Starting a few months back, you might have noticed that some text messages you received from certain friends or family members had blank or missing characters. This was because Apple included all of the new Unicode 8.0 emojis in an update to their iPhones, but Android devices didn't have some of these just yet, so they weren't capable of displaying them.

As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.
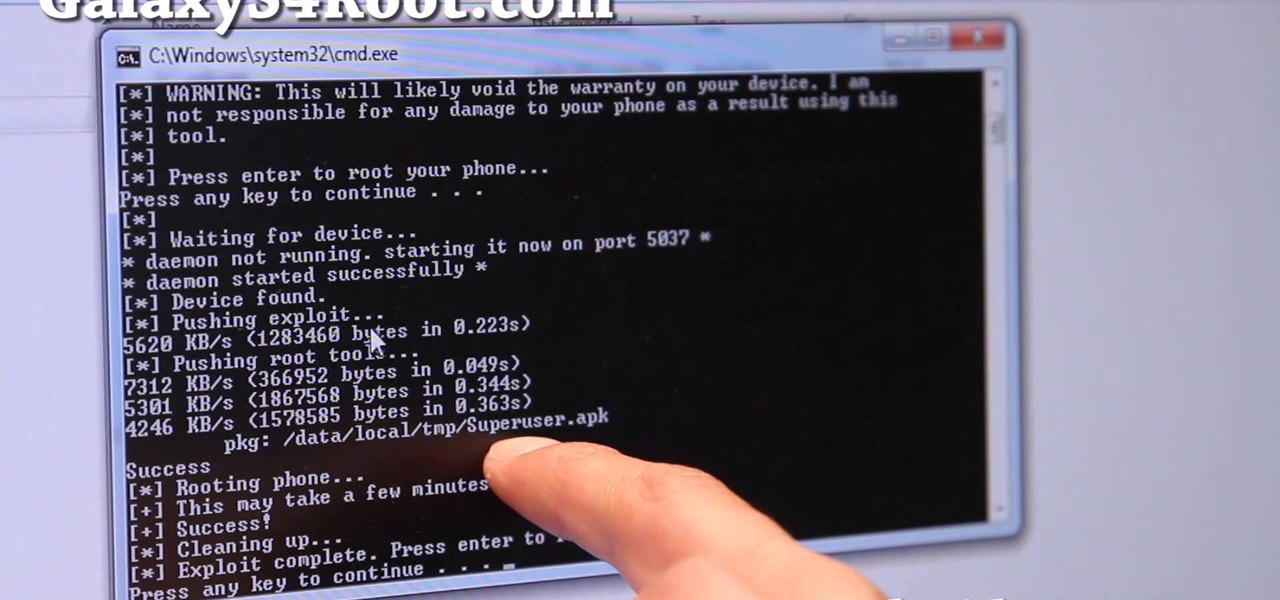
Here's a quick and easy video tutorial on how to root any Qualcomm-based U.S. or Canadian Galaxy S4 Android smartphone.

What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

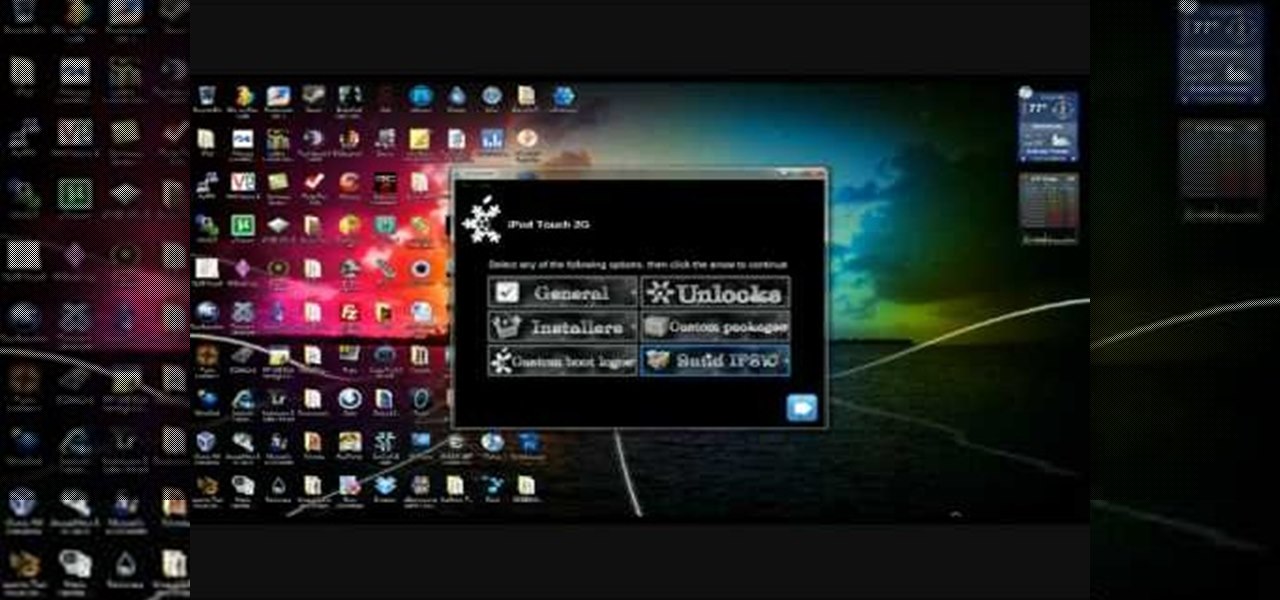
In this tutorial, learn how to jailbreak your new iOS 4 on your iPhone or iPod. This jailbreak will let you take advantage of cool new features including the huge app superstore: Cydia. Enjoy!

Steve with Eikenhout Educational Video Series and Paul Griggs with PGriggs Construction demonstrate how to install new windows during a new construction application. You will need a level, a utility knife, a caulk gun and a hammer to install the windows. First, cut the house wrap away from the area where the window will be placed. Next, properly flash the opening to protect it from water by starting at the window sill. Next, verify that the sill is level. Next, caulk around the window opening...

If you would like to use Google AdSense on your website, in order to make money from your site, you will need to get a Google account. Click "sign in" on the Google home page: www.Google.com. Next, scroll down to the bottom of the page and click on "create an account now. Fill it out. It will send you an email to verify your account. You'll need to open your email to confirm.

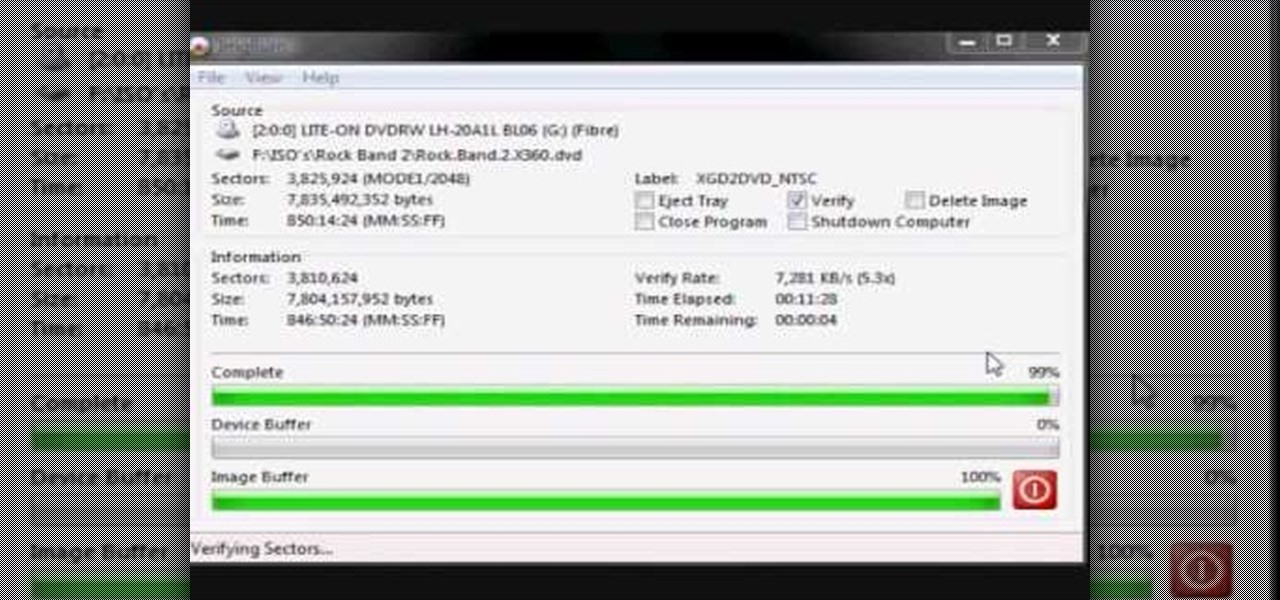
In this how-to video, you will learn how to burn game ISO's for the Xbox 360. It is important that it is only legal to back up the games that you already own. You will need the Image Burn program. Open it and click Write Image File to Disk. Next, click browse for file and look for the .DVD file. Go to tools and settings. Click the Write tab and go to sectors and make sure the number is 1913760. Check the ISO file and open it with notepad to check if the layer break number is also that number....

Tom of Videomaker teaches how to use the green screen to make a character appear in front of a set or to achieve the website spokesperson effect. Install a green screen in such a way that the fold at the corner of the wall and the ground is instead curved in order to create an even transition from the top to the bottom of the green screen. Build the base at the bottom part of the screen by weighing down the fabric at the corners and stretch it evenly. Light the green screen separately from th...

This video teaches viewers on how to inspect a motorcycle for damage after an accident as well as documenting it. The most important thing you need to do after an accident is to document all parts of the damage by taking photos of the damaged parts. Start by verifying the VIN number or Vehicle Identification Number and take a picture of it, take a photo of it. After that, get a photograph of the mileage on the dash area of the motorcycle. If there is other important information that needs to ...

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

A universal dark theme has long been one of the most sought-after features we've been urging Apple to introduce for iOS. While this wish went unfulfilled with iOS 12, there's renewed hope that it'll finally touch down with iOS 13's arrival. The jailbreak community, however, has had this functionality available for quite some time, and you can too if you're running the right iOS version.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

The new iOS 10 won't be released to the public until September 13 via an OTA update, but the Gold Master edition is available right now. Essentially, it's the same version that Apple will release on the 13th, but only for developers so they can get their apps up to snuff before everyone updates. Users on the iOS 10 public beta will not be getting this GM update.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

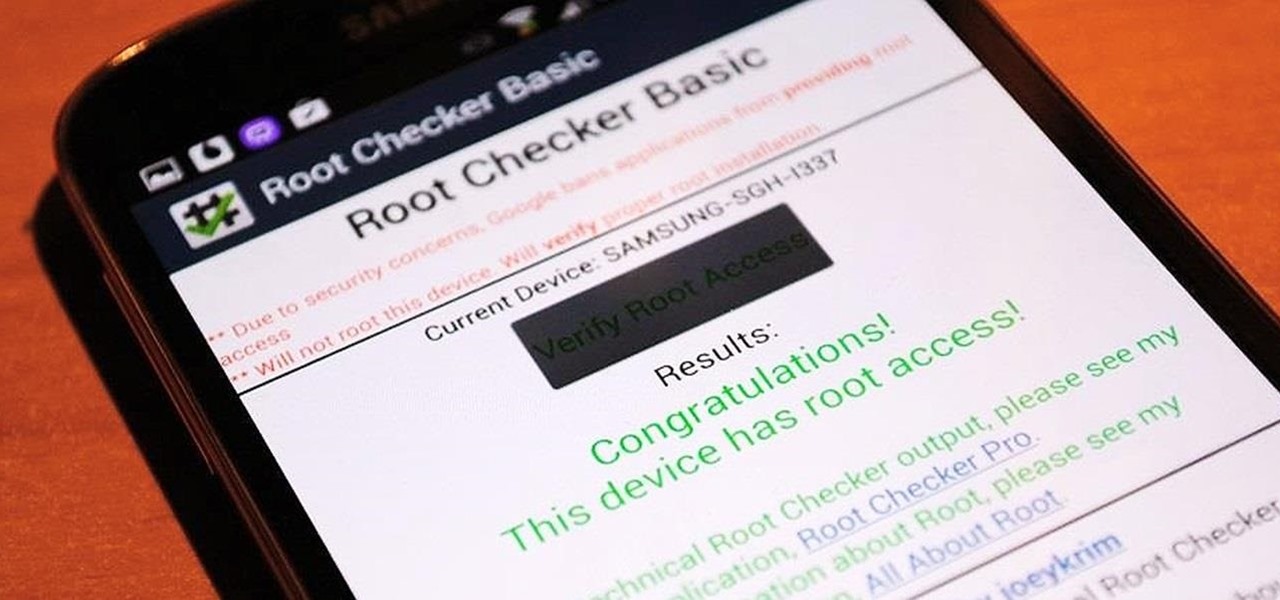
Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

It didn't take long at all for developer Chainfire to sort out a root method for the new Android 5.0 Lollipop. After handling a few issues with changes to the SELinux kernel module, Chainfire pushed out an update to his popular SuperSU root app.

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

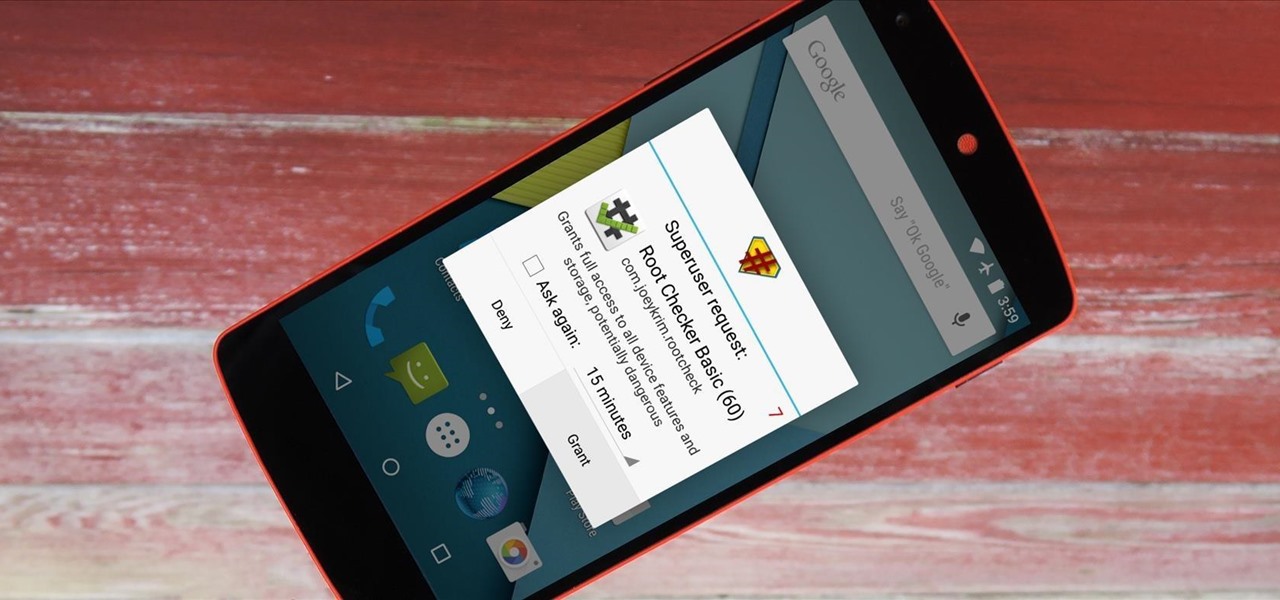
For new Android users, rooting an Android phone can often be an intimidating process, especially since there are so many different ways to gain root access, depending on your model and firmware version.

Rooting is usually the first thing on the to-do list whenever one of us softModders gets a new Android device. Unfortunately our efforts are sometimes hindered by certain obstacles; a common one is a locked bootloader.

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

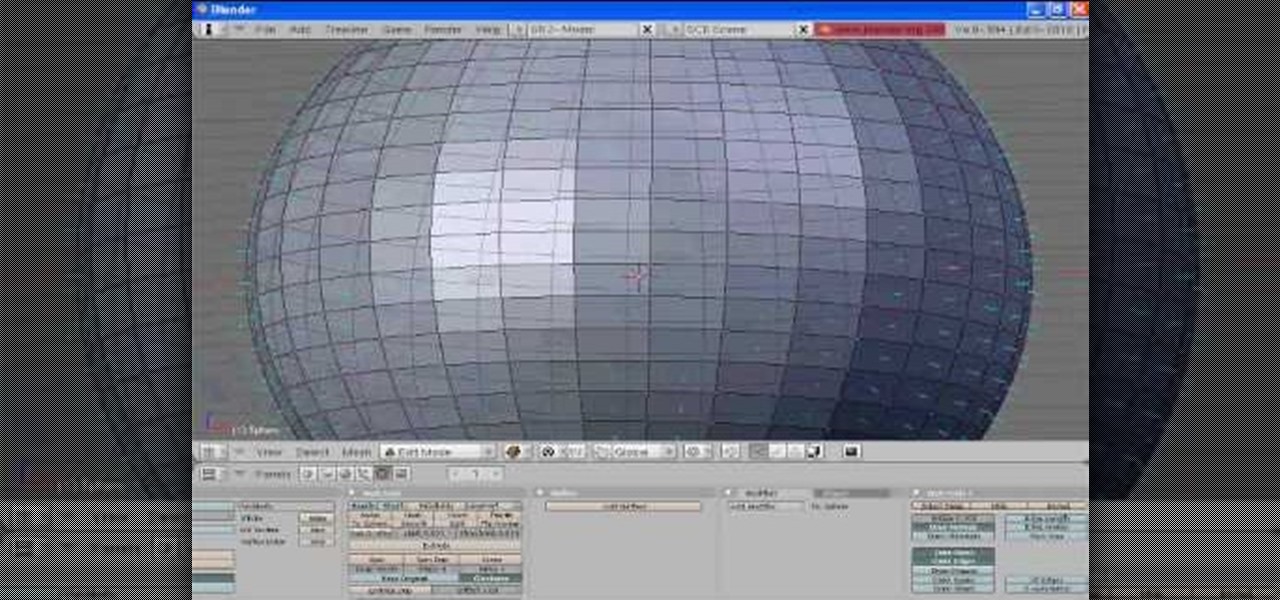
In order to unwrap and object and export it in Blender, you will need to import and object in blender, by go to "file". Click on "import". Click on "wavefront". Then, go to the parent directory. Select the object, by right clicking. Then, go into edit mode via the drop down menu, underneath the object. When your "normals" are visible and facing the right direction.

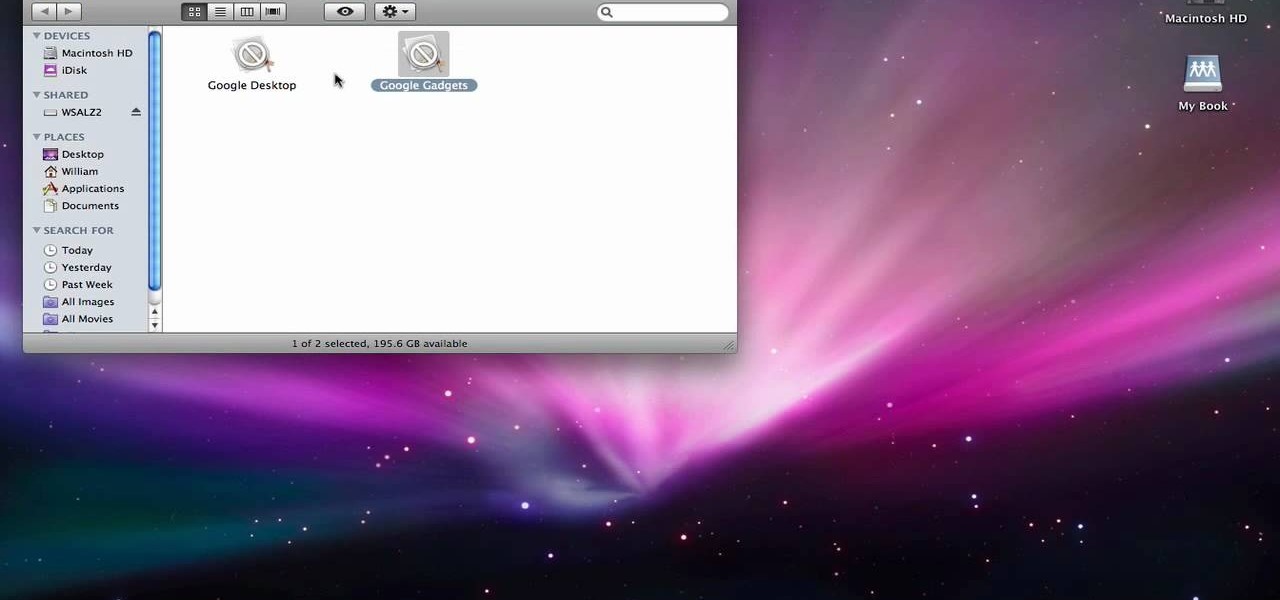
In order to completely delete items from Mac OS X. Download Google desktop. This will search your computer and the web and your computer. Go to Applications. Right click on Google Desktop. Go to Show Package Contents. Drag contents into the trash. Next, go to Google Gadgets. Click and drag it to the trash as well.

This is a handy tutorial about creating the favicon. A favicon is an icon which appears on the tab, in the address bar and in the favorite menu of browsers. To make a favicon:

This video shows you how to countersink a wood screw. 1. Find appropriate pilot hole drill. This should match the shank size of the screw.

The citizenship card is a document that naturalized Canadian citizens use to prove that they are Canadian citizens. This card is needed to get certain documents such as a Canadian passport. It never expires but it can be updated to include a new picture or name change. Citizens born in Canada do not use the card, they use their birth certificate to prove citizenship. Naturalized citizens can apply for this card and so can people with parents of Canadian descent. People who have previously had...

The first thing that comes to mind when your car is stolen is: ####!! However, once calm, cover these bases when your car is stolen to notify relevant parties and help ensure vehicle recovery or replacement.

Weird gifts from friends and family aren't the only things you can score on your birthday. With a little advance planning, you can get lots of freebies.

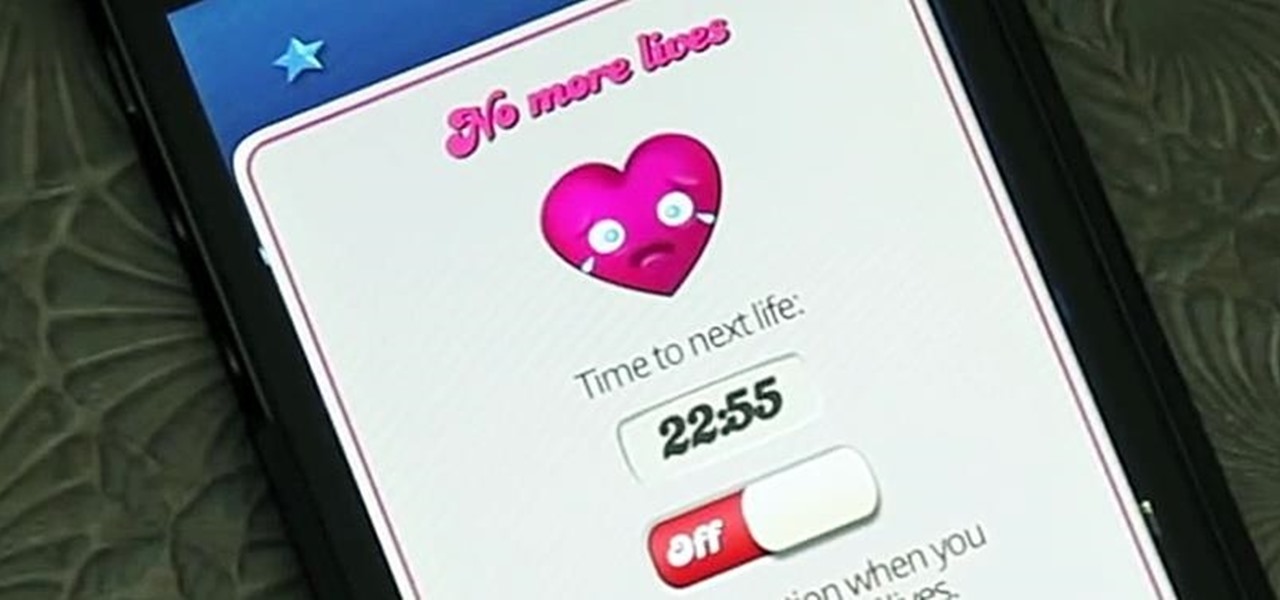
I hate waiting to play, and I hate bugging my Facebook friends even more. But that's what Candy Crush Saga makes you do if you want to get new lives and levels faster.

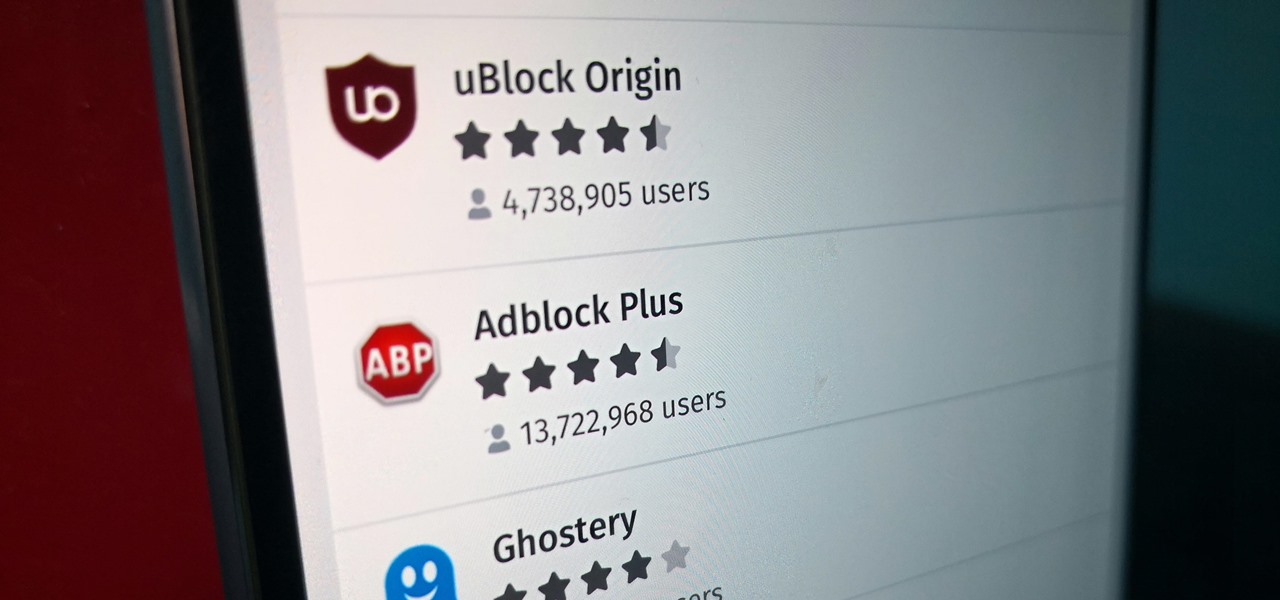
Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add features without having to upgrade the entire app.

Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.

ViPER4Android is a revolutionary audio equalizer for Android, something that I personally can't live without. That's the reason why porting V4A to the LG V20 was the first thing I did when I got the phone. There are two variants of ViPER4Android: FX and XHiFi. XHiFi is an older version which isn't developed anymore, but has amazing audio reconstruction capabilities. FX, on the other hand, has at least three times as many options and features as XHiFi without the audio reconstruction.