To play "People are Crazy," you begin with what is called the intro. For this song, the intro includes playing the same group of notes or strings two times; this is called "repeat" on the sheet music. All of the these notes will be played on the B-string except for one. The exception is played on the G-string and this is just played open. Start on the 10 thread (fifth string capo) holding it with your ring finger, count to the fifth string and play it twice, pause, then play 5, 3, 1, and then...

Watchout! Snowballs! You’re outside. You’re getting pummeled with snowballs. Time to build a snow fort and set-up teams... The snow war is on!

Bridge is one of the most popular games in the world. The rules may seem overwhelming, but all you need are a few easy steps to learn the basics.

Thanks to modern "smart phones" and the internet, media by the people, for the people is finally a reality. Here's how to use your phone to be a mobile journalist.

For anyone who's ever wondered why people are swatting an odd-looking object back and forth across a net, here's the lowdown. Watch this video to learn how to play badminton.

Turn your possessions into cash and become an online selling machine. You will need: Something to sell, a computer with internet access, an eBay account, a digital camera, shipping supplies, something to sell,a computer with internet access, an eBay account, a digital camera, & shipping supplies.

Accidents happen at work. This first aid how-to video demonstrates how to access and treat a nose bleed after a work related accident. Start by establishing what happened and making sure the patient can breathe properly. Inspect the area and apply an ice pack. These first aid tips are sure to keep your workers happy and healthy.

Watch this video to learn about screen writing and story structure in order to make your own movie. The "Inciting Incident" is explained— the moment in the first act that propels the rest of the story into motion. As an introduction into creative storytelling: Don't ever allow the inciting incident to be boring.

Watch this video from This Old House to learn how to build a retaining wall. Steps:

Watch this video from This Old House to learn how to plant a tree in poor soil. Steps:

Cloud computing has come a long way since the days of simple online storage and server networking. Virtually every major company in the world now relies on complex cloud computing infrastructures to reach customers, innovate products, and streamline communications. Their reliance on advanced cloud computing platforms is only going to grow in the coming years.

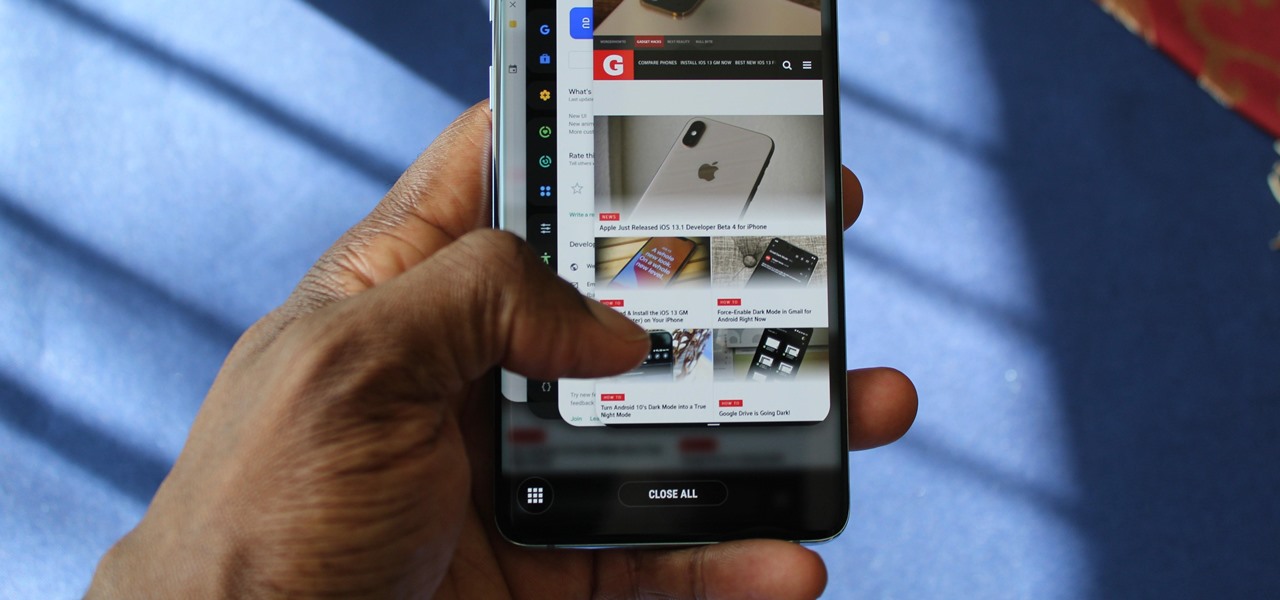
Lover it or hate it, Android 10 is a big improvement over Android 9 Pie. Based on previous versions, most flagships released in the last two years will get Android 10, but the question is when. So while you wait for those cool new gestures, how about I show you an app that gives you a nearly identical experience?

The hype around augmented reality has risen to a fever pitch over the past two years, and if this week's selection of business news stories are any indication, the din is about to get down right deafening.

Now that the Magic Leap One is out in the real world, the mystery behind the company lies not in whether it will actually ship a product, but when it will ship a consumer product. Or, does CEO Rony Abovitz steer the company in a different direction first?

Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we'll be digging into the Create app, the experience that allows you to fill the real world with objects that transform the nature of your local reality.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

If competition in the augmented reality space was a spectator sport, then ARKit, ARCore, and HoloLens dominate the prime-time broadcasts on ESPN.

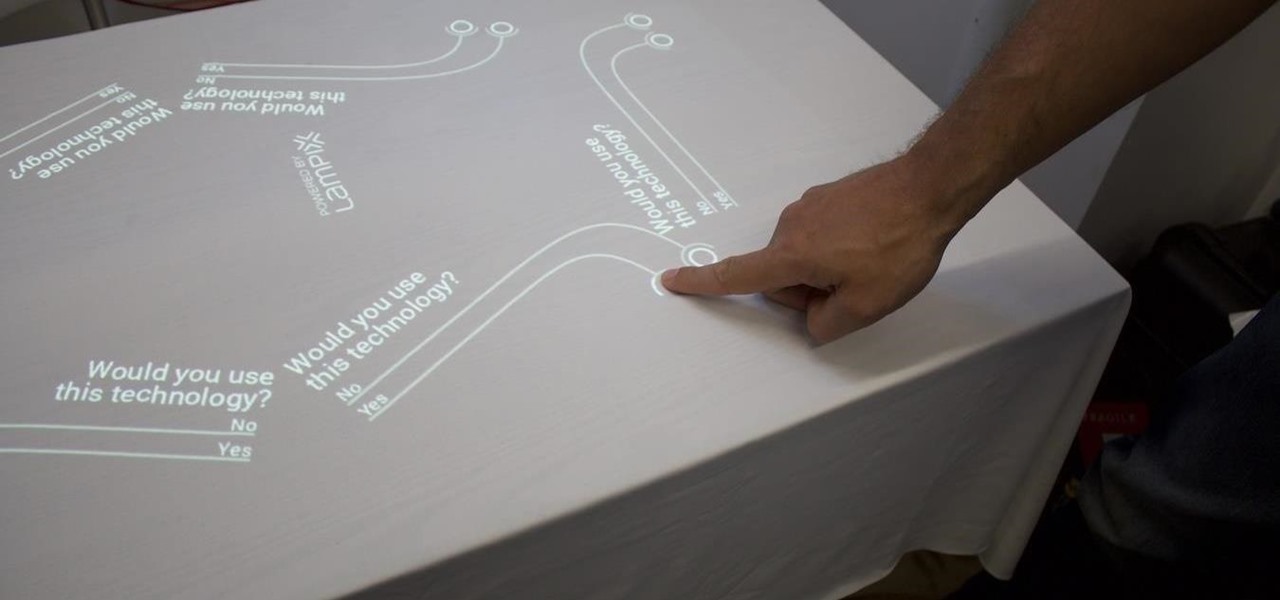
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

Breastfeeding is the ultimate in farm-to-table dining. It is sustenance prepared just for the baby and delivered with a very personal touch. Along with bonding, breastfeeding provides powerful protection to infants and young children in the form of beneficial bacteria, hormones, vitamins, protein, sugar, and antibodies manufactured on site to support infant health.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

One of the latest home-improvement gadgets out there today, smart lighting, has become more popular as prices come down. That being said, its still quite a penny to shell out. In this article, I'll go through a few of the top products out there today, including the Philips Hue, Belkin WeMo, and Lifx.

If you're not a carpenter, you may be completely overwhelmed by the information in this video. They have a tough job. Just like electricians, there's a lot of math involved in carpentry, and one of the calculations laborers struggle with is constructing a hip roof. If you're not sure what a hip roof is, you should just stop right here… don't go any further…

Another name for jumper's knee is patellar tendinitis. Jumper's knee is an injury that affects the tendon connecting your kneecap (patella) to your shinbone. The patellar tendon plays a pivotal role in the way you use your legs. It helps your muscles extend your lower leg so that you can kick a ball, push the pedals on your bicycle, and jump up in the air. Learn about the different causes of, symptoms of, and treatments for jumper's knee in this video.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.

Those of us who've taken the time to learn how to code are relatively well-suited for shakeups in the economy. Despite the recent and notable disruptions caused by the COVID-19 outbreak, demand for talented and trained programmers and developers is still high, and it will likely keep rising as companies in every industry adapt their business models to a more remote world.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

Following its dominance as a provider of silicon for smartphones, Qualcomm is eager to replicate that ubiquity with not only processors for augmented reality headsets but also reference designs to give device makers a head start.

As the year comes to a close, we've invited some of the leaders of the AR industry to take the time to look back at the progress the AR industry has made while looking forward to what's ahead in 2020. A report on the top apps of 2019 — and the decade — also offers some insights on the progress and direction of mobile AR.

After stealing the show at the HoloLens 2 launch and starring in Qualcomm's unveiling the Snapdragon XR2, holographic video conferencing app Spatial has landed a leading role in Magic Leap's second act with the enterprise segment.

As far as HBO is concerned, it's not augmented reality — it's Snapchat. The premium cable network is leaning hard on Snapchat's AR magic tricks to promote yet another series, this time for the adaptation of Philip Pullman's His Dark Materials series of novels.

As one of the household brands in creative software, Adobe is now ready to lay its claim to the artistic side of augmented reality.

Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present.

Augmented reality enthusiasts who expected an AR hardware unveiling at Apple's annual iPhone launch event might not have to wait much longer.

It looks like Jaunt's pivot from VR to volumetric captures services for augmented reality experiences has paid off.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

Augmented reality has taken the advertising industry by storm, but the technology has a steep learning curve. Luckily for advertisers, Unity is here to flatten the curve a bit.

The ability to shift between virtual reality and augmented reality seamlessly on one device is a dream of many AR fanatics, but the execution is usually fairly buggy or underwhelming.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Already a dominant force at the box office, Marvel Studios appears intent on establishing itself as the ruler of augmented reality media as well.