
How To: Make a dish garden arrangement using silk flowers
The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.


The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

The art of floral arrangement is a fun & valuable skill. Dana Plazyk lends useful tips and tricks on making simple flower arrangements.

August is a time when it is common to see bats flying overhead while taking an evening stroll or night fishing at your favorite spot. The two most common bats in Ohio are the little brown and the big brown bats and both are found in rural and urban settings. Bats serve a valuable purpose for humans because they feed on insects, including mosquitoes and those which plague farmers’ crops. However, bats sometimes create roosts, or gathering places, in people’s homes. Join Wild Ohio’s Donna Danie...

In this how-to video, you will learn how to clean your coins to make them look shiny and new. This is useful if you collect coins. First, you will need coins, vinegar, salt, paper towels, a pencil, and a jar for the mixture. Take the coin and place it in the jar. Next, add a small amount of salt to the jar. Now, pour three caps full of vinegar into the jar. Mix it with the pencil and let it rest for ten seconds. Now, take the coin and place it on the paper towel. Use the eraser on the pencil ...

Whether you're shopping for deals, need help with a little math, or any number of other occasions, it's a valuable skill to know how to quickly figure out a percentage given two numbers.

Learning how to read a compass might just save your life one day! Know how to use a compass and you'll never get lost in the wild. Follow these simple steps & you'll learn this valuable skill.

Frustration is something that comes along with learning to ride a bike. You mustn't give up as it's a valuable skill to have. This video shows you how to ride a bike and minimize frustration.

Put yourself in the shoes of a burglar so you can anticipate where they'd look for your valuables. You Will Need

You've drafted a promising team, and the season's under way. Now increase your chances of making the playoffs.

The art of floral arrangement is a fun and valuable skill. Dana Plazyk of Flowers by Design lends useful tips and tricks on making simple flower arrangements.

Compulsive gambling is a recognized addiction, just like alcoholism or chemical dependency. Follow these steps to see if you might fit the profile. Recognize the signs of compulsive gambling with this guide from Howcast.
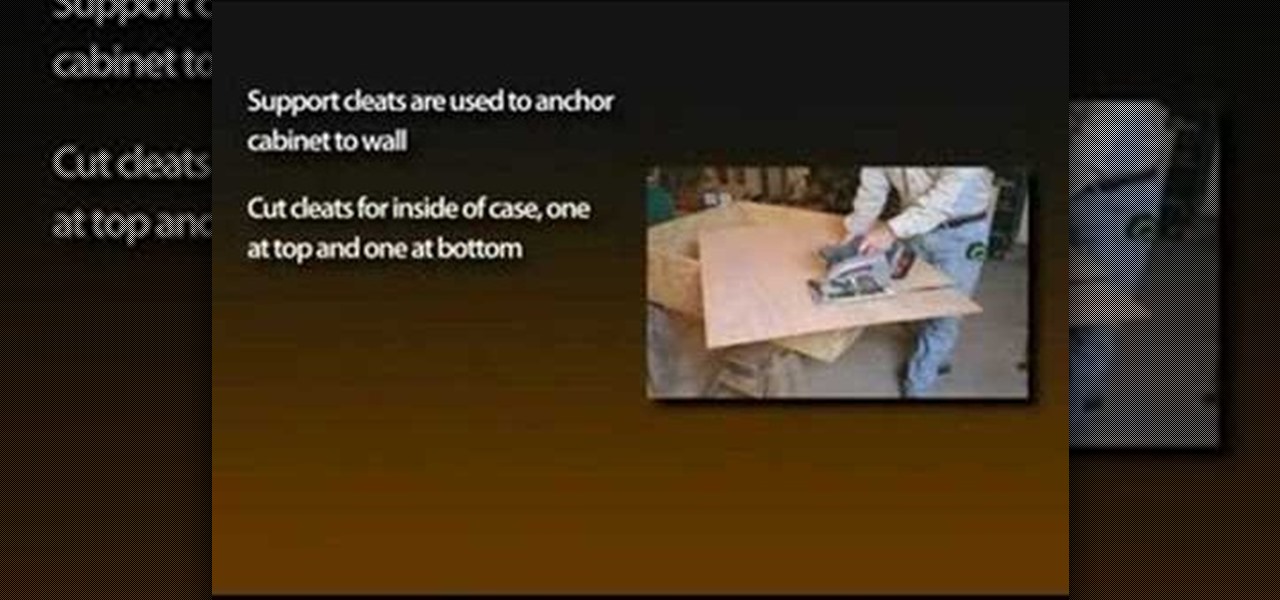
With the growing popularity of cordless power tools, it's extremely easy these days to accumulate a lot of portable tools, and when you add in quality corded tools, such as circular saws, routers, planers and air nailers, you can end up with a pretty hefty investment. These same tools are the first to “walk away” in a theft. Left lying around a shop or garage, they can also be somewhat dangerous for youngsters. A locking cabinet not only provides a secure place, but protects the tools as well...

Women's self defense strikes are extremely valuable in a world where women are attacked everyday. Learn self defense strikes, kicks and punches with tips from a martial arts expert in this free self defense video series.

Learning American sign language is valuable for anyone who is deaf or has dead friends and family. Learn how to sign words for emotions in American sign language with tips from an audiology expert in this free sign language video series.

If your old clothes are of high quality and in good shape, selling them on consignment is an easy way to make cash quickly.

Getting a Rapunzel-like mane takes time, but you can speed things up with these valuable tips. You Will Need

If even the bats are intimidated by the clutter in your attic, it’s time to tackle the mess. Watch this video to learn how to clean out your attic.

The economy is rough at the moment, and we all need our jobs more than ever. Check out this tutorial, and learn how to make yourself so valuable at your job that no one would ever want to fire you.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

If you're ever done a big race before, then you've probably had to deal with attaching a paper number to your chest with safety pins. In a triathlon, where you are going to have to change clothes multiple times, having to keep unpinning and repinning that number can cost you valuable time and effort. This video will show you how a race belt can simplify the process, making switching your numbers location a breeze, even across multiple outfits.

If you're using a Carolina rig and don't have much experience with how to use it, then check out this next tutorial. In this video, you'll learn a couple valuable pieces of information that should be useful for you when you're using a Carolina rig when out bass fishing. These tips can help you catch something that you're sure to be proud of. So good luck, pay attention, and enjoy!

Performing a 720, or two full revolutions, on a snowboard can be daunting, especially if you've had trouble doing 180's and 360's. Really, they are much the same though, you just have to keep spinning! This quick video breaks down how to perform a 720 successfully in a halfpipe. They make it sounds a little easier than it actually is, but the tips they offer are valuable and should have you spinning like a dervish in no time.

This tutorial cooking video will teach you how to use a pressure cooker. A pressure cooker is a valuable tool for any cooking.

This video will teach you how to backstick with your drumsticks whether you're playing on a drum kit or in the drum line at your high school. Backsticking is mainly triplets, and a valuable trick to learn for any drummer.

Ask the Builder host, Tim Carter, demonstrates how to drill holes for PVC plumbing pipe fittings so that you don't waste valuable time in your home enlarging a mis-drilled hole.

Tax season is always stressful, especially for entrepreneurs and small business owners. Rather than wait until March to get your finances in order every year, learning how to keep track of your expenses is a valuable skill that saves you and your business time, money, and plenty of anxiety.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

Confused by TikTok? Trying to grow your Instagram fanbase? Aiming to create the perfect Facebook ad? Growing an audience might be challenging, but with the right strategies, it is possible — and fun.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Demand for Tesla's driverless features as well as its ultra-long battery ranges and a reputation for offering the best-in-class electric car driving experience helped Tesla see a 32% surge in its value as a brand, topping out at $5.9 billion in the BrandZ Top 100 Most Valuable Global Brands study, released June 5.

Chopping veggies is pretty straightforward: grab the right knife and start slicing. Nothing to it! However, the way you cut your food does affect the length of time it takes to cook, as well as how evenly it cooks. So the next time you need to get your vegetable from hard and crunchy to perfectly soft in mere minutes, give the oblique cut a try.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.