
How To: Stop hiccups with a glass of water and chopsticks
This how to video has a unique idea to get rid of hiccups. All you need is a chopstick and glass of water. Watch and learn how to utilize the chopstick and water to cure your hiccups.


This how to video has a unique idea to get rid of hiccups. All you need is a chopstick and glass of water. Watch and learn how to utilize the chopstick and water to cure your hiccups.

Dr. Allen Bridges shows how to incorporate the use of the CIDR (controlled intra-vaginal drug releasing devices) in a synchronization program for beef cattle. CIDR devices can be used to manage the reproductive cycles of female cows. Learn how to insert and CIDR devices and how to manage the estrus cycles of female cows for farming convenience, by watching this instructional video.

This video shows how to utilize 2 step stamps. Learn how to create a layered technique that adds dimension and a professional touch to stamping projects.

Tim Carter discusses the different types of wood and how they are recognized and how their attributes are utilized. Informative video will help to make sure you use the proper wood for your build.

This video will show you how to utilize proper paintball gun posture, as well as effective methods of sliding during paintball.

This video covers some very basic tips on snake play, dorito play, dead zones, and breakouts.

In this golf demonstration, you can learn the two coin drill that teaches you proper balance and weight shift for your finish.

This video covers the construction and assembly of a decorative pencil holder. These make great gifts and are excellent for utilizing scrap. This video is for the more experienced woodworker, knowledge of tools is required. To apply a beautiful finish on the pencil holder, see the Wood Whisperer's finishing video on popping the grain.
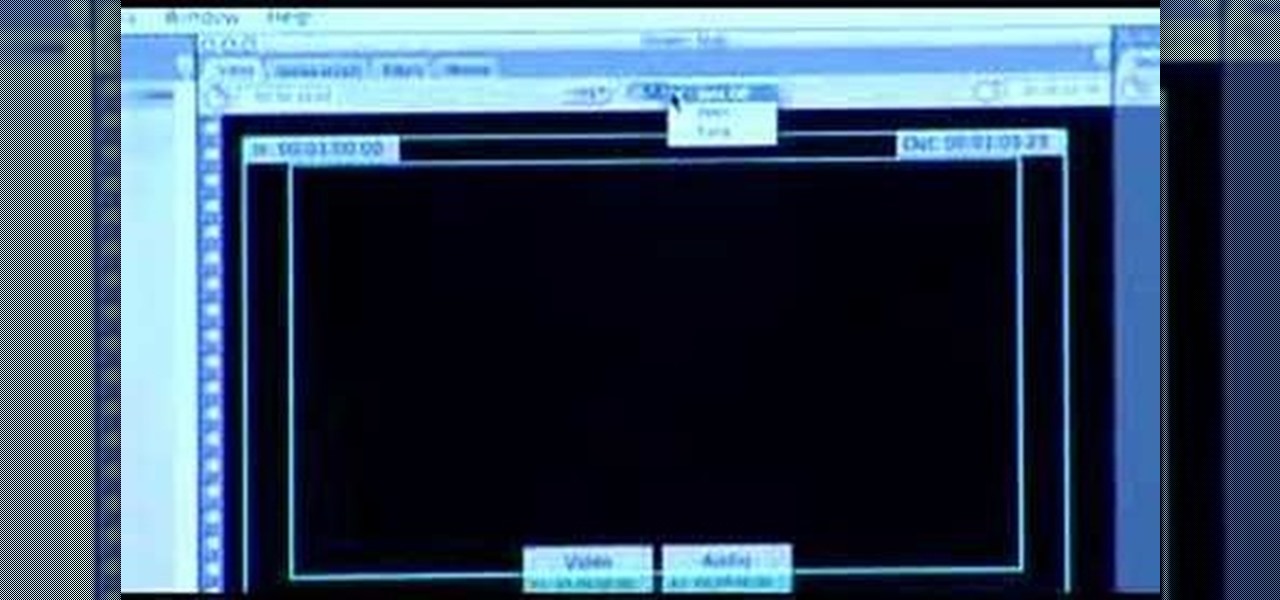
Matt, the Shirtless Apprentice, follows up his last segment on syncing timecode for a multi-camera shoot with a quick explanation on how to utilize this technique in the edit. Learn how quick and easy multi-camera editing can be when using the multicam function in Final Cut Pro.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

In the second part of this tutorial, we are going to crack the hashes that we've captured previously. I'm going to explain how to do it with the powerful John the Ripper. It comes with Kali by default, so no need to install!

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Sony has already splashed through IFA 2014 with its Smartwatch 3 and new Xperia Z3 devices, but the last drop from Sony was for gamers—specifically those that game on the PlayStation 4.
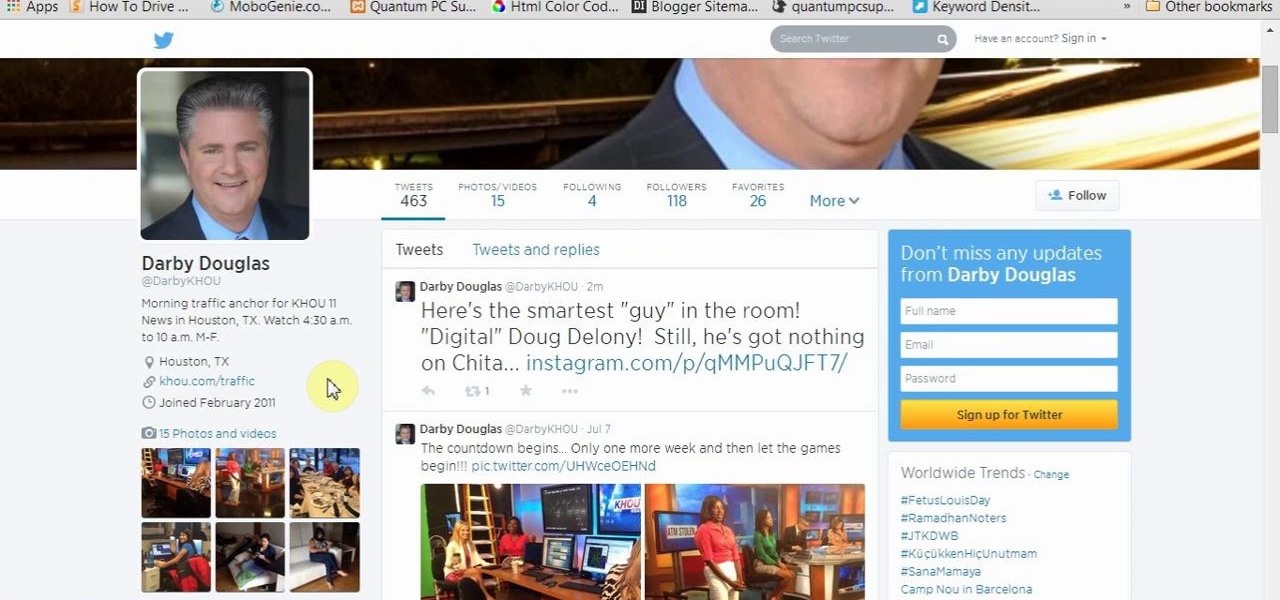
This video will show you how to search on twitter using parameters without Signup. You don't need to be sign up for twitter search. Anyone could use this twitter search feature and utilize parameter. Watch the video and follow all the steps carefully.

This video will show you how to utilize the shared album on Facebook. Multiple users could view, upload and edit picture of the same album. Thanks for watching my video.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

Macro extension rings are an affordable solution to buying expensive macro lenses, but there is no way to control the aperture when using macro extension tubes without contacts. However, by utilizing a piece of paper, you can easily control the aperture.

Is your life's goal to become a world-renowned architect and build a funky postmodern skyscraper in Dubai? Then start small: Other than learning how to sketch blueprints, you must be able to model your creations from paper.

Watering is the key to getting your lawn, landscaping and flowers looking lush and healthy. First-time homeowners don't always get a lush lawn to begin with— it takes time and a little care to get there, and water is what you'll need! Lowe's has the advice you need for watering your lawn.

If your yard has hedges, shrubs or trees, chances are you'll need to occasionally cut them back, and that's where pruning comes in handy. Not only does pruning give nice shape to the hedges, but it can also help them grow thicker and healthier. Lowe's has the advice you need to tame your bushes.
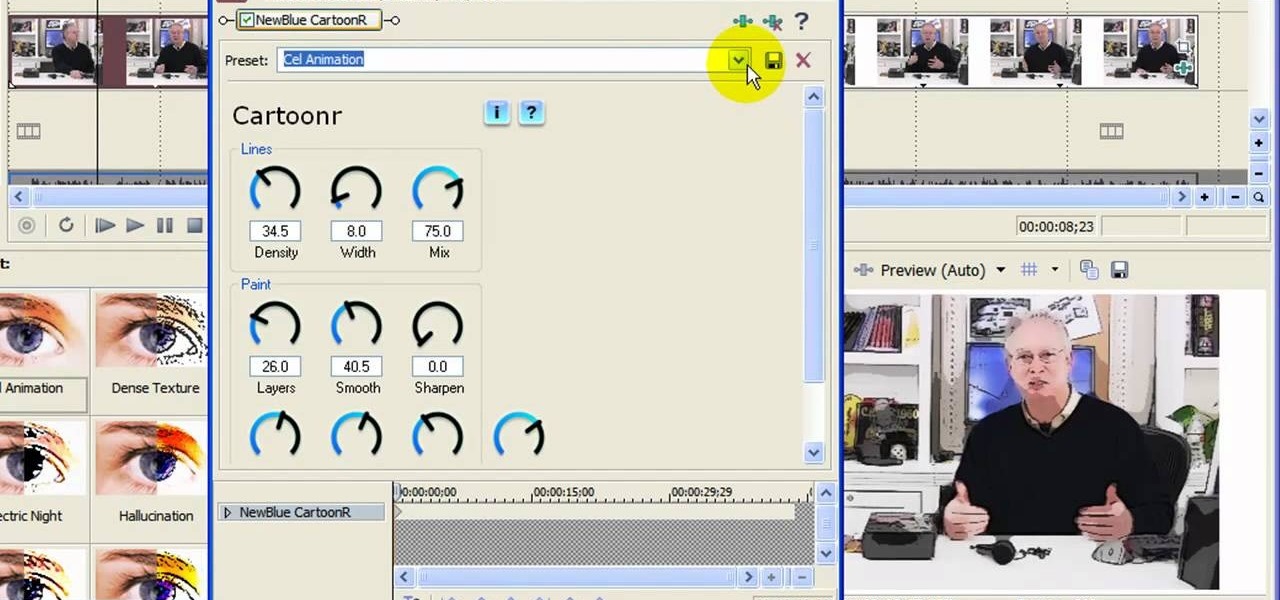
In this video tutorial, viewers learn how to create a cartoon effect from video in Sony Movie Studio. Begin by importing the video clip(s) into the time line. Then click on the Video Effects tab and select New Blue Cartoon R. This is a plug in that needs to be downloaded. Users are able to select various different cartoon styles from the Preset drop-down menu. Users are also able to configure the lines and paint of the cartoon effect. This video will benefit those viewers who enjoy create and...

Since when did everyone think that smokey eyes HAVE to be brown/black/silvery? While we love the way a murky brown smokey eye looks, there are so many more options out there if you want to do a smokey eye look but are bored of the usual colors.

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...
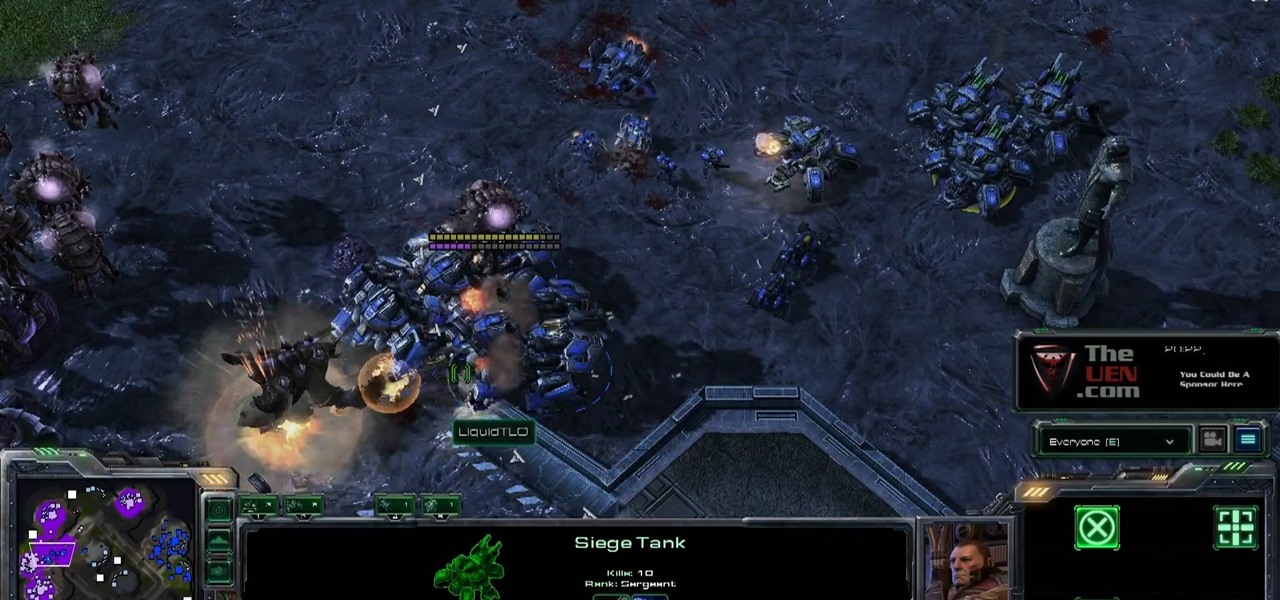
After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to build an effective and diverse army of Terran units that utilizes...

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to restore your Google ranking after your website has been hacked. Hopefully you never will be, but if you are this video is her...

Open string voicings are one of the first skills you learn in guitar. Essentially, open string voicings are the fundamental notes of unstopped, full strings. So, for instance, an open string is playing the G note and letting it resonate.

Unlike being a square, being a square knot means you're multifaceted, fun, and unique. Of course, we're talking about square knots in friendship bracelet/jewelry making, in which you utilize two different colors of string to create a tight zig zag knot pattern followed by loops.

The ssp (slip, slip, purl) is a decrease made on the purl side of your knitting, and is a mirror decrease to the p2tog (purl two together). In this clip, it's demonstrated in the English style. The ssp (slip, slip, purl) is a decrease made on the purl side of your knitting, and is a mirror decrease to the p2tog (purl two together). In this clip, it's demonstrated in the continental. style. For more information, including complete, step-by-step instructions, and to get started utilizing this d...
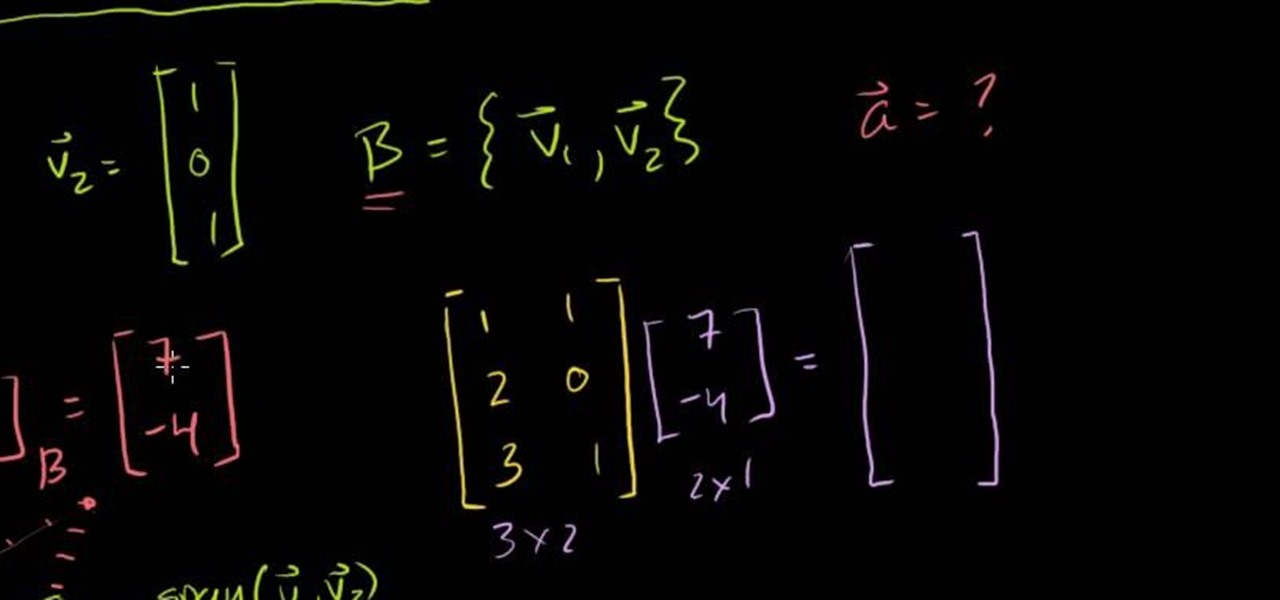
Need help figuring out how to utilize change of basis matrices in linear algebra? From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how use a ...
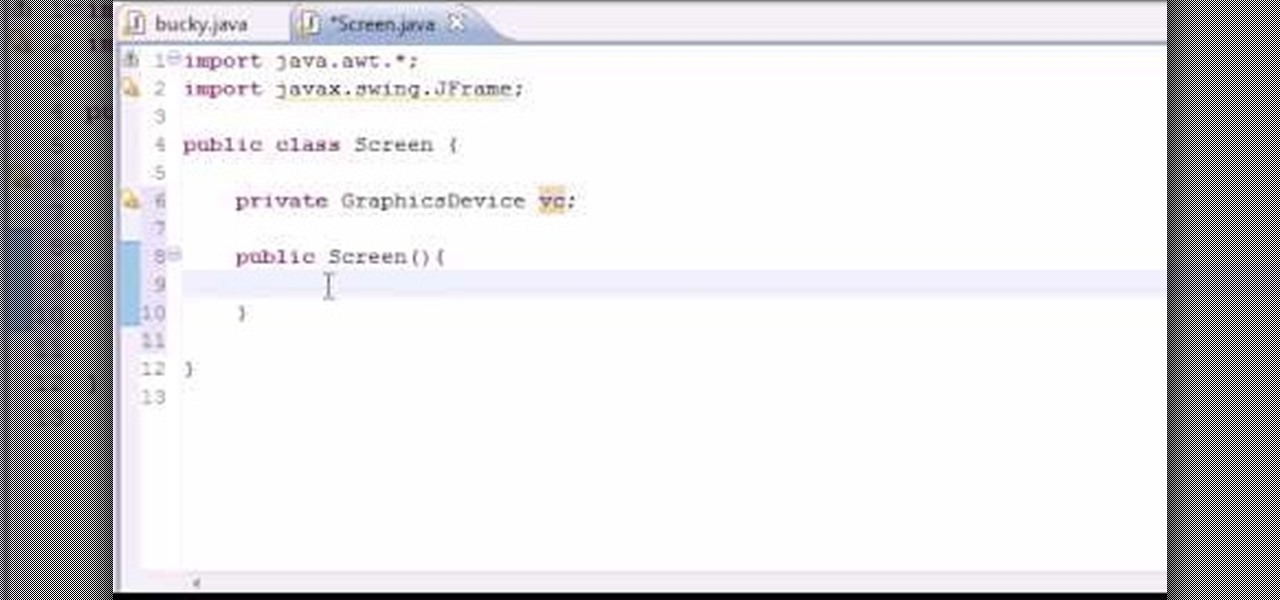
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBoston will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to utilize and display graphical user interface elements like windows when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.
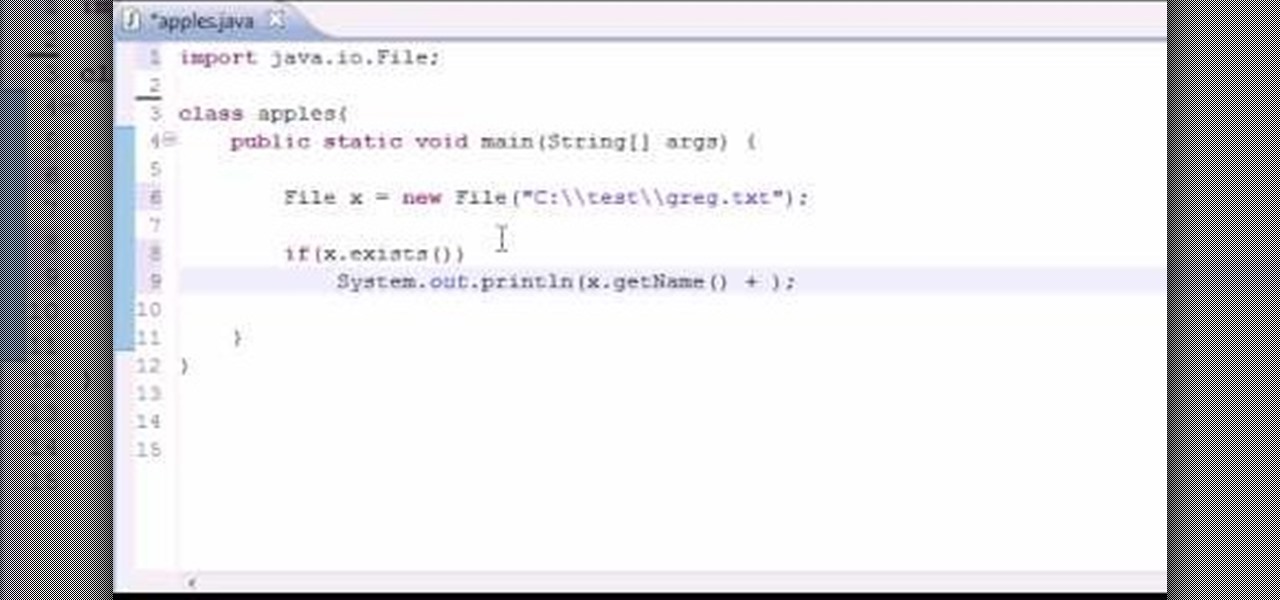
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to utilize Java's file class to retrieve information about an external file. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

In this how to video, you will learn how to spike your hair. You will need hair spray, a comb, and a blow dryer. You will also need a mirror that you can set up on the floor. First, wash your hair. Next, scrub it with shampoo. Once it is rinsed out, dry it with a towel. Comb out all the kinks in your hair. Now, generously apply hair spray to your hair. Next, utilize gravity by hanging your head over above the floor. This will create perfect spikes. Use the blow dryer on your hair while doing ...

When you need to gather information without anyone knowing you will need to utilize covert audio surveillance. There are a variety of ways and technique to most effectively get the information you need.

On this video from Bushcraft Machete, he explains the purpose of a scandi edge and how to use it. He uses the machete as a planer, stripping the bark from a log by holding the machete almost flat against the log and tapping the back of the blade with a stick. He explains that a scandi edge is sharpened all the way down to a point and has a very low angle. This type of edge makes the machete useful for carving off thin strips of wood. He has sharpened his machete with a scandi edge near the ha...

This gem, an extensive cinematography video tutorial on Motion Control systems by Mark Roberts Motion Control. In some ways this video is an advertisement for the systems they create, but there is a lot of useful knowledge shared that transfers to planning, shooting, and compositing with lesser tools. This instructional video explains what motion control is and the features of the Milo Motion control system rig. A ton of fantastic commercial and music video creative work is shown, with shot b...