
How To: Make lasagna with an easy recipe
For a warm and hearty meal, try this simple lasagna recipe. You Will Need


For a warm and hearty meal, try this simple lasagna recipe. You Will Need

Is your waffle iron collecting dust? Plug it back in and use it like never before by whipping up a batch of brownies.

It's easy to make a peck of pickled peppers – or any other vegetable – with this basic recipe. You Will Need

It's not the best part of owning a pet, but somebody's gotta do it. You Will Need

With this recipe in your arsenal, you'll be the envy of professional bakers. You Will Need

Dessert crepes, a sweet French tradition, are delicate pancakes that can be enjoyed with many types of fillings after a meal – or even for breakfast. Watch this video to learn how to make dessert crepes.

Research shows that color can have a powerful effect on our emotions. Start harnessing that power today. Watch this video to learn how to improve your life with chromotherapy.

If things are getting a bit stuffy at your desk, don’t fret. A cool breeze is just a USB slot away. Watch this video to learn how to make a USB fan.

All stuffed up and wanting to breathe – but without the chemicals? Here's how to get relief fast! Learn how to clear up a stuffed nose with this home remedy.
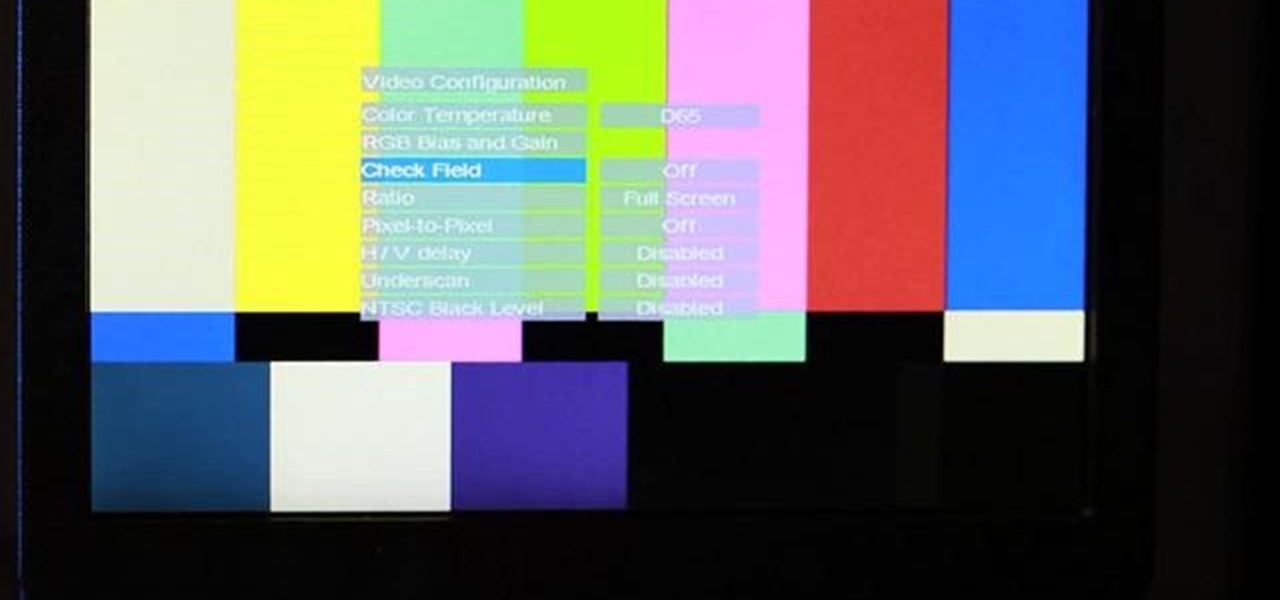
Check out this cinematography video tutorial on how to use calibrate an NTSC camera monitor, specifically a Marshall monitor.

When it comes to household versatility, baking soda is king. Here are just some of the many cleaning uses for baking soda. Cleaning tips:

This recipe comes to us from Mario Schembri, head chef at Ta´Frenc on the island of Gozo. Watch this how-to video cooking lesson to learn how to make stuffed Maltese chicken breasts. Serve the stuffed chicken breasts with a button mushroom sauce and a side of vegetables.

Abstract art may seem random but it often utilizes basic art and design theories. Learn more about making an abstract painting in this free art lesson from an art instructor.

The basics of two-dimensional design utilizes design elements such as space, balance and line. Learn foundational design skills with this free art video series.

Get kissable, soft lips by applying an exfoliator to remove dry skin and moisturizing the lips daily. Make lips soft and smooth by rinsing lips with warm water in this free video from a professional makeup artist.

This instructional knitting video provides tips for making interesting patterns using a knitting machine. Use a three prong tool to twist a stitch. Once you set the twist, you can knit an entire stretch of fabric with an elegant twisted stitch pattern. This creates a light knit with open spaces for a warm yet breathable garment.

Converting a wood fireplace to gas can warm and beautify your home. This how to video is a quick excerpt from a DIY show demonstrates the process of switching in an old fireplace for a modern one. Watch and learn how to convert a wood fireplace into a gas fireplace.

Craving some warm and creamy soup on a cold day? Then watch this how to video to learn how to make cream of broccoli and cheddar soup. This creamy broccoli recipe is better than any other out there.

Lighting up a room is easy with these simple cost efficient techniques. Watch this how to video and get some tips on how to add warm to a dark dungeon with a few tricks.

Impress your family and friends with fried ice cream for dessert! It's warm and crispy on the outside, frozen on the inside. Simply wrap French Vanilla ice cream in bread, dredge in a flour and sugar batter, and deep fry until golden brown. Watch this video tutorial for step-by-step instructions on how to prepare this dessert.

When it's cold outside, nothing warms you up like a mug of steamy hot chocolate. But don't settle for the boxed variety - watch how to make your own at home.

Traditionally, incorporating loops and grooves can translate into hours of hard work just to get the loop to fit your song's tempo and timing. Help is on the way from the Propellerhead's ReCycle which gives you full creative control over utilizing your looped material. Join electronic recording artist David Alexander as he shows you how ReCycle has revolutionized using sampled loops. In this episode, David shows us how to Chop Up A Complex Loop.

Learn how to warm up by jogging around half the basketball court while swinging your arms.

A plate of warm grits is a must-have for any traditional Southern breakfast. Learn the secrets to making a perfect batch of grits. You will need water, grits, butter, salt, pepper and bacon fat.

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Native screen recording, one of the hottest features that Apple included in iOS 11 and later, is easily started from the optional Control Center toggle on your iPhone. From there, you can stop recording from the same place or from the red status bar or bubble. It's a very convenient addition to iOS, but there's one obvious downside — that red indicator, which can appear in your recordings.
BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

The de Blasio Administration of New York City has announced that the NYU Tandon School of Engineering will be hosting the country's first publicly funded VR/AR facility.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

Oven space is scarce on that fated fourth Thursday of November. Even if you can find a spare space for pumpkin pie on the bottom shelf, you risk turkey drippings overflowing from above and ruining your beautiful dessert — not to mention a burnt crust from different temperature requirements. The bottom line is: oven real estate is valuable, and it's tough to multitask cooking for Thanksgiving when every dish requires baking or roasting.