Being lost sucks. There really is nothing worse than going to a huge event with a bunch of friends or family and then getting separated. Instead of partying with the bros, you get stuck next to this lame couple who keeps seriously making out every ten seconds. SMH.

Minesweeper is one of those games that everyone plays, but hardly anyone actually knows how to play. Most people just click random squares and see how far they can get.

Hey guys, I was building my floating island earlier today (and having a quick look at the competition) and I came up with a couple of hints and tips that will really improve your islands.
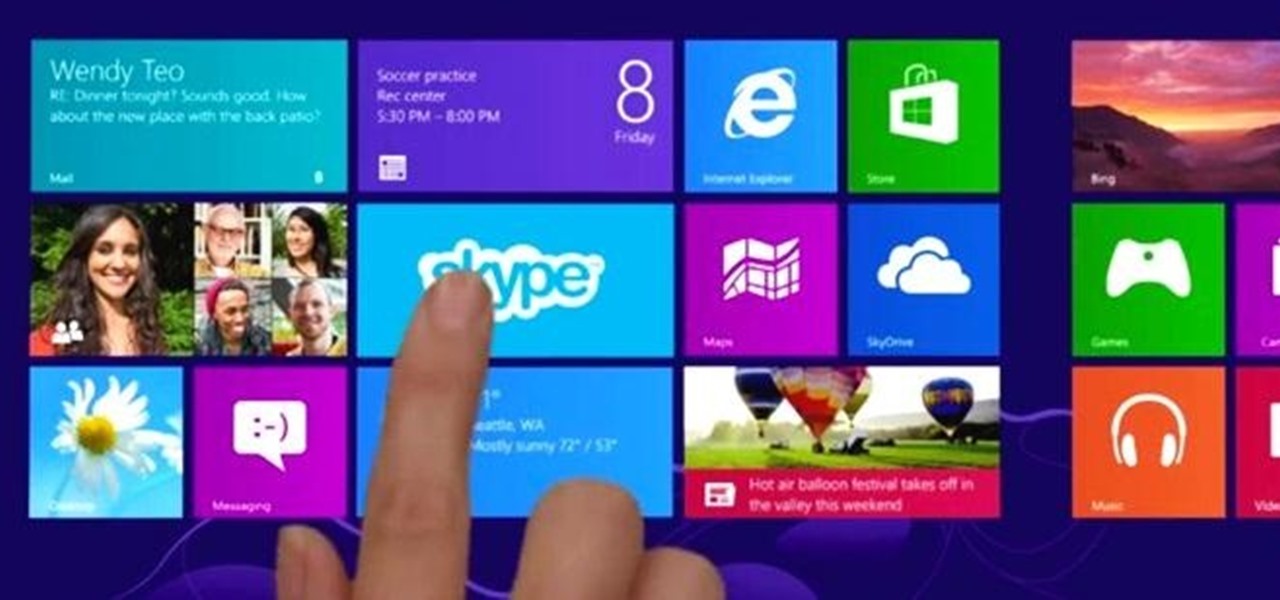
Windows 8 has been reimagined to take full advantage of touchscreen devices as the "future" of computing. A few years ago, touchscreen devices were super buggy and only played well with smartphones, but with the advent of the iPad and a ton of other tablets, touchscreen capabilities have spread to full-sized desktops and even televisions.

Before my time, people used to listen to music recorded on these things... I didn't really know what this thing was until my parents clarified and told me that they were called cassette tapes. These "cassette tapes" were utilized to store sound recordings on either side of the tape, which could usually hold between 30 to 45 minutes. I laughed at that information as I took out my iPhone 5 (roughly the same size), which can store roughly 40,000 minutes worth of music.

Small containers are useful for many things. They're good for storing snacks if you have children, as well as holding coins or odds and ends. But those regular store-bought containers are lame—who wants to keep their stuff in a Tupperware dish or old butter container?

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create a Times Square billboard in Photoshop.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Analog reel-to-reel tape is some of the most in-demand recording equipment today. Learn how to use a reel-to-reel tape machine in this free video series that will allow you to utilize this piece of musical recording equipment.

This tutorial for Sony Vegas 7 helps you utilize keyframes and create even better masterpieces!

Learn how to utilize this ankle bounce exercise as a part of your ladder training workout, geared at improving your athletic ability.

Abstract art may seem random but it often utilizes basic art and design theories. Learn more about making an abstract painting in this free art lesson from an art instructor.

The basics of two-dimensional design utilizes design elements such as space, balance and line. Learn foundational design skills with this free art video series.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

Your slow cooker isn't just for making lunch and dinner—it's also perfect for making a complete and super delicious breakfast with little work.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Traditionally, incorporating loops and grooves can translate into hours of hard work just to get the loop to fit your song's tempo and timing. Help is on the way from the Propellerhead's ReCycle which gives you full creative control over utilizing your looped material. Join electronic recording artist David Alexander as he shows you how ReCycle has revolutionized using sampled loops. In this episode, David shows us how to Chop Up A Complex Loop.

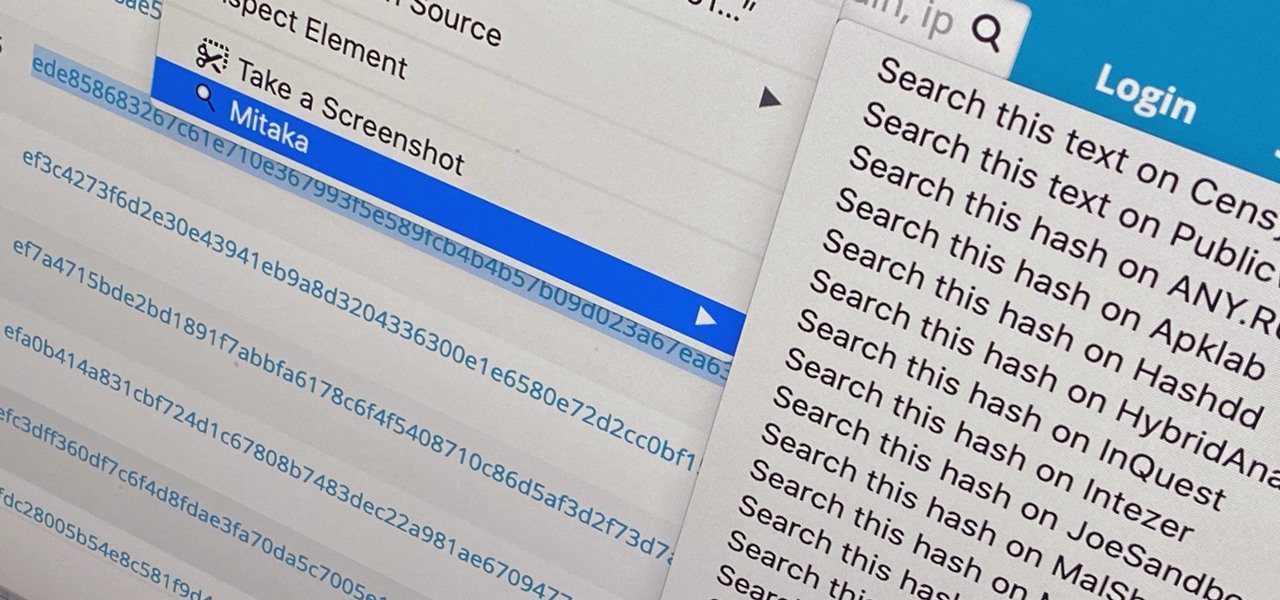
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

YouTube Music has been around since late 2015, but it only started becoming a viable music service in 2019. It makes sense for Google to utilize YouTube's existing library of music videos, remixes, and cover songs to create one massive music platform. But one downside is you get a lot of the music video versions of songs instead of the album versions. Thankfully, you can change this.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

It takes confidence and guts to pull off attractive and yet adequately frightening Halloween makeup as an adult.

It looks like Snap's foray into augmented reality billboards last year was successful, as the company has returned with two more outdoor advertisements for its Snap Originals series.

Parkinson's disease, a condition that can impair movement and coordination, affects over 10 million people worldwide. And with around 60,000 Americans being diagnosed every year, we're on track to see almost one million Parkinson's afflicted Americans by 2020.

The company that supplied some of the technology behind the Star Wars Jedi Challenges AR playset now has its own headset to offer.

For Snapchat users wondering if that selfie is ready to send to their crush, independent Lens Studio creator Andrew Mendez created a handy tool called the Smile Rater.

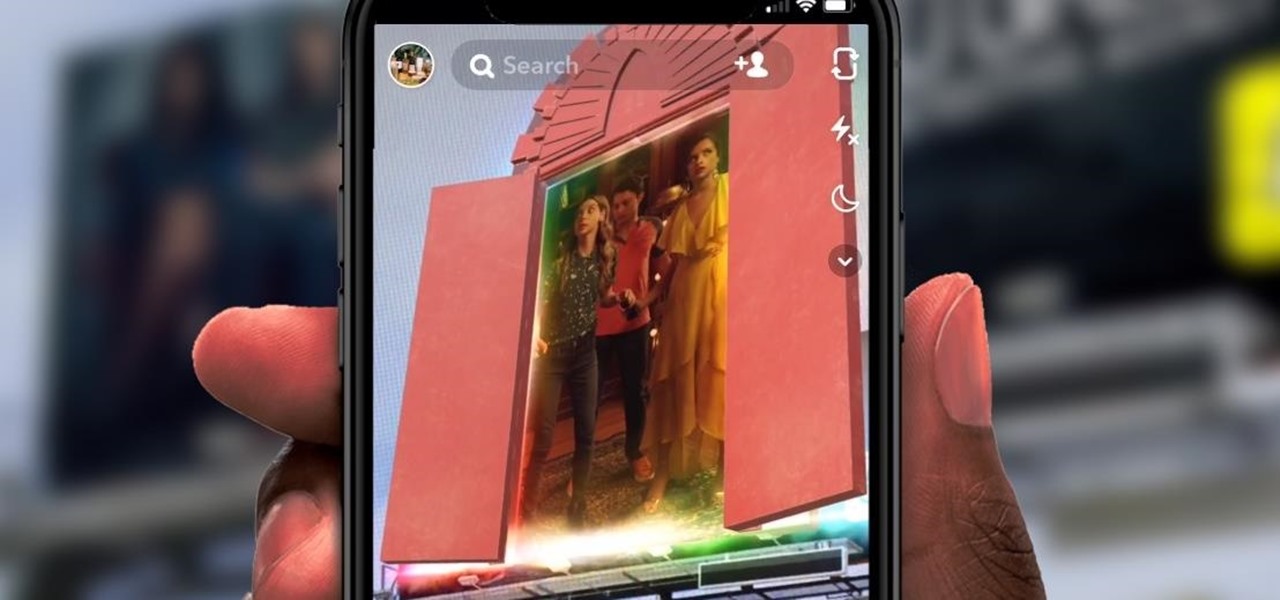
With the third season of Netflix's hit series Stranger Things set to debut July 4, it's time to crank up the hype machine, this time, in augmented reality.