The Google Play Store exists so you can download as many apps as your heart desires (and as your memory can hold). Sure, you may only use them once, but it's your choice—and isn't that what life is really about? With that said, the Samsung Galaxy Note 2 already comes with a ton of preloaded apps from Google, Samsung, and your device carrier, like Yellow Pages and Google Earth—both of which I never use. So why is it that Android won't let me remove or uninstall them?!

Rooting your Samsung Galaxy S4 has many advantages; theming, free wireless hotspots, deleting system apps, and generally being ahead of the curve when it comes to updates. It's also great for simple things like centering your clock or freezing apps.
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.
It's all about widgets. Widgets are one of the most important features on an Android phone—they can provide valuable information at a glance and are easily customizable.

While becoming the next Mark Zuckerberg may be out of reach for someone just getting introduced to code, the skill has never been more valuable. Just understanding basic programming language is a great thing to put on your resume, and if you know how to code, you’re golden. Software developers and programmers have been the most resistant to the recession, as jobs in the tech industry continue to grow.
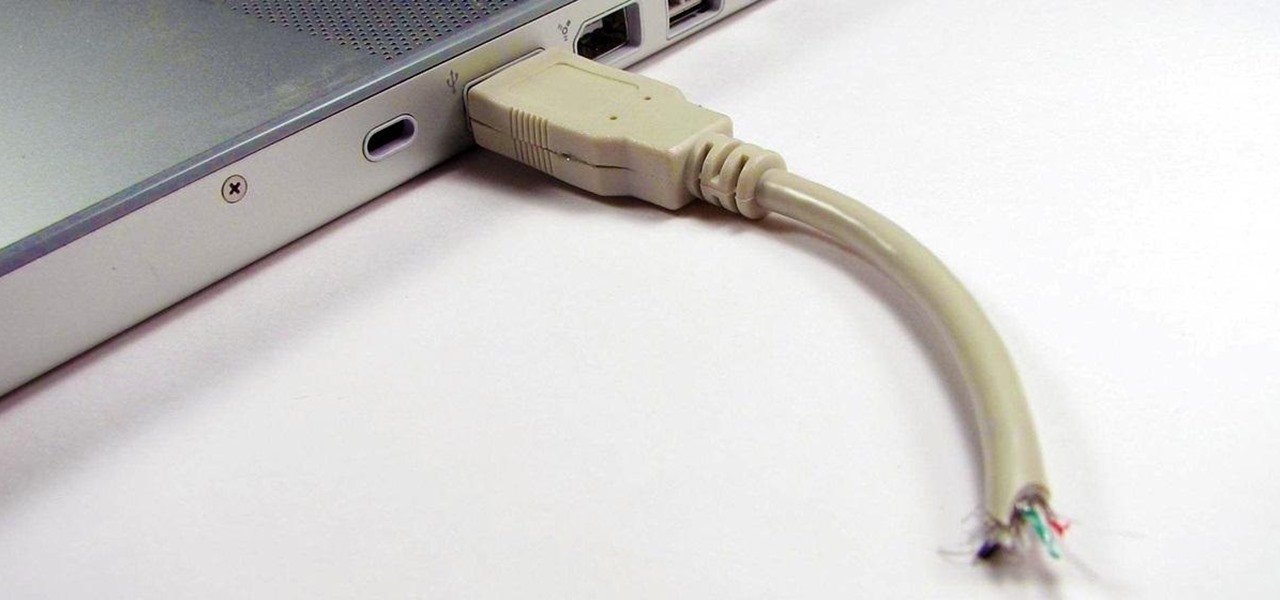
Having a flash drive is more or less a must, but the biggest downside is that they often get stolen, and it's not hard to figure out why. They're small, so they easily fit into pockets, and a lot of people store valuable information on them. Want to pretty much guarantee no one takes yours? Disguise it as a broken USB cable like Windell Oskay of Evil Mad Science Labs so it just looks like a piece of junk to would-be thieves. The materials are pretty simple: a flash drive (the smaller the bett...

It used to be that you only had to worry about maids rummaging through your belongings in your locked hotel room. But now anyone with 50 bucks of hardware and some programming skills can hack their way in—as long as it's locked by keycard.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

Thanks to a growing demand for talented and trained leaders who can inspire teams and innovate new products and services, there's never been a better time to work as a project manager. Whether you're interested in joining the ranks of a Fortune 500 company or working independently, project managers command high salaries and enjoy unparalleled opportunities for advancement.

Wherever life takes you, knowing how to successfully manage both large-scale projects and teams will undoubtedly serve you well. Whether you're eyeing a promotion at work or looking to switch to an entirely different field, having the skills to innovate products, inspire people, and solve problems will make you stand out to your current and future employers.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

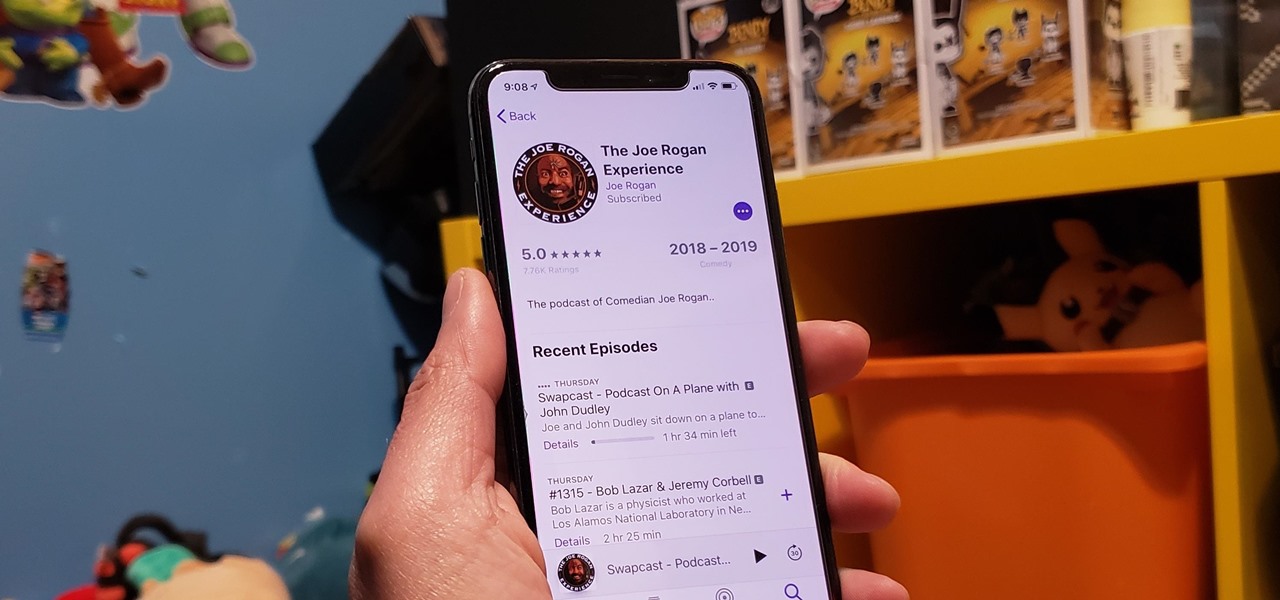
Ratings and reviews apply everywhere, from a restaurant you want to try to a new camera you're thinking of buying and games you might want to play. Podcasts are no different. Reading reviews of shows can help determine which are worth listening to, and your opinion is valuable to other people too. In Apple Podcasts, there are a few different ways to read, rate, and review shows.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

While many retailers have introduced try-before-you-buy features in their apps, Walmart has gone in another direction by bringing shoppers an augmented reality tool to help them compare products they want to buy.

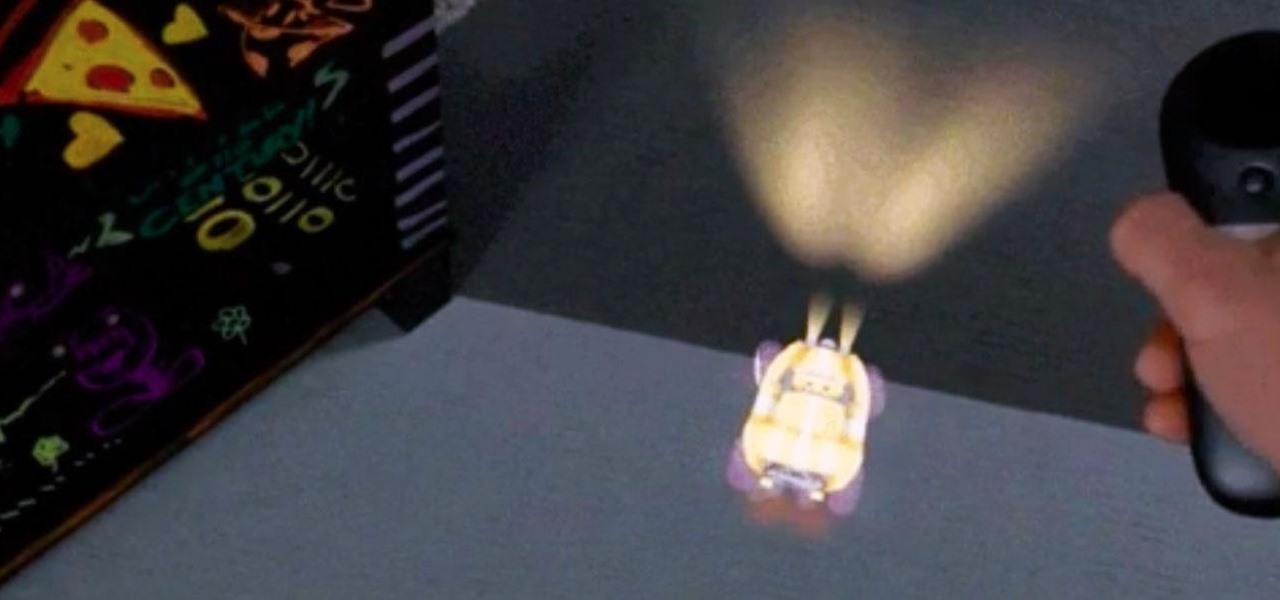
The long and slow road toward the actual release of the Magic Leap One appears to be accelerating, with a couple of new demonstrations of how the system works revealed in this week's creator's portal updates along with the company's developer documentation.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

The availability of space for filming immersive content has just gotten bigger with the launch of Innovation Studios by Sony Pictures Entertainment.

For those times when we need music grouped together for a specific task, we have playlists. Playlists are the next natural step after mastering your library and radio stations. While you've probably been an All-Star of curating playlists since your mid-90s mixtapes, Google Play Music has some pretty neat features that are going to really Smash your Mouth.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

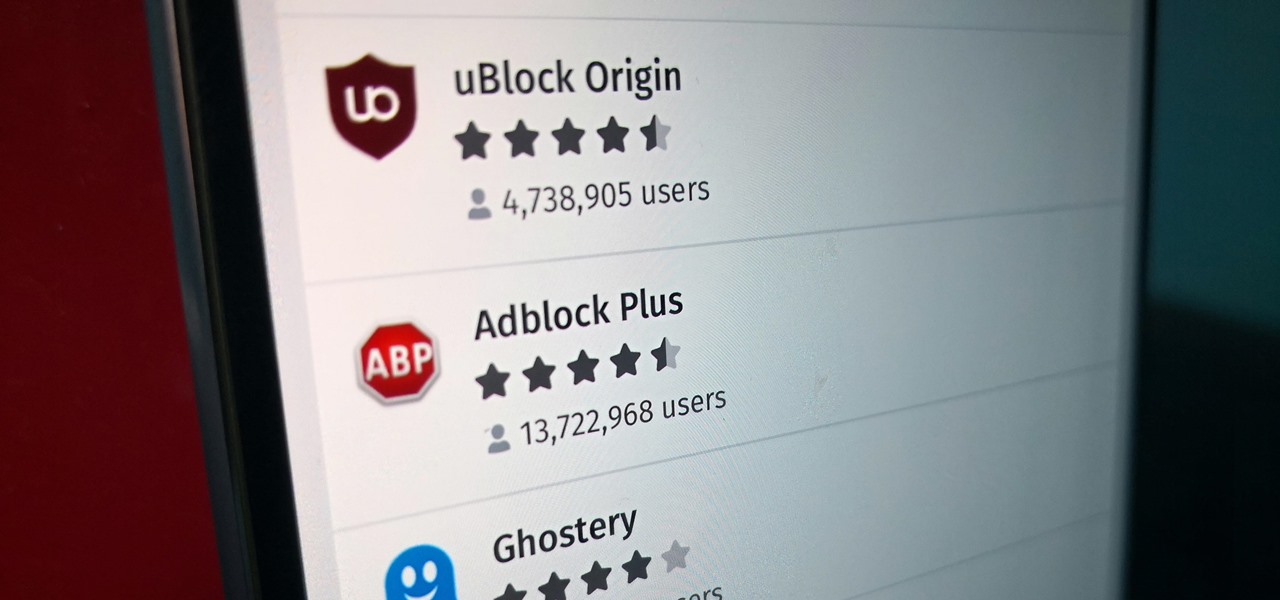
Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add features without having to upgrade the entire app.

A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union.

When Apple announced the iPhone X, 8, and 8 Plus, they had a laundry list of new features to talk about. They discussed the improved camera, the new screen, wireless charging, and many other things, but they curiously failed to mention that they just matched one of biggest features Android has touted over Apple for years — fast charging.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

If you've ever seen me glued to my iPhone, huddled on the corner of the 23rd St subway station fidgeting with my stupid hot pink nails trying to Instagram Story, then now you are about to find out exactly what I've been doing.

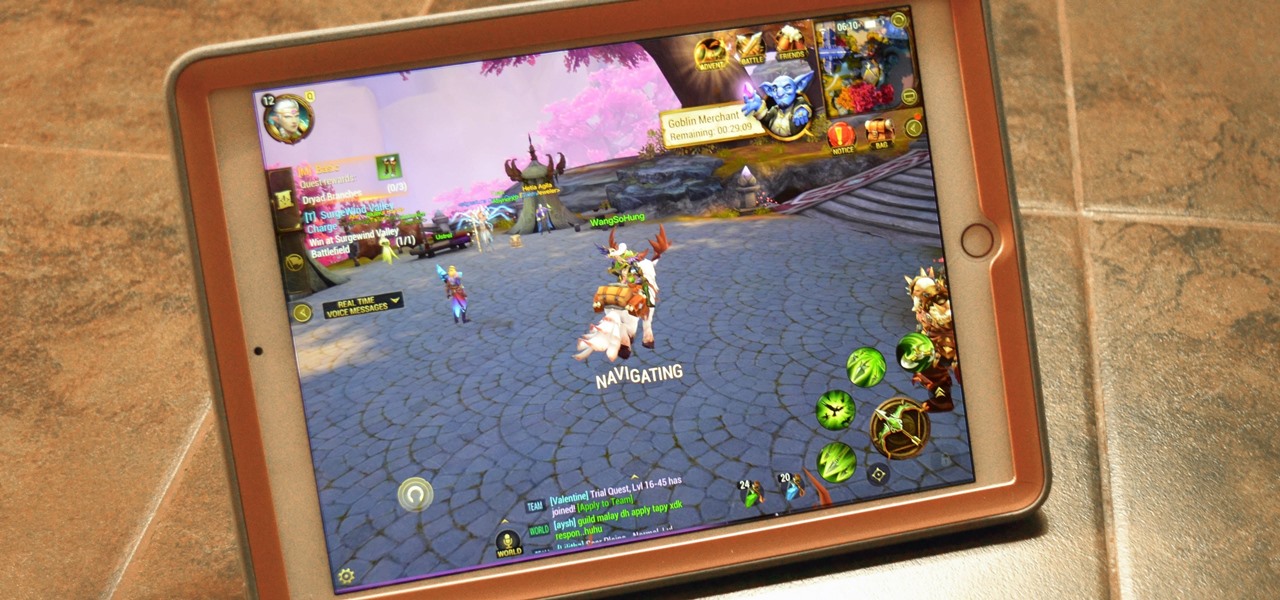
The world of mobile gaming is flush with MMORPGs that entice players with console-quality graphics and gameplay, intense co-op dungeons similar to World of Warcraft, and epic loot that'll give you a leg up over your competition. While there are games like Order & Chaos that nearly match PC-based RPGs, most simply fail to measure up. But the latest entry in this genre, Crusaders of Light, may finally get players to ditch their computers for iPhones and iPads to get their online RPG fix. Crusad...

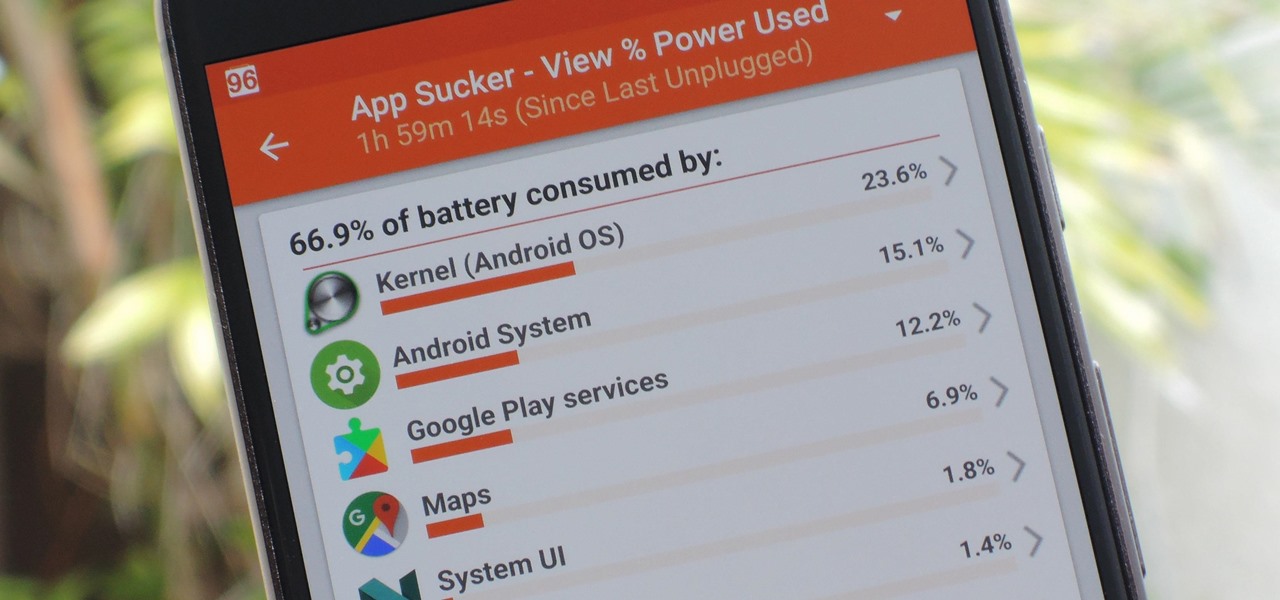
Figuring out exactly which apps on your phone are eating through resources and battery life can be a difficult task. Though some information can be found in Android's battery menu, the charts and graphs provided here pale in comparison to what's offered by the GSam app. If you configure this app properly, it provides deep insight into battery, CPU, and data usage.

We know your time is valuable to you, so starting this week — and continuing every Wednesday — we are going to release weekly Dev Reports that quickly highlight important news and updates that augmented and mixed reality developers should know about.

Dynasty Warriors has finally been unleashed on the world of mobile gaming. The latest installment in the popular series is called Dynasty Warriors: Unleashed, and it sends you rampaging through armies using a variety of devastating attacks, all while collecting and upgrading over 80 unique characters from the Dynasty Warriors series. Each offer their own unique abilities, which lets you create the ideal team to take on the seemingly endless hordes coming your way with cold, cruel efficiency.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Koji is a culture made up of a certain fungus (mold) called Aspergillus oryzae, which has been used to ferment rice and soybeans in Japanese, Chinese, and Korean kitchens for centuries. Koji can actually have other involved fungi, but Aspergillus oryzae is the most common, and therefore the names can be used interchangeably. Its end purpose is to enhance the flavor of items like soy sauce, sake, and miso.

Collecting Pokémon in Pokémon GO is only half the fun. Once you've reached Level 5, it's time to get your Pokémon ready to do battle with other Pokémon. This is where Gyms come in.

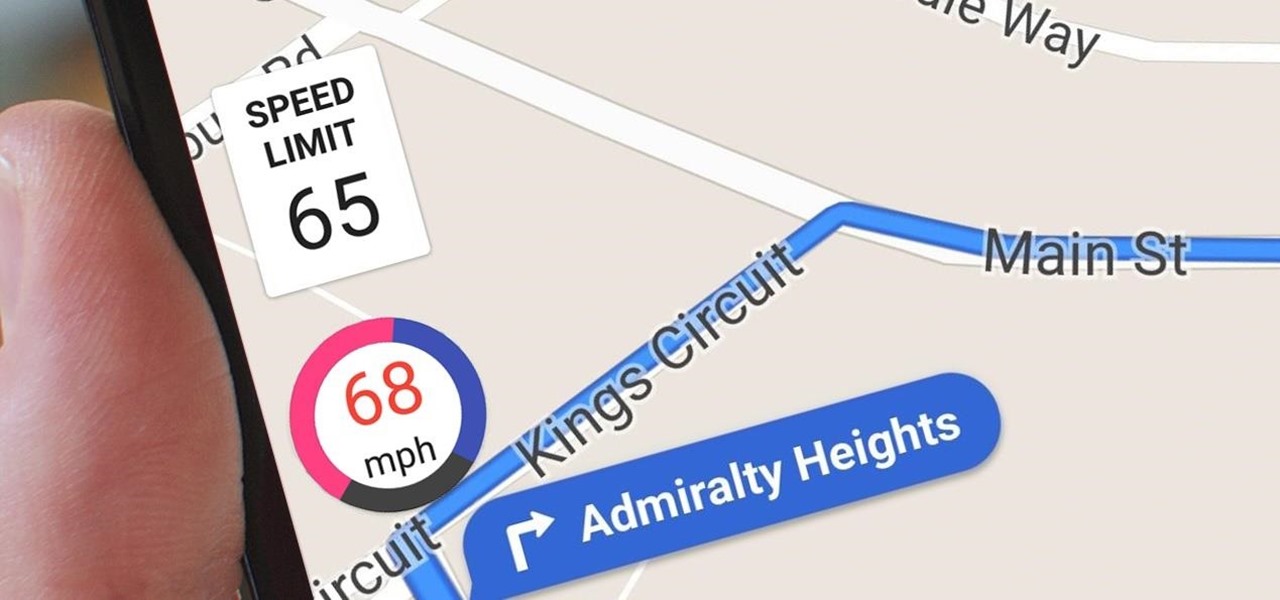
Google Maps does a lot of things well, but one feature it's always been lacking is an on-screen speedometer. Well, now you can add one with Velociraptor, and you can even set it to alert you when you're traveling above the speed limit.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

For the past couple of years, random internet dwellers have embarked on an ambitious quest to see just how useless a box can be in hopes of earning sweet, sweet internet points. Welcome to the world of useless machines.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

SentrySafe puts all sorts of measures in place to protect your valuables and important documents. This particular SentrySafe has an electronic lock, four 1-inch bolts to keep the door firmly in place, pry-resistant hinges, and it's able to withstand drops of up to 15 feet. That all sounds great, until you find out that you can open this safe—and pretty much every safe like it—in a matter of seconds using only a magnet. A rare earth magnet, to be precise.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.