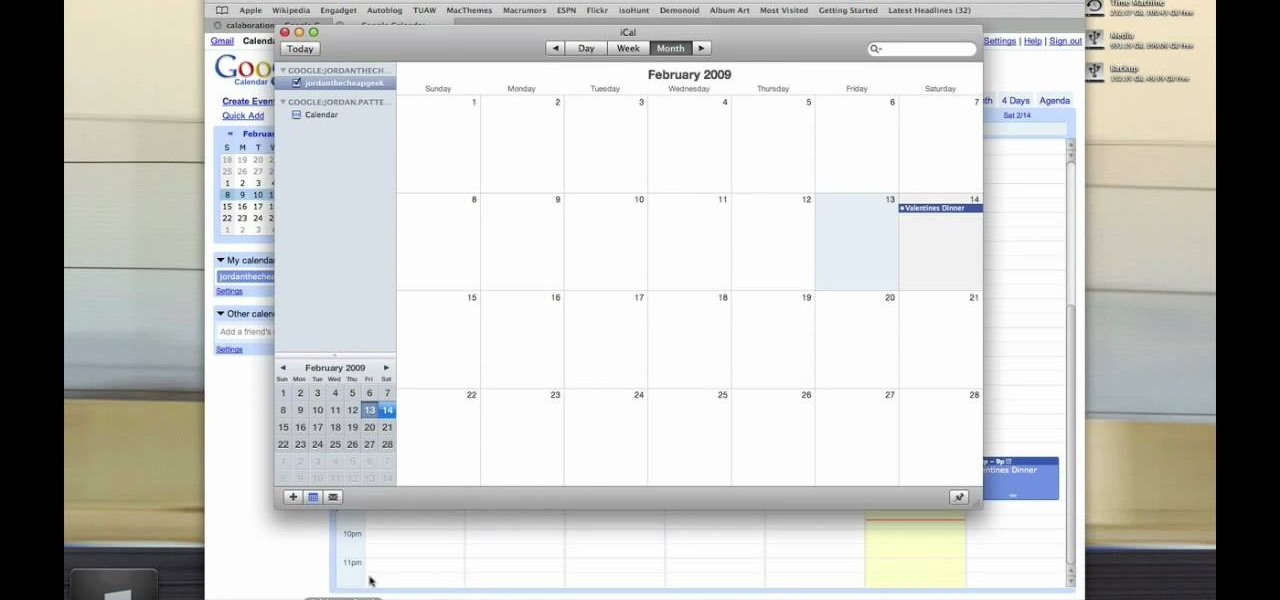
Jordan Patterson the Cheap Geek has made a video showing you the steps to sync your contacts and calendars on three mobile devices together, the iPhone, a laptop running Windows, and a Mac running OS X utilizing a few downloaded programs and Google Calendar. First he shows you how to sync calendars on the Apple computer, by downloading a program from Google code called collaboration code, and then running it. After putting in his g-mail account information, he tells the program which calendar...

This video shows how to make a recipe for pork potstickers. This recipe utilizes leftover pulled pork which is not made during the video. Some of the pulled pork is placed into a large mixing bowl. Next a table spoon of minced garlic is added to the bowl followed by a pinch of salt and ground black pepper. Afterwards, thinly sliced scallions as well as chopped cilantro are added to the mixing bowl. The mixture is then thoroughly mixed to combine and distribute all of the ingredients; this mix...

This video demonstrates how to wear your bandanna in a rockabilly style. First, you'll need to curl your hair in either rollers or hot sticks. This particular video utilizes both. Do not worry about including your bangs. Use three rollers on top, so the ends of the rollers are pointing towards your ears. The third roller will be on the top of the back of your head. Put to more rollers on each side of the top, this time the ends facing forwards and backwards. Use four hot sticks for the sides ...

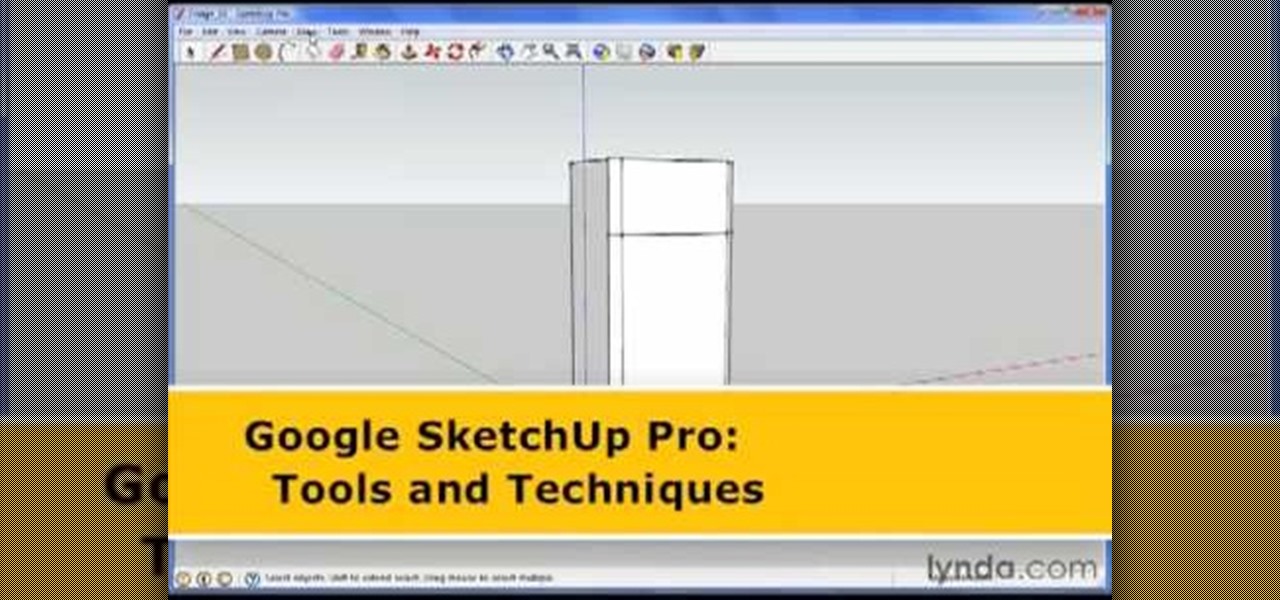
George Maestri from Lynda shows how to add interactivity in Google SketchUp Pro using a variety of tools in the program. Adding interactivity allows for added dimension and interaction with an object. The example used in the tutorial was that of a fridge, which after adding interactivity, allowed for the doors and drawers of the fridge to be opened. To utilize this technique, the object's file (without interactivity) should be opened. By selecting the fridge and then going to component attrib...

The gentleman, acting as the Instructor, starts the session immediately by suggesting that to teach early multiplication all parents should practice a method of "Count-by's" with their children when they are very young using ones to ten, twos to twenty, threes to thirty, fours to forty, and so forth. The Instructor then demonstrates this method of counting by tens using a grid behind him on a chalkboard which depicts columns of ten elements. He counts each column from 10 to 100, and then writ...

If you want to add interest to your nails, follow the steps in this video tutorial from Broadway Fashion Diva Nails. It shows you how to apply acrylic skulls, crossbones, and roses nails. The first step before application is to select nails that fit each of your fingers of one hand. Then, lay the nails out so that they are ready for application. Using pink gel glue, begin with your pinky finger. Utilize the tab to have control of the acrylic nail without actually holding the nail and getting ...

YOUTUBE Logan Salter presents a video demonstrating a method to create "Crocodile Tear" Makeup. The entire video is demonstrated through visual action, with typed titles in green appearing on the screen prior to each new step, and electronica music played throughout. Logan begins by applying moisturizer, demonstrated visually in the video by applying moisturizer to his facial area and moves at an increasingly faster rate through steps visually demonstrating how to apply various powders and br...

Stampin' Up Dawn shows how to use Stampin Up to create original gift card holders and sleeves in this craft tutorial. The tutorial shows how to create the Bashful Blue gift card holder. However, it should be noted that the Certainly Celery card does not utilize the scalloped edge design. The third style, Elegant Eggplant, uses ink #10510 and card stock #105126. You will need a strip of bashful blue card stock cut 4.5" by 7 3/4" scored at 3/4 and 4 1/4. Fold the score lines to create the sleev...