
News: Samsung Locks Out Third-Party Accessories, but the Community Brings Them Back
Update January 27, 2014: Samsung has released a statement to address the flip cover issue, claiming it as a bug with a "fix" coming soon:


Update January 27, 2014: Samsung has released a statement to address the flip cover issue, claiming it as a bug with a "fix" coming soon:

You know that feeling when your cell phone gets stolen and you figure it is pretty much lost forever. You could've used one of the millions of device managers and trackers, but ya didn't. And the Good Samaritan is not coming to your rescue.
There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

Back when I was a kid, I didn't get many awards or trophies, aside from perfect attendance three years in a row. If only there was an award for procrastination. While there are apps out there for my iPhone like Clear and even the stock Reminders app, they still don't push me hard enough to get things done on time—or at all.

The new Samsung Galaxy S4 has something no other phone has ever had before—weather sensors. Older devices like the Galaxy Nexus, S3, Note, and Note 2 do have a atmospheric pressure sensor, aka a barometer. However, they do not have a thermometer or hygrometer like the GS4 does, which measures ambient temperature and humidity.

I've taken a few photography classes back in the day, so I'm pretty confident in my abilities with a DSLR, but my iPhone is a completely different story. Lighting makes all the difference, so unless you're outdoors in the sun, it's hard to take a good snapshot with a mobile.

You know that moment when you finally figure out something, but you figured it out years after you really needed it? Don't you freaking hate that?!
If the Nexus 7 wasn't your first Android tablet, you may have noticed something different with the user interface when compared to other Jelly Bean tablets. You may not know exactly what it is off the top of your head, but it's there.

"Dude-man-bro, are you going to Coachella this year?" If I got a dollar for every time I was asked that question, I might just have enough money to actually buy the dang ticket. Concerts have been, for a very long time now, a great way to spend a night or a weekend having fun with friends and listening to some great tunes.

With Google Maps, we can fly from Los Angeles to Tokyo to Paris and New York—all in a matter of seconds. We can zoom in with relative ease and flock around the city of our choice, checking out restaurants, historical landmarks, traffic and scuba divers. Easily the most recognizable and iconic part of Google Maps are the markers that signify all of these locations and point of interests. The iconic markers have already spurred artists to create Google Map inspired art pieces—with one such arti...

The Jelly Bean update brought a lot of cool features to the Samsung Galaxy S3, but one nasty bug remained. Something was causing "Android System" usage to be consistently high. Of course, the percentage of this process that is used is dependent on what you're doing at any given time, but it shouldn't be anywhere near this level with "standard" use (calls, texts, emails, light browsing, etc.).

For the most part, keyboard shortcuts are great. They save you some time and make it easier to do everything right from the push of a button. But like most things in life, there is always a caveat, and in this case, for me—it's a huge one.

Creating a class in Black Ops 2 is kind of like an art form. Every player has an insane amount of options for creating a character for all sorts of situations. Combining perks, with secondary weapons, and attachments allows for a wide range of killing options. But in order to unlock a lot of these perks and attachments, you need to gain XP. Gaining XP and collecting tokens is the lifeblood of the online gaming experience.

I think part of the reason why I don’t eat more vegetables or fruits is because there's always a process—a simple one, but a process nonetheless. Having to wash my fruits and veggies is just flat out annoying. I just want to eat them, not take a shower with them.

Using a second monitor is great for multitasking, especially if you tend to max out your computer's brain power on tons of simultaneously running apps that you want to see, well, simultaneously. That second screen becomes more like a lifesaver.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Think of your brain like a muscle, if you train it correctly and diligently, it will perform at its top capacity. The retention of information is a skill like any other that can be improved with some practice and even rest when appropriate.

In this video tutorial, viewers learn how to draw a skull. Begin by selecting a skull image to draw from. Then draw a circle and sketch a few lines to position the eye sockets, nose and mouth cavities. Now erase the guidelines and re-sketch the drawing. Then start toning the eye sockets and nose cavity by shading. Now tone the other parts of the skull. Finish by shading the background. This video will benefit those viewers who are interested in drawing and art, and would like to learn how to ...

In this tutorial, learn an important safety tip for the next time you head out camping or hiking. In this video, you will get advice on how to make a Swiss seat rope harness. You will learn to utilize a length of rope to make a field expedient rappelling harness, that is similar to the seat used by the military. With practice, you can tie this Swiss seat in 90 seconds or less. Essentially, this is a high speed, low drag way to make your own harness. This harness is useful for rappelling or ex...

This step-by-step video tutorial will have you building metal riffs in no time! Andrew Wasson of CreativeGuitarStudio has written a short two-part riff using the harmony from a popular scale out of the style called Phrygian dominant. For the riff, Andrew uses a series of open strings, eighth note triplets, hammer-ons, and pull-offs. Because a lot of progressive metal utilizes different time signatures, Andrew changes the time signature for the last measure of the riff. Don't forget to downloa...

Teresa Richardson from the crochet-mania blog will be teaching us how to crochet a left handed seed stitch scarf. In her video, she is going to be guiding us through the process of crocheting single and double seed stitches as well as providing us with step by step instructions on how to make the scarf. Teresa designed this tutorial with beginners in mind, so newcomers are more than welcome to utilize and learn from it as well. Be sure to have a crochet needle and some yarn handy prior to wat...

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Learn how to design a defense to stop dribbling penetration or passes to the middle. If you're a basketball coach, you'll definitely want to utilize this two-three zone defense.

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.
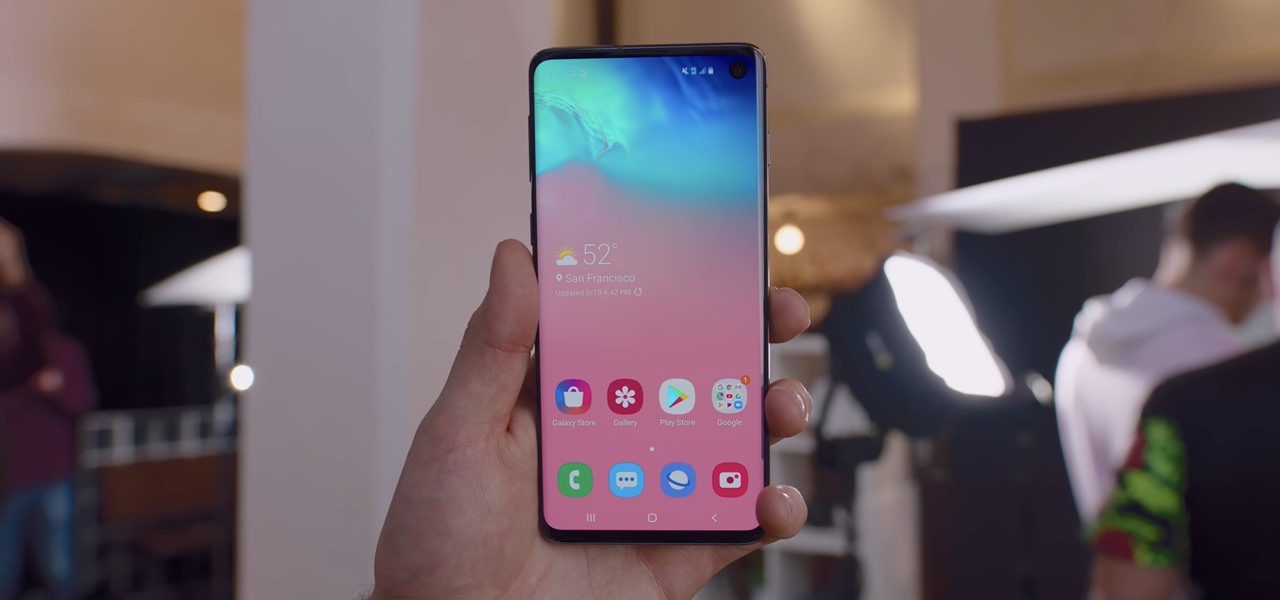
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.
Sure, Snapchat AR Lenses can be fun, but they can help communicate complex issues as well. While our Facebook news feeds were filled with references to 311 Day, March 11 is also World Kidney Day, the United Kingdom's National Health Service Blood and Transplant (NHSBT) used the occasion to educate its constituents about organ donation.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.
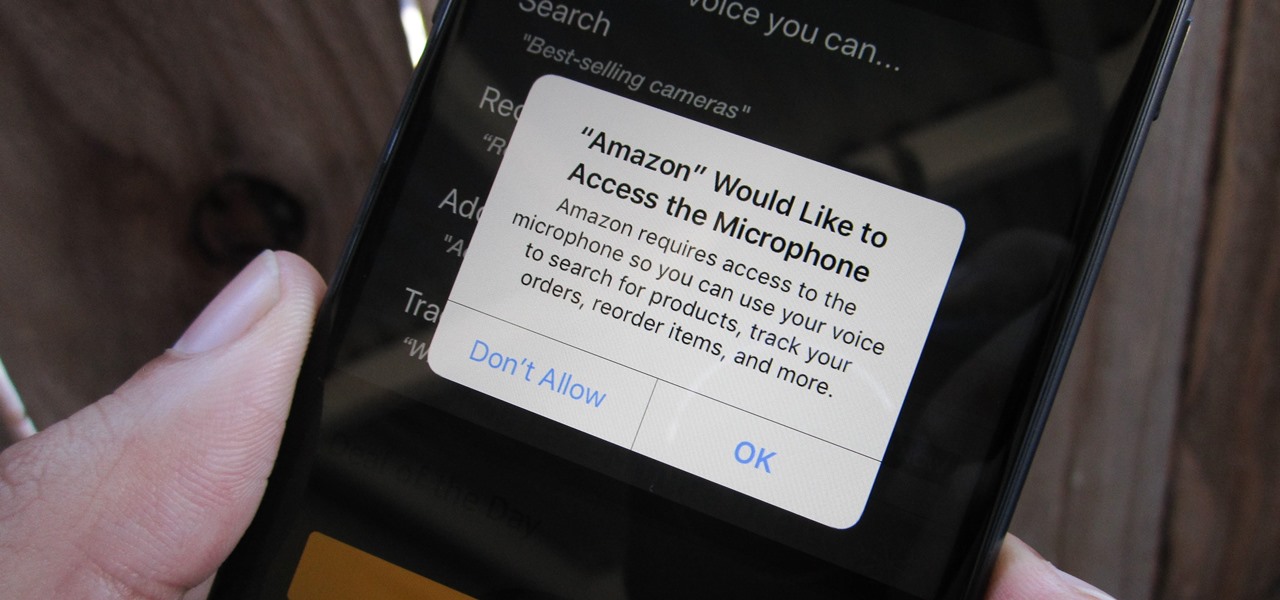
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.