While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

One of my favorite things to do when I visit my parents is cook. Aside from the fact that I adore cooking with my mom, there's something comforting about returning to the kitchen that I first started playing in 20 years ago. Nearly all of the tools and appliances are the same ones that I used as a kid, and the familiarity is palpable.

It's a small but very real frustration: you want a chilled drink, but you open the freezer only to see nothing but empty ice trays. Fortunately, there's a simple way to make ice cubes quickly—use hot water. Yup, you read that correctly. Hot water freezes more rapidly than cold.

As the Chromecast becomes more and more popular (it's even available overseas now), the market has seen an avalanche of Chromecast-compatible apps. We can play games, cast TV stations, and even mirror our screens, but today I'm going to show you a multifaceted tool that'll do everything from broadcasting your camera to displaying your documents.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion.

The enterprise applications powering the adoption of the HoloLens 2 are only just ramping up as developers continue to work with the still relatively new hardware.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

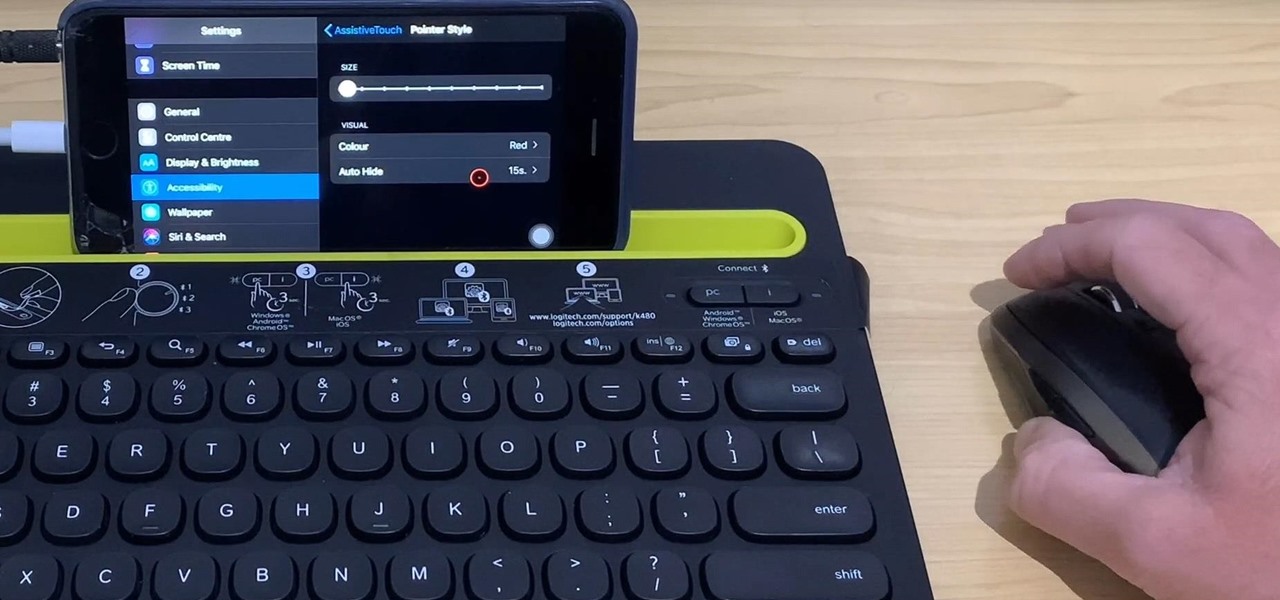
With stay-at-home orders for most of us in the US because of the new coronavirus, many of you are likely struggling to be productive and efficient when working from home. Unless you've worked from home before, it can be challenging to separate work from personal life throughout the "workday." But your iPhone can help make the transition easier and more successful.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Now that we have installed the toolkit, set up our prefabs, and prepared Unity for export to HoloLens, we can proceed with the fun stuff involved in building a dynamic user interface. In this section, we will build the system manager.

Whether your palate runs to domestic or imported, a piece of cheese can be a real treat for the senses. Its smell, taste, and texture are all parts of its appeal. A big part of what makes that savory wonderfulness comes from the microbes in and on the cheese. Thanks to a team of researchers dedicated to studying those microbes, we have a better understanding of their importance to cheese and us.

When it comes to global warming, most of us think of carbon dioxide emissions. While carbon dioxide is the most important greenhouse gas, carbon dioxide emissions have stayed constant for the last three years. On the other hand, methane, the second most important gas, has been steadily rising since 2007.

The new Samsung Galaxy S8 and Galaxy S8+ phones were announced on March 29 at the Samsung UNPACKED 2017 event. Preorders start on March 30 for the Korean tech giant's latest flagships, and sales officially begin in the US on April 21. Samsung will need a smooth release to win back consumer trust after the Note7 mess, and it's already looking like the S8 won't disappoint.

The world of augmented reality has seen a myriad of different products, from sensor-laden smartphones to robust holographic headsets, but Google Glass's failures nearly killed the middle ground.

Home cooks are often quite intimidated when trying to reproduce the delicious ethnic dishes they enjoy at various restaurants. Thankfully, there are definite flavor profiles and spice/seasoning/herb combos that are very specific to various regional cuisines and cultures; with a little guidance, you can create dishes that are tasty homages to the cuisines you love to eat. In this two-part article (second part here), I'll cover both categories and sub-categories of some of the most popular ethn...

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

What is old is new again. In this case, a classic arcade game gets the augmented reality treatment. In a new promotion playing off its ad campaign featuring actor Craig Robinson (The Office, Hot Tub Time Machine), Pizza Hut has turned its pizza boxes into a virtual Pac-Man game via web-based AR technology.

The new WandaVision series is perhaps the hottest TV show on the Disney Plus streaming service since...well, its own The Mandalorian wrapped up its second season late last year.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.