The Google Now Launcher that was introduced with the Nexus 5 seems to have a lot of folks torn. On the one hand, having a home screen page dedicated to Google Now, as well as the always-listening voice search, are killer features. On the other hand, its lack of customization options like home screen gestures and variable grid sizes has some people considering switching to third-party launchers.

You can read at 500 words per minutes. Don't believe me? Here, see for yourself. This amazing technology comes from the startup Spritz, and they're ready to unleash it onto the smart device world, starting with the Samsung Galaxy S5 and the Galaxy Gear line of smartwatches.

Last week, we covered a new, open-source live wallpaper (LWP) called Muzei, and less than a week later we have no less than twenty beautiful add-on extensions to the app.

Of the hundreds of uses for our devices, the one that I cherish most is the ability to kill time just about whenever and wherever I need to. Whether it's reading news, checking social media, or watching videos, we have a ton of ways to pass the time in that two-hour DMV line or dentist's waiting room.

The iPhone 12, 12 mini, 12 Pro, and 12 Pro Max's new Scene Detection mode automatically adjusts Camera's settings to best suit your subject. That means it won't use the same shooting options for a close-up shot of your friend as it would a wide-angle landscape picture. If you don't want Apple to choose how your scene should look, there's a way to stop it to regain some control.
Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

Now that Samsung upgraded DeX in the Galaxy Note 10 and Note 10+, more users will be looking to use their phone as an "anywhere PC." With a simple USB-C to HDMI cable or adapter, you can turn your Note 10 into a desktop, complete with full access to your apps.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

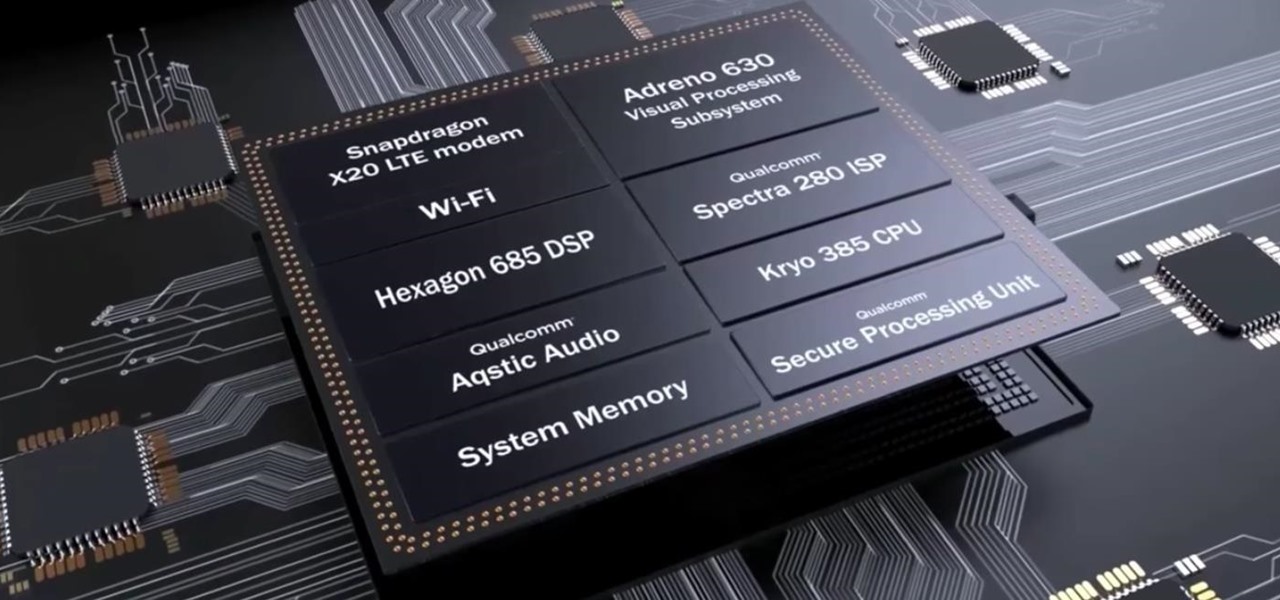
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

In 2017, major breakthroughs in smartphone-based simultaneous localization and mapping (SLAM) opened up new doorways for developers and users of both Apple and Android phones. Unfortunately for Android users, the solution that Google is previewing, ARCore, currently only works on three Android smartphones. But Silicon Valley start-up uSens is stepping in to fix that with its new engine called uSensAR.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

We live in a computer world full of file formats. Whether we are talking about images, videos, or text documents, there are dozens of file types for each, and there are new ones added every year to applications. Keeping in mind that many of these formats were created before the internet was widely available (at least, in infant form), the primary reason for this glut of often complex choices is competition.

If you've got big plans to lose weight and get healthier in 2017, know up front that it will be an ongoing challenge. It's not easy to break bad habits, and it's even harder to form new and better ones.

Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already has over 6 million views on YouTube, covered the journey made by a stolen smartphone and how the theft and ensuing tracking affected all parties involved.

Pumpkin pie is a symbol of autumn, and it's the traditional dessert to whip up for your fam when Thanksgiving Day arrives. But year after year of the same old thing can be a total bore if you're not a strict traditionalist. So, we found 8 unique ways to make that pie a little less snooze-fest and a little more interesting.

Augmented, mixed, and virtual reality are all a little bit different, but as many expect—including Metavision—the continuum of our next realities will converge and give us one head-mounted display (HMD) platform that can do it all. If Vrvana, a Canadian company building AR and VR headsets, succeeds, that convergence could begin as early as next year.

A cup of ginger tea with lemon first thing in the morning, a pick-me-up cup of green tea (or matcha) to fight off the afternoon slump and a soothing cup of chamomile tea to help me unwind before bed—I would be lying if I said I weren't a major tea enthusiast.

Back in the days when June Cleaver was our role model, stay-at-home moms eagerly greeted their offspring's arrival home from school with fresh-baked cookies. But in the current vernacular, "Ain't nobody got time fo' dat!"

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

One of my favorite things about American Chinese food is how easy it is to eat: the pieces are bite-sized, the flavors are addictive, and the meat is always tender and easy to chew. But if you've ever tried to replicate any of your favorite takeout in the kitchen, you've likely noticed that the high heat required for most recipes thoroughly dries out the meat that you're trying to cook.

The awesome thing about Android is that you rarely need to settle for what comes stock on your device. If your music app sucks, switch it. If you don't like your home launcher, swap it for a better one.

Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs.

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

Modern medicine utilizes cutting-edge technology more than ever, so it would only make sense that the powerful handheld computers we all carry around these days could play a big role in wellness.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

After years of making do with a cheap knife, I finally bought a really good 8" chef's knife—a Henckels, although I was also eyeing a Global santoku. It quietly but literally changed my life.

We Nexus users are fairly spoiled. There's a ton of third-party development for our phones, which translates to a virtually endless stream of custom ROMs being made available to us.

Nokia's recent foray into the world of Android brought a plethora of goodies along with it. The Finnish smartphone manufacturer offers a slightly different take on our favorite mobile operating system, with customizations ranging from ringtones to its very own app store.