
How To: Do stability ball skiers
Learn how to do stability ball skiers. Presented by Real Jock Gay Fitness Health & Life. Benefits


Learn how to do stability ball skiers. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do landmines with a barbell. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do side-to-side steps over flat bench and sculpt your body without weights. Presented by Real Jock Gay Fitness Health & Life.

Traditionally, incorporating loops and grooves can translate into hours of hard work just to get the loop to fit your song's tempo and timing. Help is on the way from the Propellerhead's ReCycle which gives you full creative control over utilizing your looped material. Join electronic recording artist David Alexander as he shows you how ReCycle has revolutionized using sampled loops. In this episode, David shows us how to Chop Up A Complex Loop.
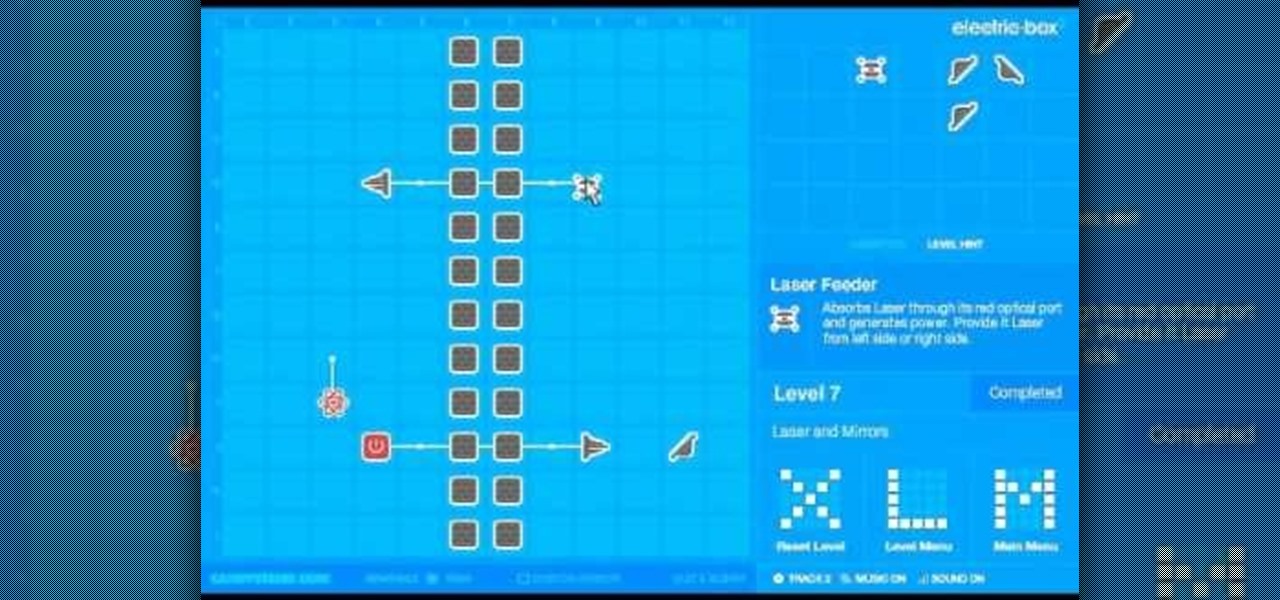
Box 2 is a fun and educational Flash game on Candystand that teaches people about the joys of renewable energy generation in increasingly complex puzzles. This series of videos will show you how to beat all 40 levels, including the alternate level 38 in it's own section.
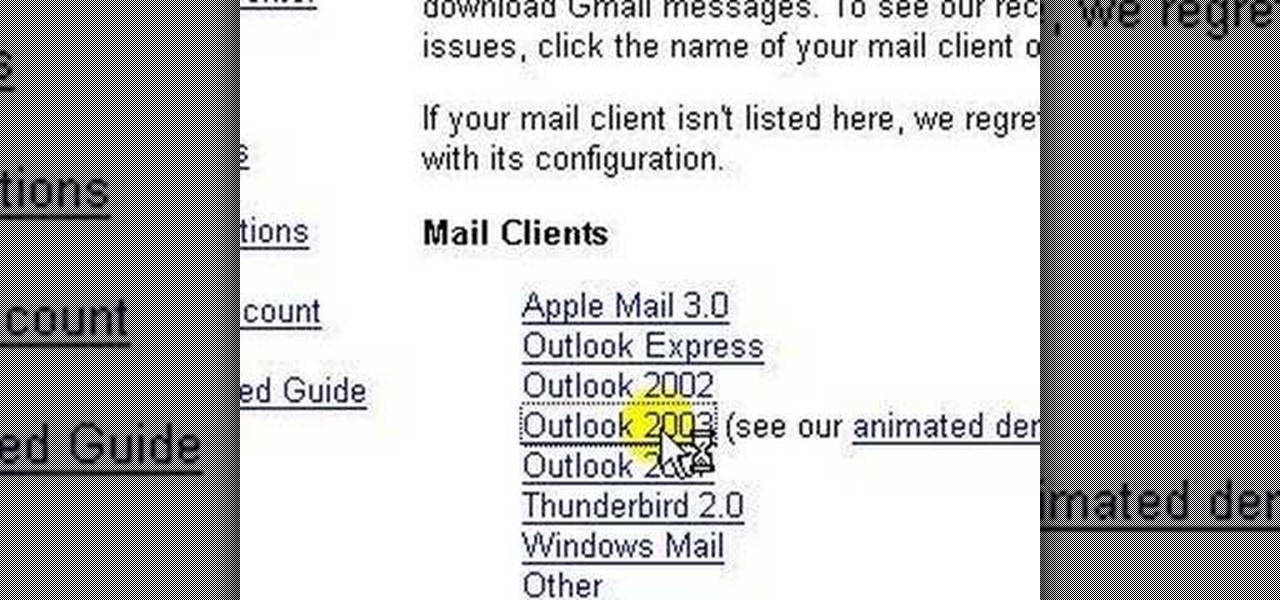
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

In this how to video, you will learn how to perform an advanced jig rhythm Bodhran. The way it is performed is going down down up. The down and up accent create an alternating back and forth feeling. If the accent is the same sound every beat, such as on the down, it has only a forward drive to it. First, do a down stroke but do not follow through. Drop the stick to hit a few inches below. From here, go up and hit the drum. The instant way to get this is to do the opposite. Basically, go up, ...

Rick Pitts takes us through how to do a push up using a coffee table. First, he starts by doing a push up for shoulders and triceps. You do this by placing your hands slightly wider than shoulders with fingers pointing forward. Keep your elbows near body as you lower yourself towards the table.

Our instructor will choose set 2, 6 and 8 to show you what the company offers. On the wrappers are pictures of the types of beads possible with each set. She will create from set 2 today, which makes oval beads. Inside of the packages, such as this package which holds set 2 are several items. First is the thin metal pins or rods that can go into the baking oven with the polymer clay molded around them. Next, two pieces for the mold, a bottom and top that fit together with grooves. There are a...

Knitting blogger Sapphires'n'Purls provides step-by-step basic instructions of the magic loop knitting technique. To begin Magic Loop knitting, you will need the following supplies: One circular needle with flexible cable, skein of yarn of your choosing. To begin, you will cast on 12 stitches onto the circular needle. Next you will slide all your stitches onto the flexible cable. Once all your initial 12 stitches have been cast, divide the stitches in half, putting six stitches on the left si...

Assemble the necessary equipment: a roll of 1- to 2-inch-wide athletic tape and a pair of scissors. Wrap one piece of athletic tape under the heel of the foot and bring both ends up the ankle to either side of the leg. The tape should form a "U," like the stirrup on a horse's saddle.

Take a paper: we need 60 rectangles (length-width ratio of 6:1) And fold in 4 equal parts.

• Start by warming and relaxing the lower back of the person you are looking to massage. Warm some massage oil in your hands, and spread it evenly over their lower back.

Making lemon zest isn't hard and doesn't take a long time, especially if you have a lemon zester. A zesting tool is the number one preferred way to get that lemon zest with no mess and no fuss. So, in the first video tutorial, see how to make lemon zest with a zester. Use a zesting tool for the peeling, and make sure to wash the outside of the lemon thoroughly to remove dirt and residue. Then zest away!

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

Shave precious seconds off your running time and you just might win your next 5K. You Will Need

Math skills and strategic planning are essential to winning this ancient African game. You Will Need

Learn how to shuffle a deck of cards. Impress your poker buddies by learning how to shuffle and deal like you do it for a living.

Create a cute headband out of your own hair with this braiding trick. You Will Need:

Alton Brown serves a blueberry buckle that's perfect for a tasty breakfast. Follow along in this cooking how to video to learn how to make this sweet treat. You can serve up the warm blueberry buckle with a cup of coffee or milk.

Looking for an easy vegetable recipe for the grill? Follow along with this cooking how to video to learn how to make some grilled veggie skewers. Enjoy the bounty of summer by grilling your favorite summer veggies.

Watch this how-to video from the Dog Channel and learn how to make healthy and tasty anti-flea biscuits for your dog. These anti-flea biscuits are sure to be a hit with your dog. Not only are they healthy but they have the added benefit of flea control.

Abstract art may seem random but it often utilizes basic art and design theories. Learn more about making an abstract painting in this free art lesson from an art instructor.

The basics of two-dimensional design utilizes design elements such as space, balance and line. Learn foundational design skills with this free art video series.

Learn how to do alternate side lunges with shoe taps. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do dumbbell front raises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do seated dumbbell hammer curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to pronounce the OUGH sound in American English. This video language lesson from Rachel's English provides a basic guide for pronunciations for ESL students. Say "ough".

Learn how to do downhill ski series exercises. Presented by Real Jock Gay Fitness Health & Life. Benefits

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Native screen recording, one of the hottest features that Apple included in iOS 11 and later, is easily started from the optional Control Center toggle on your iPhone. From there, you can stop recording from the same place or from the red status bar or bubble. It's a very convenient addition to iOS, but there's one obvious downside — that red indicator, which can appear in your recordings.
BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

The de Blasio Administration of New York City has announced that the NYU Tandon School of Engineering will be hosting the country's first publicly funded VR/AR facility.