This video covers the construction and assembly of a decorative pencil holder. These make great gifts and are excellent for utilizing scrap. This video is for the more experienced woodworker, knowledge of tools is required. To apply a beautiful finish on the pencil holder, see the Wood Whisperer's finishing video on popping the grain.

Discussing the technique of cutting a turkey quill pen, with reference to the bamboo pen. These quills can be used to write calligraphy. Part of the Tools and Techniques of Calligraphy series.

The most basic of DIY jewelry-making tutorials. You'll need seed beads, a bent-tip eye needle, and a seed-bead spinning tool.

In this episode, The Shirtless Apprentice gives us some tips and information on how to use one of the most versatile and under appreciated tools in a videographer"s arsenal, the sungun! Matt compares two types of sunguns, incandescent and L.E.D., and weighs the benefits of each.

Corinne Bradd helps Kristy Clarke get to grips with the tricky art of quilling. Using thin strips of brightly coloured paper and a quilling tool, she shows how simple it is to coil gorgeous, dimensional floral motifs.

Citrus segments make refreshing additions to salads and desserts, but the bitter white pith and chewy membranes sometimes detract from the deliciousness. To make citrus segments -- sometimes called "supremes" -- the only tool needed is a sharp paring knife. Cut the top and bottom off the fruit, then carefully cut away the peel and pith, leaving as much of the fruit as possible.

You've found the perfect photo for your presentation but the background is the wrong color or worse, a cheesy image. Well, if you're creating your presentation in Keynote '08, you can just remove the unwanted background using the alpha tool! See how in this tutorial from Apple.

iMovie has a voiceover tool that allows you to add your own voice (or someone elses) as narration over your movie. This tutorial will give you tips on getting the best quality recording and then add it to your movie.

Watch and see how to use the cropping tool to crop and improve compositions of photos in this iPhoto tutorial.

Take better advantage of your Gmail tools -use aliases to organize your mail and forwarding to manage multiple email addresses and locations.

The golf lob shot is a handy tool to have in your bag. It's a real showman's shot and one which will really impress your mates, if you can pull it off. You need confidence and commitment to execute the lob shot with flair. Scott Cranfield gives you some simple tips to make it easier.

This video demonstrates how to run a scandisk in Windows XP. To do this, just right click on your c: drive and select properties, click the tools tab, hit check disk and click ok.

Illustrator CS2 has a great tracing feature called Live Trace. However, sometimes you may want to trace something and have a more artistic effect. With Illustrator's Pen Tool and the Gradient Mesh feature you'll be able to create the exact look and feel that you want.

The Clone Stamp Tool has been a long time favorite for most Photoshop users. However, trying to remove something that is on an angle or a different perspective is often challenging. In this video, Terry White will show you that by using the Vanishing Point feature you can remove images and add images with ease.

In this video you will learn to enhance a sunrise or sunset using Photoshop. Learn to use the sample tool and gradient to do the job. You won't believe how easy is til you watch this video!

Annoyed by a leaky or dripping faucet? Don't be intimidated by trying to fix it yourself. Here are the tools and step by step instructions to tackle it yourself.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

Imagine an Instagram feed filled with a wild array of vivid color. Beautiful right? But when you look at the photos in your iPhone or Android phone's albums, they're all just too dull to pull off that dynamic look. There's no doubt that colorful images are more eye-catching than dull ones, so how do you get your photos to overflow with vibrant color? The answer: Add it in post.

If cameras are a priority, one of the first specs to check on a new phone is the image stabilization. You've probably been told optical image stabilization (OIS) reigns supreme, but this isn't the case if you're taking a lot of videos. Instead, we would argue, electronic image stabilization (EIS) actually works better for video.

Developers in the augmented reality industry got a lot of love this week.

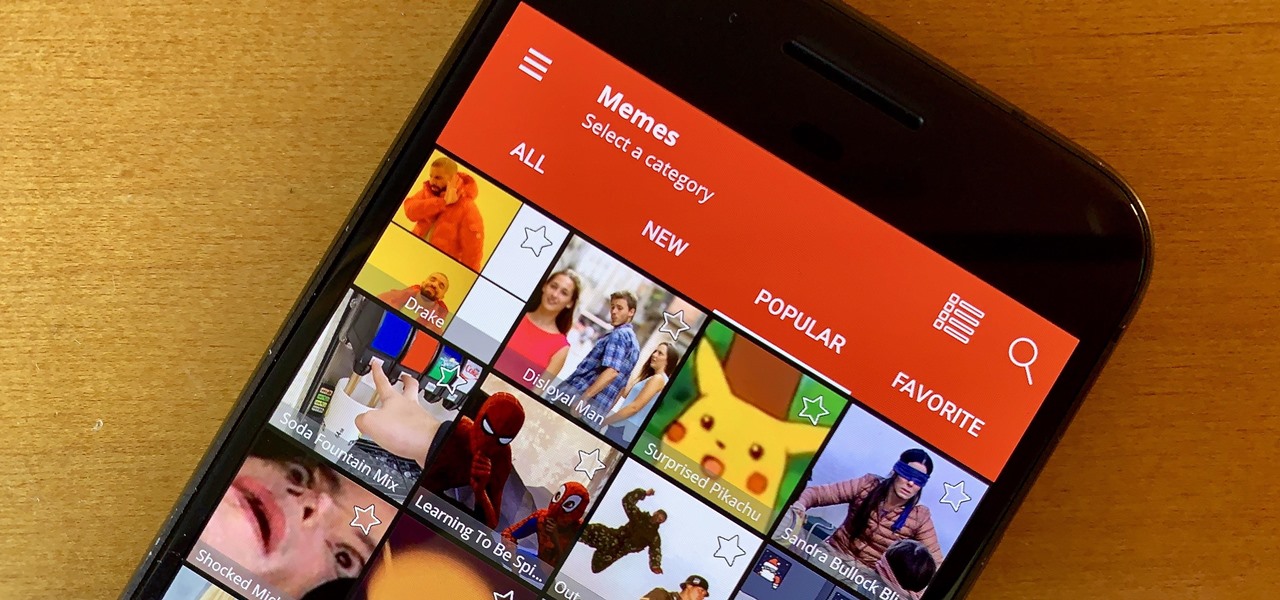
Internet memes are simply everywhere these days. While they've been popular since the '90s, memes, as we know them now, are much different these days. You used to need a computer to make viral images that spread from one random user to the next, but thanks to modern technology, you can quickly create a meme right on your Android phone — you just need the right app.

Depending on how you use your phone, you may have noticed your status bar is a bit crowded due to various icons being enabled. While some icons make sense to have, such as Wi-Fi and Bluetooth, the VPN key icon can be redundant, especially if the app uses a notification. Good thing, there is a way to get rid of the icon.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

Apple first included a dual-lens camera onto its iPhone 7 Plus back in late-2016, yet not many developers besides Apple have harnessed the depth data that "Portrait" mode photos provide. A relatively new app is changing that, though, by using that depth information to let you add realistic-looking light sources to your photos.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

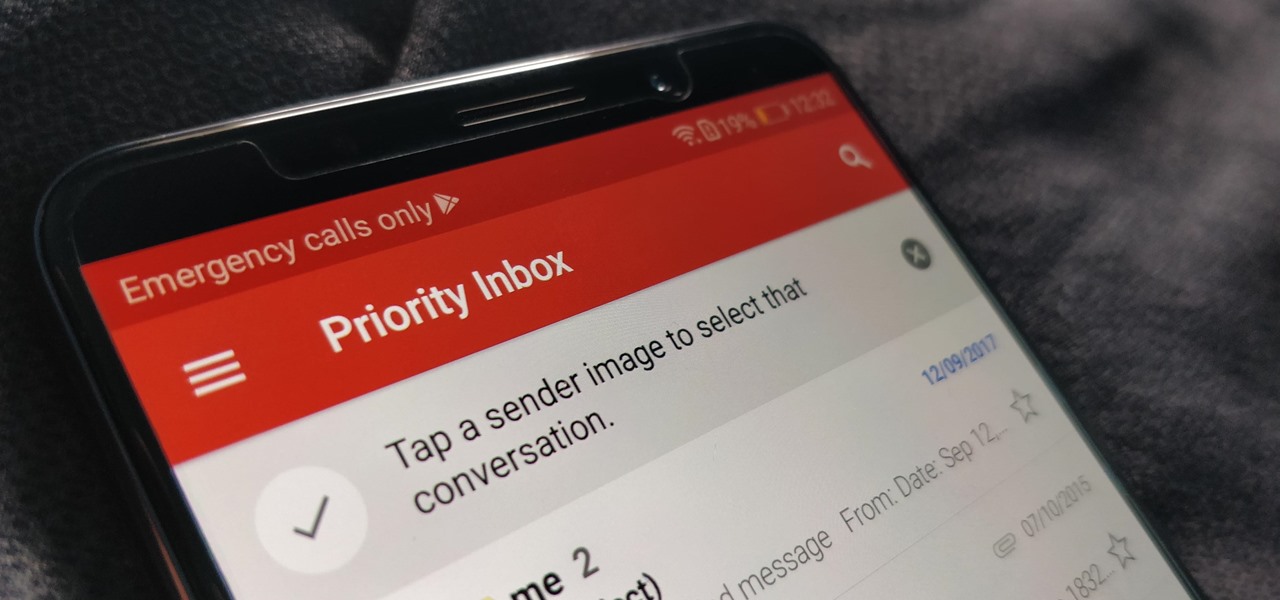
On average, an office worker receives 121 emails a day. Many of these emails are trivial and don't require immediate attention. While Gmail's automatic spam filters catch plenty of irrelevant emails, some still make their way into your inbox. Fortunately, Gmail's tools aren't limited to just spam filters.

Most of us have probably used a GIF at least once or twice to respond to a message, and that's why a lot of messaging services and keyboards have GIF search tools readily available to use. Now, Google wants to take GIF responses to a more personal level, by allowing you to create your own selfies GIFs to instantly sent to family and friends.

Root, TWRP, Xposed, Magisk, custom ROMs — before you can have any of these, the first thing you should do is unlock your bootloader. Thankfully, the Pixel 2 and Pixel 2 XL are some of the most modder-friendly phones out there, so you only need to send a single fastboot command to unlock the bootloader.