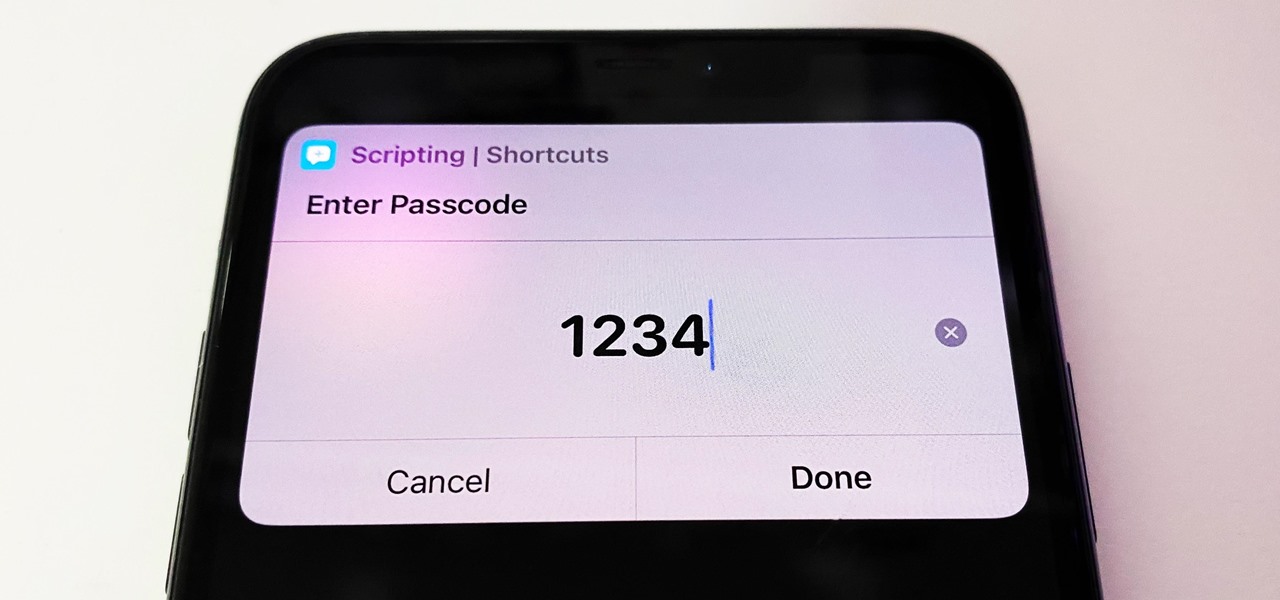
How To: Easily Lock Any App on Your iPhone or iPad Behind Passcode or Biometric Authentication
Some iOS and iPadOS apps give you an option to lock them behind Face ID, Touch ID, or a passcode, but there aren't many.


Some iOS and iPadOS apps give you an option to lock them behind Face ID, Touch ID, or a passcode, but there aren't many.
If you're like me, you don't have time to sit down and leisurely read an entire article from start to finish — but you still want to be informed throughout the day. Instead of just browsing the daily headlines, there's a free service that will summarize any article you throw at it, giving you a better idea of what's going on without committing to reading an entire article.
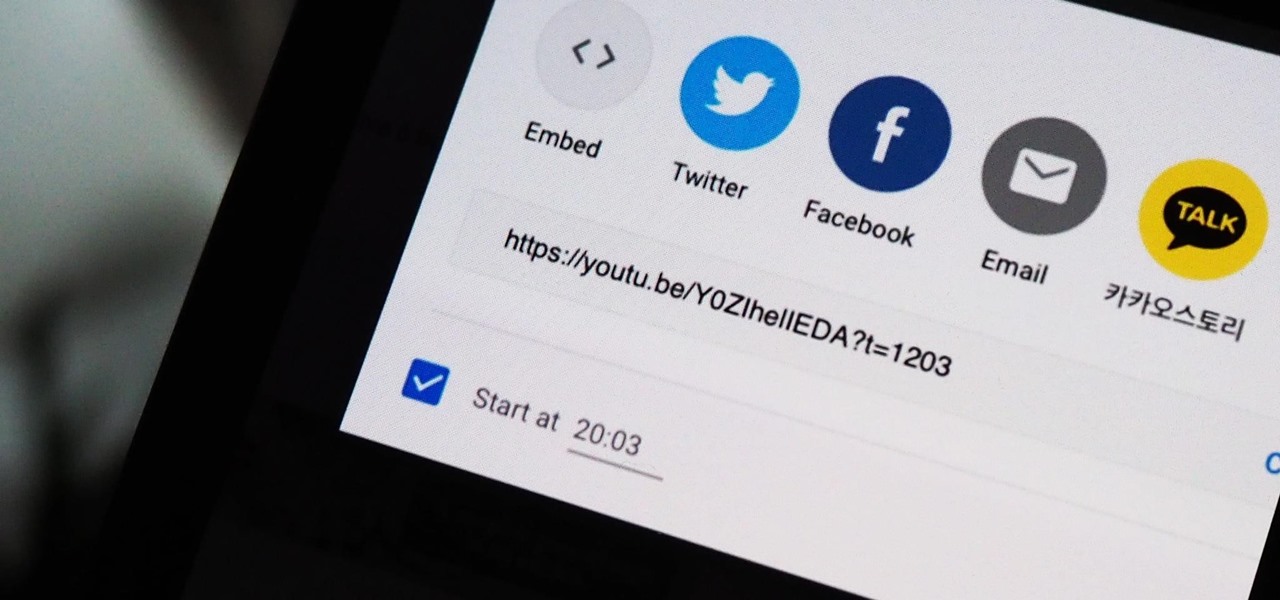
You can add a timestamp to any YouTube video in just a few clicks from the desktop website on your computer but not from YouTube's iOS or Android app. Until YouTube adds a "start time" when sharing videos from the mobile app, you'll have to use one of these workarounds on your phone or tablet.
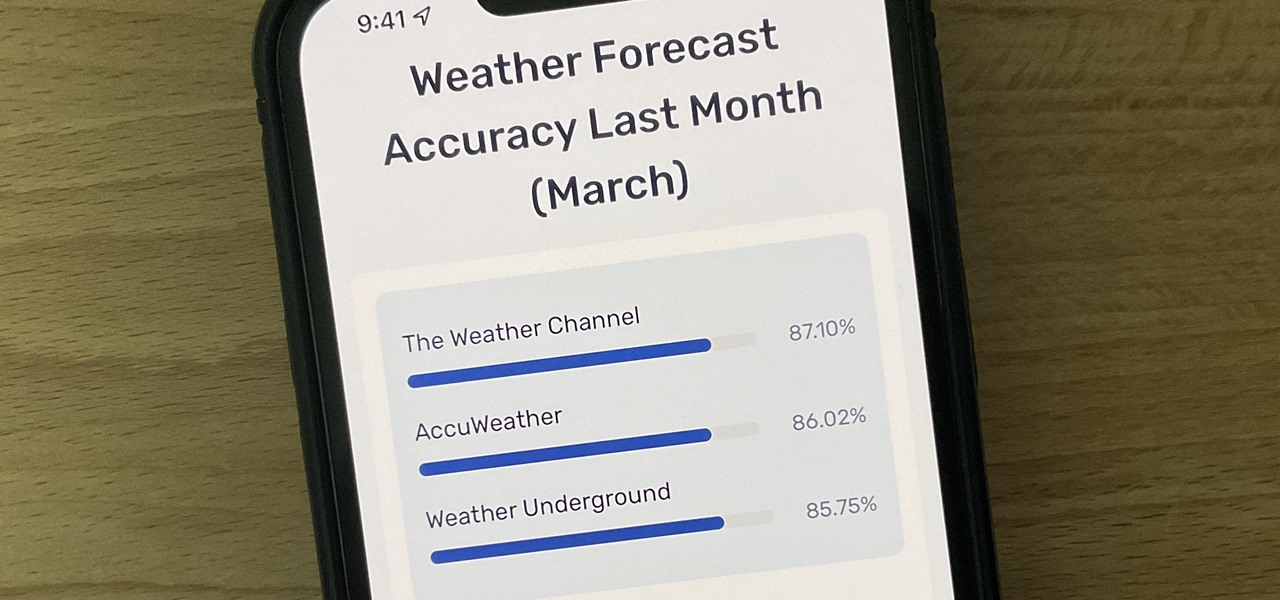
Not all weather sources are equal. When you're looking at the forecast, you hope that it's at least semi-accurate so you can plan the week and days ahead, but many sources are unreliable. And with the famous Dark Sky API shutting down on March 31, 2023, you'll need an alternative source of weather information if you use an app that utilizes that API.
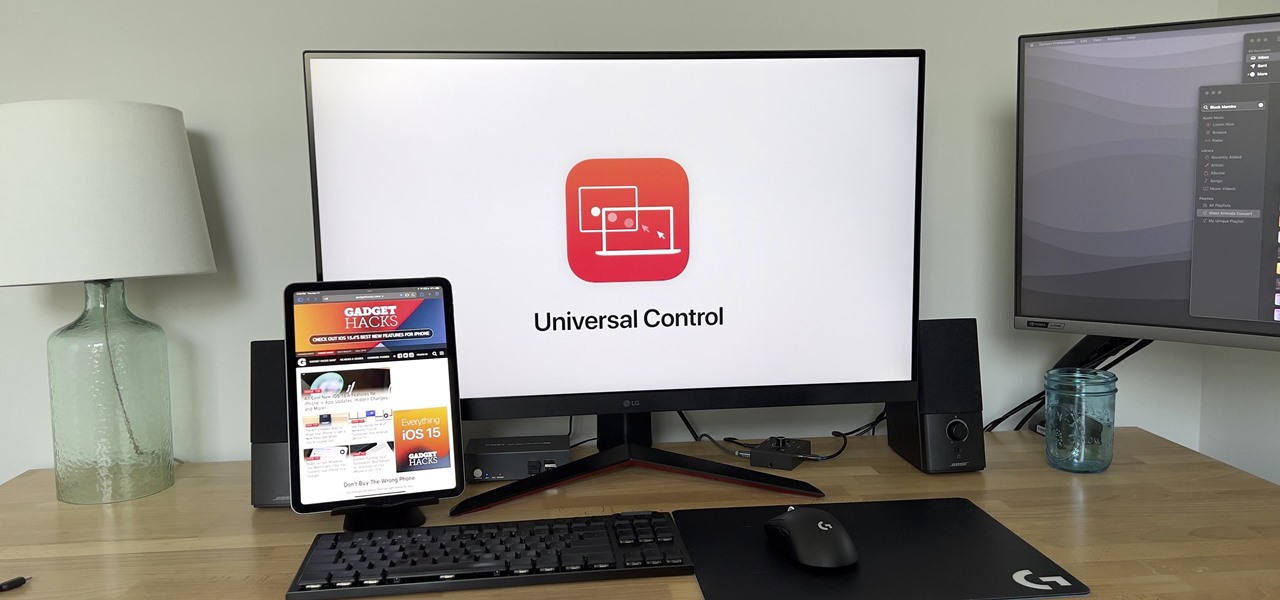
With the release of iOS 15.4, iPadOS 15.4, and macOS 12.3, Apple unleashed a ton of new features. We saw a preview of one of the most anticipated new features way back in June 2021 when it was announced at WWDC, and now it's finally available for everyone with an iPad and Mac.
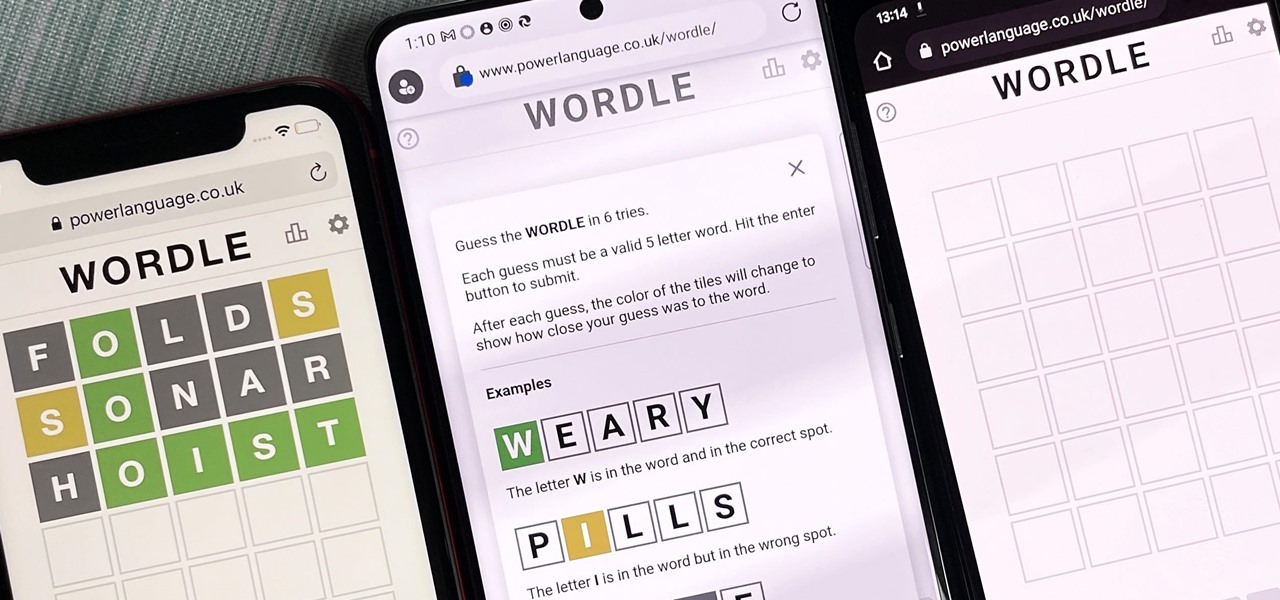
The hottest word game right now is Wordle, a simple game that gives you six chances to guess the five-letter word of the day. I've already shown how you can add the real Wordle app — not a fake clone — to your iPhone or Android phone's home screen. But there's also a way to save Wordle for offline gameplay for years to come.

Gaming on smartphones has grown considerably since the days of The Impossible Game and original Temple Run. Mobile games can be just as in-depth as console and PC video games, but some of those require external controllers for the best gameplay possible. One controller you can use is the PlayStation 5's DualSense wireless controller, and it pairs nicely with most Android devices.'

If you have a PlayStation 5 and an Android phone running Android 12, you can stream and play your PS5 games right from your mobile device using PS Remote Play. While simply pairing your PS5's DualSense wireless controller with your phone will give you the basic controls to play third-party games, Remote Play takes a little bit more work to set up.

On May 17, Apple announced that Lossless Audio playback for Apple Music was finally coming to subscribers in June. The long-awaited option will let users stream songs at a much higher quality than ever before. Still, in the fine print, Apple noted that you wouldn't be able to listen to the best sound quality — Hi-Resolution Lossless — on your iPhone without a DAC.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

There are tons of tools out there that do all kinds of recon, but it can be hard to narrow down what to use. A great way to be more efficient is by taking advantage of scripting. This doesn't have to mean writing everything from scratch — it can simply mean integrating existing tools into a single, comprehensive script. Luckily, it's easy to create your own subdomain enumeration script for better recon.

The Metaverse, or AR cloud, has been a sci-fi dream for decades, but only recently have companies begun to actually develop the technology to build it. With its latest funding round, Epic Games is suddenly a front-runner in this pursuit.
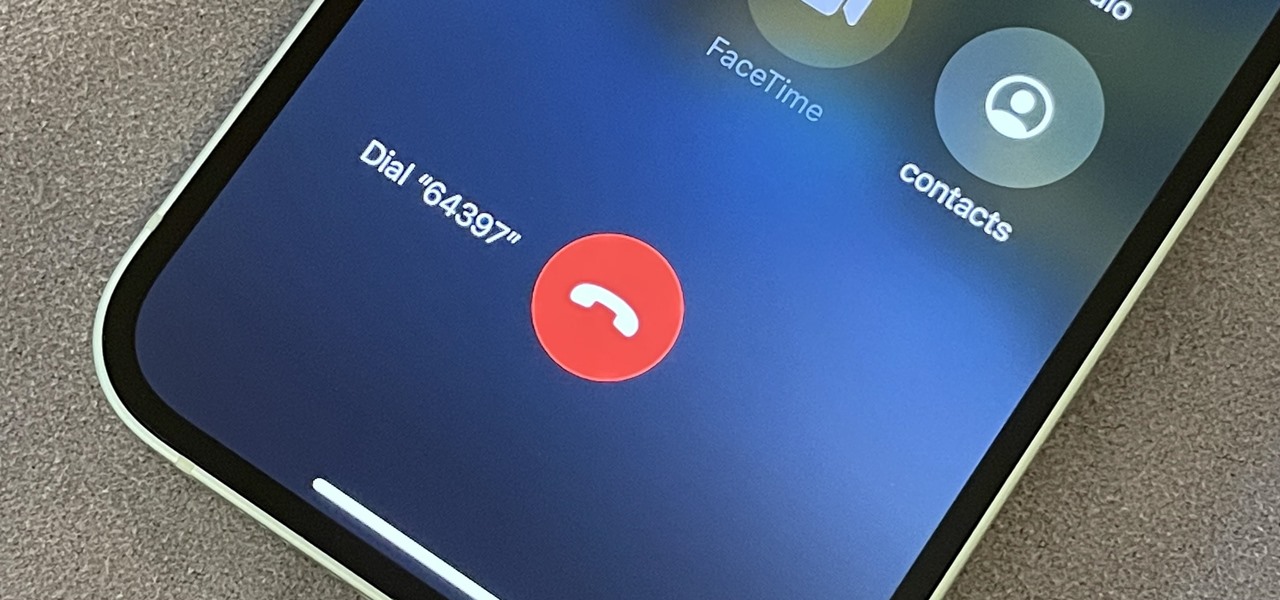
Automatic phone menus are the worst. You call the number, listen to prerecorded prompts, press button, listen, press button, listen, press button, listen, until you're routed or connected to the right extension, directory, menu, person, or whatever. But you can bypass these automated attendants to get right to where you need to go by setting up a simple shortcut on your iPhone.

The race for the future of AR wearables gained steam this week with several pivotal developments. First, Apple, the subject of numerous reports and rumors regarding its purported AR headset, is reportedly eyeing an in-person unveiling of the device for later this year, rather than introduce it at its upcoming virtual Worldwide Developers Conference, which would usually be as good a time as any to make a big AR hardware announcement.
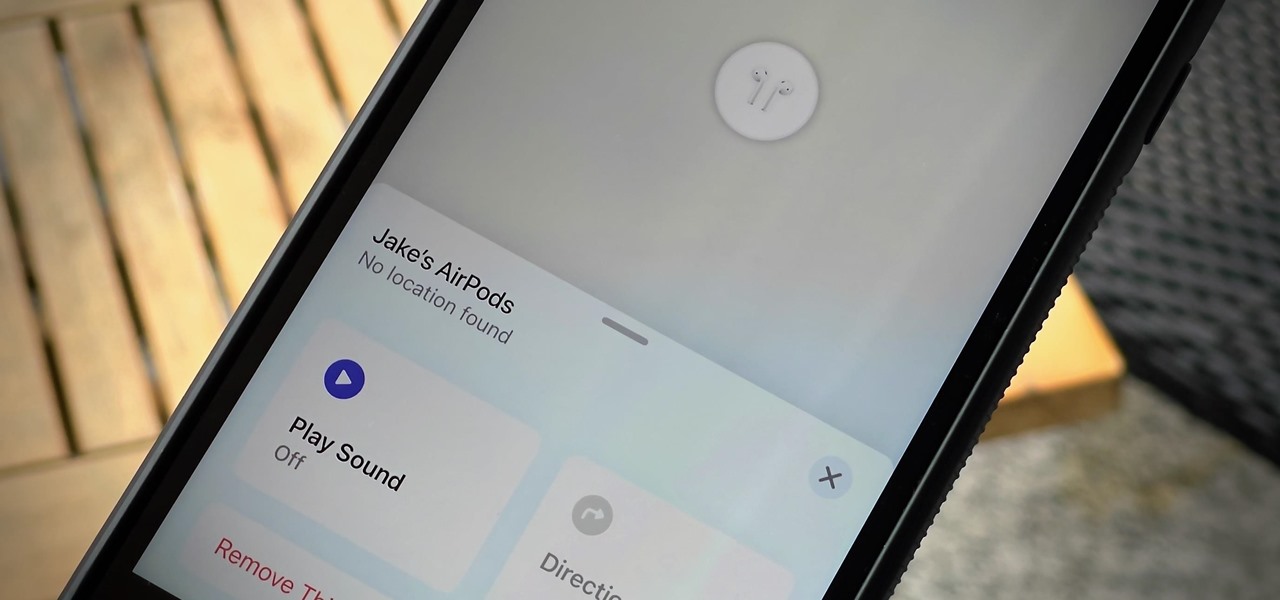
If you lose your AirPods, AirPods Pro, or AirPods Max, you can turn to Find My to locate them. But sometimes, things don't go according to plan, and many things can go wrong. For example:

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.
If your Safari browser is lagging when opening new tabs or windows on your Mac, there's an easy fix that will speed things back up to how they're supposed to be.

I always keep my iPhone's Portrait Orientation Lock on so that my screen doesn't randomly rotate while I'm lying down. However, there are certain apps that I do turn it off for. It's kind of a pain since you have to swipe down the Control Center and toggle the orientation lock — but that ends now. Instead of doing it manually, a new iOS update can automate app orientations for you.

The iPhone doesn't stop at last year's excellent iPhone 12 lineup. Apple's been developing its iPhone 13 models for a while now, and there are a lot of rumors already with eight or nine months still to go until a release. This year, we're expecting four new models with similar sizes and features to 2020's offerings. If you want to know what makes the 2021 iPhones so different, we've got answers.

Finding an instrumental or karaoke version of a song can be pretty easy unless you're dealing with a song that isn't popular. That leaves you with just the full version of the song, complete with vocals. So how do you convert it into an instrumental or karaoke track?

Three new wallpapers showed up in iOS 14.0, each with dark and light versions, while iOS 14.2 added eight more. Each iPhone also has live wallpapers catered specifically for it. However, none of Apple's wallpapers are dynamic. That means they won't change automatically based on certain conditions, such as what time of day it is. MacOS's do, though, and you can get those working on your iPhone.
If you upgrade to an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, you can take advantage of super-fast 5G speeds, but which 5G network are you actually getting and is it better than the others? Depending on your carrier, you may see 5G, 5G+, 5G UW, or 5G E in the status bar next to the signal strength, and there's a pretty big difference between them.

The sound your iPhone makes when you connect it to a power source has been the same for a long time. Unfortunately, it was never possible to change that chime to something different without jailbreaking first, which opens your iPhone up to malware and hackers. Thankfully, iOS 14 has changed that.

Apple has four iPhone models for the remaining months of 2020, but the most impressive ones are the iPhone 12 Pro and iPhone 12 Pro Max. While the iPhone 12 and iPhone 12 mini are great smartphones, the "Pro" models offer more advanced features, especially for photographers and augmented reality enthusiasts.

Not much about 2020 is what you'd call normal, but if one thing remains the same, it's that Apple will still release new iPhone models. This year, the company is offering four new options: two "Pro" models and two "consumer" devices. If you want to know more about the latter two, the iPhone 12 and iPhone 12 mini, keep reading.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.
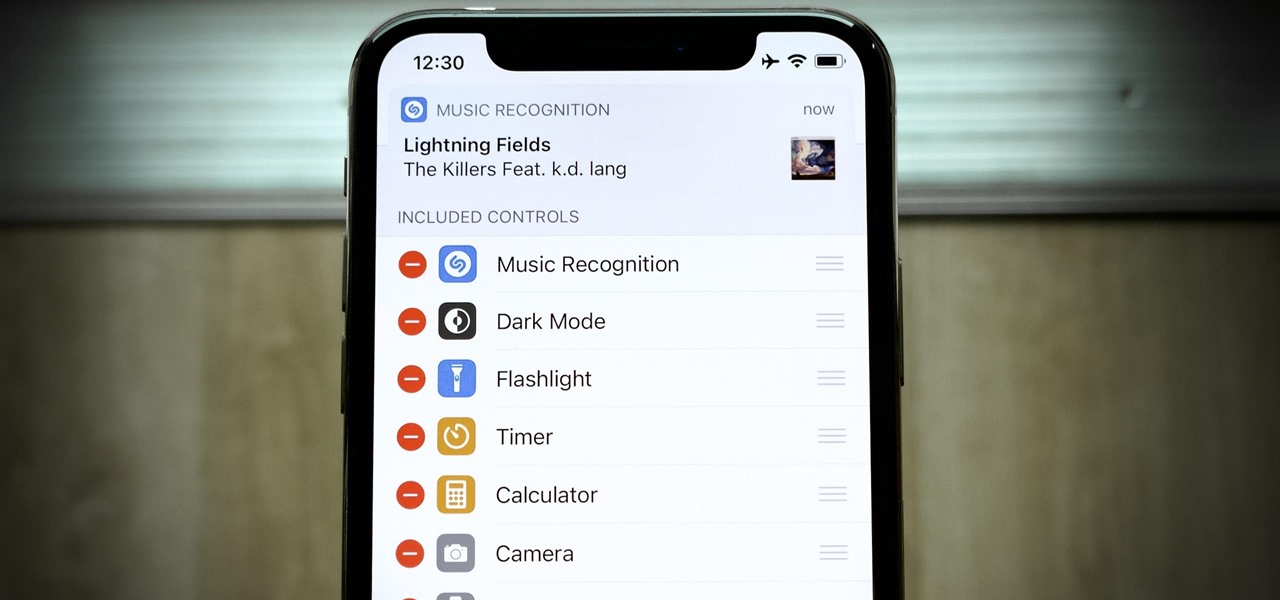
Apple just released the first beta for iOS 14.2 to iPhone software testers today, Monday, Sept. 21. This update brings a new Control Center tile for Shazam music recognition, a redesigned Now Playing Control Center tile, and a new "People Detection" feature in Magnifier.
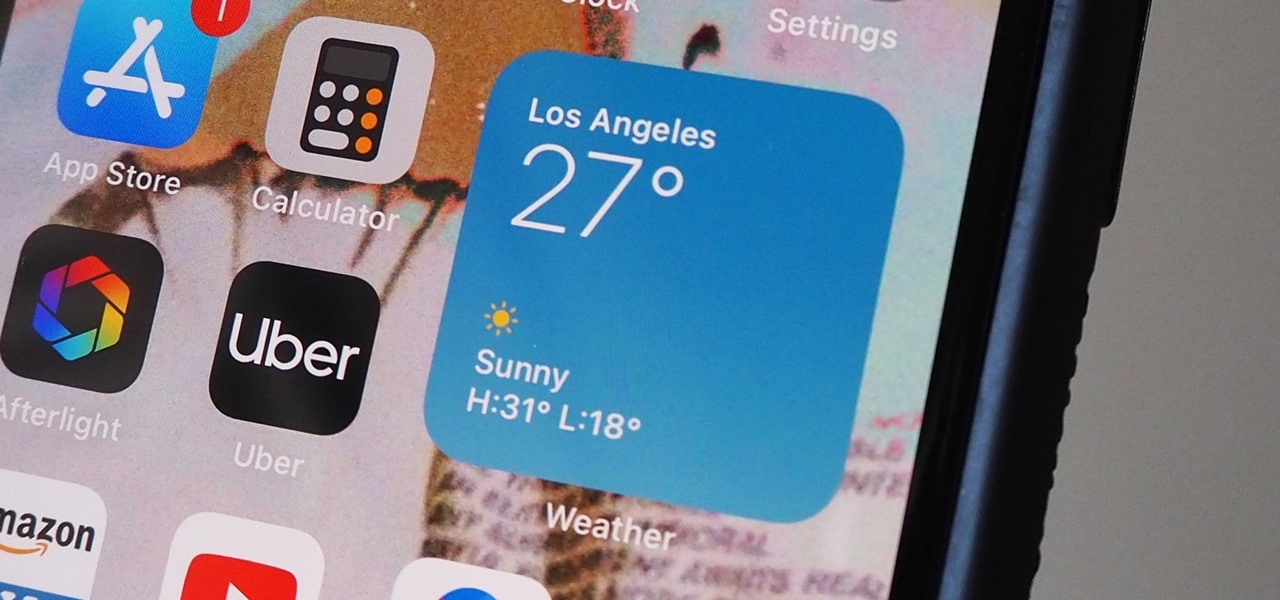
Widgets have been available on the iPhone for a while now, but they were tucked away in the Today View or hidden in the quick actions menu for app icons on the home screen. Android had always had a leg up on Apple in the widget department because they were so much more versatile, but that changed with the introduction of iOS 14.
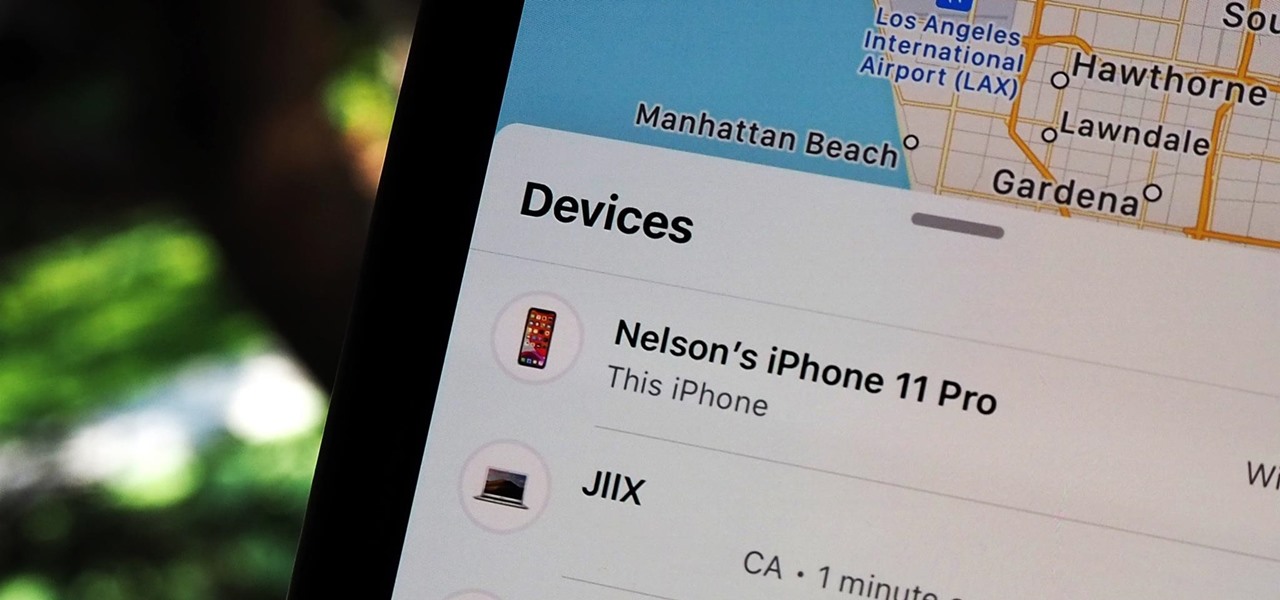
You might be giving out your name to every stranger you see, and you don't even know it. That iPhone of yours has a name — generally a combination of your first name and device model — and it broadcasts it to others via AirDrop, Personal Hotspot, Bluetooth, Wi-Fi, and other connections. Sure, it's useful to keep your device name simple and to the point, but there are upsides to changing it.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI that shows you the signal strength of nearby devices.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.
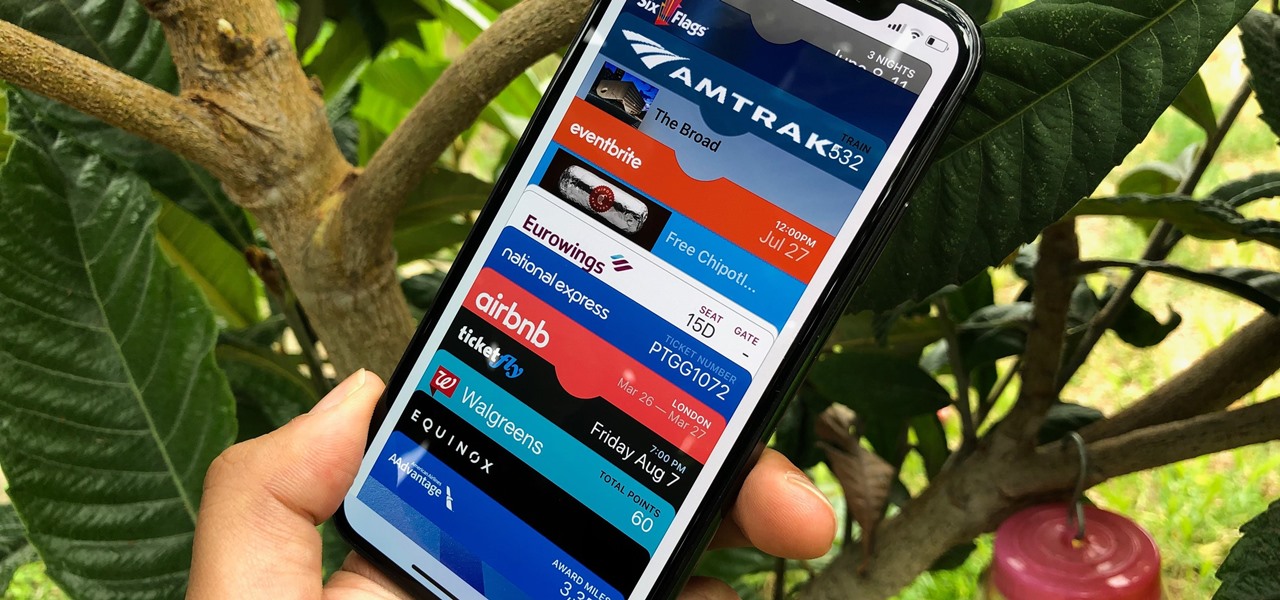
The Wallet app on your iPhone can be used to store and access event tickets, loyalty cards, boarding passes, gym memberships, airline miles, gift cards, coupons, and more — all in one centralized place. Before doing so, though, you must add your passes to Wallet, and there is more than one way to do it. However, not every pass can be added using all of the available methods.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Facebook Messenger is a messaging app first, but of its more than 1.3 billion monthly users, 32 percent use its video chat feature at least once every month. While it may seem pretty straightforward to video call with family and friends on Messenger, there are many tips and tricks that can help enhance your experience.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

5G is here. Well, not everywhere. All three wireless carriers have turned on their 5G networks, but only in select markets. Like 4G, each carrier is doing things a bit differently, which means your 5G experience will not be the same across the board.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.