First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

Apple's built-in search on iPhone is an incredibly valuable tool you shouldn't ignore or underutilize, and we're here to show you why. So, buckle in because this list covers hidden and lesser-known Spotlight features that will leave you wondering how you ever lived without Spotlight Search on iOS.
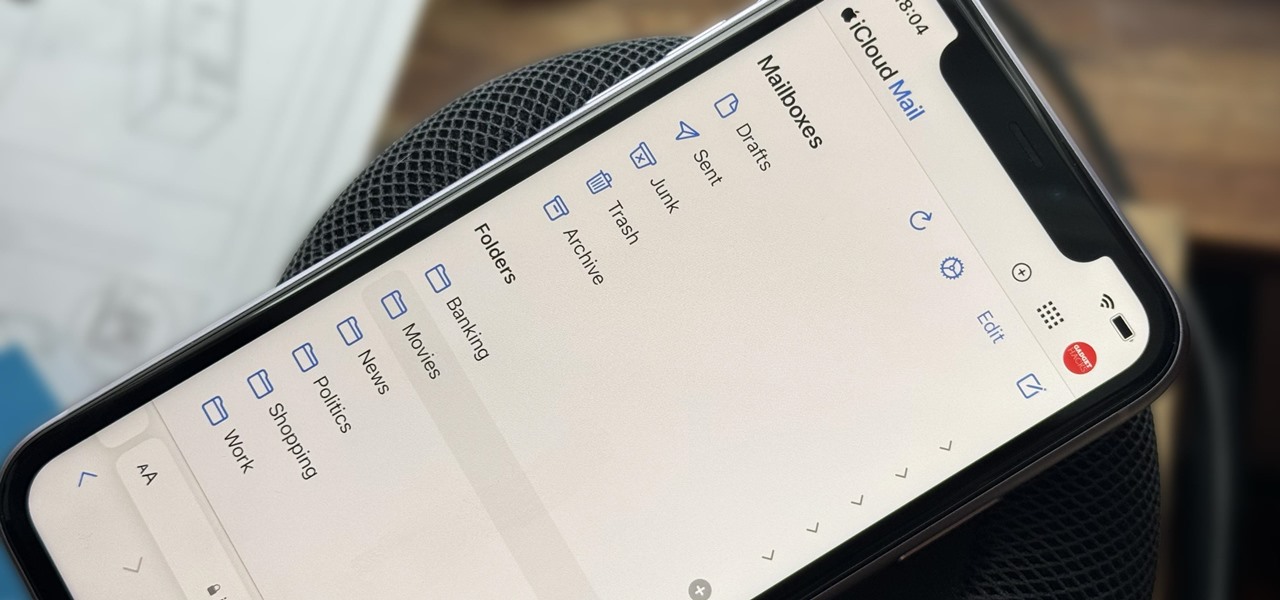
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro.

Many of the iPhone 15, 15 Plus, 15 Pro, and 15 Pro Max features were carried over from last year's models. Still, quite a few capabilities are exclusive to the 2023 lineup, and some may be worth the upgrade.

You may think your iPhone has all the features you could ever need or want, but that may change once you discover the features and services you're missing out on by residing in the United States.

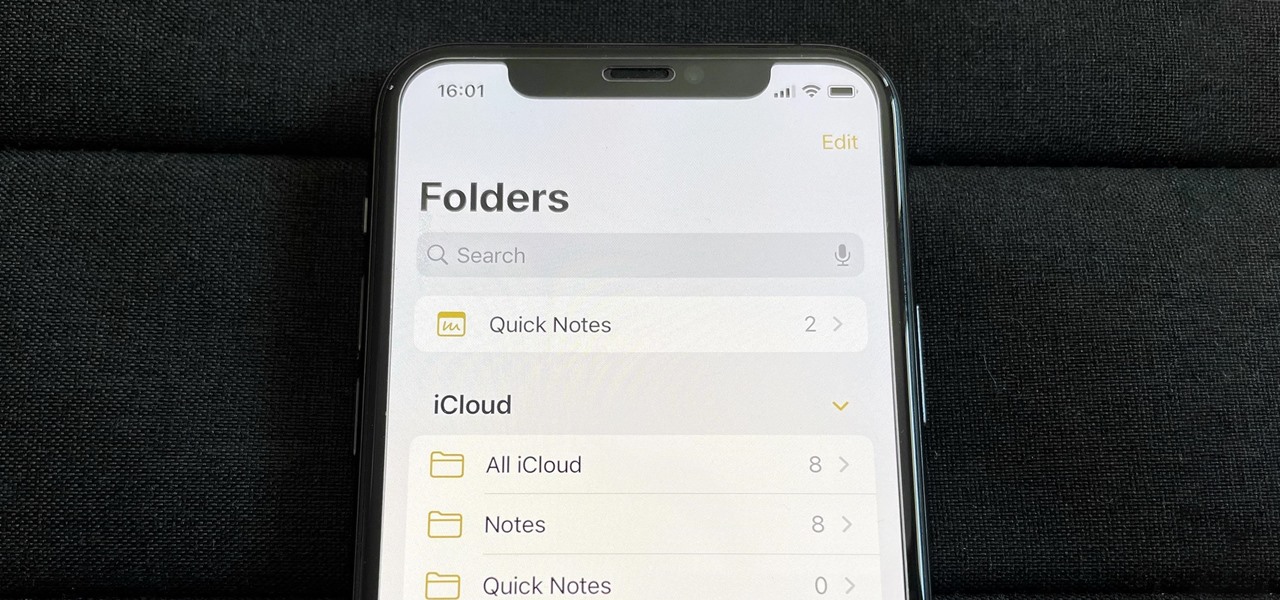
Apple's Notes app has an important feature many users overlook, yet it's arguably the most crucial thing you should use for all your notes synced across iOS, iPadOS, macOS, and iCloud.com. And Apple makes the feature much easier to use than years before, so there's no reason you shouldn't be using it.

You've decided you want to lose weight or build lean muscle. That's great! Now grab your smartphone. It's a valuable asset that can help you achieve your physical fitness goals, whether to improve your health or enhance your appearance, and I'm going to show you how.

If you use the Notes app on your iPhone and haven't updated to the newest software yet, you're missing out on some pretty valuable upgrades that improve smart folders, note security, collaboration, and more. So what are you waiting for?

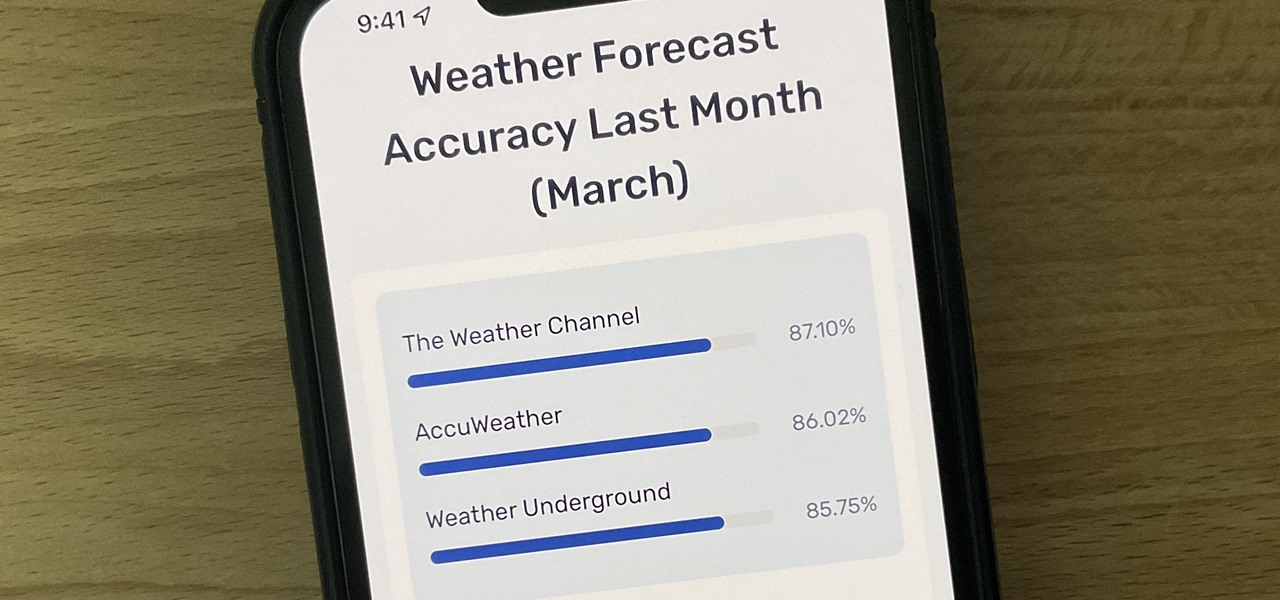
Not all weather sources are equal. When you're looking at the forecast, you hope that it's at least semi-accurate so you can plan the week and days ahead, but many sources are unreliable. And with the famous Dark Sky API shutting down on March 31, 2023, you'll need an alternative source of weather information if you use an app that utilizes that API.

Believe it or not, there are legitimate iOS apps beyond the App Store that you can install on your iPhone. Some of them even work for iPad, Apple TV, and Mac, and there are also benefits to using them over apps found in the App Store.

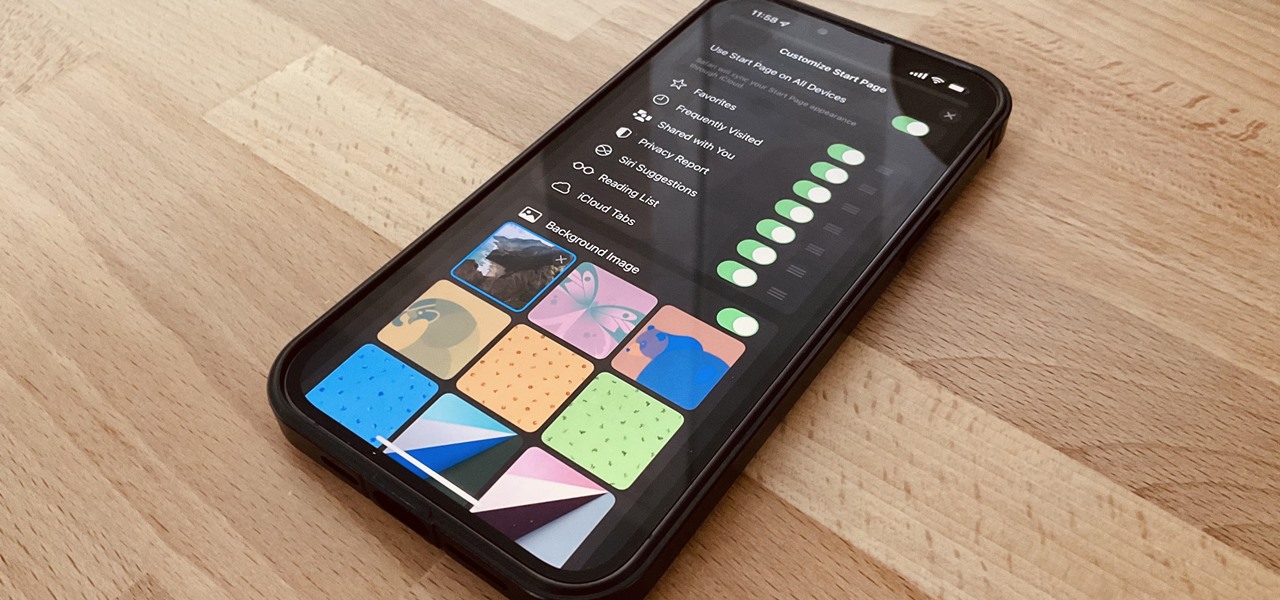
One of the biggest grievances with Safari on iPhone was always its lack of customization, and iOS 15's browser upgrades tackle that problem head-on. Apple added many great features, including Safari extensions, Tab Bar, and Tab Groups, but the most prominent feature caters to those obsessed with finding the perfect Home and Lock Screen look.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

Smartphones are vital travel companions. While you're on the go, they connect you with loved ones back home, help you find tickets and passes for tourist attractions, and make it easy to find your way through foreign roads — but even the most powerful smartphone could use help from travel accessories.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operating system. Using VirtualBox, the OS can be installed within a host to create a full-featured test environment.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

The private automobile has been an intrinsic part of our lives for around a hundred years. But over the last decade, car sharing has gained a very small but growing part of the mobility market. The more recent rise of companies like Uber and Lyft is witness to a more dramatic shift in mobility and car ownership. Private vehicle ownership to a transportation-as-a-service model has already started, and high capability SAE Level 4 vehicles will complete this trend.

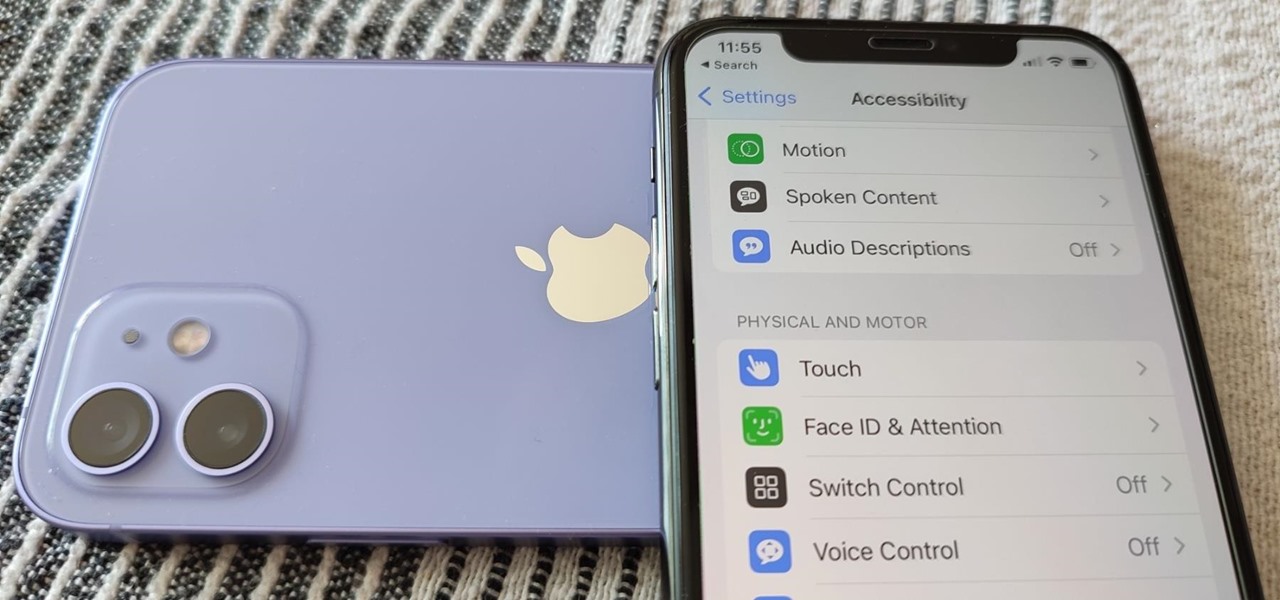
While it's not usually the first thing everyone looks at after installing a new iOS software update, I'd give the new accessibility features on your iPhone priority attention because there are some highly valuable tools that even users without disabilities can enjoy.

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.

Apple officially unveiled iOS 14 on June 22 at its first all-virtual WWDC. After months of beta testing, iOS 14 hit iPhones on Sept. 16, but that doesn't mean that Apple is done beta testing iOS 14. There will be new features to try out right up until iOS 15 comes out next year.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Keeping track of your money and expenses is one of the hardest things to do in life, not to mention one of the most hated things. But it's also one of the most important things. Making sure your finances are in order means keeping track of them. So watch to see how to balance a checkbook. The last thing you need is a bad check.

http://www.howtogeek.com/howto/19020/microsoft-desktop-player-is-a-valuable-tool-for-it-pros/

Want to keep your money and valuables safe while traveling abroad? Play it safe and outsmart thieves by placing your money, passport, jewelry and other expensive things in unexpected places. Sew a secret inner pocket in your pants, or if that's too much work, try cutting open a tennis ball, using empty film canisters, or simply placing a small amount of money in a spare wallet while your real wallet is more concealed within your luggage or purse.

This prank starts with a small plexiglass box (about 12in X 12in X 12in) with a round hole in the top big enough for someones hand/arm. Next, Knoxville goes around collecting the other cast member's valuables (car keys, wallets, phones, etc.) and places it in the box. The kicker is, the box is filled with scorpions. A scorpion sting won't kill you, but who the hell wants to get stung by a scorpion? Knox can then look on in laughter as they try to get their valuable out of the box.

All-Star Harold Reynolds shows the proper techniques for stealing, running the bases more effectively and mastering the base paths! Baserunning is a valuable skill for earning runs and stealing bases. Steal and run the bases with Harold Reynolds.

Water leaks weaste too much of our water. The amount of water you use is measured by a water meter. Your water meter is a great way to check if your property is leaking valuable water. For more, or to get started checking for leaks with your own water meter, watch this water-conscious video how-to. Check your water meter.

As someone who suffered the indignities of an Oakland school education, I'm always thrilled to hear about education reforms that take place and are successful. In this video, you'll get to hear about the program that lets Oakland high school students participate in rooftop gardening and learn valuable skills. And recognition of vegetables other than French fries.

Keep your dog from chewing. Puppies chew because they are teething, bored, or curious. It's up to you to protect your valuables. Give your dog a toy to chew. Keep your dog from chewing.

Entrepreneur Jason Fried is co-founder of 37signals, a successful Chicago-based software and design firm that has doubled its sales every year for the past decade. Although Fried has a degree in finance, making money isn't a skill he picked up in the classroom or a book. Practice makes perfect, and Fried's experience has taught him that excelling at making money is separate from the product or services provided. Understanding the buyer and experimenting with price models are two of Fried's ke...

Sounds like an odd bragging right, but hold your horses, artist Hannes Langeder's handmade Porsche is pretty damn interesting.

Nolan's Express Tips: Hall of Famer Nolan Ryan describes how he learned to throw his change-up. Pitching legend Nolan Ryan developed his change-up out of necessity. He describes the challenges and how he made it a valuable pitch to throw. This is an MLB official pitcher's lesson to bring your baseball game to pro level. Throw a change-up pitch with Nolan Ryan.