Just weeks after revealing plans to port one of its most vital augmented reality products from HoloLens to the smartphone world, Microsoft has finally opened the mobile software floodgates to the public.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

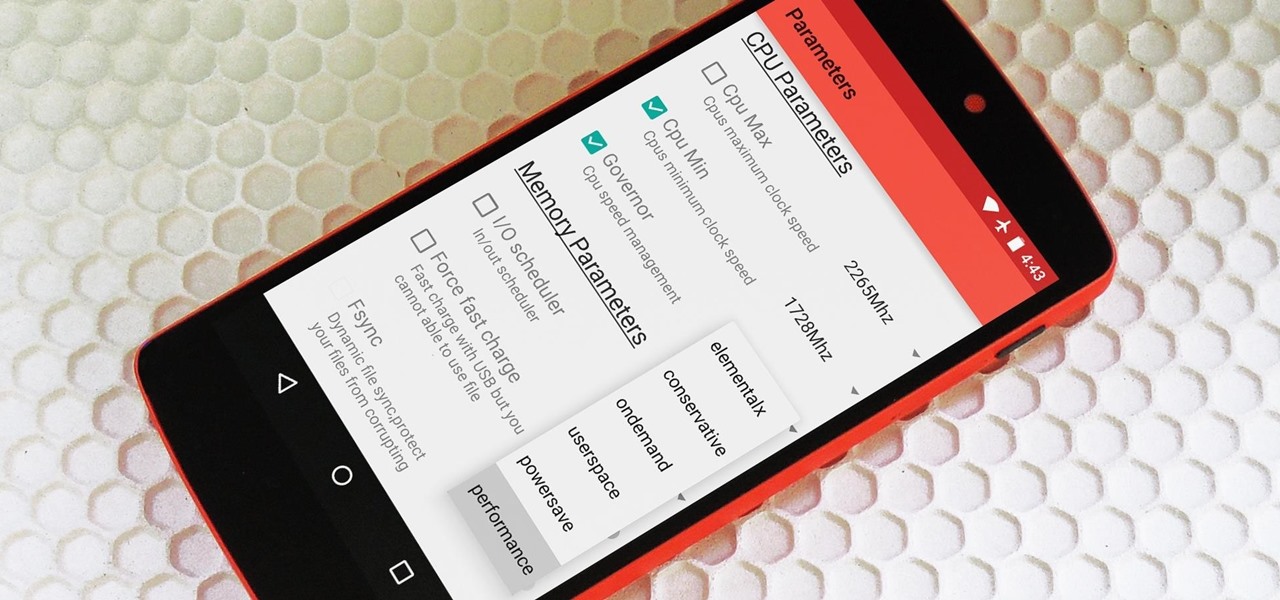
Deep down at the core of Android lies the system kernel, which serves as a bridge between software and hardware. Custom kernels can be installed in place of the stock offering, and these are generally optimized for better performance or increased battery efficiency.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

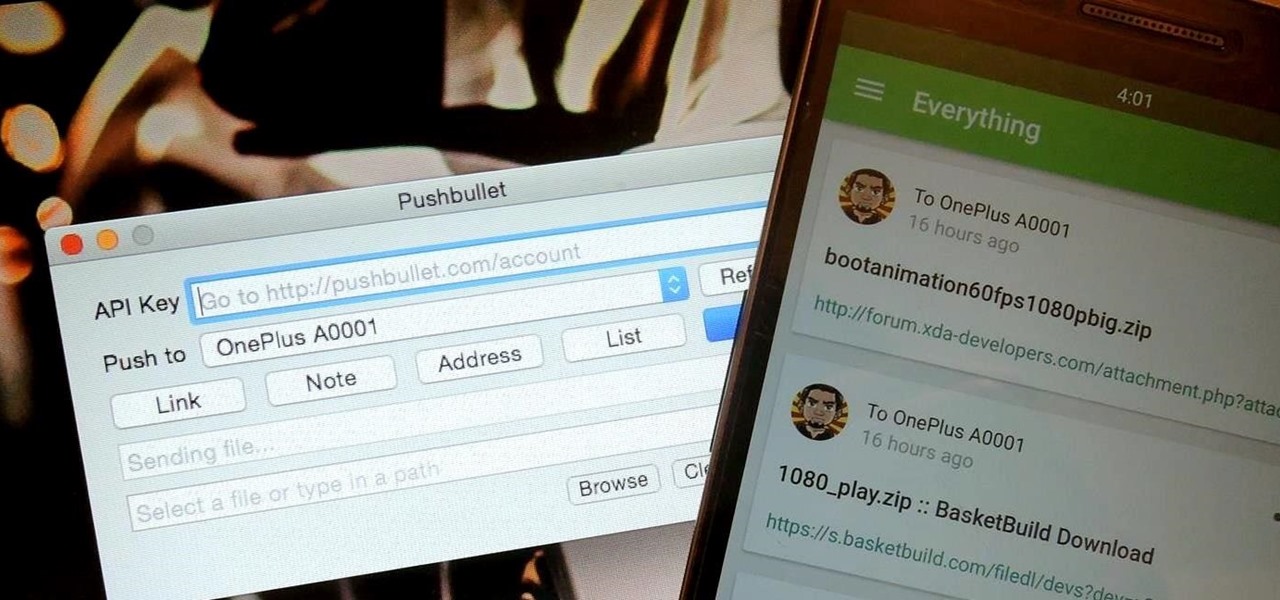
Before Continuity and Handoff were even announced, Pushbullet was already allowing users to quickly send notes, links, and photos between their devices with a few clicks.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

To become a bounty hunter, you will want to first check your state's laws to see if you need to be a licensed private investigator. If you live in Florida, South Carolina, Oregon, Wisconsin, or Kentucky, don't even try it--bounty hunting is not allowed! Otherwise, your first step is to find a client who needs a target to be caught. Bail bond agents employ bounty hunters to track down people who have refused to show up to court. Find out who your target is. Assemble a file, look into any recor...

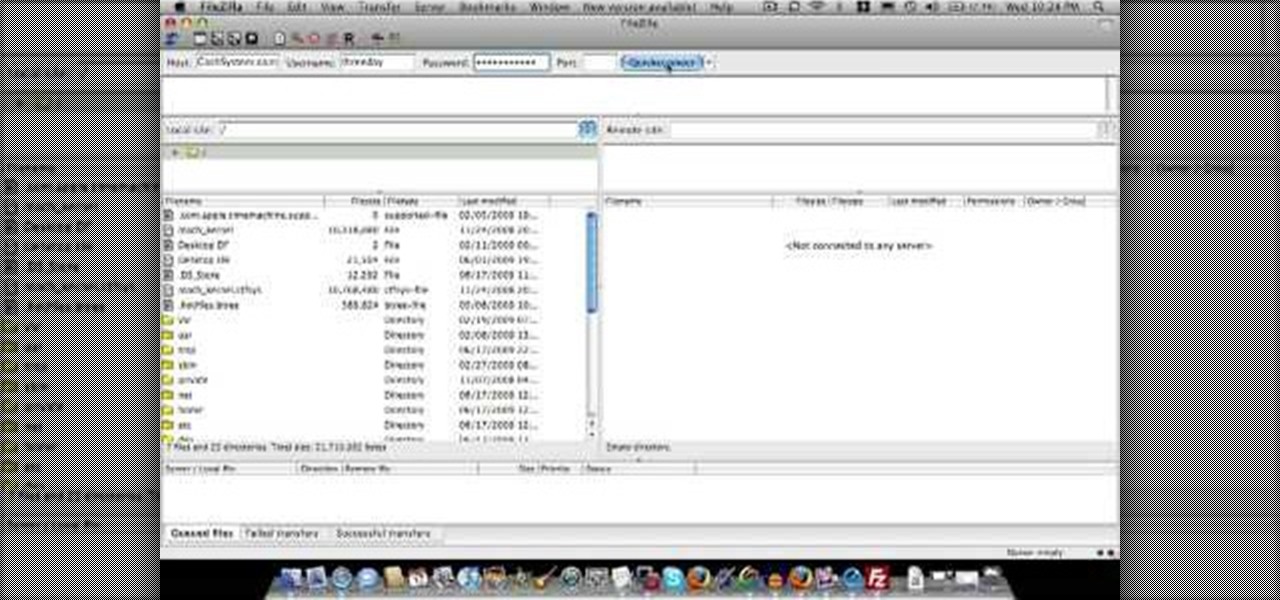
In this video tutorial, viewers learn how to create a FTP from a local computer to a website. In this video, viewers are shown (once you've chosen a web host) how to perform FTP file transfers from your local computer to your website. FTP (File Transfer Protocol) is a process that you can use to transfer files from your local computer to a remote computer (your website). Once you've set up a hosting account, your hosting company will provide you with FTP login credentials. Using an FTP softwa...

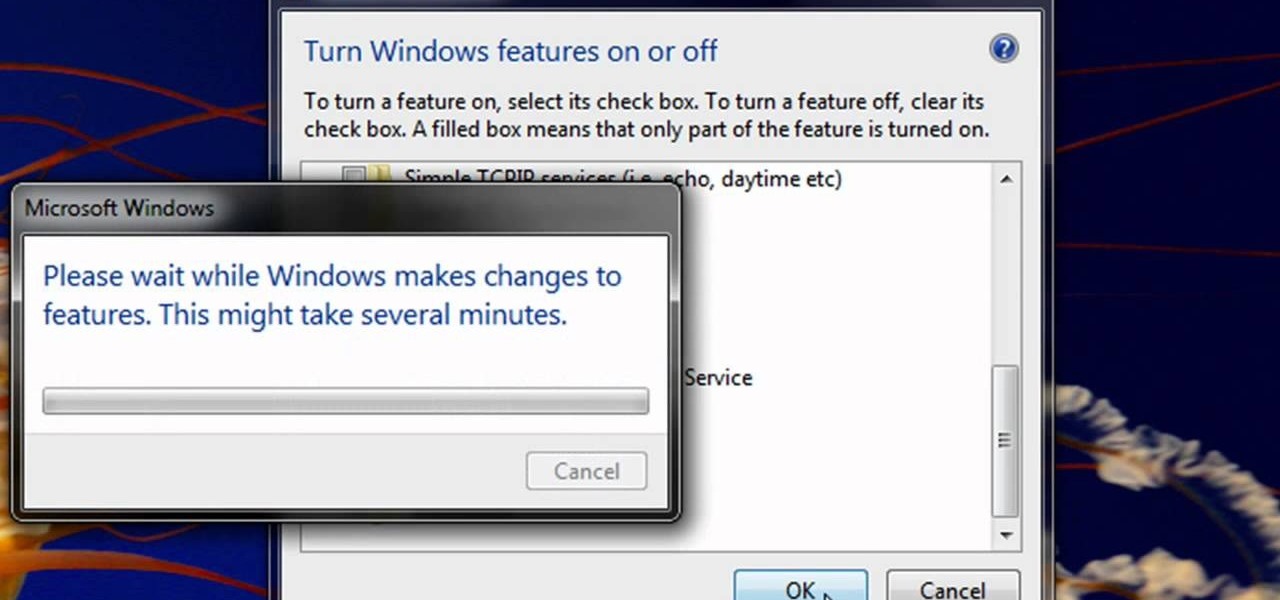
Enabling Telnet in Windows Vista is a little bit more difficult than its predecessors but it still can be done. This video will demonstrate exactly how to enable Telnet in Windows 7 and Vista.

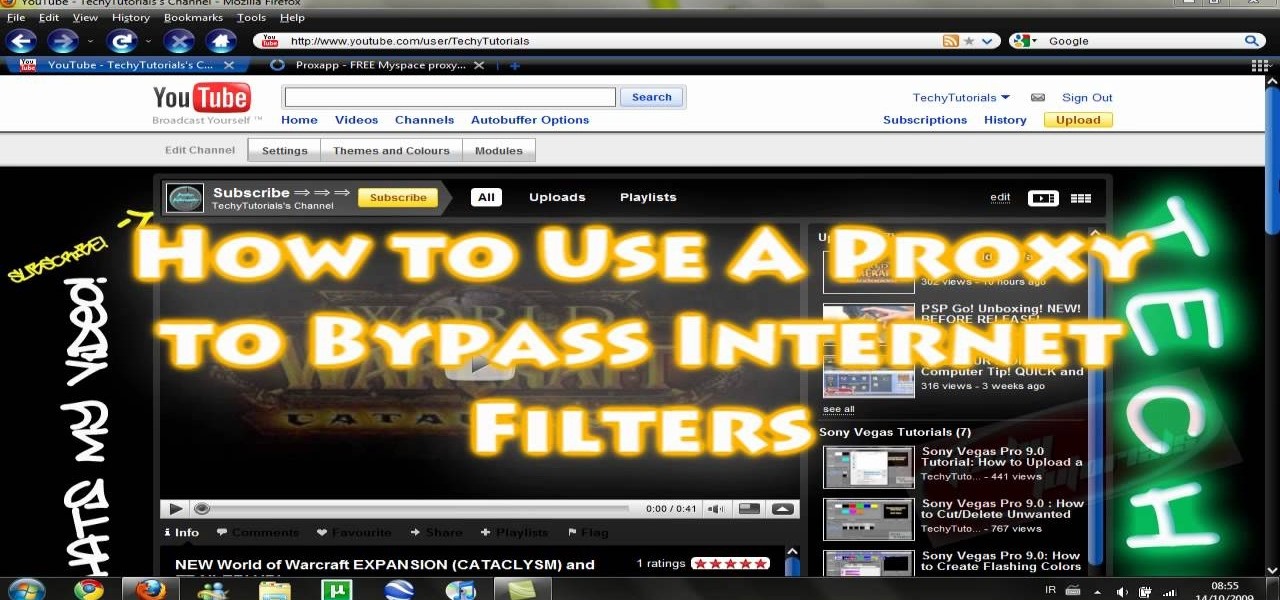
The video shows us how to use a proxy to bypass the Internet Filters. Most of the times in our schools and colleges most of the websites including the social networking ones will be blocked for security reasons and makes us unable to log into those websites. In such cases even the ones from the YouTube, several videos will be blocked. So in this video, we will be shown how to bypass those filters and log into those sites. Firstly go to the website Proxapp and over there you will be asked the ...

When conducting covert mobile surveillance with video it is vital to have a good bag that will contain and allow you to get footage in an inconspicuous manner. Always take into consideration the lighting and distance you’ll be at.

Do your presentation skills need a little work? Being in front of a crowd or some potential clients may be one of the hardest things you will ever do, but staying confident makes all the difference. Losing any bit of confidence will result in your presentation falling flat and killing your self-esteem, and perhaps even risking your job. So, being confident is a must.

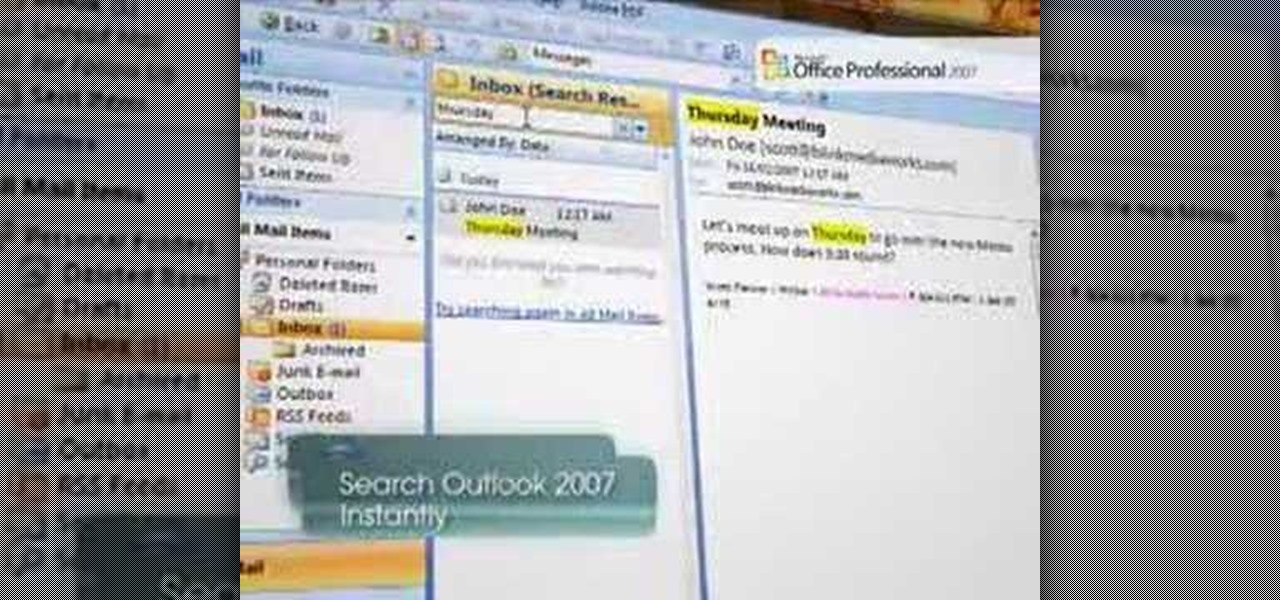
Microsoft Windows Vista Tips - Finding Information with Instant Search in Microsoft Office Outlook 2007 - Somewhere in the hundreds, or perhaps thousands of messages in your Microsoft Office Outlook 2003 mailbox is the one that has the information you need about that client meeting on Thursday. So how do you find it without reading through every one of your messages? The new Instant Search feature in Microsoft Office Outlook 2007 allows you to find the information you need instantly. For more...

Work out the pelvis with pelvic tilts. Learn about exercises for strength and flexibility in this training video. Take action: keep your back flat, this is a high repetition exercise, and keep feet flat on floor. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training aspiring female ...

Increase muscle strength with barbell exercises done while lying down. Learn about muscle training, fitness, and growth in this fitness video. Take action: do not rock arms and keep core tight. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training aspiring female body builders as sh...

Exercise the quadriceps muscle with quad extensions. Learn about increasing leg strength in this training video. Take action: keep core tight, squeeze legs at top of movement, but only legs will move. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training aspiring female body builder...

Working out the arms with standing dumbbell curls. Learn to increase muscle strength in the arms with dumbbells and curl exercises. Take action: start with feet shoulder-width apart, palms face forward, keep elbows at sides, and do not rock. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enj...

Gain muscle strength and flexibility with diagonal lunges. Learn about dumbbell exercises to promote fitness in this weightlifting video. Take action: maintain balance, keep back leg straight, and increase difficulty by adding dumbbells. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys ...

Sumo squats will help to strengthen the legs. Learn how to properly do squats in this workout video. Take Action: hold in squat position to increase difficulty, feet wider then normal squat, and keep chest and head high. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training aspiring...

Increase flexibility and prevent injury by stretching the triceps. Learn how to do stretches and arm exercises in this video. Take action: hold stretch for 20-30 seconds, stretch when muscles are warm, and hold stretch at point of mild discomfort. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and s...

Increase muscle strength and flexibility with dumbbell rear lunges. Learn about dumbbell weight training and exercises in this video. Take action: keep chest high, shoulders back, core tight, raise knee to increase difficulty, make sure back step is big, and add hop to increase difficulty. Michelle is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting ...

Increase muscle strength with dead lift exercises. Learn tips and techniques for proper weightlifting in this fitness video. Take action: keep bar close to legs, don't round the back and use proper form. Michelle is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training aspiring female body builders as she is one herself. She focuse...

Working out with bent knee hip extensions requires attention to form. These knee extensions are also called Romanian Dead Lifts. Learn about hip extension exercises in this dumbbell fitness video.

Starting a business has to involve a desire to benefit someone else other than you. If all your reasons for starting a business are to benefit you, chances are good that you have missed the big picture. At least one reason you have to want to stat a business needs to be to help someone else. Either use proceeds from the business to help a charity of your choice or to solve a problem or provide a solution to a need for the target group that your business serves. Focus on one issue to start wit...

In this video, we learn how to get a girl to like you. The ideal man for a woman is confident and makes the girl feel like she has earned you. You should come from a mindset of high value. You should never let the woman be the challenge for you, you should be the challenge for you. If you have a lot of women friends and date a lot of women, this will make her realize that you are in high demand. Don't let the woman think that she has control of you, so make sure you don't stick with one girl ...

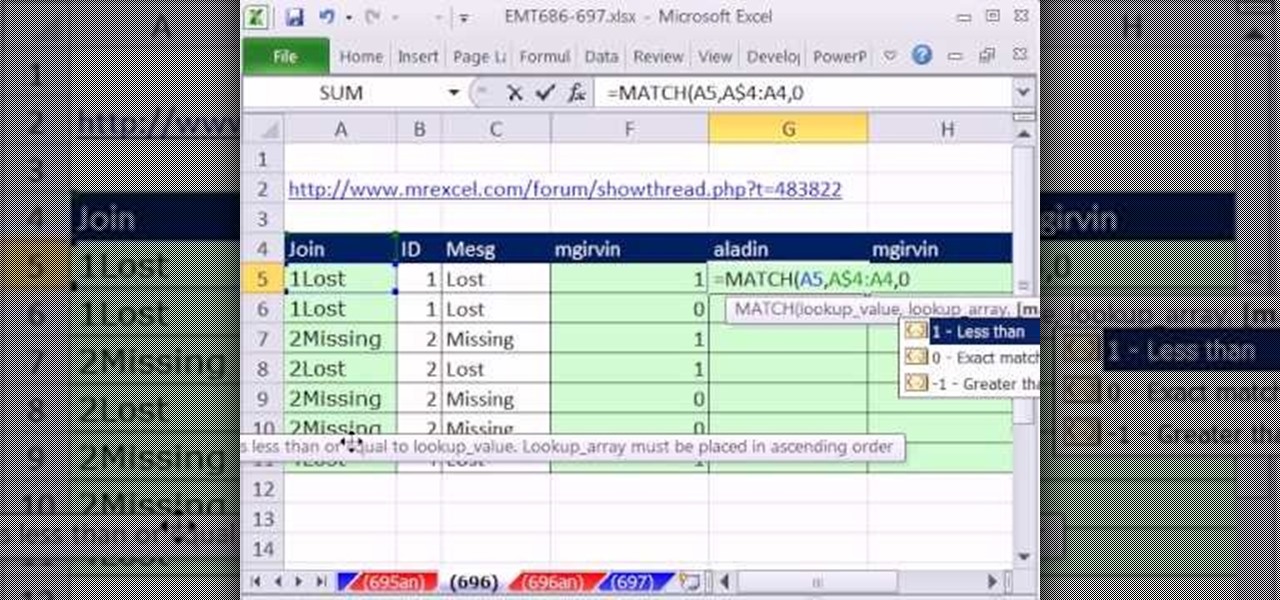
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 697th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a column of 1s and 0s (ones and zeroes) where 1 indicates the first occurrence and 0 indicates any remaining duplicates.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 677th installment in their series of digital spreadsheet magic tricks, you'll learn how to average the last three scores eneterd for any Player using the functions: AVERAGE, IF, ROW, COUNTIF, MIN, LARGE.