You can read at 500 words per minutes. Don't believe me? Here, see for yourself. This amazing technology comes from the startup Spritz, and they're ready to unleash it onto the smart device world, starting with the Samsung Galaxy S5 and the Galaxy Gear line of smartwatches.

Last week, we covered a new, open-source live wallpaper (LWP) called Muzei, and less than a week later we have no less than twenty beautiful add-on extensions to the app.

No matter how careful or decent you are, there will always be pictures or videos that you want to keep private. They say a picture is worth a thousand words, but if someone were to go through my photo gallery, only one word would be coming out of my mouth—"%@&#!!"
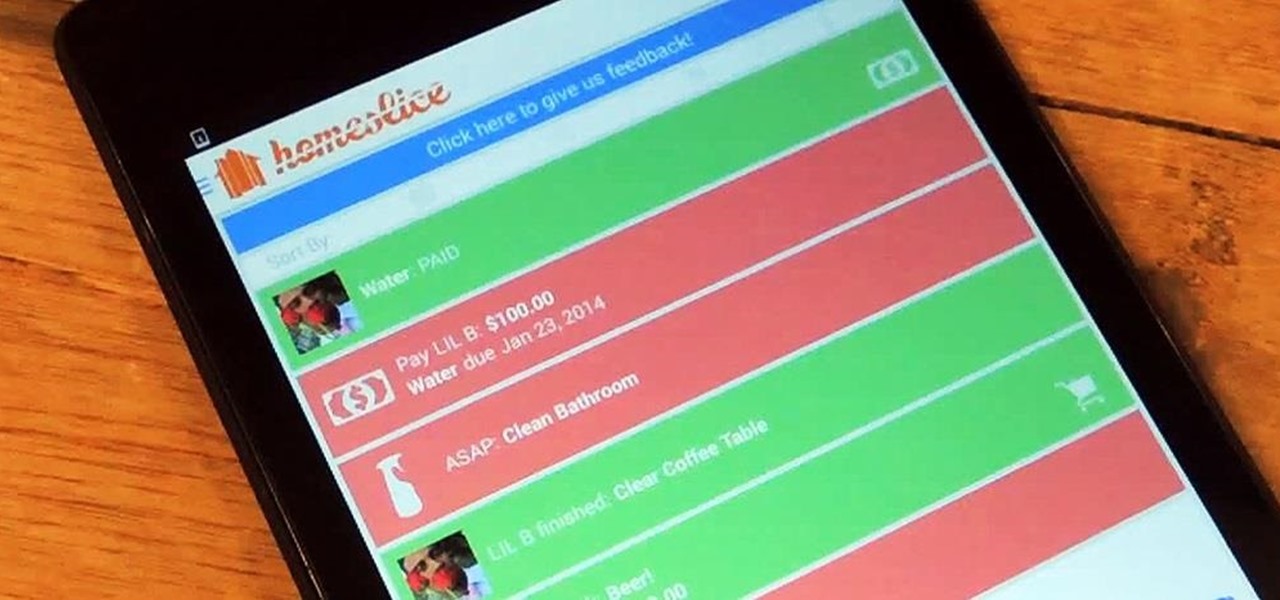
We've all heard our fair share of roommate horror stories, or have some of our own, because we never truly know who someone is until we've lived with them. Cohabitation issues generally revolve around things like bills, chores, cleaning, and groceries. Approaching a roommate, especially an adult one, to remind them to do their chores can be an anxiety-ridden and daunting task. After all, we're roommates, not parents!

I have literally played Madden, watched YouTube videos, and listened to music on my phone all at the same time. Some would call this pathetic, but I call it talent. Life is way too short, so I need to get the most out of it when I can. Thank goodness for multitasking, which should be a key feature when you're looking into a new tablet or phone.

One of the coolest features that Samsung built into the Galaxy S4 is the infrared (IR) blaster and WatchON software to control your television. I've been using my GS4 for the past few weeks to control my DirecTV setup and it works great. Smartphones are truly becoming all-in-one devices these days.

It may not seem like it, but the Status bar at the top of your Samsung Galaxy Note 2 is one of the most important and heavily utilized features. From checking the time, to finding out your battery percentage, to viewing Wi-Fi and cellular connections, the Status bar is critical for keeping tabs on your device.

Of the hundreds of uses for our devices, the one that I cherish most is the ability to kill time just about whenever and wherever I need to. Whether it's reading news, checking social media, or watching videos, we have a ton of ways to pass the time in that two-hour DMV line or dentist's waiting room.

BEATS by Dr. Dre started making their studio-style headphones and speakers over four years ago, which claim to help listeners actually "hear" music as it was intended by the artists, since commodity headphones and earbuds are known for producing lackluster results. But you can only go so far with Beats Audio headphones, since your computers and mobile devices weren't built to take advantage of high quality audio equipment.

The advantages of rooting have been covered before, and with rooting comes flashing ROMs and mods to your device. The easiest method for flashing anything is to do it through recovery.

The director of 100 Musicians and Nurse/Fighter/Boy talked with us about old school filmmaking Charles Officer has directed shorts, music videos for K’naan, and the features Nurse/Fighter/Boy and Mighty Jerome, a documentary about Canadian track star Harry Jerome. His new short 100 Musicians, which screens Monday as part of Short Cuts Canada, is a small ode to civic optimism, concerning itself with a lovers’ argument over who exactly misheard a radio DJ reporting the plans of Toronto’s much m...

Tai Chi is a meditative practice that helps to relieve the body of stress while centering the mind and soul. Learn about various movements and postures utilized in Tai Chi from a professional Tai Chi instructor in this free video series.

Tai Chi is a meditative practice that helps to relieve the body of stress while centering the mind and soul. Learn about various stretches and positions utilized in Tai Chi from a professional Tai Chi instructor in this free video series.

Learn how to voice certain chords on the piano in this free video music series that will teach you how to utilize one of the essentials of mastering the piano - voicing chords.

There are a few julienne peelers on the market, but how do they work. Watch this how to video for a quick demonstration on the proper or way to utilize a julienne peeler.

If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

One feature in iOS you're likely underutilizing is 3D Touch, a highly useful, unique tool for iPhones ever since it first appeared on the iPhone 6S. Apple's pressure-sensitive interactivity gives iOS an extra layer of functionality, which can be clearly seen across the entirety of your device. From the lock screen to the home screen to the apps in between, there are plenty of ways to use 3D Touch.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Eating out is great, but being able to cook the delicious ethnic foods you eat at restaurants is even better. It may seem daunting to put together a bunch of ingredients with which you might not be familiar (some with names you've never even heard of!), but with the guidelines below, you'll be making your own versions of ethnic favorites in no time.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.

This video series will teach you how to train your cat, emphasizing positive reinforcement obedience techniques. Utilize clickers, water and meaningful alternatives to bad behavior to help your feline friend be a happy and non-destructive member of the family.

There are a lot of great features for your iPhone with iOS 18, released Sept. 16, but one of the coolest features is also one of the simplest and most satisfying — one that you'll notice every day you use your iPhone. And for now, it's an iPhone exclusive, so you won't get the same gratifying experience on an iPad with iPadOS 18.

The iPhone 12, 12 mini, 12 Pro, and 12 Pro Max's new Scene Detection mode automatically adjusts Camera's settings to best suit your subject. That means it won't use the same shooting options for a close-up shot of your friend as it would a wide-angle landscape picture. If you don't want Apple to choose how your scene should look, there's a way to stop it to regain some control.

Google Drive has been a gamechanger in the business world. First launched in 2006, Google Sheets has become much more than an alternative to Microsoft Excel. The powerful spreadsheet program is a boon for efficiency that's accessible wherever you have an internet connection—or when you have time edit offline.

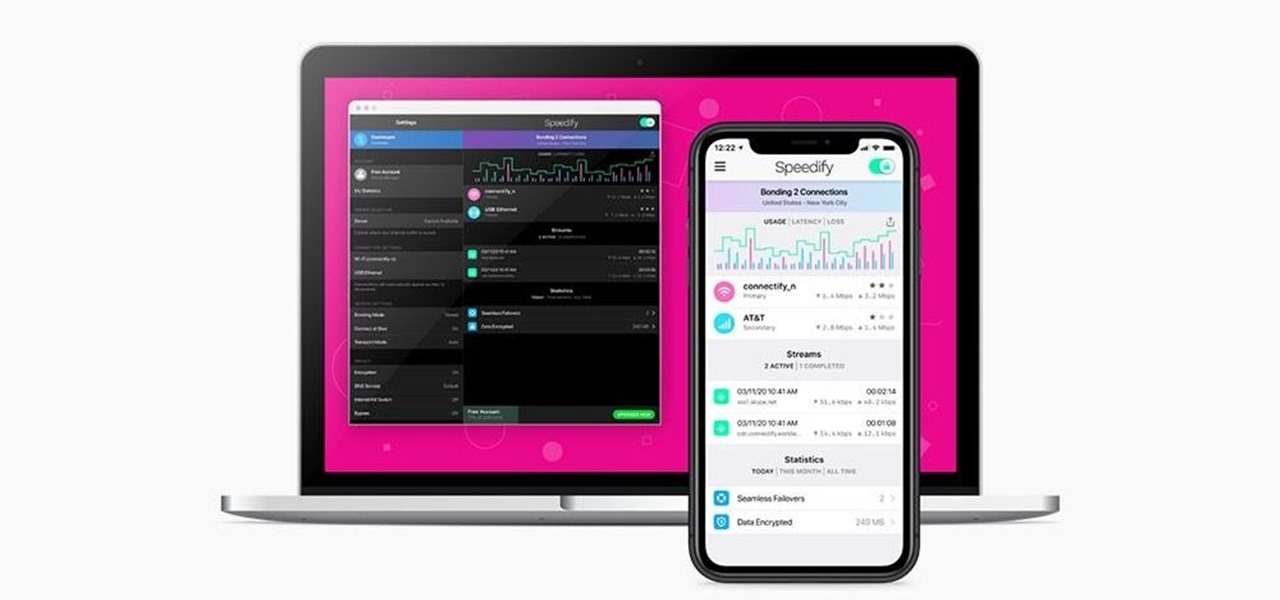
Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.

If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.

It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.

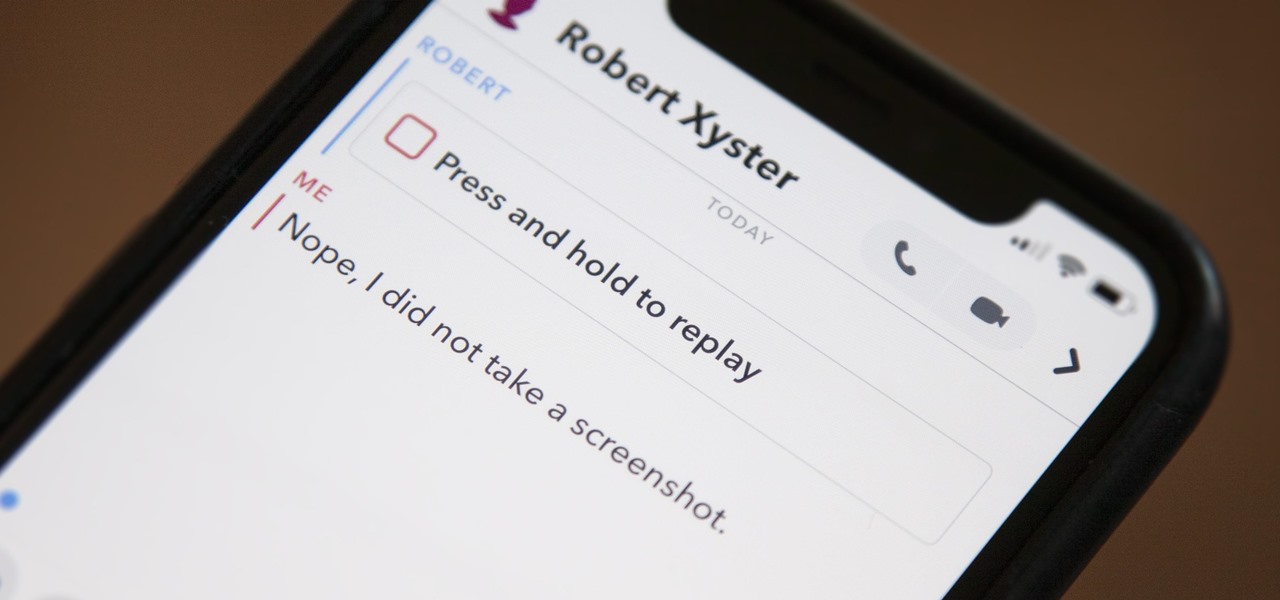
Snapchat doesn't prevent you from taking screenshots of snaps received, but the other user will get an alert either as a prominent push notification or a subtle note in the app. Snapchat has improved its screenshot detection abilities over the years, so it's much harder to circumvent its technology for truly undetected screenshots — but not impossible.