Grab your PSP and get ready to ROCK Metal Gear Solid: Peace Walker! This video walkthrough guide will take you through every mission, from the main ones to the secondary ones. Follow along and learn the tips and tricks to the gameplay so you can beat the game yourself! Peace Walker is the fifth installment in the Metal Gear series.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

Check out this three-part series on how to play Super Smash Bros. Melee (advanced). This is not a beginning tutorial for all you newbie gamers, it's more detailed and advanced for pros, or semi-pros.

When caring for your pet, finding and treating their insect bites which may cause allergic reaction in your pets. Bites from wasps, spider, bees, and other insects may cause an intense allergic effect. First, check if your pet is still breathing and check if there is a stinger still is in their body and scrape it out using a credit card. Using a medication that contains only chlorpheniramine if your pet is conscious, breathing, and not vomiting. Using this method, you will be able to ensure t...

The Shim Sham or the Shim Sham Shammy is a line dance with many different variations in choreography. This version may be different from the one you may have already learned. This version is credited to Leonard Reed and Willy Bryant of the Apollo Theater. Learn how to do the Shim Sham dance steps with this video tutorial. Though this video was shot with music in the background from another room, the tunes normally accompanying this dance include Chick Webb or Benny Goodman's version of "Stomp...
Learning a new language as an adult isn't just hard because your brain works differently from when you were a kid. You also have to contend with having less time and energy to practice. However, if you're looking to add another language to your repertoire at a pace you decide, then the Babbel Language Learning: Lifetime Subscription for All Languages: 2-Pack will be a useful tool for you.

Twitter is a science. The smarter you post and engage with others, the better chance you have at building a bigger audience. Scheduling your tweets is one way to get there. Most engagement occurs at specific hours, but you may not be around then to post your tweet manually. While the official Twitter app on iOS and Android doesn't allow you to schedule, there is another way.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

One of the best gifts that someone with an iPhone can receive is a paid app, hot new movie, bestselling album, gift card, or anything else in iTunes, Books, or the App Store that costs money. Even if it's a small $0.99 game that you heard a friend talking about, a gesture like this can go a long way. Gifting apps and media is now easier than ever, even if you don't have an iOS device yourself.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Bed bugs are brown and creepy. Could you spot one in your hotel room? A new study reveals most people are freaked out by bed bugs, but only about 35% could identify one.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

Disney's animated film Toy Story 3 beat all expectations at the box office, and is now the highest-grossing movie of 2010 in North America and second worldwide. Can Disney Interactive Studio's Toy Story 3: The Video Game match the success? Who knows, but no matter how successful it is, it's still a fun game full of animated delight, and this Mahalo video walkthrough series will show you the entire gameplay for the game on the Xbox 360.

The new Medal of Honor video game is out for the PlayStation 3, Xbox 360 and Windows, and if you happen to have yourself the Xbox 360 version, check out this extensive video walkthrough series. It takes you through the entire gameplay for Medal of Honor— all 10 missions. Make your way through modern-day Afghanistan and eliminate all of the Taliban forces.

Spider-Man hits the iPhone, iPod Touch & iPad! In Ultimate Spider-Man: Total Mayhem, you take control of Spidey, slinging webs and fighting crime. No longer do you have to stick to comic books, you can enjoy Spider-Man right from your Apple mobile device.

Apple continues to suffer production delays caused by COVID-19 era factory closures, and the products taking the biggest hit are its customized 14-inch and 16-inch MacBook Pro configurations. Long story short, you'd be lucky to get one of those 2021 MacBook Pro models by the end of June 2022.

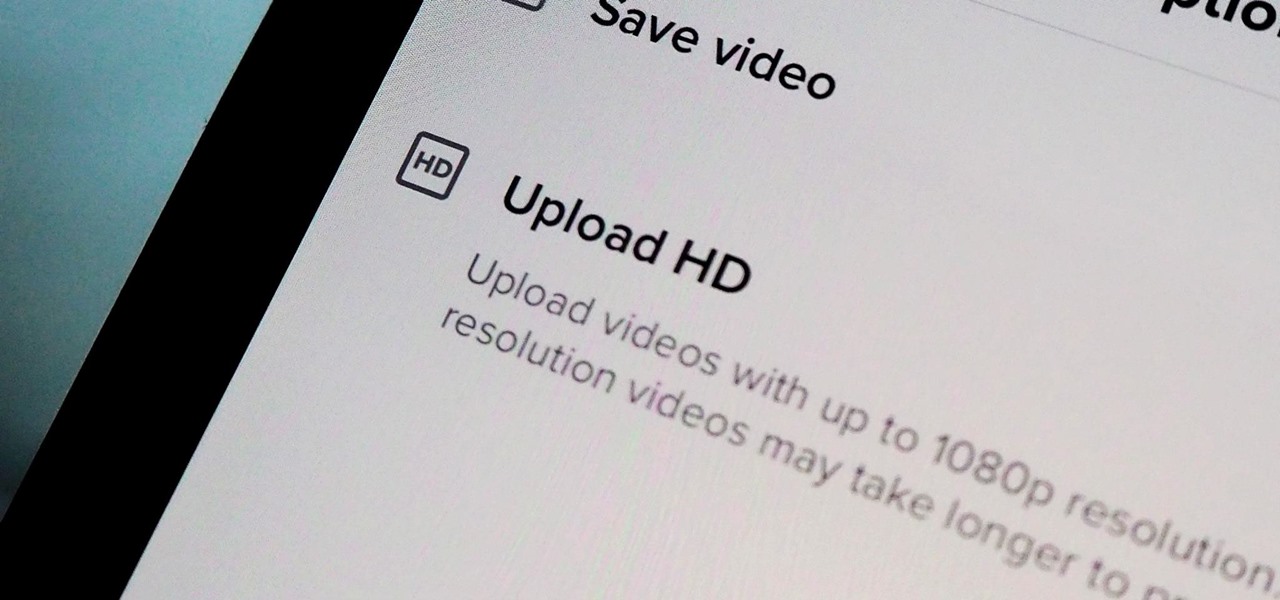
You might have noticed some of the videos you upload to TikTok don't always look great. If you think the answer is that you need a DSLR, you're wrong. The blurriness, pixelation, and overall bad quality that can happen in your uploaded videos is probably not your smartphone's fault — it might be because you aren't uploading your videos in HD.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

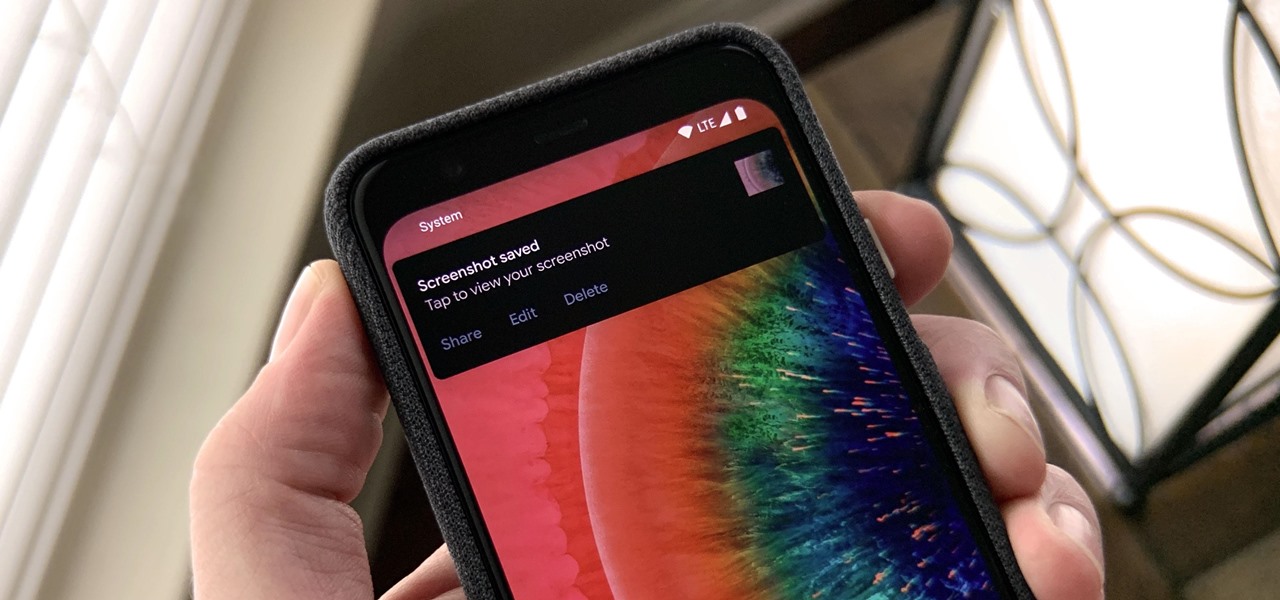
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

Last December, Google unceremoniously killed off Google Glass Explorer Edition with a final software update, leaving the Glass Enterprise Edition 2 as the only remaining AR wearable from Google.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

It's a good sign for any emerging technology when one of the leaders of an industry adopts it. So when Mastercard, a brand so recognizable that it dropped its name from its logo at CES last year, decides to develop a mobile augmented reality app, the moment is a milestone for the AR industry.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

I go back and forth between two home screen apps: Nova Launcher and Action Launcher. While I prefer the aesthetics of Nova, I like Action's Quickpage feature since it puts some of my favorite apps just a swipe away. But now, I've found a way to replicate this feature on Nova (or any other launcher), and it works even better.

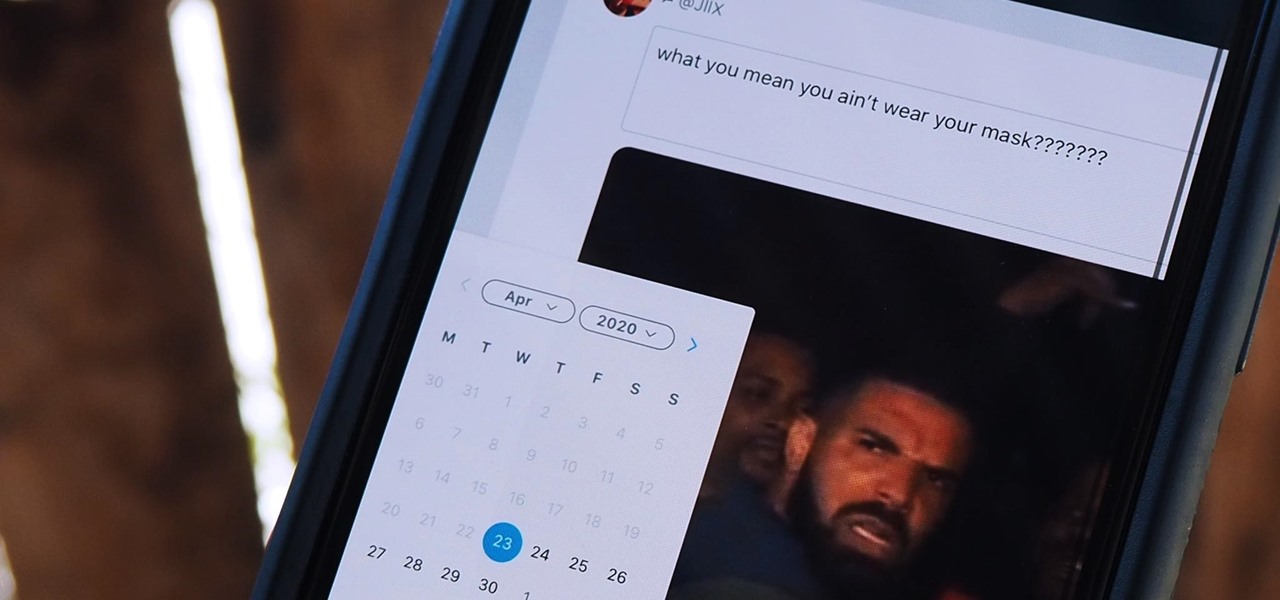
You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Fast-food chain Jack in the Box has decided to put an augmented reality twist on the traditional sweepstakes promotion by employing the immersive powers of Snapchat.

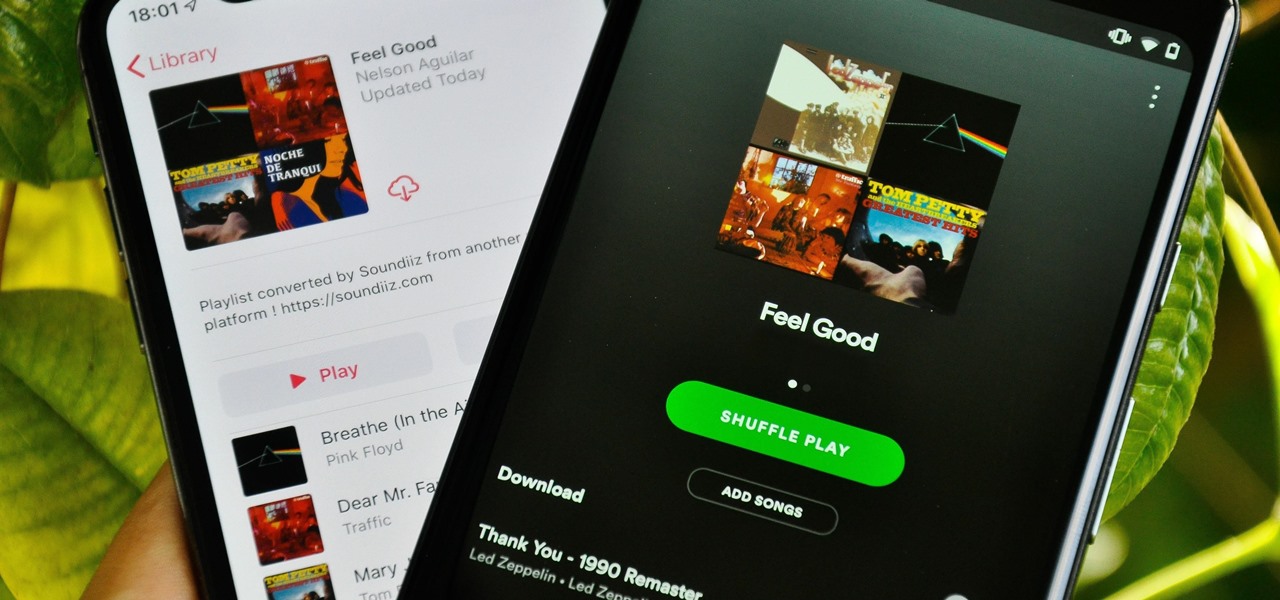
Music streaming services make it difficult to transfer your favorite songs and artists from one service to another and for a valid reason: they don't want you to leave. But when it comes to switching, playlists are a big concern, because who wants to do it all over again? Luckily, if you're moving from Spotify to Apple Music, you can use a third-party app to take playlists with you.