While music may not technically be a "universe language," it is the one language listened to by all. There are over 1,500 music genres today—rap, classical, rock, jazz, trap, hip-hop, house, new wave, vaperwave, charred death, nintendocore... and the list goes on. And if you're like most people, you now probably listen to the majority of your music on your phone.

Apple's official feature list for the Music app on iOS 18 and iPadOS 18 may highlight only one update, but there's much more happening under the surface than that. Whether you subscribe to Apple Music, the latest version brings hidden gems that enhance your up-next queue, playlists, and overall experience.

Not all websites need a dedicated mobile app, which is why so many don't. Web apps are now designed to scale to different screen sizes, so mobile sites in your web browser are easy to navigate and utilize. Still, there's just something about an app on your iPhone's Home Screen that makes it feel more like an app from the App Store.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

If you're in the market for a new smartphone and want nothing but the best of the best, now's the time to act. Some of the greatest phones money can buy are being released as we speak, while others are still in their prime and will continue to be for most of 2024. Whether you want an iPhone or Android, we've rounded up the best picks you have to choose from for top-of-the-line specs and advanced features.

The volume buttons on the side of your iPhone can do more than just adjust the volume levels for media, ringers, alerts, Siri, and other sounds and voices. You can use them to perform different actions in certain apps and even create custom actions using the Shortcuts app. It's not exactly button mapping, but it's as close as you'll get without jailbreaking iOS.

Apple's iPhone lineup has always been at the forefront of technological innovation, captivating the world with each new iteration. As we eagerly anticipate the iPhone 15 series release, rumors, leaks, and speculations about the highly anticipated 2023 models are at full steam.

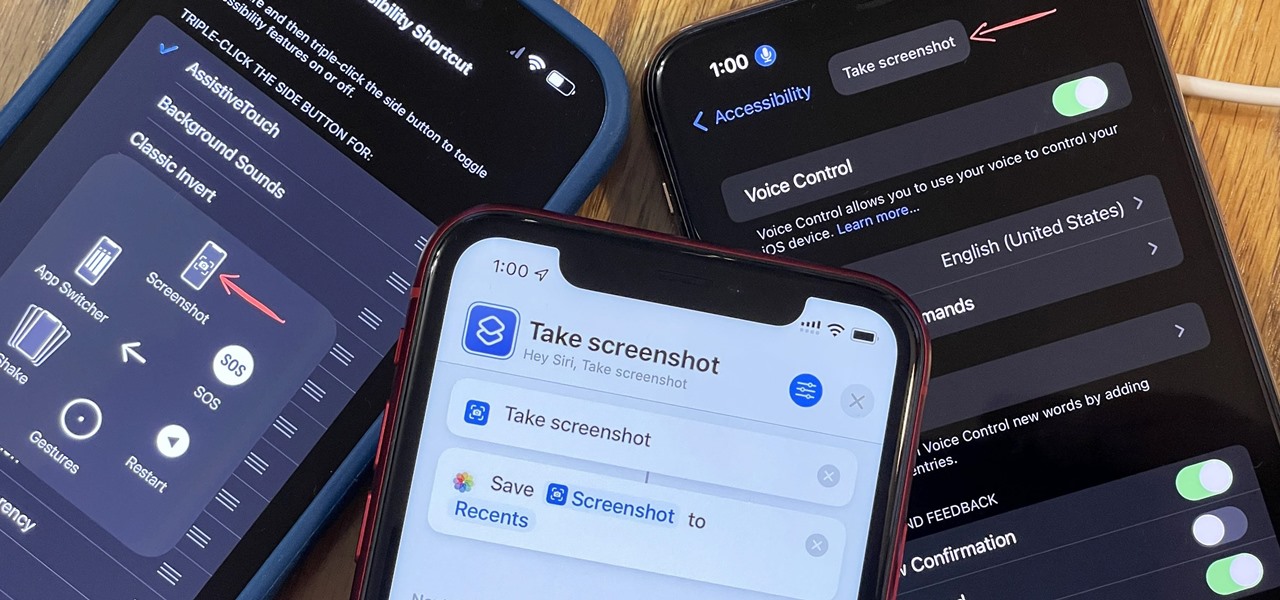
You may know the traditional way to take a screenshot on your iPhone, but it may not be the best action for your needs. There are faster ways to capture an image of your iPhone's screen, methods for capturing overlays and other elements that won't show in regular screenshots, and even options for blocking screenshot thumbnail previews from appearing.

Apple's Notes app has an important feature many users overlook, yet it's arguably the most crucial thing you should use for all your notes synced across iOS, iPadOS, macOS, and iCloud.com. And Apple makes the feature much easier to use than years before, so there's no reason you shouldn't be using it.

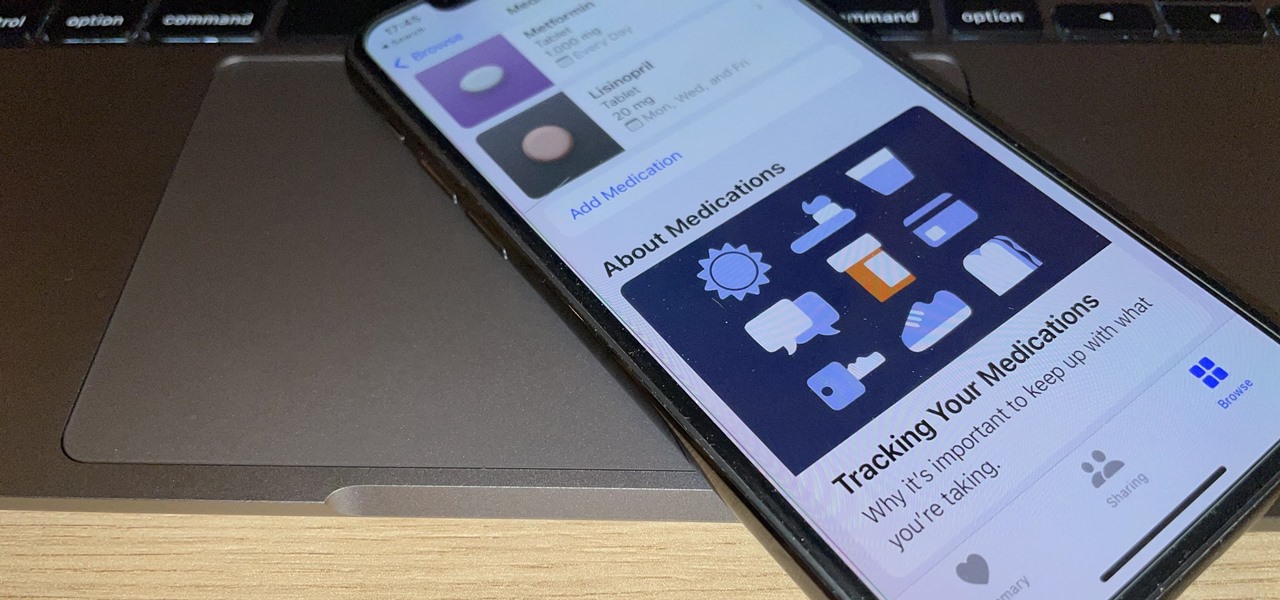
You've probably already been using iOS 16 on your iPhone for months, but there's a good chance you haven't found or explored everything the new software has to offer. Health-related features are usually the first to be ignored or go unnoticed, but they're essential to know about even if you don't plan on using them right away.

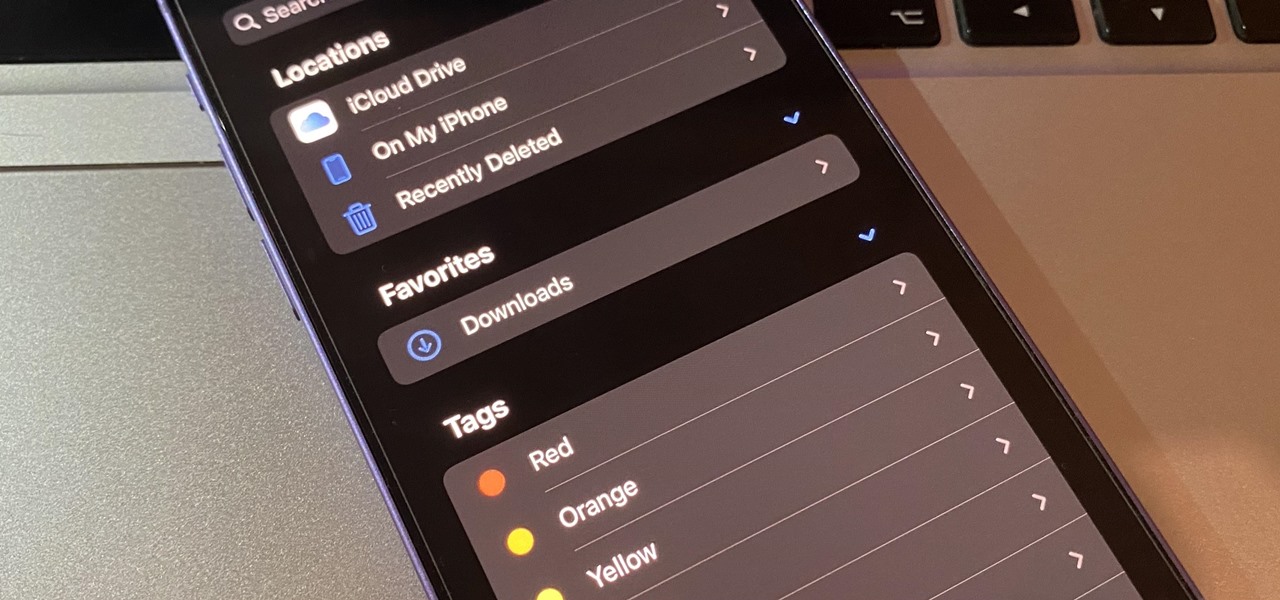
If you're not using your iPhone's Files app yet to manage images, documents, and other files on iCloud, third-party cloud services, or your local storage, it's time to start. Apple's built-in file manager is finally a powerhouse with many tricks up its sleeve in the latest software update.

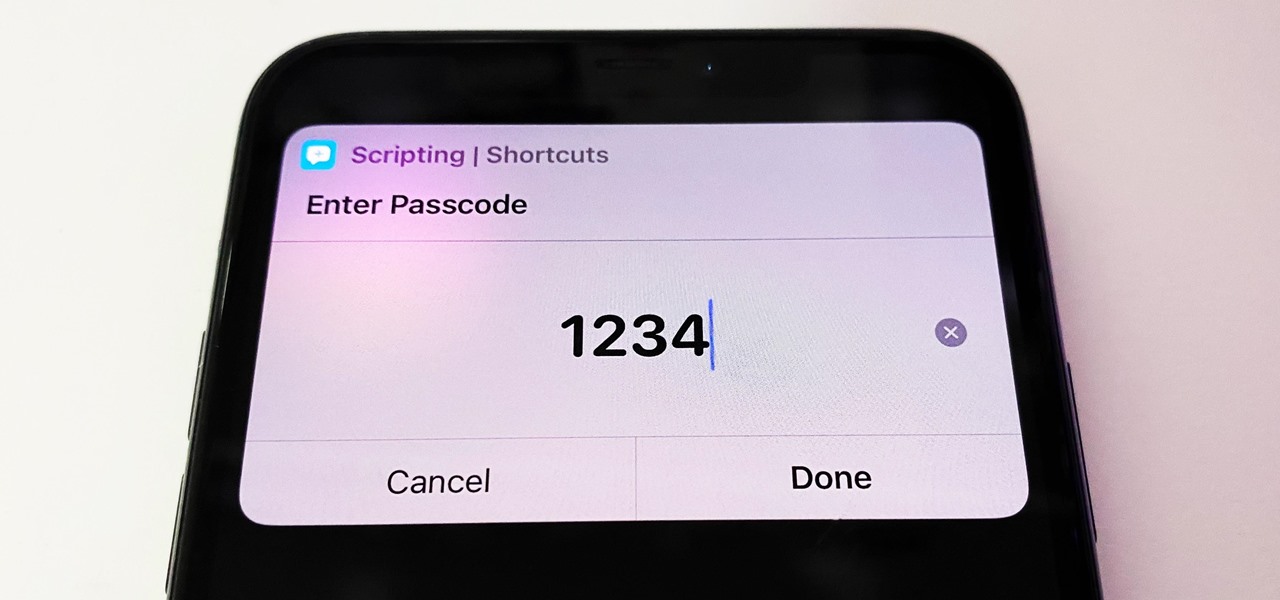
Some iOS and iPadOS apps give you an option to lock them behind Face ID, Touch ID, or a passcode, but there aren't many.

Your iPhone's built-in Voice Memos app is a great way to record the audio around you, whether it be conversations, lectures, meetings, interviews, discussions, chitchat, gossip, or other kinds of talks. But if your goal is to record audio on the down-low without being noticed, you'll need to know the hidden shortcut.

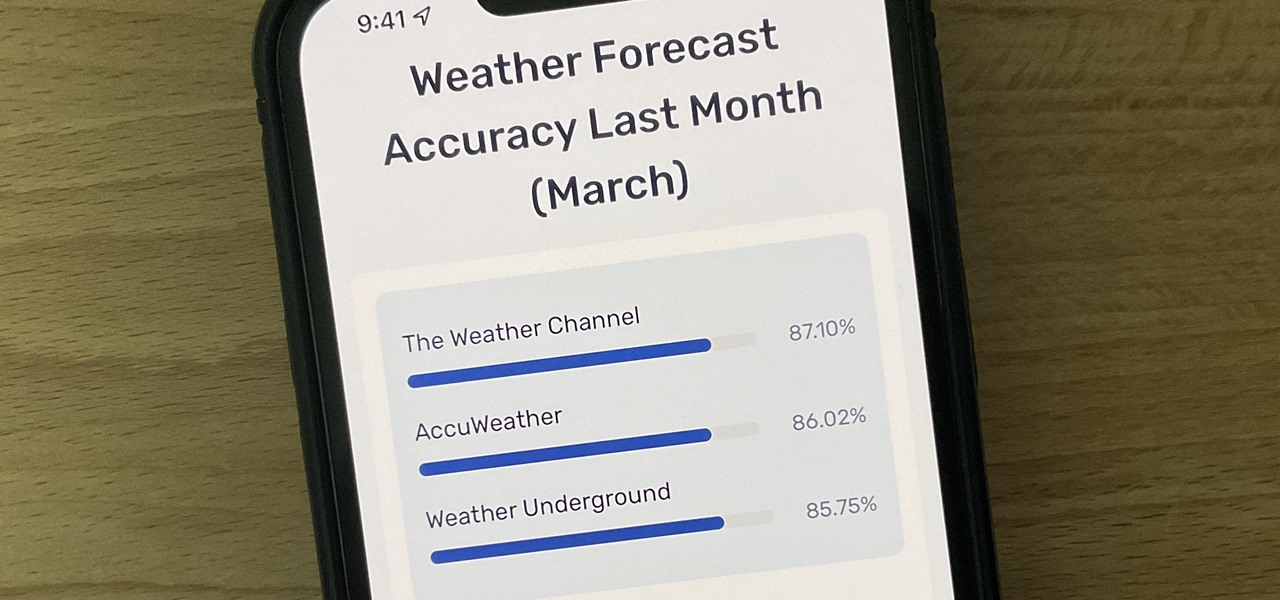
Not all weather sources are equal. When you're looking at the forecast, you hope that it's at least semi-accurate so you can plan the week and days ahead, but many sources are unreliable. And with the famous Dark Sky API shutting down on March 31, 2023, you'll need an alternative source of weather information if you use an app that utilizes that API.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

There are tons of tools out there that do all kinds of recon, but it can be hard to narrow down what to use. A great way to be more efficient is by taking advantage of scripting. This doesn't have to mean writing everything from scratch — it can simply mean integrating existing tools into a single, comprehensive script. Luckily, it's easy to create your own subdomain enumeration script for better recon.

As a hacker, the final stage of exploitation is covering their tracks, which involves wiping all activity and logs so that they can avoid being detected. It's especially crucial for persistence if the target will be accessed again in the future by the attacker.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

Finding an instrumental or karaoke version of a song can be pretty easy unless you're dealing with a song that isn't popular. That leaves you with just the full version of the song, complete with vocals. So how do you convert it into an instrumental or karaoke track?

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI that shows you the signal strength of nearby devices.

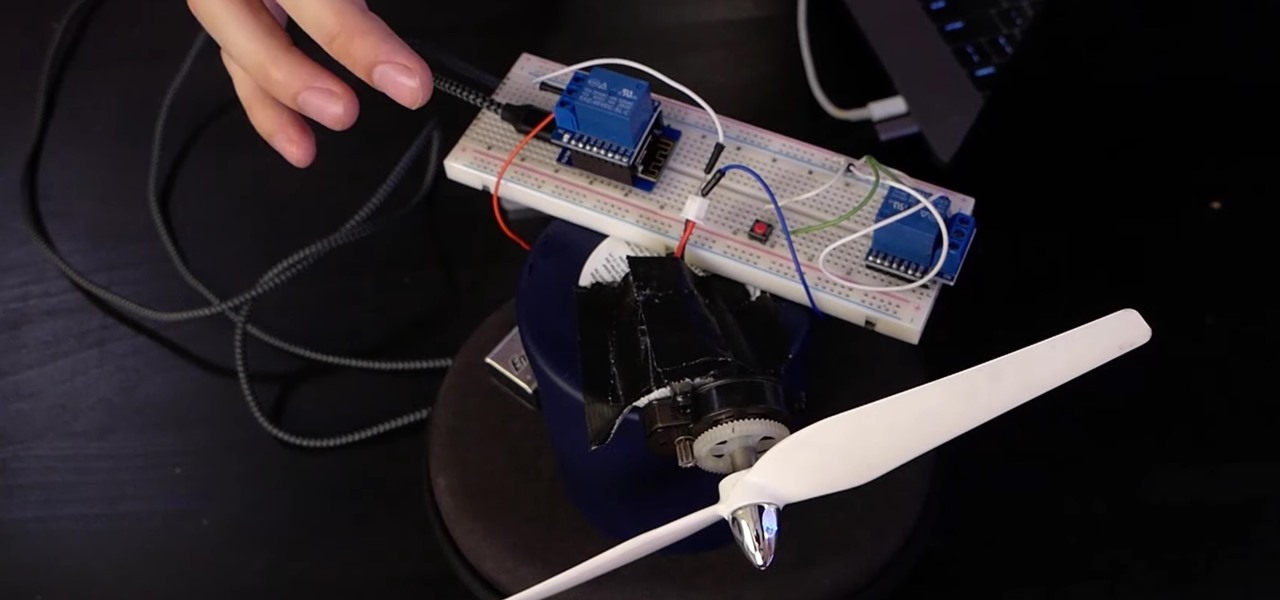
If you want to control electronic devices, such as a relay or motor, you can do so using MicroPython with an ESP8266 and web browser. Usually, you'd program an ESP8266 using Arduino, but C++, which Arduino uses, is not always the easiest programming language for beginners to learn.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra help. That's where these video recording apps come into play, to ensure the footage you capture is as good as can be.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

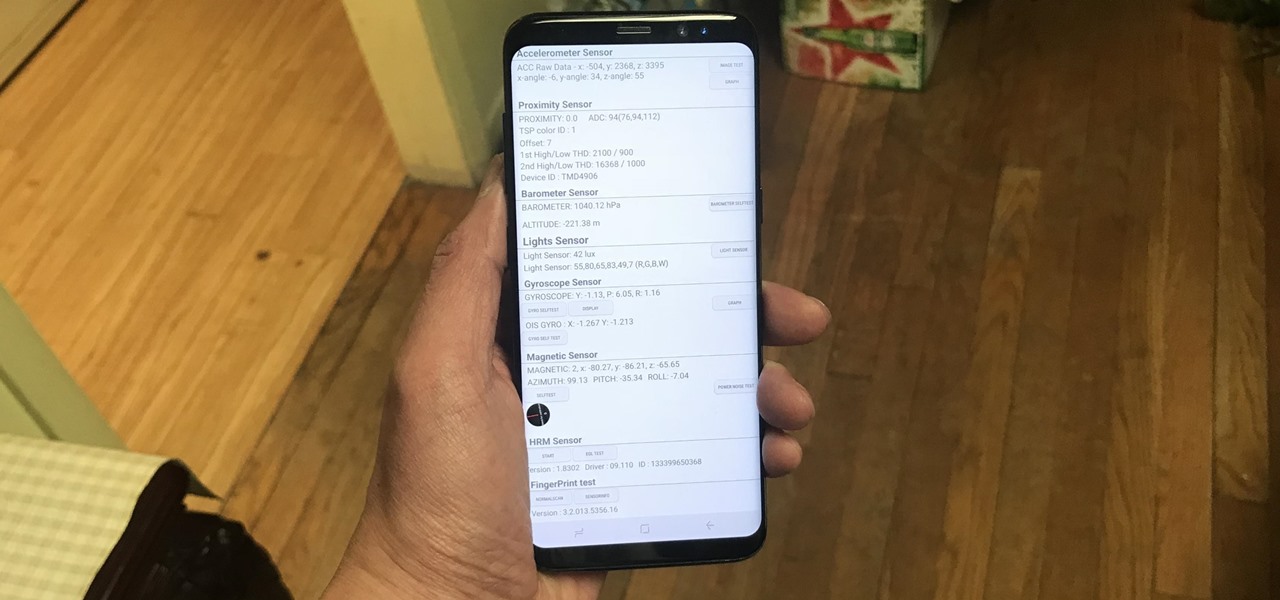
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

Your days as an ordinary Muggle are over — as long as you have an iPhone. With just a word or two, you can use your iPhone and newfound Muggle-born powers to cast spells or utilize charms just like Harry Potter and team. Only your "wand" is from Apple, not Ollivanders in Diagon Alley.

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

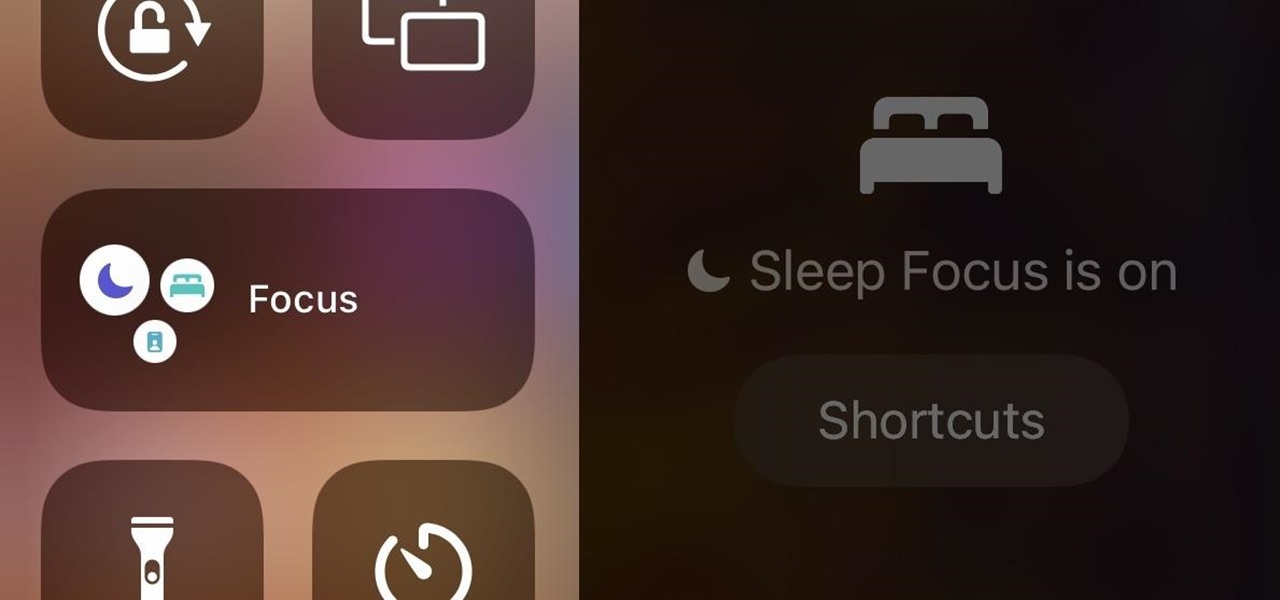
In iOS 15, Apple unveiled a new feature called Focus, an extension of Do Not Disturb that lets you focus on the one thing that's important at any particular moment. It does so by minimizing distractions from your iPhone and other Apple devices, but there's a lot you should know about setting up and using Focus on your iPhone or iPad before you dig in.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

This video exposes some good techniques for precise alignment in modo. The material is based on architectural content but the concepts can be used for many purposes. Learn how to use this precision modeling tip about alignment in modo. Content provided by Takashi Hibi-san. Align precisely when modeling in modo.