
How To: Use the chrome text in Photoshop
Make your Photoshop letters shine like chrome. Learn how to use the creative text tools of Photoshop in this Photoshop tutorial from a professional graphic designer.


Make your Photoshop letters shine like chrome. Learn how to use the creative text tools of Photoshop in this Photoshop tutorial from a professional graphic designer.

This video is all about removing and replacing steel brake lines and includes tips and techniques for doing so. Learn what tools you need, how to remove brake lines, how to mount brake hoses, the differences in brake line fittings, retaining clips, replacing brake lines, and different types of brake fluids.
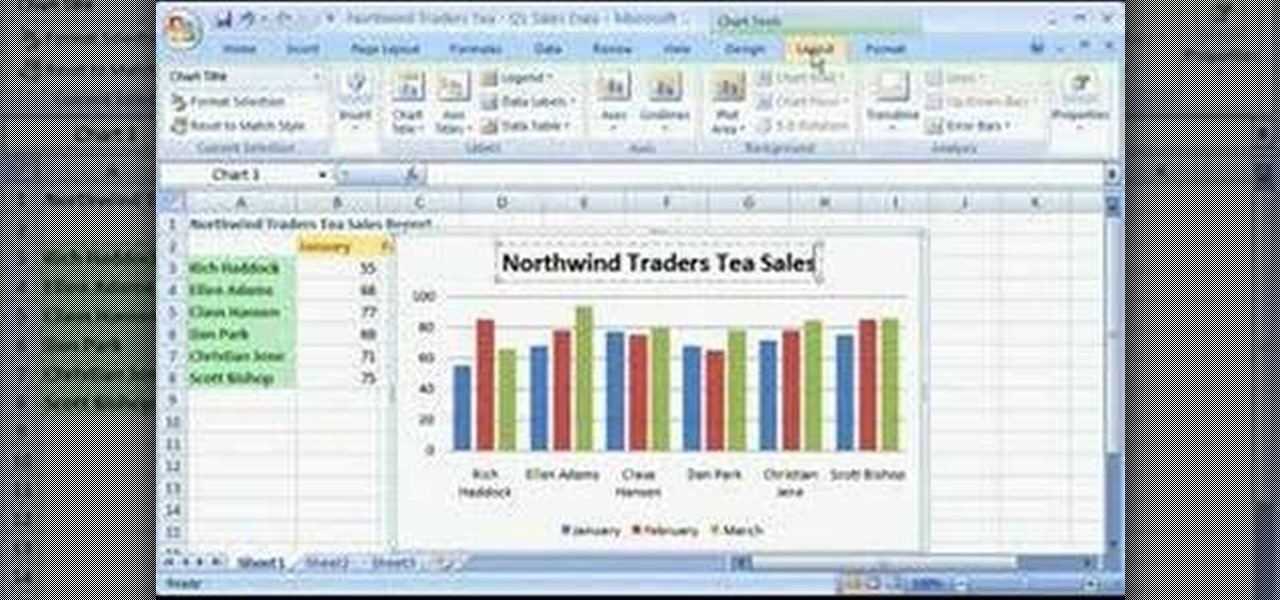
Check out this tutorial and learn how to create chars in Excel 2007. In Office Excel 2007, you just select data in your worksheet, choose a chart type that best suits your purpose, and click. Want to try a different chart type? Just click again and select a new chart type from a huge range of possibilities. Then work with the new Chart Tools to customize the design, layout, and formatting of your chart. You can see how various options would look just by pointing at them.

Do you own a Playstation Portable? There's a number of things you can customize on your PSP with the right tools. A few things you can do with an IR Shell: you can stream files via WiFi or USB and play MP3's while in game. If you're interested, take a look at this instructional video and learn how to install the latest IR Shell 3.9 onto your PSP. Keep in mind that this IR Shell only works if you have the custom firmware 3.80m33 on it.

This gardening tutorial teaches you how to create a successful terrarium for kids of any age. This how to video covers the major points of making a terrarium and I give you lots of alternative methods. Learn how to select a kid-friendly container, select plants, make the terrarium, care and maintain the terrarium. You can use the terrarium as an eco system learning tool for children. This is a great project to do with your children with this how to video.

This is a step-by-step video tutorial on how to fold the windshield of a Jeep Wrangler JK. You will notice there are three tools needed; a Phillips head screwdriver, a 13mm deep well socket w/ ratchet and extender, and a t40 torx. First you should remove the plastic covers on the A-pillars of the Jeeps windshield. Make sure you put all bolts back into the holes they came out of for safe storage. That will also keep dirt out of the threads as you drive your vehicle with the windshield down. Ma...

Modeling software is a wonderful tool for experimenting with modifictions of a product first before building it in real life. Plus, it's just cool to build things virtually. This Maya software tutorial teaches you how to use basic lighting effects in Maya.

Ever wondered how a tornado works? Well, wonder no longer and watch this video tutorial for teachers and students alike. You will see how to create tornado demonstrations for use in the classroom or for fun.

One thing you should do every time you approach a tool is think of the worst-case scenarios. Its a bit gruesome to let your imagination take you there, but there is a good reason for it. This simple mental exercise not only raises your awareness of the potential dangers, but essentially shows you exactly what you need to do to prevent injury. This how to video walks you through potential dangers in the workshop and how you can avoid each one.

Do you want to learn how to build cabinets? Watch this five-part video tutorial for the basics of cabinet making using wood. Part one demonstrates the basics of making cabinet boxes from sheet goods while part two goes over how to cut the deck and stretchers for European-style frame less cabinets. Part three shows all the tools and some of the techniques you can use to apply edge banding. Finally, parts four and five demonstrates how to assemble to the cabinet carcass.
It's difficult to learn programming in the abstract. By building something I need and care about I can learn piecemeal, asking just the questions I need to solve the next step.
In this video tutorial, Chris Pels will show how to configure an ASP.NET web site to use a specific version of ASP.NET/.NET Framework. First see how to identify what version of the .NET Framework a web site is associated with by viewing the script map in Internet Information Server (IIS). See how a script map is associated with the root in IIS and then with individual web sites. Next learn about the ASP.NET IIS Registration tool (aspnet_regiis.exe) used to configure IIS or an ASP.NET web site...

Check out this two-part Autodesk Maya 8.5 video tutorial on creating set driven keys. If you're and animator and your having trouble with your organic or unorganic animation, maybe this is your problem; it's a very powerful tool in 3D modeling in Maya. When ever you come into an object that you are constantly rotating, maybe you should put a set driven key on it, no?
Tired of writing addresses on your outgoing letter mail? Well, you can start printing them out instead! But how!?! If you have Microsoft Word, it's a cinch, and it's not just about making envelope address labels, it's about adding your own personal, creative touch to each one.

Make a bow using Stone Age tools. You don't have to find a cave or anything--you can always do it in your backyard!

In this episode, Brandon Jackson shows how to merge two images with the Photoshop gradient tool to create a banner montage. Doug Grammar joins D.Lee Beard again, this time to explain spyware, adware, and keylogging. They explain what these threats to your privacy & computer speed are as well as how to prevent and get rid of them. Speaking of security, Jason Rybicki shows one way to tell if your privacy is being compromised on a Mac using a free widget.
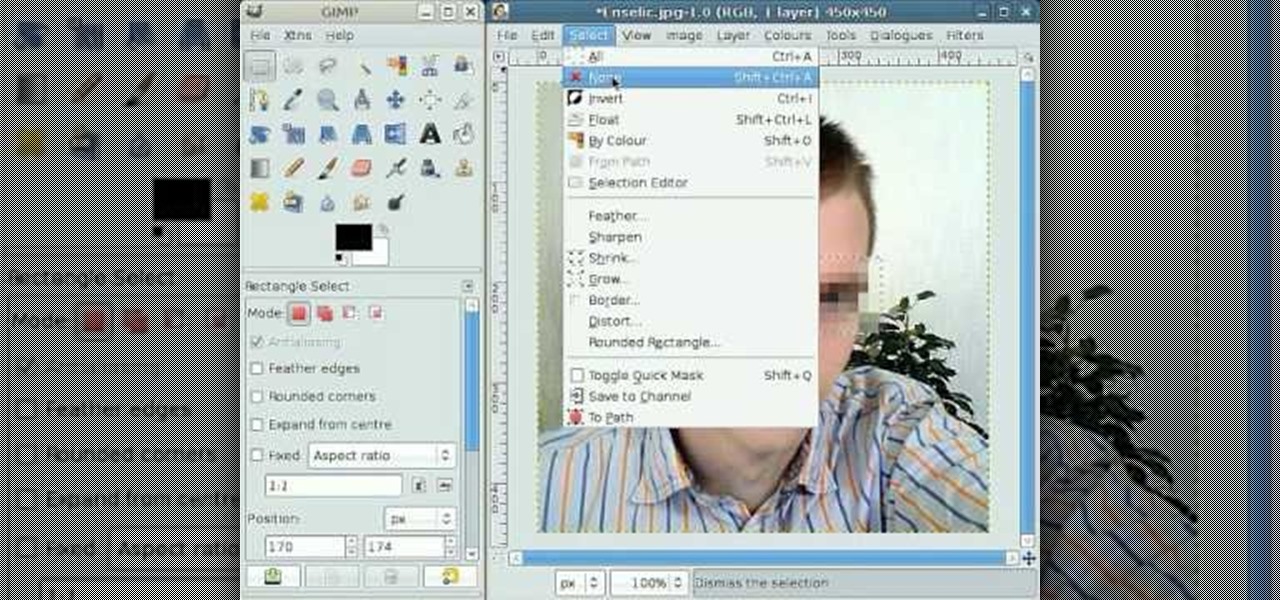
By following this tutorial you will learn the concept of selections in GIMP. Whenever he says "layer mask" he really meant "selection mask".

In this online video series learn from power tool expert and Industrial Technology teacher Jon Olson as he teaches and demonstrates how to use and maintain the power screwdriver. Learn important power tool tips and techniques such as construction work area safety, electrical safety, how to use the chuck on a power screwdriver; how to use a power screwdriver; tool maintenance; battery tool use and care; how to use the torque adjustment collar; how to drive a screw at an angle; how to use the v...

Learn how to care for fruit trees from a professional landscape designer. Our expert will educate on what tools you need and how to select and plant your new fruit tree. Learn valuable how-to tips for your fruit tree. See how to care for the tree by activating the soil. With all the luscious fruit dangling from the tree it can be an invitation for deer to come have a snack. Our expert will show how to protect your tree from becoming a treat. Pruning your fruit trees for maximum flowering and ...

Finding an instrumental or karaoke version of a song can be pretty easy unless you're dealing with a song that isn't popular. That leaves you with just the full version of the song, complete with vocals. So how do you convert it into an instrumental or karaoke track?

These days, most images we post online or share with others come from our smartphones. Whenever personal data is in them, such as debit card numbers, addresses, phone numbers, passwords, and other sensitive information, it's easy to jump into your iPhone's markup tools to black out the text before sharing. But a digital marker may not hide everything.
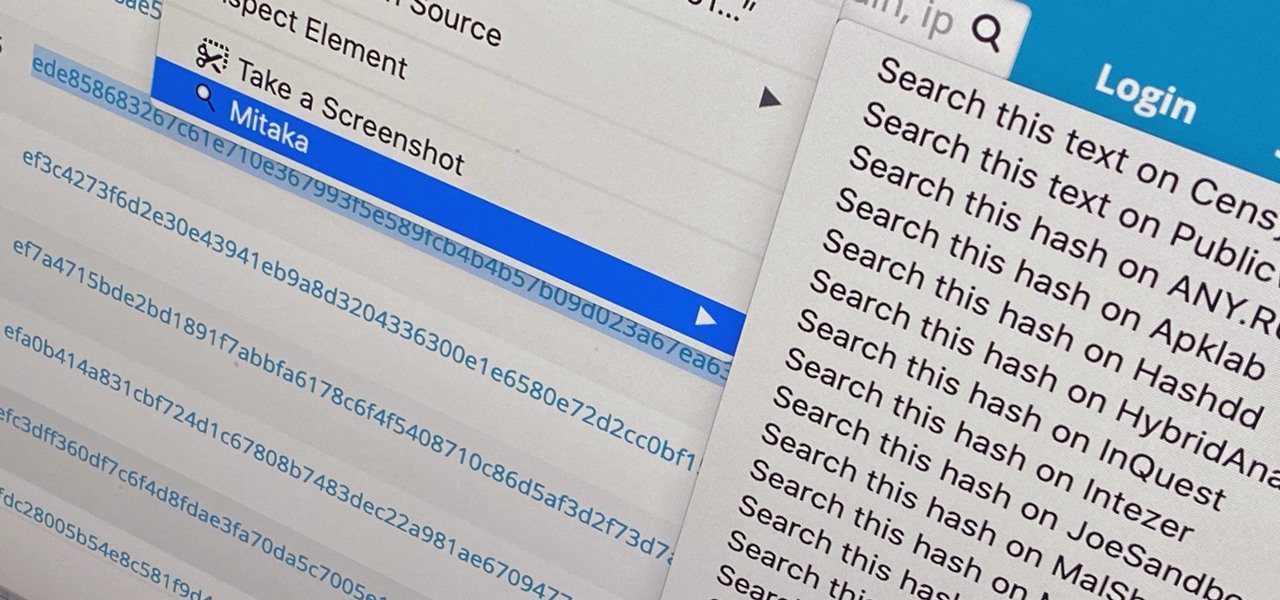
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.
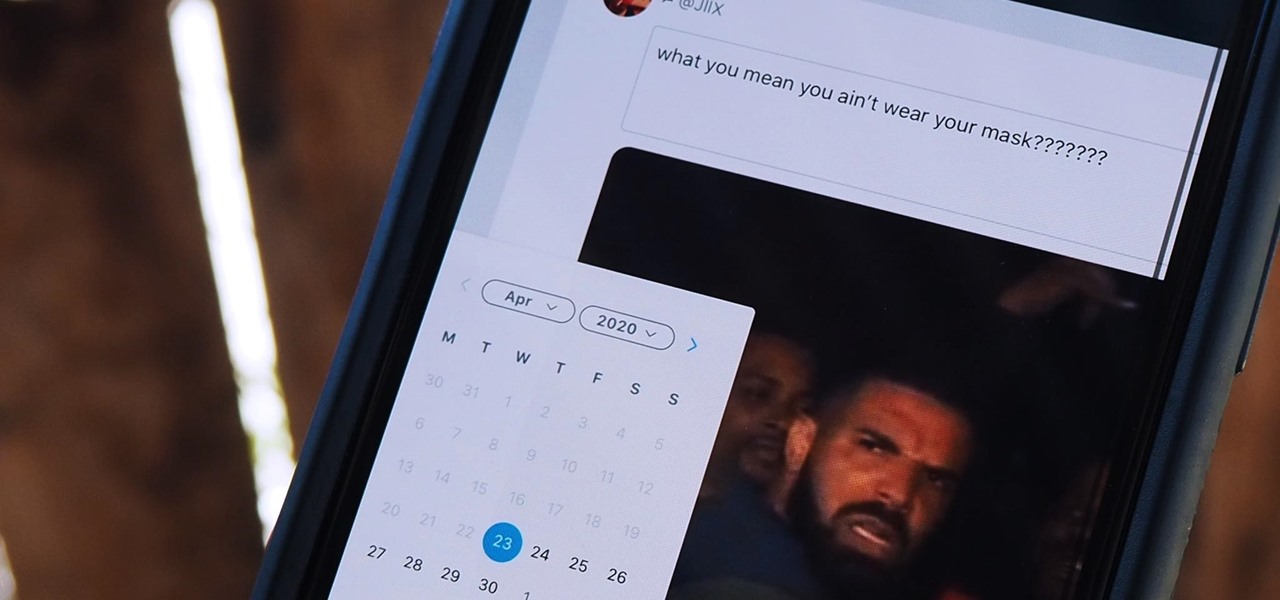
Twitter is a science. The smarter you post and engage with others, the better chance you have at building a bigger audience. Scheduling your tweets is one way to get there. Most engagement occurs at specific hours, but you may not be around then to post your tweet manually. While the official Twitter app on iOS and Android doesn't allow you to schedule, there is another way.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.
TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

The music and sound effects that play in the background of any videos you edit helps set the tone, so it's essential to get it right. Enlight Videoleap, an extremely powerful and popular mobile video editing tool for iOS, lets you quickly and easily add audio from your iPhone and the cloud, but things can still get a little confusing when you have a timeline full of clips.

Using a green screen is an affordable and easy way to transport your video to anywhere imaginable, even to places that don't exist. You can use it to sit behind a desk in a busy newsroom or dance on the moon, but first, you have to know how to properly perform chroma key compositing two videos together. Fortunately, Enlight Videoleap on iOS makes it easy.

Editing photos can be tedious, especially if you are using a similar theme for all of your photos. It takes time to select every tool, play with the bars, and find an adjustment that you're happy with. Luckily, there's a faster way. Adobe Lightroom for Android and iPhone allows you to save your favorite editing presets so you don't have to change every photo every time.

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

If you want the ability to play YouTube videos in the background as you multitask on your iPhone, you'll have to shell out $11.99 a month for the privilege of doing so with YouTube Premium. Not all of us can afford nor justify such an expense, but if your iPhone is jailbroken, you can get your hands on this sought-after feature — and much more — without spending a dime.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.
If you installed Android 9.0 Pie, you might have enjoyed trying out some of the new features in the latest version of Google's OS. However, change isn't always a good thing, so you might be wishing you could downgrade back to Oreo right about now. Good news — you can.

Nova Launcher is one of the most popular apps on the Play Store thanks to its rich features and fluid navigation. But one downside that comes with this abundance of features is that much of Nova's functionality is lost on the masses. Fortunately, I've used Nova for several years and learned a few tricks along the way.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.