We're a little butter-obsessed here, and that includes topics on why butter should always be browned, the rationale behind clarifying butter, and even how to make a DIY butter candle. And while some may consider the problem strictly one for the first world, we're always very interested in ways to spread cold butter on toast without ripping the bread to shreds. If you read that post, you know the ingenious solutions are many and range from grating your butter to buying a heated butter knife.

I love cheap, nutritious food: lentils, rice, toor dal, and other beans and grains. Even popcorn. The only problem is that they usually come in floppy plastic bags that make measuring ingredients more difficult. I usually open up one corner of the bag only to have everything come spilling out all at once whenever I try to pour out measured amounts.

It's so nice to be able to reuse old glass jars for food storage. Occasionally, though, even the sturdiest container has to be recycled because it retains the smell of its previous contents. Usually the culprit was garlic, garlic-based, or something pickled, and you're certainly not going to store your fresh herbs or fruit in that. There is, however, a quick and easy way to get that old stink out of your jar and make it usable again. You just need two things...

Toilet paper isn't the first thing that comes to mind when you want a hot meal, but when you're camping or out in the field (i.e. military training), a little TP is the difference between cold tuna and luxury.

Plastic bags may be banned from retail stores in some cities, like Santa Monica, Seattle, and San Fransisco, and will be banned in Los Angeles shortly, but we still use billions of them every year. What else are we going to use for throwing away cat litter or picking up dog poop?

Plastic red cups are synonymous with college parties, beer pong, and generally a good time. The reason these cups are so rampant in the party scene is because they're cheap, easily disposable, and, well... who wants to drink out of a blue cup?!? Oh, to be young and in debt.

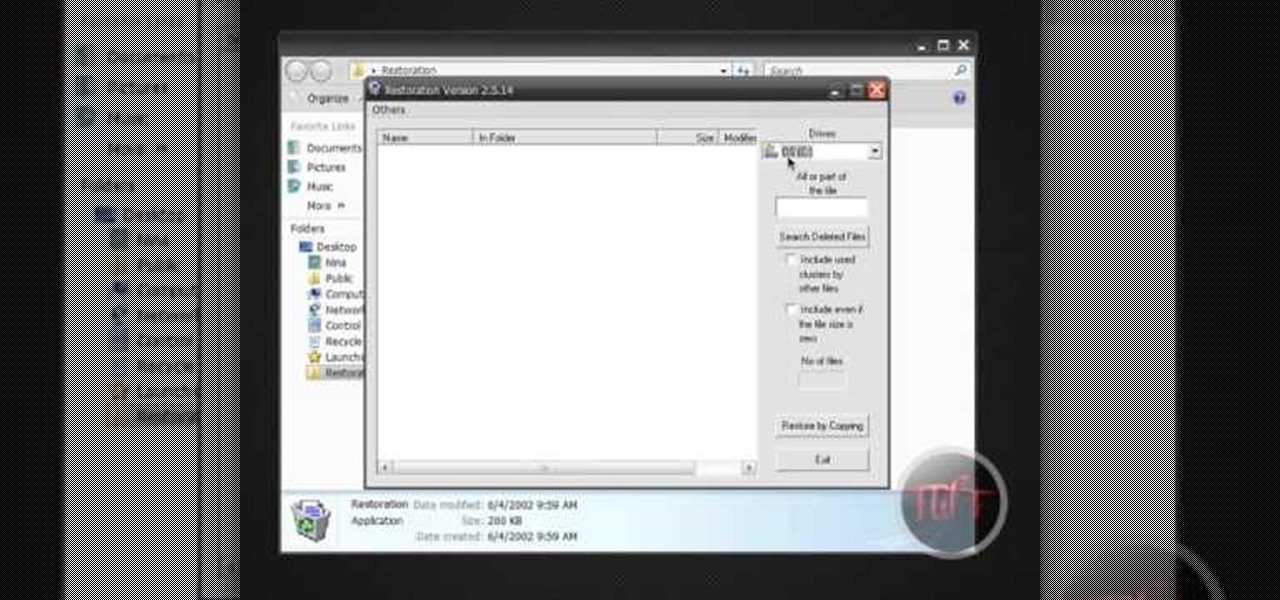
FireworksTutorial shows you how to restore your recycle bin files that you've already deleted. Go to Google and search "Restoration." Click on the first link that pops up from the list (the one from Snapfiles that's free) and download it. Once it's downloaded, run it and unzip it to somewhere you can easily access. Organize it by creating a new folder and putting the files into the folder. Double-click on the application Restoration with the trash can icon to load up the program (If you're on...

Analog reel-to-reel tape is some of the most in-demand recording equipment today. Learn how to use a reel-to-reel tape machine in this free video series that will allow you to utilize this piece of musical recording equipment.

Let your fingers do the walkin' and give the Yellow Pages a piece of your mind. In this tutorial, learn how to perform a very cool magic trick that will impress everybody.

The video is part of the awesome web show and this video is about recycling of plastic into beautiful shapes-Shrinky Dinks .At the beginning of the video an old plastic container top is taken and using scissors is cut into a circular shape. The scratchy surface of the circular plastic is coated with one color and on the other side some designs are drawn using another color. This piece of plastic is kept in a microwave oven which is preheated to 350 degrees to shrink it to a smaller size and t...

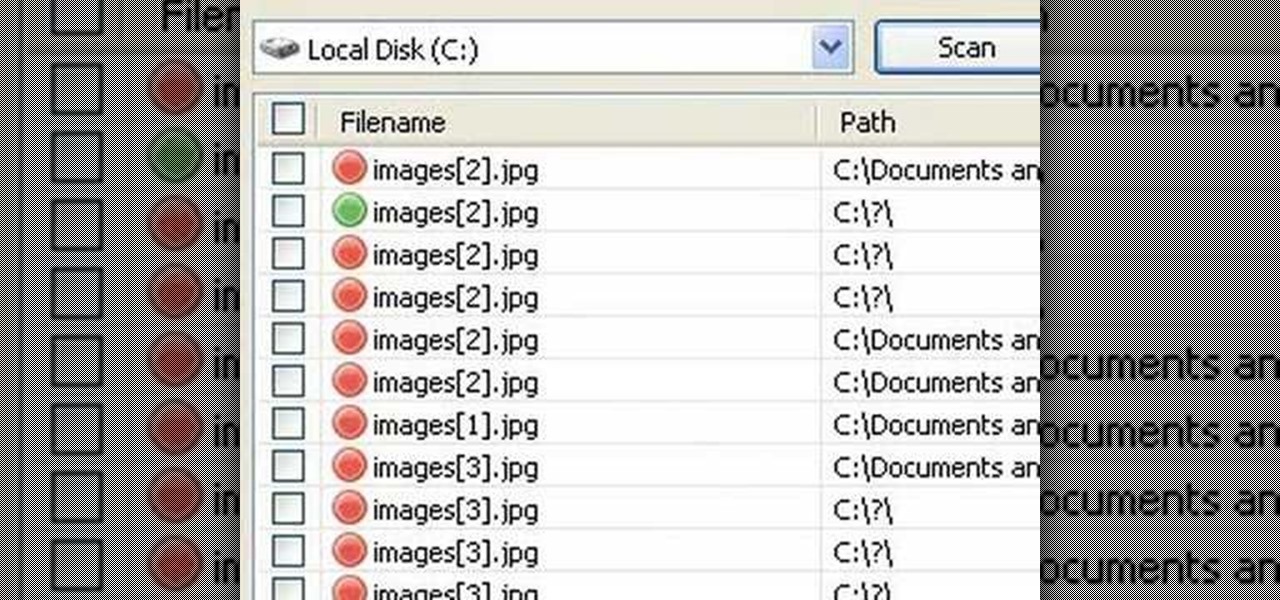
In this video tutorial, viewers will learn how to restore and recover deleted files using Recuva. Recuva is a freeware data recovery program. Recuva recovers files deleted from your Windows computer, Recycle Bin, digital camera card, or MP3 player. Begin by selecting the type of file and continue inputting the information. Then it will begin scanning the driver for the deleted files. It will then display all the deleted files. The green files are recoverable while the red ones are not recover...

Abstract art may seem random but it often utilizes basic art and design theories. Learn more about making an abstract painting in this free art lesson from an art instructor.

The basics of two-dimensional design utilizes design elements such as space, balance and line. Learn foundational design skills with this free art video series.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Native screen recording, one of the hottest features that Apple included in iOS 11 and later, is easily started from the optional Control Center toggle on your iPhone. From there, you can stop recording from the same place or from the red status bar or bubble. It's a very convenient addition to iOS, but there's one obvious downside — that red indicator, which can appear in your recordings.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

Razer just made a big step into the mobile industry by releasing an absolute beast of a smartphone. The gaming-centric Razer Phone tries to provide the best experience for its target audience: Gamers. With that in mind, they created a top-tier device with some of the best specs available on Android. But how does it compare to the current spec champion, the Samsung Galaxy Note 8?

The de Blasio Administration of New York City has announced that the NYU Tandon School of Engineering will be hosting the country's first publicly funded VR/AR facility.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

Yes, there's already a way to jailbreak iOS 9 on your iPad, iPhone, or iPod touch, but given the fact that it's only been out for about a week means that not all developers have had a chance to make their tweaks fully compatible yet. That doesn't mean they won't work, but that they might not be as smooth as they should be.

Android is all about customization: "Be together. Not the same," as Google's latest ads for the platform put it. Changing your device's boot animation, for instance, is one of the many great ways you can add a touch of personal flair.

Google has already started to roll out the over-the-air update of Android 5.0 Lollipop to older Nexus series phones and tablets, but chances are it will take a long time for the OTA to hit your device.

This is a really serious video. This video tell us about how to get rid of virus/spyware. It is based on JNBJABNK's own experience. She describe some step to destroy the virus which affected the computer. First of all make sure to confirm your system have spyware. Then open my computer folder and trace as quick as possible the infected file. Then run a full virus scan on that file. Delete the virus using the spy ware you have in your computer. On completing that you should restart your comput...

In this video tutorial, viewers learn how to recover and restore deleted files using Recover. Recover is a freeware data recovery program. Recover recovers files deleted from your Windows computer, Recycle Bin, digital camera card, or MP3 player. Start by selecting the type of file. Continue by inputting the information. It will then take an hour to scan the drive for the deleted files. Once finished, it will display all the deleted files. The green files are recoverable and the red files are...

This tutorial teaches you how to make a headboard from an old closet door and a red recycled curtain fabric. You will need a closet door or plywood cut to size, batting, fabric, a staple gun, foam, scissors, a circular saw, and an exacto knife. Watch this how to video and you can spice up your bedroom with this homemade headboard.

See these videos on making an eco-friendly home. Earthships are a passive solar home made of natural and recycled materials. They are thermal mass construction for temperature stabilization. The renewable energy & integrated water systems make the Earthship an off-grid home with little to no utility bills.