Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

Data makes the world go round. It has gotten to the point that it's considered the most valuable resource, perhaps even more important than oil. Businesses use data to collect critical information about their users and improve their services; governments utilize it to improve things like public transportation; doctors analyze data to find more ways to save lives.
If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.
It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.
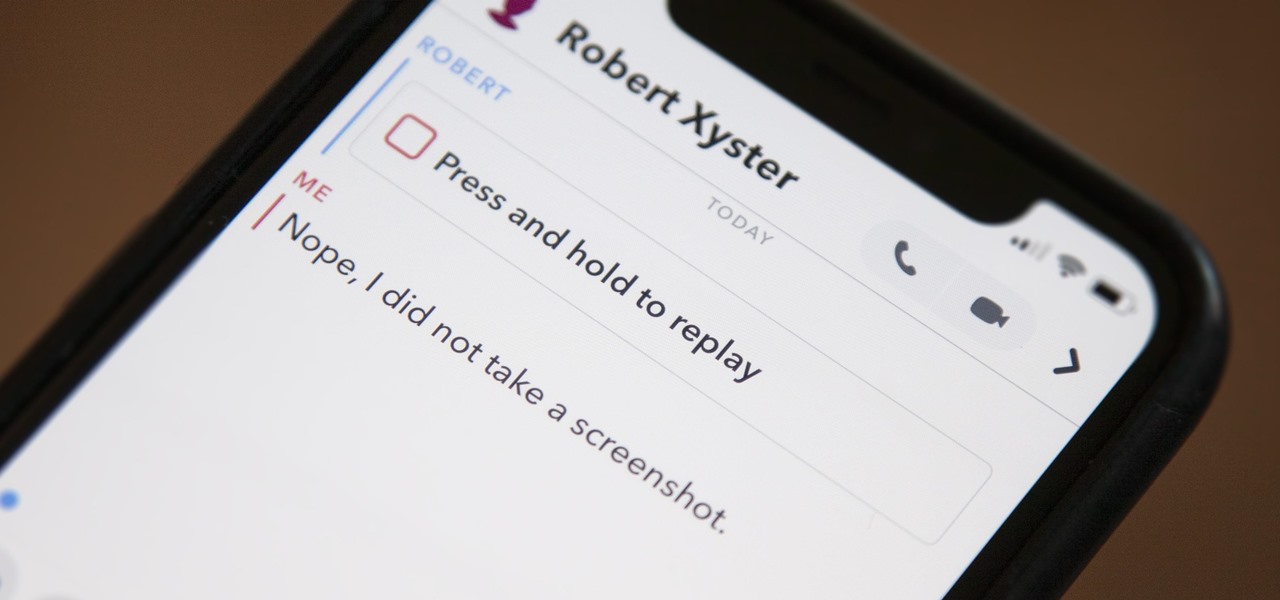
Snapchat doesn't prevent you from taking screenshots of snaps received, but the other user will get an alert either as a prominent push notification or a subtle note in the app. Snapchat has improved its screenshot detection abilities over the years, so it's much harder to circumvent its technology for truly undetected screenshots — but not impossible.
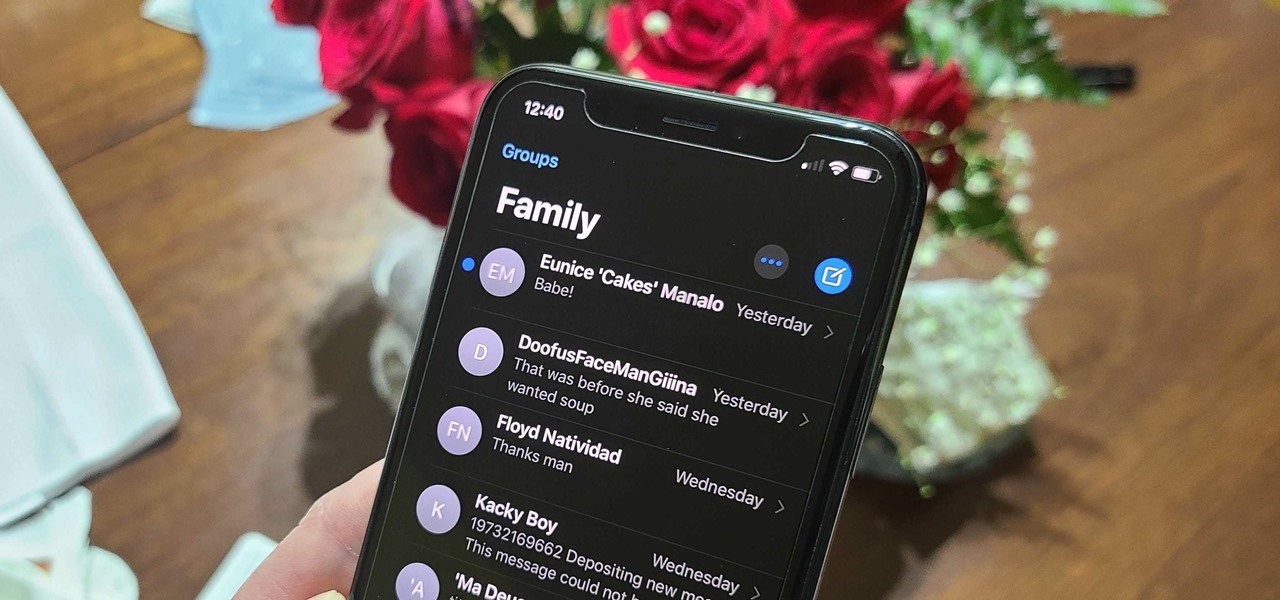
There's not much to the Messages app for iPhone when it comes to finding the right conversations. It did get some enhanced search capabilities in iOS 13, but beyond that, there's no good way to find the threads you need aside from just scrolling through the main page, which lists newer ones first. However, there is a tweak that gives you the power to group like-minded chats together.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

Whether you're calling the unemployment office, a popular radio contest, or any other phone line that gets super busy, having to recall the number manually is a pain. Whatever you do, however, don't punch in the same digits over again and again — our smartphones can help do it for us, saving our time (and sanity).

AirPods are starting to show up everywhere, and with more and more people owning them, it can be fun to make yours a little more personalized. One way you can do that is by giving your AirPods a unique name, something a bit more fun than "John's" or "Jane's AirPods." With just a few taps, you can change your AirPod's name right from your iPhone or Android phone.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

While the long-awaited HoloLens 2 officially arrived this week, details leaked about another, arguably longer-awaited AR headset, the fabled wearable from Apple, and a previously undisclosed partner assisting the Cupertino-based company with the hardware.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

Apple might not be ready to unveil its rumored-yet-unconfirmed smartglasses. But the iPhone's current depth-sensing hardware is proving to be useful for both smartglasses makers and mobile AR apps.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

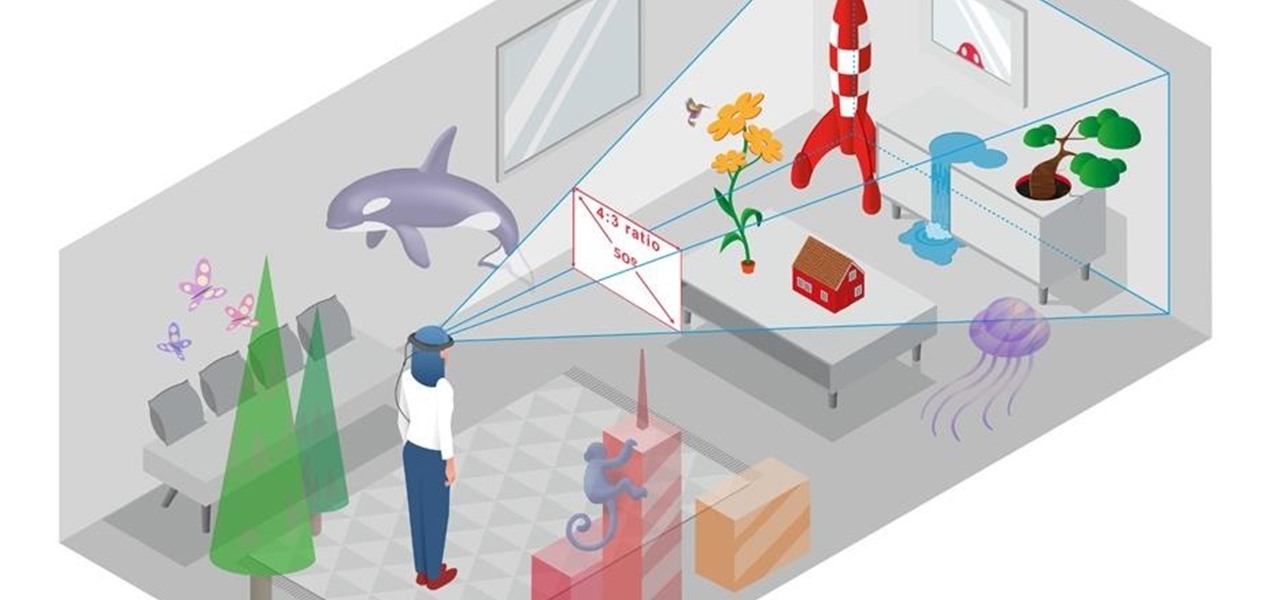
Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

Now that Samsung upgraded DeX in the Galaxy Note 10 and Note 10+, more users will be looking to use their phone as an "anywhere PC." With a simple USB-C to HDMI cable or adapter, you can turn your Note 10 into a desktop, complete with full access to your apps.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

The ability to shift between virtual reality and augmented reality seamlessly on one device is a dream of many AR fanatics, but the execution is usually fairly buggy or underwhelming.

This week, the recurring theme in augmented reality can be summed up fairly succinctly: content is king.

Update February 25: The new Sony Xperia flagship has been announced, and it has a new name: The Sony Xperia 1. You can read all of the official specs and details at our full article on Sony's new model.

Now that its first developer conference is in the rearview mirror, Magic Leap continues to nurture its content development community, this time with an assist from strategic investor and retail partner AT&T.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

Improved security options in iOS 12 provide you with automatic password suggestions, a way to find and change weak passwords, auto-filling of 2FA codes, and Siri integration. Most of these apply to iCloud Keychain, but Apple hasn't forgotten about users of third-party password managers; In iOS 12, you can use 1Password, LastPass, and others with the AutoFill feature in websites and apps.

In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

In this series, we are going to get you to the edge of building your own cloud-based, cross-platform augmented reality app for iPhone, Android, HoloLens, and Meta 2, among other devices. Once we get the necessary software installed, we will walk through the process of setting up an Azure account and creating blob storage.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

Samsung Internet offers excellent features that enhance the mobile web browsing experience, often through its extensions. A QR code scanner, ad blockers, tracker blockers, and more work directly in the browser, so you can do exactly what you want to do on the web.

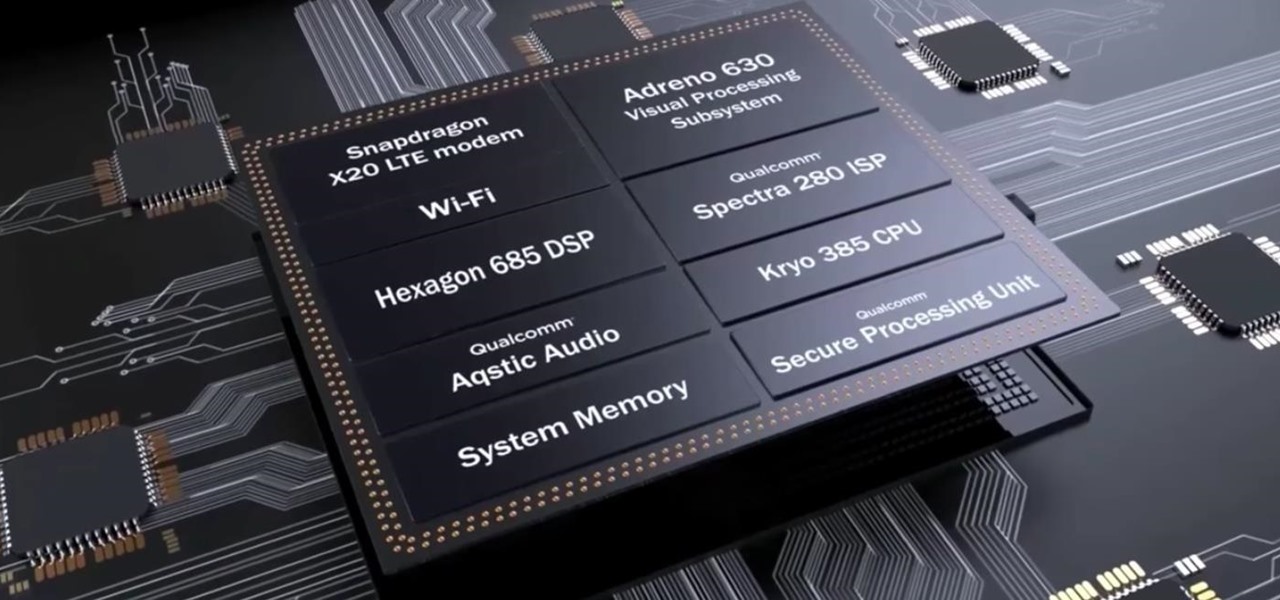
After the success of the Snapdragon 835, Qualcomm now has its eyes set towards the future with the arrival of its next-generation SoC, the Snapdragon 845. Debuting alongside the Samsung Galaxy S9, the 845 is now set to take over the market for flagship Android phones in 2018.

The latest and greatest in Qualcomm's long line of mobile processors, the Snapdragon 845, is now set to touch down along with the Galaxy S9 and S9+. And as gorgeous as Samsung's newest flagships are, the processor that powers them under the hood is just as highly anticipated.

With only one profitable quarter in the last two years, LG's mobile division is undergoing a shakeup. With a fresh set of executives, LG has delayed the expected launch of the upcoming G7 and instead decided to start the year with yet another variant of the V30.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

In 2017, major breakthroughs in smartphone-based simultaneous localization and mapping (SLAM) opened up new doorways for developers and users of both Apple and Android phones. Unfortunately for Android users, the solution that Google is previewing, ARCore, currently only works on three Android smartphones. But Silicon Valley start-up uSens is stepping in to fix that with its new engine called uSensAR.