Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

If you ever had trouble trying to properly write a research paper then this quirky, 1950's style filmstrip movie will break it down for you, even if you're a dummy. The Oscar-worthy performances in this movie will help teach you valuable lessons when it comes to preparing and working on a research paper. The narrator in the movie will give you essential tips and strategies to guide you in the research paper writing process. The key things the movie will share with you are: (1) Choosing a topi...

Ramen noodles don't have to be just plain old noodles. Cheap meals don't have to taste cheap. Take Ramen noodles to the next level with some green onions, mushrooms, red bell peppers and more. Check out this video tutorial to learn how to rock out and make ramen noodle stir fry.
MAKE and Collin Cunningham brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

The come command is the most valuable training tool for your dog. Learn the importance of dog training and how to get your dog to come with this free dog training video series.

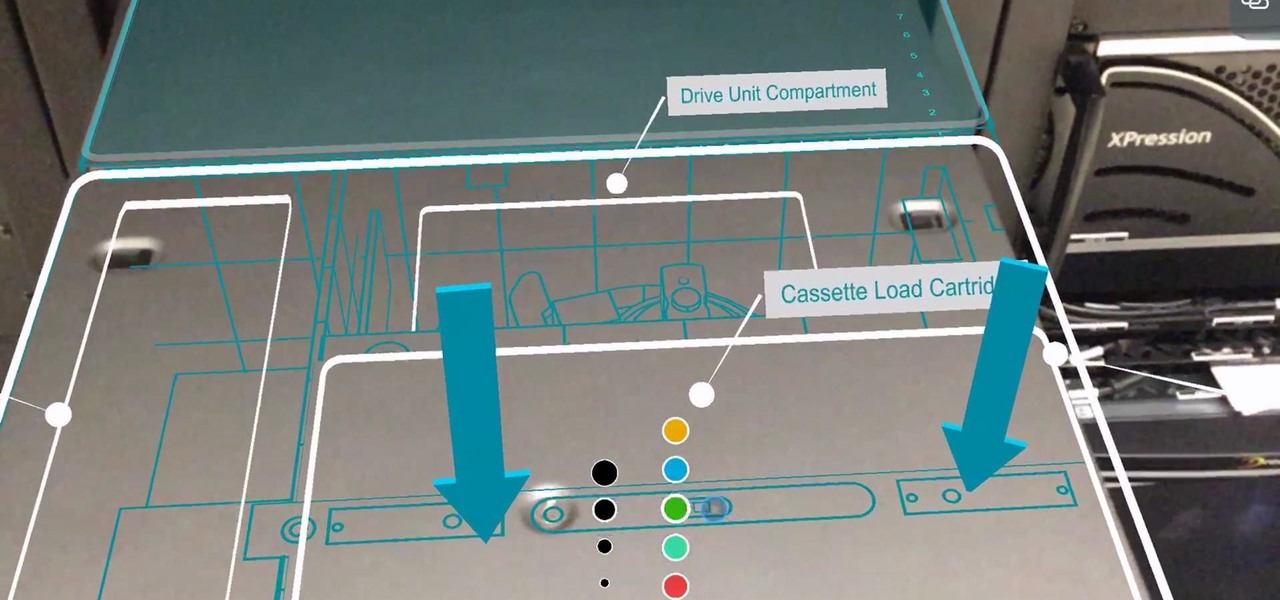
Enterprise augmented reality software maker Scope AR is bringing the powers of its two productivity apps together like the Wonder Twins into the form of a single app.

Despite the abundance of sci-fi titles in the iOS App Store, very few of these mobile games ever have the staying power keep us glued for more than a few hours. Enter Space Pioneer, an awesome space exploration game that soft-launched in Canada ahead of a worldwide debut. With a little spoofing, you can experience the game yourself right now.

EXPAND YOUR VISION: So many people don't achieve their goals and dreams in life because they don't have a big enough vision for themselves. The biggest enemy lies within. Picture and see yourself achieving your goals, becoming financially independent, making yourself more valuable to the market place, or losing that excess weight that you have always wanted to lose.

This is a fun project that doesn't take much in terms of time or resources. You can even make it out of your scrap fabric! Use whatever notions or embellishments you want to create a lovely, Victorian inspired pillow at home.

The massive offices that represent so much of the American economy are an ecological disaster. They aren't heavy manufacturing, but they use incredible amounts of paper, electricity, and other resources. This video will give you some tips for making you office more green, saving electricity and paper and making the Earth a better place.

In this tutorial, actor Shaun Pilkington offers his advice for choosing the best acting classes in Hollywood. LA is a town full of actors and there are many resources available, make sure you pick the best classes and become the very best you can be in your field.

These days it seems like budgets are on everybody's minds. Big or small, financial planning is an essential part of daily life following the latest recession. In this tutorial you will learn how to create budget resources, using MS Project 2007, that you can assign to your project to compare you actual hours and costs against your budget.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

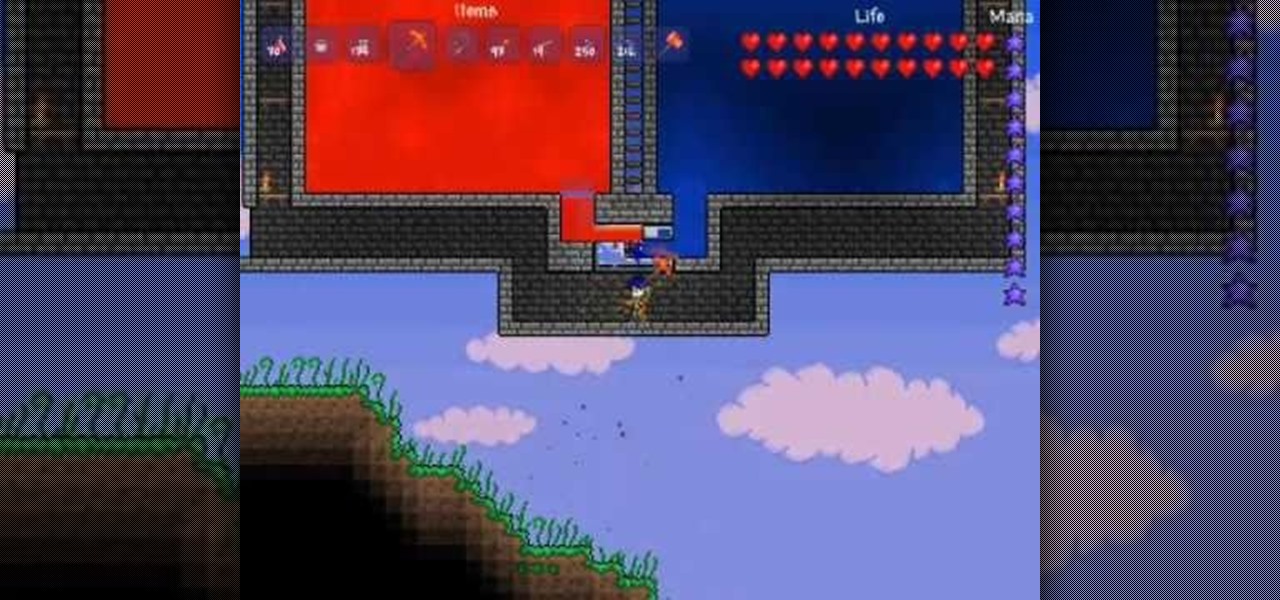
Take your creativity to the next level, build some incredible pixel art in your Terraria world. This video will show you how to build an 8-bit version of Luigi from Super Mario Bros. using common Terraria building resources. Throw a Mario party in your Terraria world!

In the world of Minecraft, style counts for a lot. Why get around by resource-expensive ladders when a water ladder will get you there just as easily? This gamer's guide presents a complete walkthrough of how to build both standard and stealth (i.e., invisible) water ladders. Note: Water ladders must face North or East.

Recycling things isn't nearly as efficient a means of conserving resources as reusing your waste material in it's current form. Enter this video. It will teach you how to make an awesome little trash can / waste paper basket out of perhaps the most appropriate material of all: old newspapers!

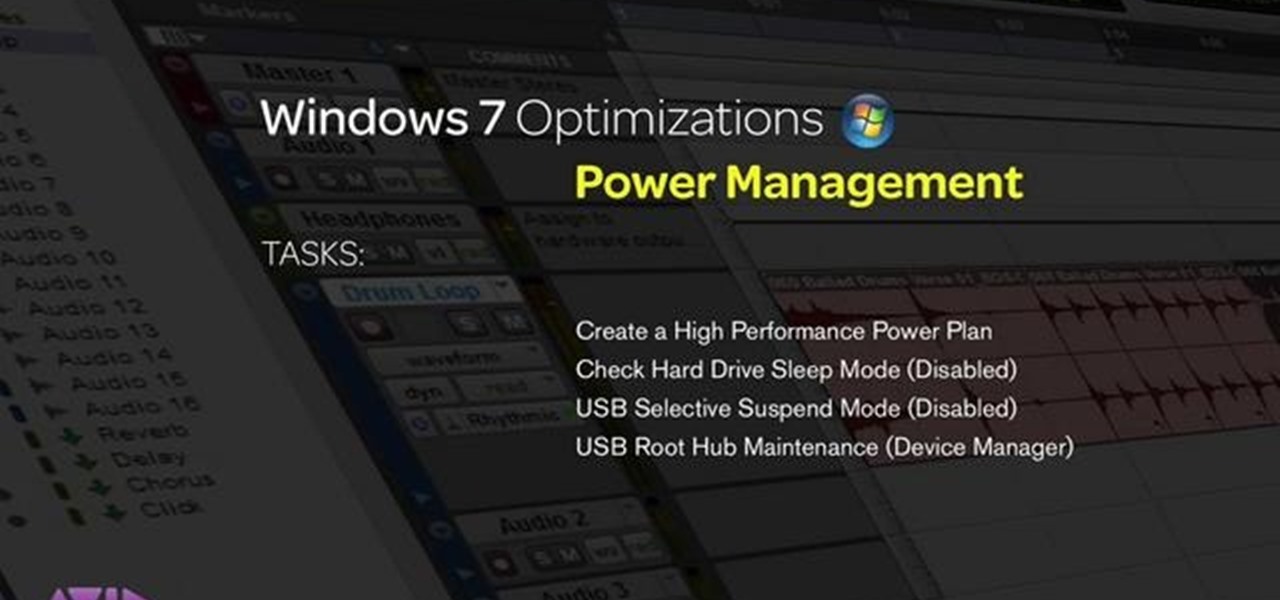
Pro Tools can be resource-heavy when it comes to running on your computer. This tutorial walks you through all the necessary steps so you can configure Windows 7 in just the right way to maximize the performance of Pro Tools on your computer.

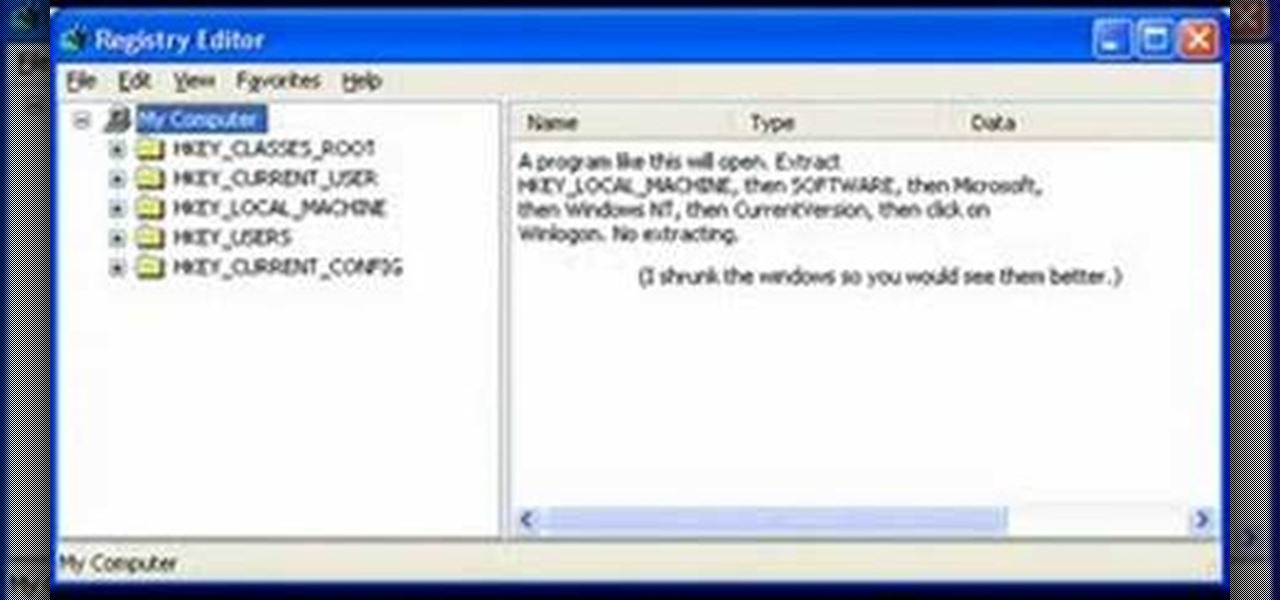
In this how-to video, you will learn how to change your start menu text. You will need resource hacker and regedit in order to perform this. First, open resource hacker. Click file and open. Go to 37, and click on 1033. Change 578 to whatever you want the text on the start menu to be. Press compile script. Next, save this file. Now, open regedit and go to software. Go to shell and click modify. Change the value data to the name of your .exe file, which should be saved in the windows folder. N...

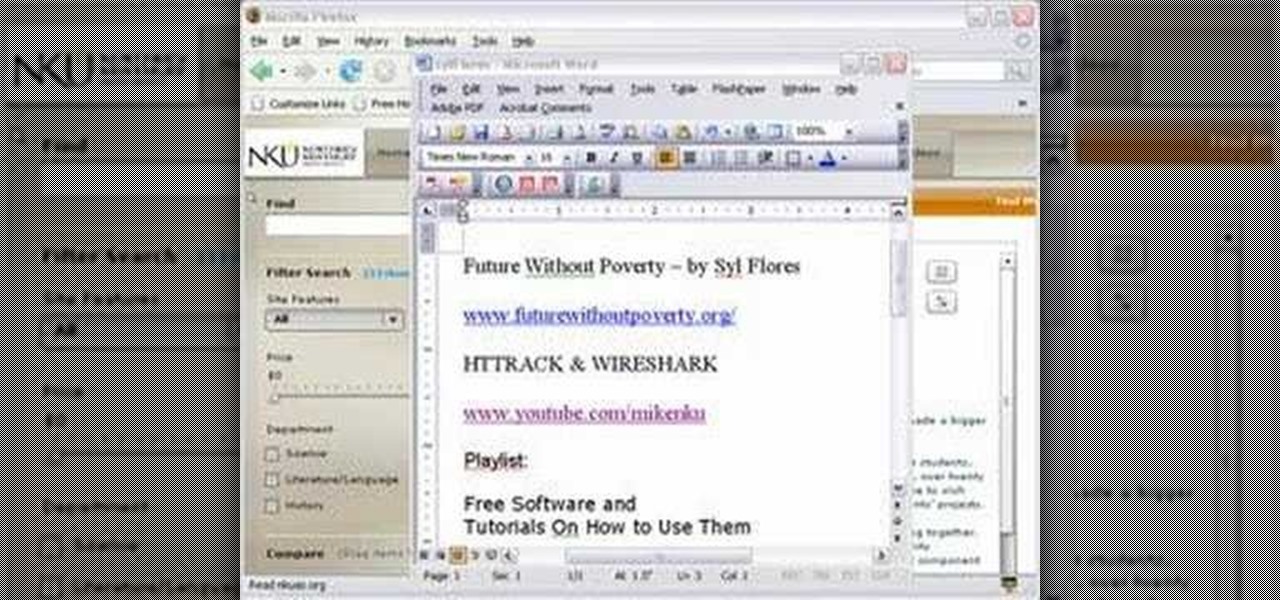
Mike Lively of Northern Kentucky Universtiy demonstrates how to grab a website's resources for reconstruction in Flex using HTTRACK and Wireshark. This tutorial is especially helpful for sites you want to grab that think they are very locked down and secure. All with the free softwares HTTRACK and Wireshark.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Where are all the caves? Let this video show you. Watch this Minecraft guide to learn how to find caves in Minecraft. Learn techniques for finding caves in your Minecraft world and start discovering new resources to use for crafting.

Have you found a dungeon in your Minecraft world yet? There are a lot of great items and resources in dungeons, so if you are having a hard time locating one, consider using the X-ray texture pack and the technique demonstrated in this video.

Watch this video to learn how to use Terrafirma to make a map of your Terraria world. If you've got designs for a constructions project but not a location, or you really need a certain resource, having a map will really come in handy.

Mushrooms and shooting stars are two essential resources in Terraria. If you'd like to be able to collect them at will, watch this video to learn how to use tunnels to set up a mushroom farms and how to use sky bridges to harvest shooting stars.

Obsidian is an excellent resource for crafting in Terraria. With enough, you can even build yourself a fine house. This video will show you how to set up an Obsidian generator using vats, grinders, and duplicators. This is expert Terraria crafting.

If you've been playing Terraria, you should check out this helpful video to learn how to use buckets for harvesting lava and turning it into obsidian. This is a simple, easy, way to farm obsidian in Terraria so that you can use it as a resource in crafting later.

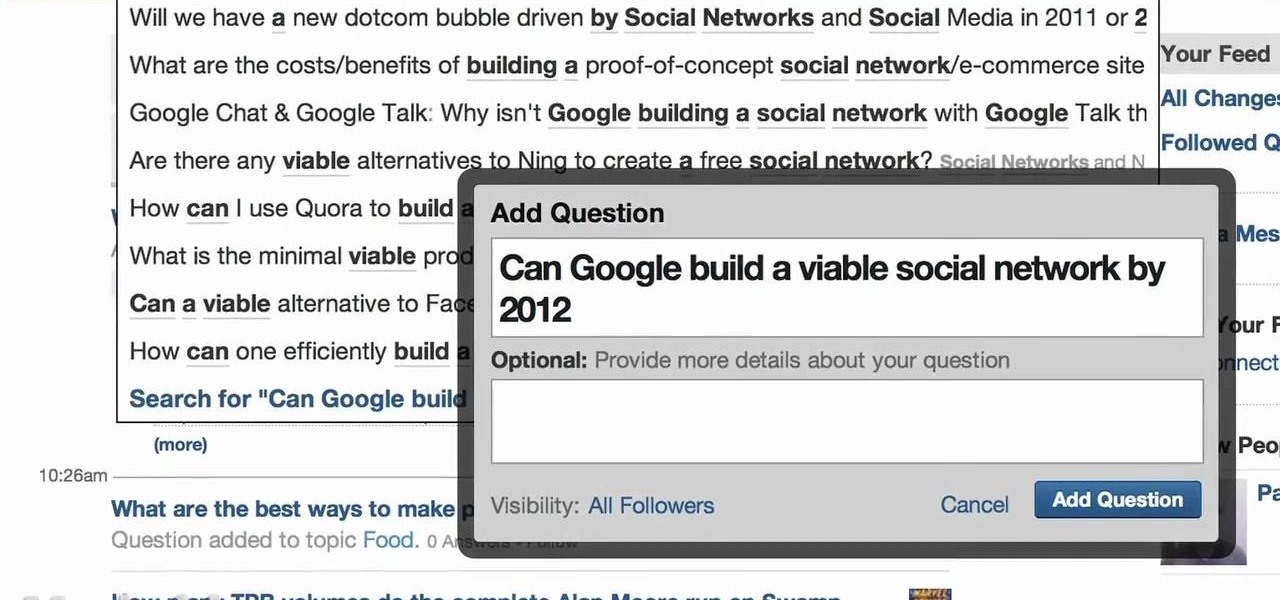
If you got a question that needs an answer, Quora.com is a great resource. You can pose your question to the community and have it answered by experts from many different fields. This video will show you how to use some of Quora's most helpful features.

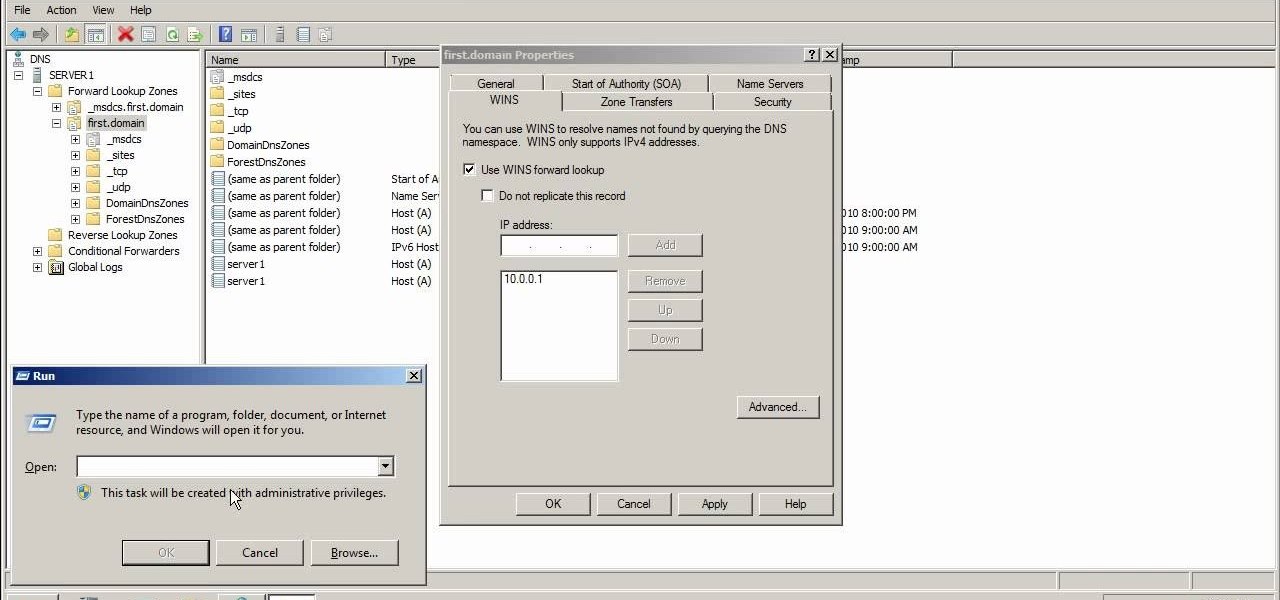
This video explains how to modify your DNS server to perform WINS lookups. Using Microsoft Windows Server 2008, you can perform WINS lookups across several networks which can resolve to a common resource. While Server 2008 cannot act as a WINS server, Server 2003 can.

In Minecraft, traps provide an easy and safe means of harvesting monster-specific resources. This gamer's guide will walk you through the construction of a simple fire trap. For complete instructions, watch the video!

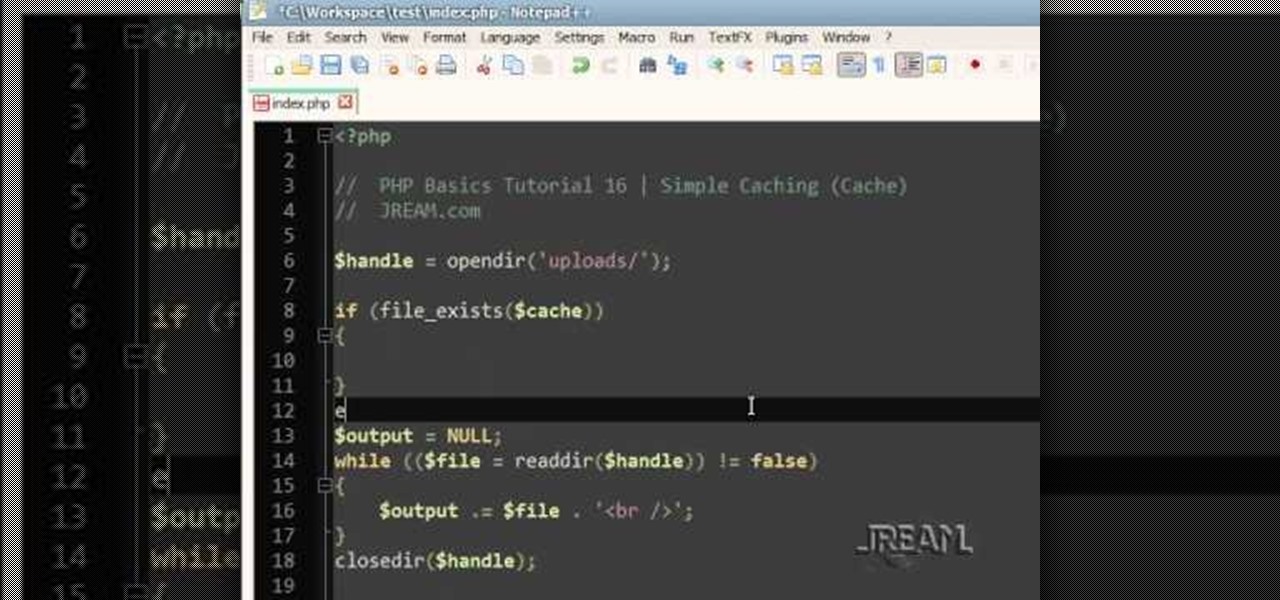
Sometimes server space can be an issue, especially when you're talking about costly actions such as iteration, file scanning, and numerous queries. In those instances it's often best to cache! This tutorial gives you a simple example which can help your site load faster and take less abuse.

In Minecraft, traps provide an easy and safe means of harvesting monster-specific resources. This gamer's guide will walk you through the construction of such a trench-style trap. For complete instructions, watch the video!

In Minecraft, traps provide an easy and safe means of harvesting monster-specific resources. This gamer's guide will walk you through the construction of a simple lava trap. For complete instructions, watch the video!

In Minecraft, traps provide an easy and safe means of harvesting monster-specific resources. This gamer's guide will walk you through the construction of such a trap. For complete instructions, watch the video!

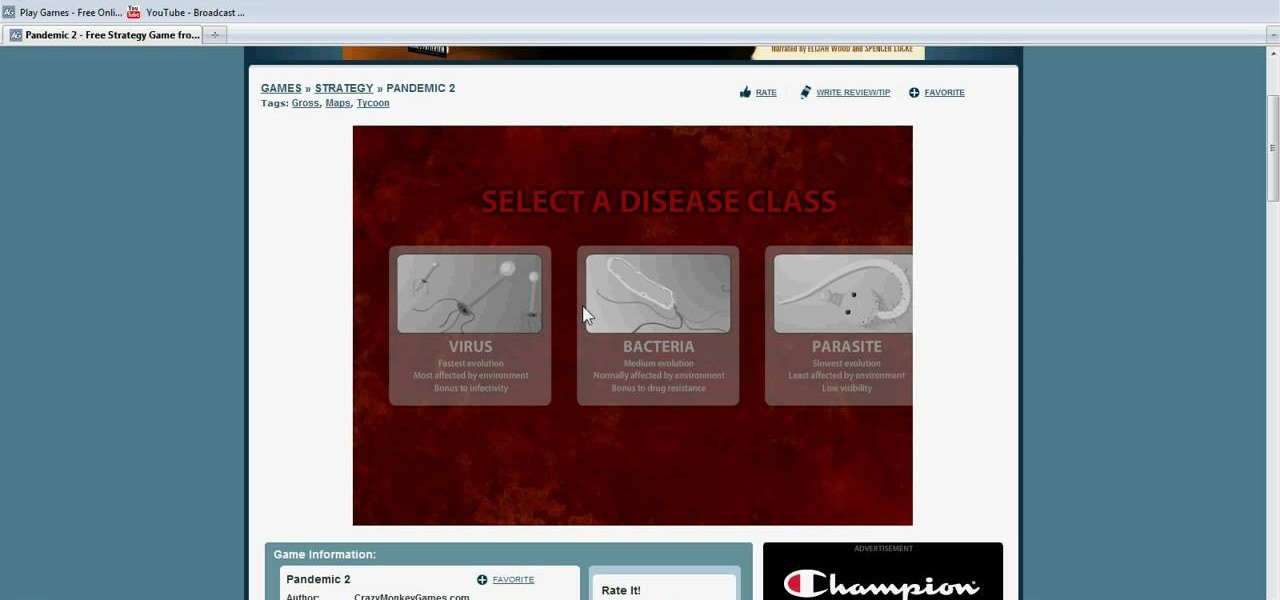
Pandemic 2 is a fun little game published by Addicting Games, and this tutorial shows you how you can hack the game using the Cheat Engine program. Give yourself more points, more resources or increase any stat you want by following this tutorial.

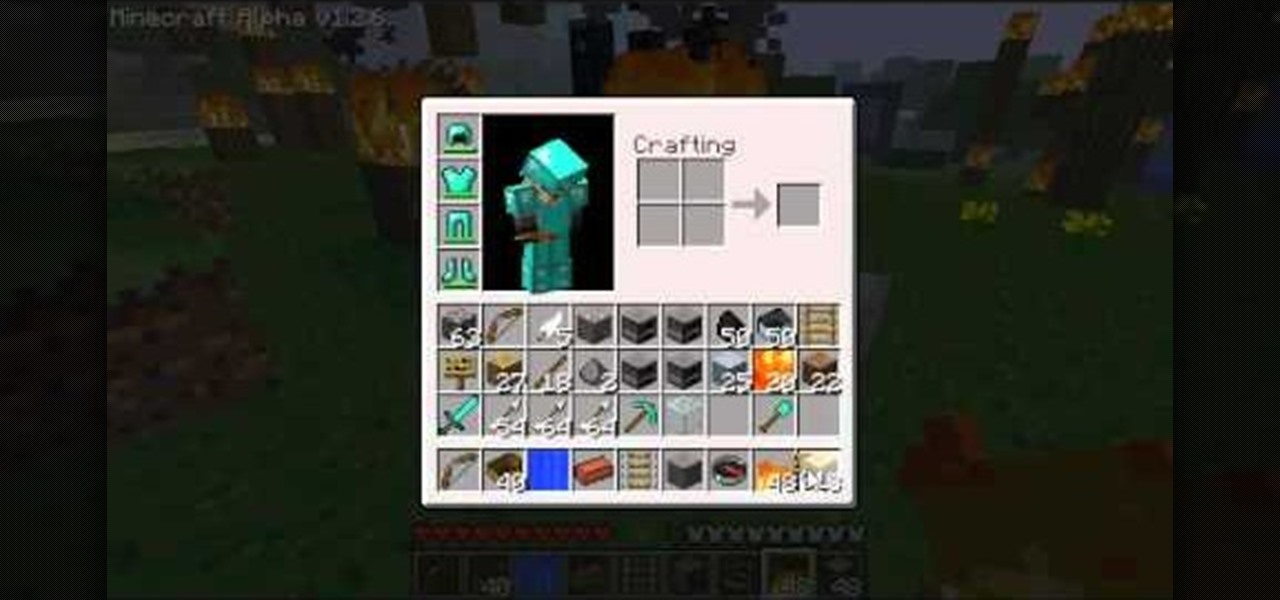
Don't want to use INVedit for more Minecraft resources? You can build a well to get infinite water, and a firepit that will keep burning for a long time. This short Minecraft tutorial shows you how you can accomplish both!

Want to find the most efficient way to spend your resources mining in Minecraft? This two part tutorial shows you how you can set up easy and efficient systems for mining the caves and mountains on your game of Minecraft.

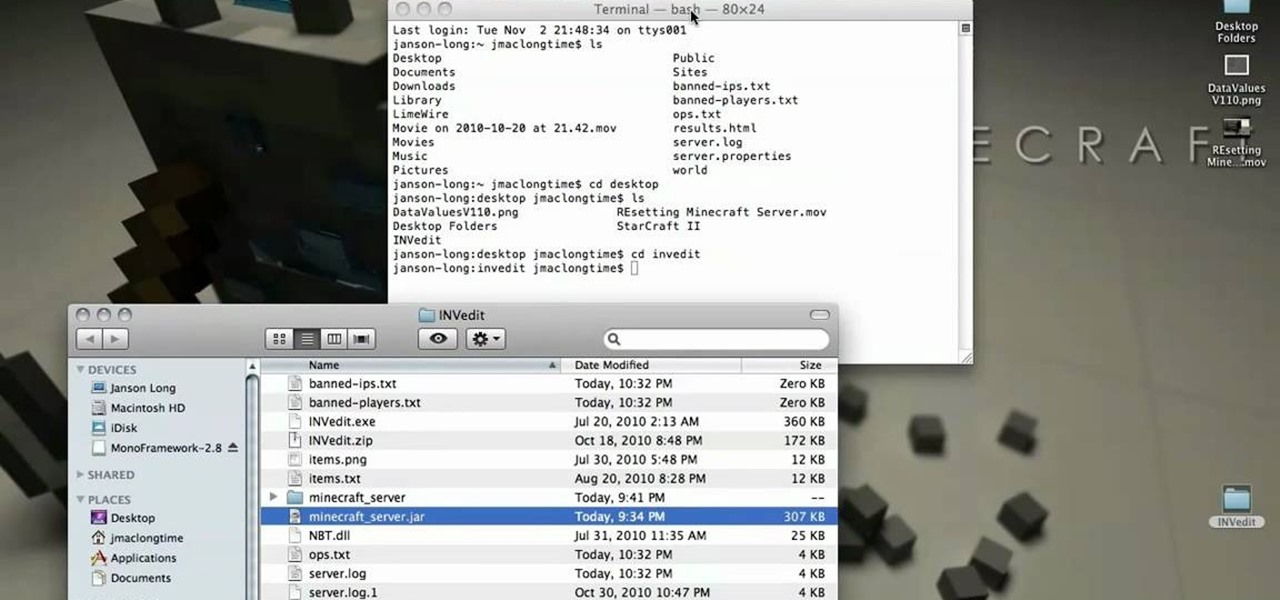
If you've already created your own Minecraft server, you can also set it up to launch with more RAM, making the game faster with more resources. This tutorial shows you how you can increase the amount of accessible RAM on your servers.

As if just mining and breaking up cobblestone wasn't enough, there's a way to generate an unlimited resource of them just by building a simple machine and using some water and lava. In this video you will learn how to create your own machine that will make an unlimited amount of cobblestone for you to harvest!

In this clip, you'll learn how to work with custom fonts when working in MS Silverlight. Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.