In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

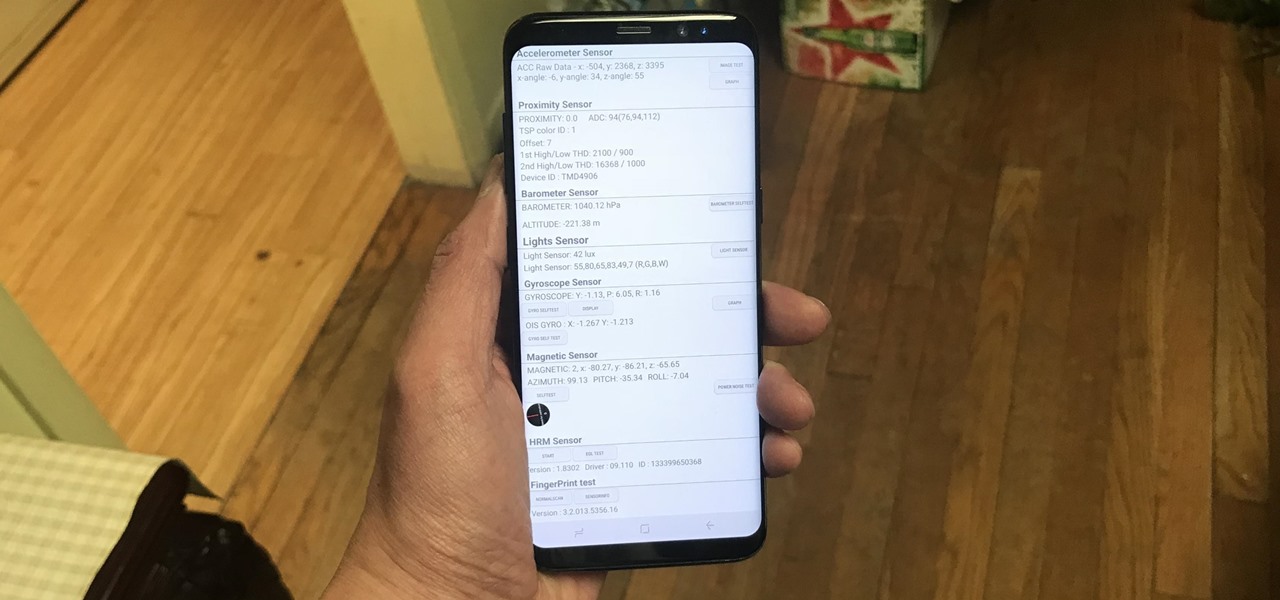
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

Your days as an ordinary Muggle are over — as long as you have an iPhone. With just a word or two, you can use your iPhone and newfound Muggle-born powers to cast spells or utilize charms just like Harry Potter and team. Only your "wand" is from Apple, not Ollivanders in Diagon Alley.

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

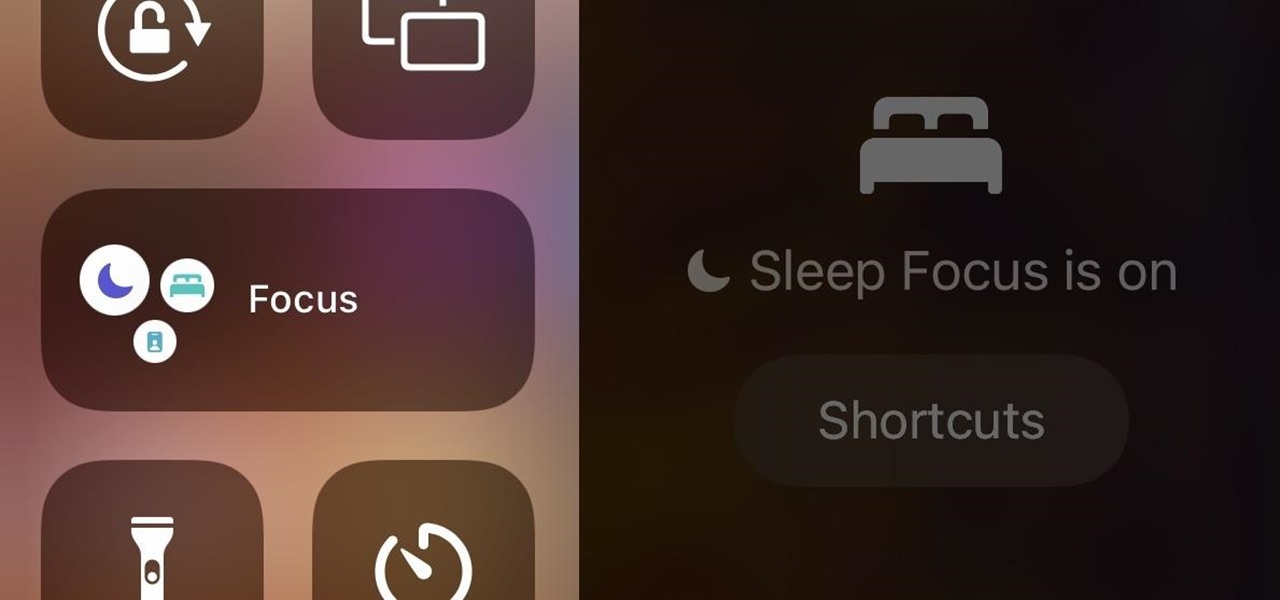
In iOS 15, Apple unveiled a new feature called Focus, an extension of Do Not Disturb that lets you focus on the one thing that's important at any particular moment. It does so by minimizing distractions from your iPhone and other Apple devices, but there's a lot you should know about setting up and using Focus on your iPhone or iPad before you dig in.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Not sure I quite understand the point of modding two Powerbooks into a snowboard, but I admire the energy behind the project. Very rough translation via YouTube:

"Picture Perfect" is a five minute film that won Best Cinematography in the Gainesville 3 Day Film Challenge in January 2012. A Portuguese photographer struggling to reconnect with his artistic passion admires a woman from afar. Made in two days with three Canon 7Ds and various Canon lenses.

Impress your friends by learning how to make pie crust decorations with this easy-to-follow cooking video. This pie decorating lesson is brought to you by Susan Reid on How2Heroes. Search How2Heroes on WonderHowTo for more cooking videos.

Creating a wooden inlay for any piece of furniture can help add a beautiful accent that will be admired by all. In the past, making inlays was a difficult task that required time and patience and was a tough challenge for any woodworker. Nowadays, technology is so advanced, that making these inlays can be an easy task, especially when you use a router. Check out this tutorial on how to use a router in order to create a great inlay for you table, dresser, or whatever you want. Enjoy! Make a gr...

Top-Windows-Tutorials is a great site dedicated to Windows tutorials for almost all things Windows. Whether you are a computer novice or an expert in Windows operating systems, you'll find useful information in these guides catering to your level of expertise. These user friendly and easy to follow free Windows tutorials will show you all that you can do with your Windows PC.

Top-Windows-Tutorials is a great site dedicated to Windows tutorials for almost all things Windows. Whether you are a computer novice or an expert in Windows operating systems, you'll find useful information in these guides catering to your level of expertise. These user friendly and easy to follow free Windows tutorials will show you all that you can do with your Windows PC.

There are many ways to open a bottle, but you have to admire the simplicity and karate-esque action required in Instructable member Carleyy's scrap wood method. Don't be deterred by the use of power tools in the video below. All you really need is a piece of scrap wood, one nut, and one bolt.

Glastonberry Solar Concept Tent

Dirty or hazy headlights can cause your visibility to drastically decrease, but the kits to clean them can be expensive. Save yourself some money and time with this fast and easy trick.

Poker, Blackjack, Old Maid... take your pick. A marked deck will make you an ace at 'em all. For this cheat you need a Bicycle deck, a box cutter, keen eyesight and an excellent memory of the code. Essentially, you're carving a miniscule symbol for every card's value onto its back.

We have long admired the imaginative energy of IndyMogul. A new generation of filmmakers empowered by affordable filmmaking technology and free distribution.

Danny Lipford shows you how to utilize the space above your garage door. Just watch this video tutorial to see how to use the space above a garage door with a storage rack.

This video shows how to check for and prevent a scratch in pool by utilizing the 90 degree rule and sending the object ball into the correct pocket. Two techniques shown to are "follow" and "draw," hitting the cue ball above or below the center. Prevent a scratch in pool using the 90 degree rule.

With 2015's generation of flagship smartphones fast approaching, LG is turning to virtual reality to clear its G3 inventory. VR for G3 is a Google Cardboard-inspired virtual reality headset that was custom fit to encase the phone and uses a pair of lenses to create stereoscopic imagery.

If you're a musician in need of some lessons, there's no better way to learn than with MusicRadar's so-called "Tuition" instructions. Although the title tuition is misleading, this video class is anything but costly, because it's free, right here. Whether you're looking for help with your voice, bass, electric guitar, drums, guitar effects, piano, Logic Pro or production techniques, Music Radar is here to show you the way.

Learn how to use the new displacement ratio tool in modo 302. The Displacement Ratio render option optimizes projects which utilize large displacement mapped surfaces such as ground planes or water. modo 302 is a service update, free for all modo 301 users. Use displacement ratio in modo 302.

You can utilize your television to display your videos and other files that are on your laptop. Connect your laptop to your television.

This tutorial explores how to create and utilize the cloth effects available in Maya. Specifically, it will go over draping cloth over an object. Use the cloth effect in Maya.

Some free tricks on how to use the color range command in Photoshop. Many people use the old method of utilizing the magic wand tool for selecting areas of color, the color range selection tool has more flexibility and control. Richard walks you through using this tool and shows some new features added in Photoshop CS4.
Greetings and Salutations,

Sanctum is NOT directed by James Cameron, but it DOES utilize his Avatar 3D camera technology so that must mean it'll make a ton of money, even if it stinks. Right?

Sanctum is NOT directed by James Cameron, but it DOES utilize his Avatar 3D camera technology so that must mean it'll make a ton of money, even if it stinks. Right?

This video demonstrates the process utilized by seamstress Maria Perez to make piped pockets for the fashions in Manuel's Nashville, Tennessee, shop. It goes over how he makes the piping and then how it's added to the pockets. Make sure to click the RealPlayer or Quicktime link to start the video. Add piping to pockets.