I love YouTube for listening to music I don't already have on my phone or in my iTunes library, but there is one very simple thing that you think they would've figured out by now—the ability to have your video continue to play outside of the app!

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

Want to learn a valuable skill? Well, just watch this video tutorial to see how to cross one eye or speak with an echo.

This retro informative video gives a general overview of a woman's menstrual cycle. A curious young girl asks her family questions about having a period, what's normal, what isn't, who gets one, who doesn't. While this video feels a bit dated, and eschews medical terminology, it offers some basic insight to that time of the month. Check out this video and learn how to understand the feminie menstrual cycle.

Long term power outages can be an inconvenience. It means that you no longer can heat or cool things. This how to video talks about how to protect your home from a long term power outage, or how to protect your valuables from power loss with a generator.

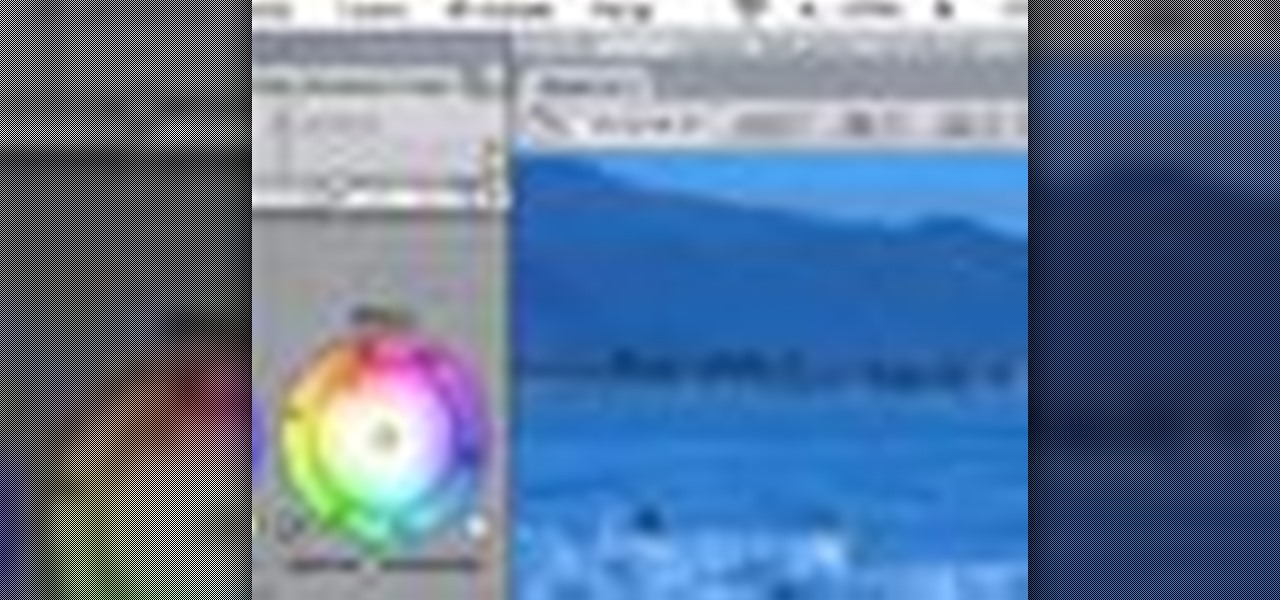
In this video i give you a small insight into the roll feature on the DJM-700 DJ mixer.

Learn how to adjust the brakes on your bike. This information is valuable to teach you how to do maintenance on your bike by yourself.

Steve gives his insight about weighing yourself. Your weight is going to fluctuate day by day.

How to pick plants and trees at a nursery

Disk space is a valuable commodity on your PC, and if you're running low, it's time to sell some of that unneeded property! This video shows you the steps to freeing up space on the hard drive of your Windows XP or Vista computer. There are many areas in Windows from which you can delete temporary files and hence, decrease your overall disk usage.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

In this podcast tutorial Randall Bennett and Adam Nielson look at Sony's Vegas, Color Correcting and insight into some expensive storage and how much Randall hates P2 cards (he really does.) Stay tuned and learn how to color correct in Sony Vegas, amongst other things.

Watch this instructional video in basic Buddhist Vipassana (Insight) Meditation. In this how-to video, there is an instruction on how to incorporate the meditation practice into one's daily life. Learn all about Buddhism & meditation.

Watch this instructional videos in basic Buddhist Vipassana (Insight) Meditation. In this how-to video there is a demonstration of mindful prostration - a preliminary Buddhism meditation technique which also creates a sense of respect for the meditation practice but, most importantly, it creates clear thought centred on the present reality.

This instructional video demonstrates basic Buddhist Vipassana (Insight) Meditation.

This video shows how to check your hosts file for spyware. This is a valuable tool, if your computer has spyware it can greatly affect the performance of your computer.

If your old clothes are of high quality and in good shape, selling them on consignment is an easy way to make cash quickly.

Getting a Rapunzel-like mane takes time, but you can speed things up with these valuable tips. You Will Need

If even the bats are intimidated by the clutter in your attic, it’s time to tackle the mess. Watch this video to learn how to clean out your attic.

No matter the field you work in, tech dominates every industry in 2020, and that means that you can always increase your earning potential by adding valuable coding skills to your arsenal. Coding can lead to dream software development career paths, lucrative freelance work, and it can be an impressive boost to your résumé. Now, you can learn these valuable skills at home with The Complete One Hour Coder Bundle, an offer at an unmissable 97% off its usual price, at just $34.99 (usually $1,200).

Google's feature drops for Pixel devices have added fun and useful new abilities, such as AR effects for Duo, Call Screen automation, scheduling Dark Mode, and Quick Access Wallet for Google Pay, that are exclusive to the company's line of smartphones.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.

While Magic Leap has gained attention for its ability to raise capital, the company (now with an actual product on the market) still faces an uphill climb against the titans of the industry.

Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Job interview success can be a difficult thing to measure. Is confidence a job-winning trait? Or were the interviewer's questions not answered as fully as they had hoped? Maybe you weren't sure how your big, happy smile went over with such a formal setting.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

Discover the art of Telescopic Pole Setup in this informative video, where we guide you through the process of preparing your pole for speedfishing. Whether you're targeting Bluegill, Crappie, Trout, or Perch, pole fishing stands out as one of the most effective methods to reel in a catch.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EQ Series Telescope to ogle the universe.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...