Each year, Apple seems to design its devices to be more difficult for owners to repair themselves. So when an iPhone breaks, a trip to the Genius Bar or an Apple Authorized Service Provider is most likely necessary. But if you have an iPhone X that needs a new battery, a leaked video just spilled the beans on how to replace the battery precisely as Apple would.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Over the past week, we've had a number of important launches take place in the Android community. Samsung is in the middle of their rollout of the Galaxy S9, with preorders in the US shipping this week. Google also rolled out the first Android P developer preview last week. While these may seem unrelated, there are actually a number of Android P features inspired by Samsung software.

Samsung hopes to make a splash with the new Galaxy Note 9 to make up for the underwhelming sales of its signature Galaxy S9 series. This flagship is a radical departure from its predecessors — it's now optimized for gaming and paired with the most advanced S Pen stylus to date. Here's everything you need to know.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

The Guardians of the Galaxy have to be the most fun superhero team to have at a Halloween party. They dance, they break the rules, and they definitely have the grooviest music. So the Guardians are a great bunch to pick from for your Halloween costume — or even for a themed group costume. Just imagine the badass vibe when you all walk into a venue together with Star-Lord blasting "Cherry Bomb" from a portable speaker. Here's a roundup of some of the best Guardians of the Galaxy costume guides...

It's not always easy to get to the root of an infection outbreak. Epidemiologists study infected people, contacts, and carefully examine where the infections happened and when. In the case of a 2012 outbreak of pertussis — whooping cough — in Oregon, scientists just published an analysis of how vaccination status affected when a child became infected during the outbreak.

The Samsung Galaxy Note 8 (or Galaxy Note8, depending on how you like it) is one phone which couldn't possibly have bigger shoes to fill. Samsung's latest flagship has officially been announced, so it's time to decide whether not it's capable of filing the void left by the failed Note 7. From the revealed specifications and details, the Note 8 is turning out to be one device worth pre-ordering.

If you want to appreciate the value of microbes, look no further than a chunk of cheese. Because cheese roughly traces back to the Neolithic Era, we might say the earliest cheesemakers were the first humans to manipulate microbes—without even knowing it. Now, thanks to microbiologists and the long tradition of cheesemaking, we know a lot more about the microbes that make our favorite types of cheese possible.

It seems like everyone is getting in shape these days (or at least trying to improve their fitness), and as a result, there's an endless supply of fitness trackers and smartwatches hitting the market. This is all very wonderful, unless of course, you're broke and can barely afford a decent pair of running shoes.

The world of augmented reality has seen a myriad of different products, from sensor-laden smartphones to robust holographic headsets, but Google Glass's failures nearly killed the middle ground.

These days, there are Android apps for every budget—forgive me if that sounds like a car commercial, but that's just the way things are in the age of the smartphone and tablet. You've got apps that require monthly subscriptions, paid apps that will run you a $30 one-time installation fee, and even games that start at 99 cents, but quickly skyrocket in price with in-app purchases.

Welcome back, everyone! In this lesson, I'm going to go over the use of the echo function and variables, as well as basic syntax.

We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of Samsung Galaxy S7 Punch-Out!! and see what happens.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

The bumper for bObsweep Pethair and Standard are installed the same way. It holds the sensors that allow Bob to see any obstacles in his path. If a repair of the wall detection sensors is needed, the steps for replacing the whole bumper are the same when working on either bObsweep model.

Whenever you buy a newer iPhone model, you get a set of Apple EarPods with remote and microphone built-in. Aside from their comfortable design and high-quality sound they provide, these headphones offer additional functionality beyond just pausing and playing music.

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

So, you've finally scored the coveted upgrade to chocolaty KitKat deliciousness, or you've managed to get your hands on a Nexus 5, the freshest thing from LG and El Goog. Satisfied with your new lease on life, you direct your phone's web browser to catch up on your Amazon Instant Video library, but not all is well—there are errors to be found. Much of the internet utilizes Adobe Flash, and Amazon Instant Video (who does not have an Android app) is just one such example. It simply won't work u...

Over time, the dryer belt can become hard and brittle when the drum is turning loud noises such as squeaking, squealing or thumping noises can occur. Replacing the belt is an easy task for the do-it-yourselfer. All that’s required is a few simple tools. Here’s a step-by-step guide to help you install a new belt in your dryer.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

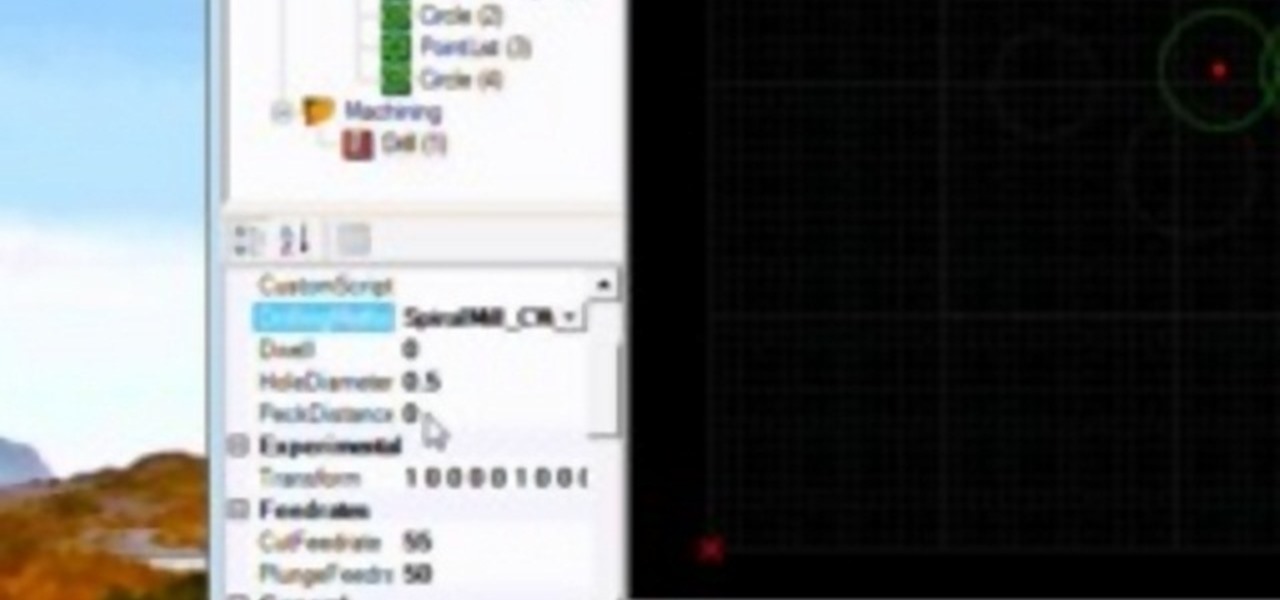
A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

In older Android versions, you could flood your status bar with a wall of notification icons. But starting with Android 9, Google made it to where you can only see four icons by default, and it was mostly done to accommodate phones with notches. But Google's only notched phone is the Pixel 3 XL, so what if you have literally any other Pixel?

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

After launching its first augmented reality title for Angry Birds on the Magic Leap One, Rovio has doubled back to the platform that made its franchise famous.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

Augmented reality content makers often position the technology as a new storytelling medium. And who loves stories more than children?

Magic Leap has already entered the realm of entertainment and enterprise, but on now it has blazed its way into a new augmented reality frontier: fashion.

After building its business on virtual reality, Jaunt is leaving the technology behind to focus on building tools for creating augmented reality content.

Do price tags on mobile games give you pause? We get it. With so many freemium games out there, it's tough to justify spending three or four dollars on a game for your iPhone or Android device. That's why you wait for moments like this one, as both "Reigns" and "Reigns: Her Majesty" are aggressively on sale.

Less than three weeks after Rovio Entertainment announced the game, the augmented reality adaptation of Angry Birds is now available for the Magic Leap One.

A Series B round of funding, totaling $30 million, will enable Helsinki-based startup Varjo to launch its industrial-grade augmented and virtual reality headset capable of "human-eye resolution" before the end of the year.

The iPhone X ushered in the Swiss Army Knife-like Side button, which can perform numerous functions, such as summoning Siri and opening Apple Pay through click gestures. This has carried over into the iPhone XS, XS Max, and iPhone XR, so if you've upgraded to one of these devices from a Home button-equipped iPhone, you'll have to learn how to shut down your new device.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

Location-based gaming pioneer Niantic has offered a preview of its augmented reality cloud platform that could change the immersive content game yet again.