Make Slime! This one is easy. Just mix equal parts of glue and water and then add an equal part of liquid starch. Just like that you have gooey slime. The more you play with it the more fun it becomes. This acclivity causes the polymer chains in the glue to cross link with chemicals in the starch. The result is an awesome stretchy slime.

Learn how to do low cable bent bar squat and curl holding the bar high. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single medicine ball on the shelf crunches. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do side to side pop push ups across a step. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do break dance push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

In this video tutorial, viewers learn how to draw a skull. Begin by selecting a skull image to draw from. Then draw a circle and sketch a few lines to position the eye sockets, nose and mouth cavities. Now erase the guidelines and re-sketch the drawing. Then start toning the eye sockets and nose cavity by shading. Now tone the other parts of the skull. Finish by shading the background. This video will benefit those viewers who are interested in drawing and art, and would like to learn how to ...

In this tutorial, learn an important safety tip for the next time you head out camping or hiking. In this video, you will get advice on how to make a Swiss seat rope harness. You will learn to utilize a length of rope to make a field expedient rappelling harness, that is similar to the seat used by the military. With practice, you can tie this Swiss seat in 90 seconds or less. Essentially, this is a high speed, low drag way to make your own harness. This harness is useful for rappelling or ex...

This step-by-step video tutorial will have you building metal riffs in no time! Andrew Wasson of CreativeGuitarStudio has written a short two-part riff using the harmony from a popular scale out of the style called Phrygian dominant. For the riff, Andrew uses a series of open strings, eighth note triplets, hammer-ons, and pull-offs. Because a lot of progressive metal utilizes different time signatures, Andrew changes the time signature for the last measure of the riff. Don't forget to downloa...

Teresa Richardson from the crochet-mania blog will be teaching us how to crochet a left handed seed stitch scarf. In her video, she is going to be guiding us through the process of crocheting single and double seed stitches as well as providing us with step by step instructions on how to make the scarf. Teresa designed this tutorial with beginners in mind, so newcomers are more than welcome to utilize and learn from it as well. Be sure to have a crochet needle and some yarn handy prior to wat...

Learn how to gain better control of handling the ball with both hands while staying in the lane with the help of this great basketball dribbling drill for alternating hands.

The swiss army triplet is a unique one-way rudiment that can be played in both right and left hand leads. Unlike most of the other rudiments, this rudiment isn't designed to alternate. As its name suggests this rudiment has a 'triplet' feel.

This blueberry crumb cake is practically a masterpiece, if you dare try too make it. If you're up for the challenge, this moist and tender crumb cake packed with fresh blueberries and a delicious crumb topping will never last a day in your home. This yummy cake is hard not to like. It's irresistible. Check out this video recipe for baking buttermilk blueberry crumb cake.

For this project you will need some 4 mm orange beads, acrylic spacers, 4 mm black glass beads, 8 mm black glass beads, 10 mm orange glass beads, memory wire, headpins & skull charms. You also need pliers that include bent nose pliers, chain nose pliers, round nose pliers and memory wire cutters. Ordinary pliers become blunt when used on memory wires. In the first step cut some loops of the memory wire depending on how many loops you want to have on your wrists. Now take a skull charm and a 4...

Saher known as “sbGALT” is here to help with your singing vibrato. He gives an example of what vibrato is & how it varies from straight tone when singing. He sings a note with & without vibrato to illustrate the differences.

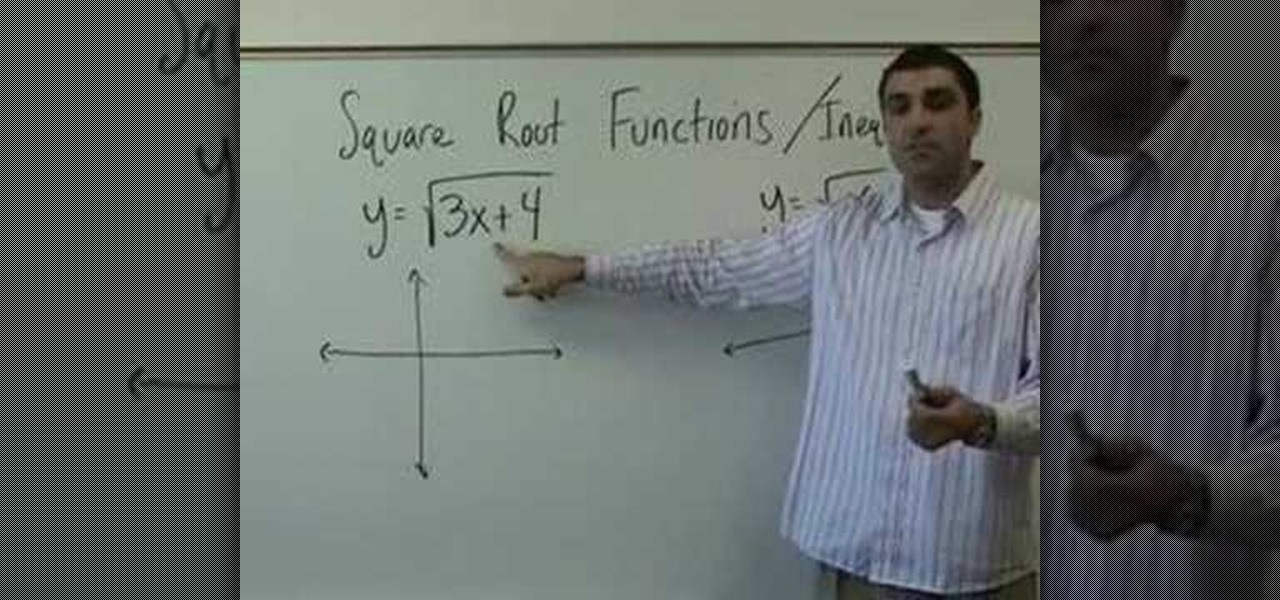
On Yay Math, Robert Ahdoot, founder of Yay Math, will show you some square root functions and some inequalities. He begins with the problem y=x². Then he makes a sketch with two intersecting lines in a t shape. The problem is illustrated by a curved U shape, the U's bottom resting on the horizontal bar, which represents x, while the center takes the vertical line. The vertical bar represents y. This U is directed up because the x² is a positive number. If the number were negative, the U would...

UAV Corporation has put together an 8 minute routine of 9 moves to improve the tone of your abs! -Note: There are 9 movements with 45 seconds dedicated to each one.

Spit, or speed, is a fun, fast-paced card game that will have your heart racing nearly as fast as your hands.

Charades is a word-guessing game that's acted out in pantomime by players at parties or other gatherings.

Make everyone in your neighborhood green with envy over your lush lawn with these landscaping secrets. Learn how to get your lawn green with this Howcast landscaping guide.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Here is a cake type of chocolate cake, it uses biscuit cookies. You will probably have to fight the kids off just because you want it all to yourself. The best part is that there is no baking required and it is very simple to make. The only thing you need is patience - just enough to make it and allow it to chill before you dig into it. Watch this how to video to learn a quick recipe for a chocolate biscuit cake recipe.

Learn how to squats and plyometric jump squats. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to design a defense to stop dribbling penetration or passes to the middle. If you're a basketball coach, you'll definitely want to utilize this two-three zone defense.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

This how to video teaches you different wrap moves with glowsticks. Learn how to do arm wraps, leg wraps, side bicep wraps, neck wrap, double bicep wraps, and the alternate arm wraps. Watch this tutorial and you will be performing glowstick wraps in no time.

This is a solution to the Snake Cube, a puzzle made up of 27 cubes connected on a string through alternating holes in the blocks. There's no sound, so you'll just have to watch, or maybe play some music in the background. Oh, and there's no talking, either.

Everyone loves ice cream, no matter what age they are. So why not try making a little homemade ice cream instead of hitting up Ben & Jerry's? You'll enjoy it, and most of all, you're kids will love it. With this recipe and an ice cream maker, you can create your own sundaes, shakes and ice cream cones at home.

The US Department of Treasury isn't generally known for being on the very edge of technology innovations (see the current hubbub around crypto), instead usually waiting until certain tools have been battle-tested in the mainstream or enterprise sector.

Sure, Snapchat AR Lenses can be fun, but they can help communicate complex issues as well. While our Facebook news feeds were filled with references to 311 Day, March 11 is also World Kidney Day, the United Kingdom's National Health Service Blood and Transplant (NHSBT) used the occasion to educate its constituents about organ donation.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

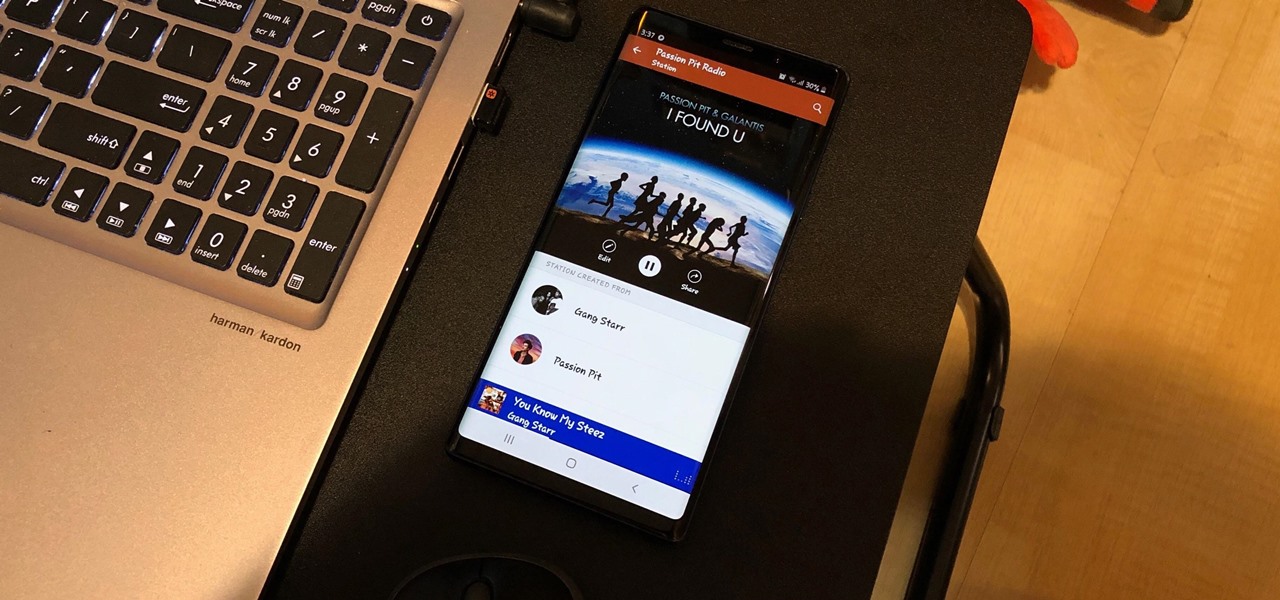
Whether you're out for a drive, commuting to work, or just taking a stroll, listening to your favorite tracks on Pandora takes the legwork out of choosing which songs to play next. After a while, however, you go-to playlist can get repetitive, as the same songs from the same artists seem to play over and over. Luckily, Pandora makes it easy to add variety to your stations in just a few taps.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

We all listen to podcasts differently — on the way to work, at the gym, when drifting off to sleep. If you're in the latter group and rely on Overcast to help you with your nightly routine, you're probably sick of its blinding light theme keeping you up. That's why the app features a dark mode, to keep things easy on the eyes while picking out or playing an episode.

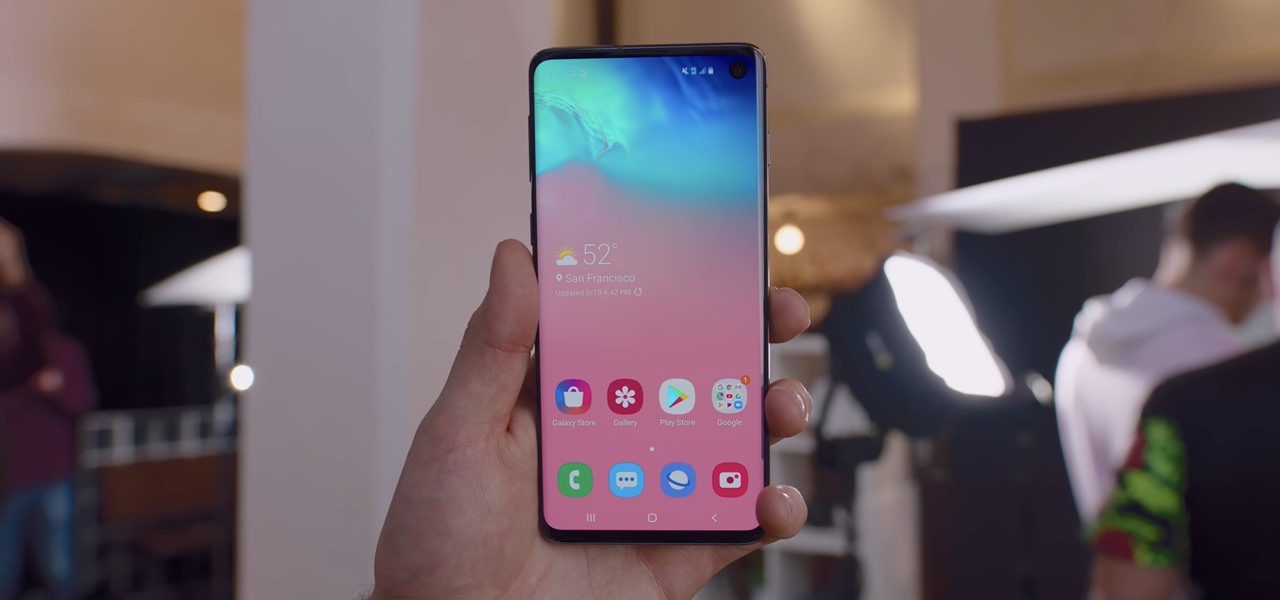
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

When Google finally gave us a dark theme for YouTube, it was a bit disappointing. They didn't use a pure black background, reducing some of the battery savings you'd get with an OLED panel. But with the help of another app, we can fix this, and not only get a real dark mode, but other colors as well.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.