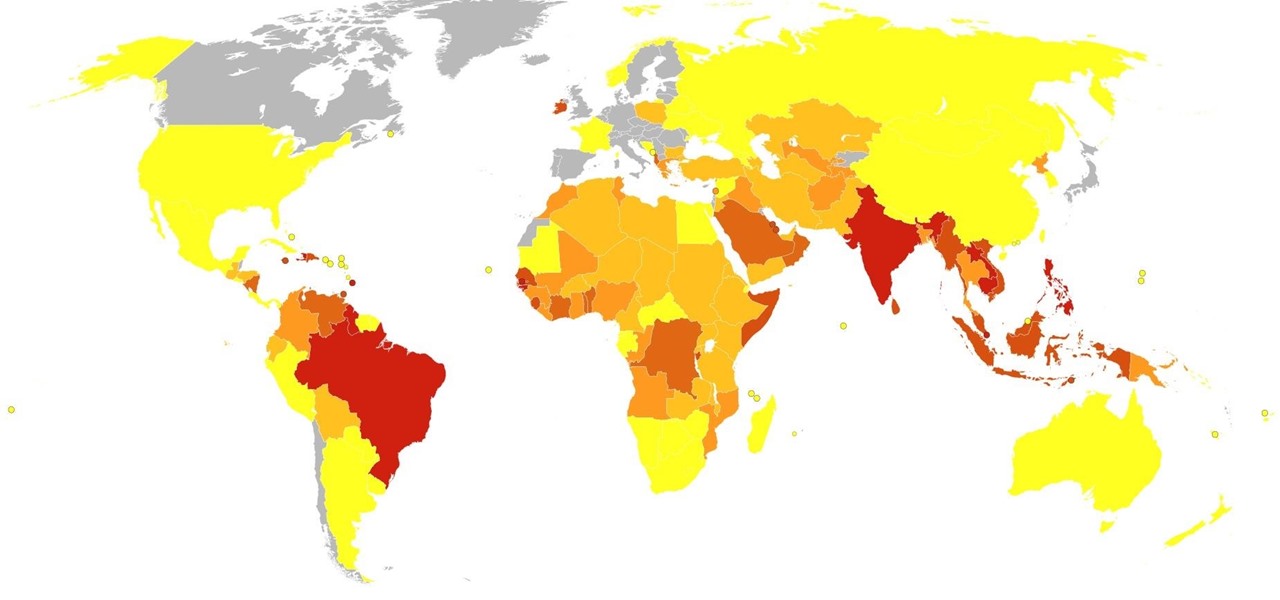
Dengue fever is a danger to anyone living or visiting tropical or subtropical regions. It can be hard to detect the infection in its earliest and most treatable phase, especially in children. Luckily, new research highlights better techniques for triaging the disease in infected children with more severe symptoms, potentially saving lives.
This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

You may have heard that Samsung Push is an incredible service that all Android users absolutely love. For one, Push provides extremely useful notifications for Samsung apps to assist you in all aspects of your life.

We're year-round pesto eaters. We eat pesto outdoors in the summertime on a light pasta with a glass of rosé. We eat pesto in the wintertime by the fire atop a bowl of soup with a warm mug of tea. We eat pesto with scrambled eggs for breakfast, pesto-slathered sandwiches for lunch, and baked pesto chicken for dinner.

You can put spices in a scramble or fry an egg in bacon fat, so why poach eggs in just plain water? Water doesn't add any flavor whatsoever, so you're wasting a valuable opportunity to give your poached eggs more oomph—an extra important step if you're not frying your poached eggs afterward.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Sometimes the best way to hide things is in plain sight. Whether you're trying to sneak some medication past security at a concert with a zero-tolerance policy, or you're just worried that maybe Omar comin', YouTuber MrGear has a clever way to put your mind at ease.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

Back in the days when June Cleaver was our role model, stay-at-home moms eagerly greeted their offspring's arrival home from school with fresh-baked cookies. But in the current vernacular, "Ain't nobody got time fo' dat!"

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

In my opinion, there is no candy greater or more timeless than Sour Patch Kids. They're the ultimate treat: sweet and refreshing, yet sour and tangy. These contrasting flavors are what make Sour Patch Kids perfect for the people of all ages—especially your kids. So let's make dishes that incorporate this awesome candy into your cooking rotation!
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

The other day I was doing the math on roughly how many eggs I eat each year. I estimated about 500. That's a lot of eggs. And, subsequently, that's a lot of eggshells to throw in the trash.

One of the great joys of cooking is taking the most basic of foods and preparing them in new and exciting ways. About two years ago, my wife opened my eyes to a delicious staple of Indian and Moroccan cuisine that is made in a very elementary way, the preserved lemon.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Many home cooks were taught never to press down on a burger as it cooks since that would ruin your all-beef patty by getting it to release the juices it needs to stay tender and moist.

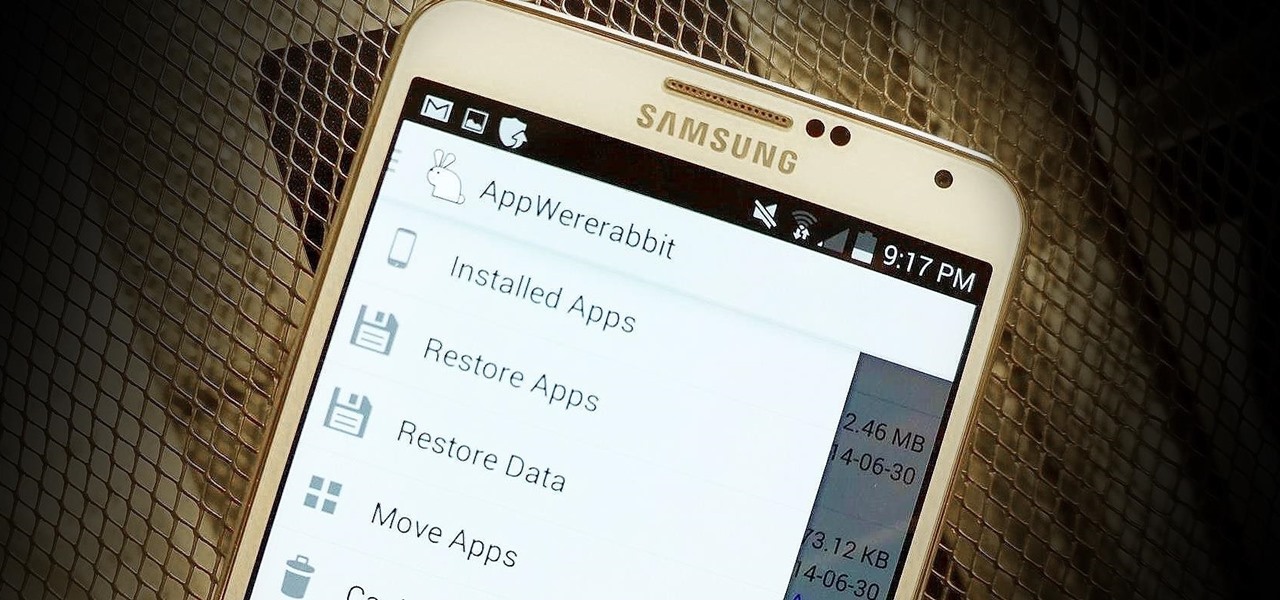
There are over 60-something Android apps cluttering my app drawer. While I'm constantly on the look out for new mods and apps to install, the default way of managing them is cumbersome and just feels unintuitive. I mean, who on Earth would wants to individually manage each app on their device?

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

Last week, we rolled out a major site-wide update on WonderHowTo, making it even easier to follow the subjects you're passionate about—and easier to share your creations with people who'll give you the kudos you deserve!

Learn how to care for fruit trees from a professional landscape designer. Our expert will educate on what tools you need and how to select and plant your new fruit tree. Learn valuable how-to tips for your fruit tree. See how to care for the tree by activating the soil. With all the luscious fruit dangling from the tree it can be an invitation for deer to come have a snack. Our expert will show how to protect your tree from becoming a treat. Pruning your fruit trees for maximum flowering and ...

Watch these series of antique collecting videos to find out just what qualities make these oil lamps valuable. Our antiquing expert discusses the rarity of different patterns and chimneys and how to determine the ways condition affects their value. She also tells you how to use your prize lamp safely and even the best way to display them. You may not get your three wishes, but you can still have a satisfying collection of lamps.