With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

Demand for Tesla's driverless features as well as its ultra-long battery ranges and a reputation for offering the best-in-class electric car driving experience helped Tesla see a 32% surge in its value as a brand, topping out at $5.9 billion in the BrandZ Top 100 Most Valuable Global Brands study, released June 5.

Depending on your device, when you lower your brightness slider all the way to the minimum, it may still emit a considerable amount of light. This is because manufacturers have the option of setting a minimum brightness value, and while 1 would be the true minimum brightness that your display is capable of, some have set is as high as 5 or even 10.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.
This is for those using Kali Linux 2.0 that need to edit the CRDA values to get the increase in Txpower

3D Touch on the iPhone 6S and 6S Plus is a pretty cool feature, and will only get better as more developers begin to roll its functionality into their apps.

When I started to go to this site I found it fascinating and found myself coming here all day I have used a lot of the info I have gotten from here in my professional career and on my own. I currently am the VP of RND for a small IT company. I have been pushing toward Penetration Testing as a service for our clients and future clients. For the past 10 years here it has been a very long uphill battle and have hit a lot of road blocks. So I decided to work on this on my own of course as soon as...

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Ah, the fabled dark mode. In the past, many users were delighted to find the existence of something called Royale Noir, a dark theme option that was available for Windows XP. Yet for reasons unknown, Microsoft had kept knowledge of Royale Noir a secret until some bright minds discovered its existence, and the rest is history.

When you see a color depicted on your computer, smartphone, or tablet, odds are it was processed as a hex triplet before it was rendered. Most modern websites and operating systems use a hexadecimal coding system to signify certain colors, and these are represented as 6 letters and numbers.

When I first received my HTC One M8, I was in love with the 5-inch screen size, but the icons and font just seemed too big, wasting valuable screen real estate. Phablets, like the Samsung Galaxy Note 4, have only slightly larger screens, but don't seem to have this problem since manufacturers lowered the device's DPI, or dots per inch.

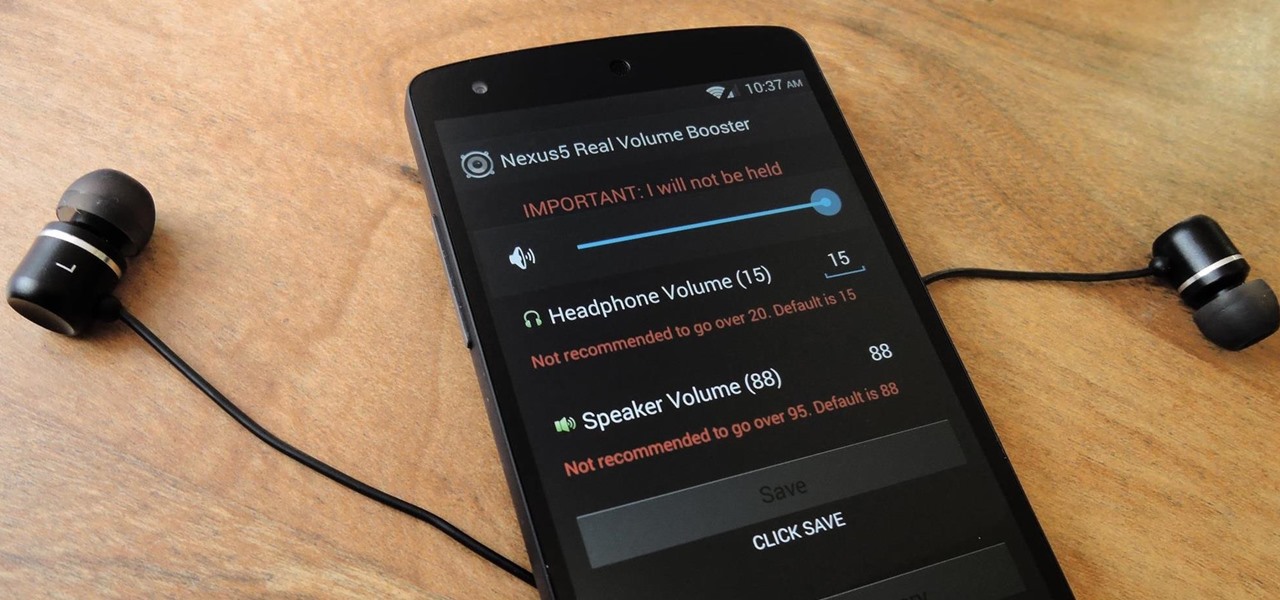
There's a known issue affecting some Nexus 5 users where the speaker volume is fairly low. This could be attributed to a manufacturing defect, which you could possibly fix with a hot needle, but if your built-in speakers and headphones seem muted, don't take your Nexus apart just yet.

Despite having the UltraPixel branding, the M7's camera can leave you feeling a little let down. The picture quality is clear and the low-light shots are decent, but when looking at the same shots taken on a friend's iPhone, you may feel a little inadequate.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

I can't say that I'm a huge Tweeter, but I'm definitely a good follower. Having the ability to follow comedians, brands, and athletes helps me stay up to date on the things I'm interested in, and I appreciate being thrown a good joke every now and then.

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

If you're interested in running the Minecraft 1.9 pre-release on your server and giving it a spin (or letting others with the Minecraft 1.9 pre-release client give it a spin), take a look at this guide to setting up and installing the server. This guide will also help people who are getting stuck on the loading screen in the 1.9 prerelease as well.

Jennifer Lopez, better known by her diva moniker J Lo, doesn't step foot out of her multistory mansion without a full face of makeup on, beautiful, voluminous curls, and her neck and hands dipped in diamonds.

Nicole Richie is the poster child of boho chic. Whether it's her wispy milkmaid braids, her flowy hippie dresses, or her arm full of bangles, she always looks effortlessly gamine.

In this tutorial, we learn how to unblock Facebook or MySpace at school or work. First, go to your start menu and run "services". After this window pops up, look for DNS client and then right click on it. Then, click "stop". After this, restart the browser that you are on with your computer. From here, type in the address of the website that you want to go to. It should not be working and you will be able to go onto the website without any problems! This is a great way to get past blocks your...

In this video, we learn how to download games with torrents. First, go online and download a client from uTorrent. Once you download and install this to your computer, you will be able to search for the torrents that you want. Go to: the Pirate Bay and you will see a search bar in the middle of the screen. Choose what you want to search for, then click on what you want to download. Once you double click this, it will give you an option where you want to download it. Chose uTorrent, then this ...

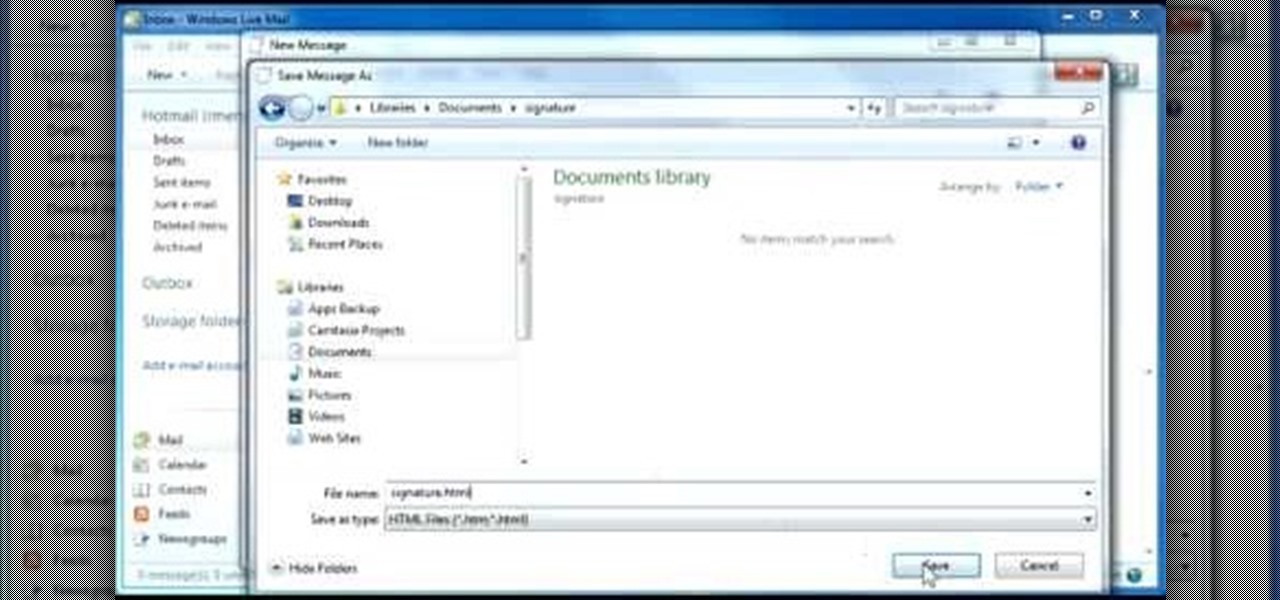
Whether you own a business or work for a company, you probably send out millions of emails every day corresponding with clients, PR, and whoever else you have to deal with. It's hard enough making sure you get around to all of them, but what's more is that even after you've finished composing the message you have to add your name, company name, phone, etc.

In this tutorial, we learn how to use Tarot cards and perform readings with Peter John. When you start to learn how to read cards to clients, you will first lay the cards out on the table. Then, the person who you are reading to will choose the cards from the pile. Depending on the card that they choose, you will read to them the description of what this card means. Then, you will delve deeper to tell them how it tells about their life and what their future will hold. After they are finished ...

In this video, we learn how to hack your Android phone. First, plug your phone into the USB to your computer. Now, search for telnet on your phone and install it onto your phone. Download this client to your phone from the Google Marketplace, then you can unplug your phone from the computer. Once this is installed, run this on your phone, then wait for it to load so it can hack your phone. When it is finished, your phone will be hacked and you can change the setting on it how you prefer. This...

In this tutorial, we learn how to do an auto damage appraisal. First make sure you have all your paperwork ready and lined up before you go to inspect the vehicle. When you have this done, the clients will be happier that you have everything ready to go and the claim is getting taken care of quicker. After you inspect the vehicle, write down all the notes about the vehicle and then calculate what the amount of damage is. Then, give a copy of the appraisal to the owner. After this, submit your...

Want to make a cartoon representation of yourself? See how to create free cartoon avatars that can be customized to represent your unique personality or interests across the social networks or chat clients you frequent with this video guide. For more information, including detailed instructions, take a look.

Need help drumming up new business as a Pilates instructor? This clip presents an overview of the five principle benefits derived from the practice of Pilates. Whether you're considering the possibility of starting your own Pilates studio or already have one and just need a little help tackling a particular pedagogical problem, you're sure to be well served by this free video lesson from the folks at Balanced Body Pilates. For more information, including a comprehensive overview, watch this v...

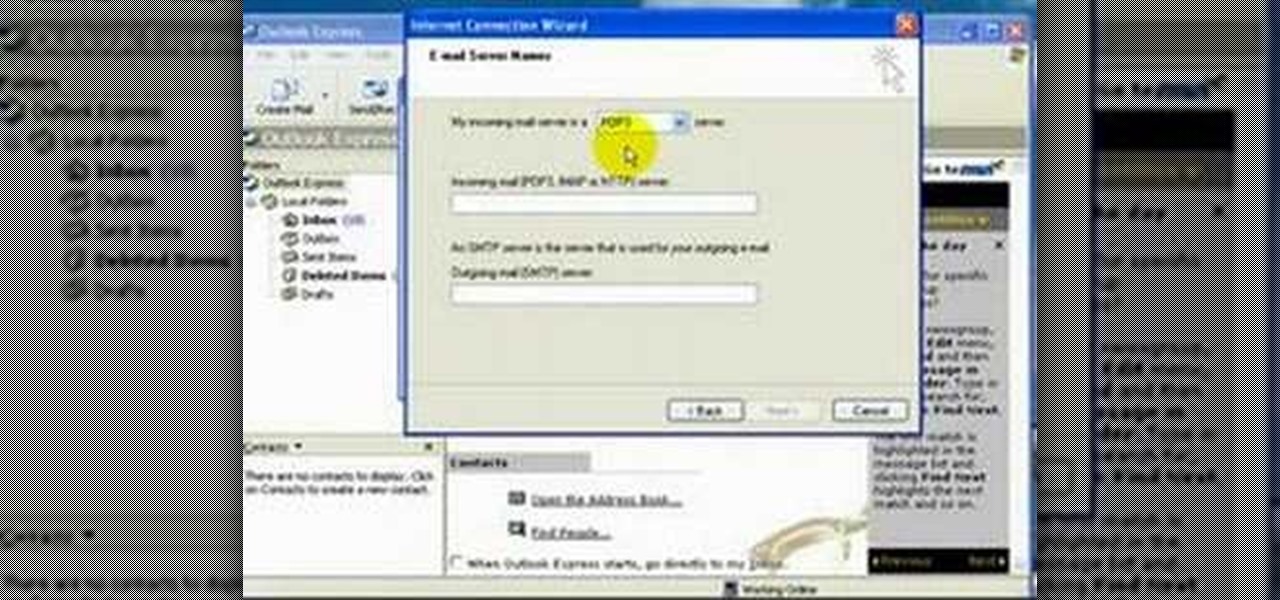
Carole Gallesie from Creative Media Web shows viewers how to set up a new account in Microsoft Outlook Express. Express is preferred because it is a scaled-down version of the popular email client and it is easier to navigate. From your Windows desktop, go to the start menu, all programs, and click on outlook express. When the program opens, look at the top of the page for the "tools" menu, select accounts, add, and mail. The new account wizard will then appear and will walk you through setup...

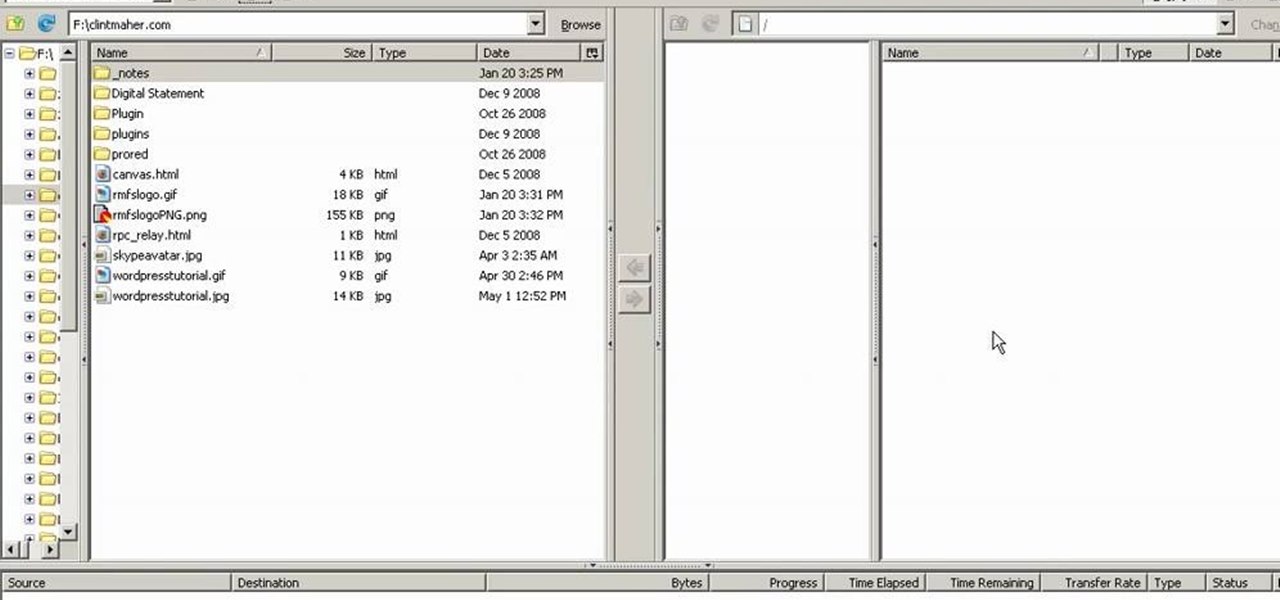
In this video, our author, atomicinteractive, shows use how to use Fetch FTP to upload a temporary webpage. Please make sure your directory has the html file. Please find your email with ftplogin information. This will also show login information for the control panel and creating alternate email addresses.

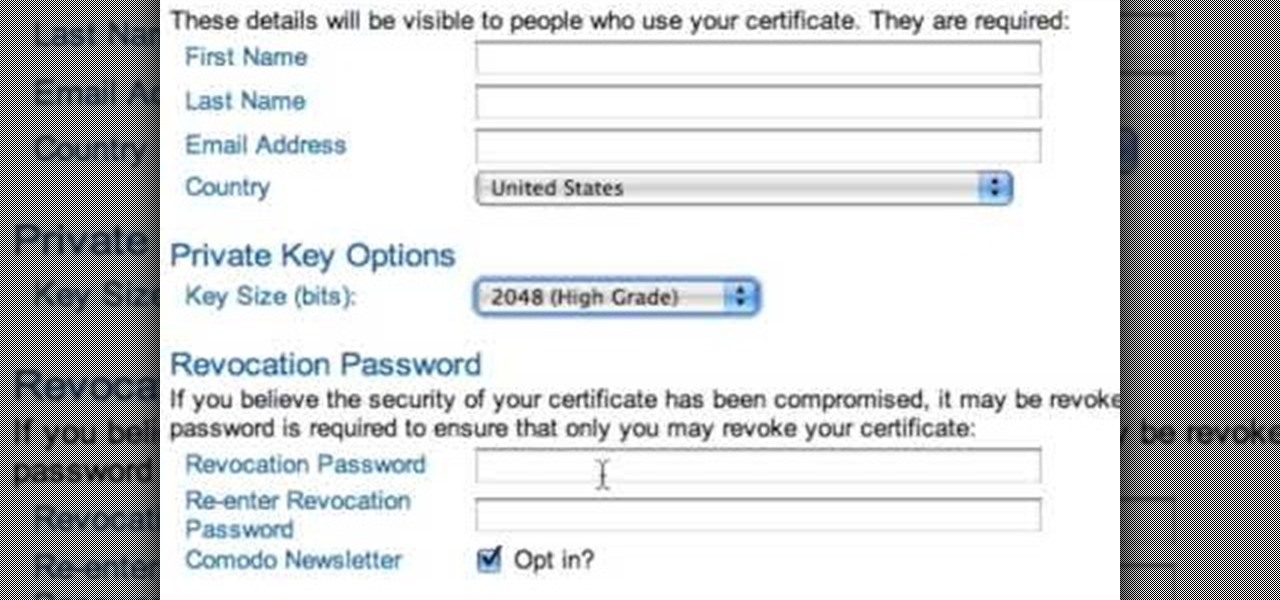
The only people who should read your emails are you and your intended recipients. Protect your privacy with this simple crytography guide, which shows how to obtain a free certificate for signing and encrypting email messages, how to download and install the certificate on Mac OS X 10.5, and how to use the newly installed certificate in Apple Mail.

This is a video tutorial showing its audience how to install Super Nintendo onto an Ipod Touch or an IPhone. The first step is to open Cydia and click on packages. Scroll down and click on Open SSH, install the program and then open it. Then go to games and you can install the Super Nintendo application. Next install SSH Client on your computer and open it. Next plug your IPhone/IPod into your computer and transfer your Super Ninentdo game onto your IPhone/IPod. When you are finished transfer...

In this Computers & Programming video tutorial you will learn how to update websites from Firefox with the FireFTP add-on. Go to the Firefox add-ons page, search for FireFTP, add it to Firefox and install it. Restart Firefox to activate the add-on. Go to tools and click on FireFTP and that will open up a new tab with the FTP client. To configure the FTP to your account, create a new account by giving it a name. The host will be your domainname.com and use the login and the password for the ho...

Some data can be very confidential. In such case you need to encrypt the data so that it does not go into the wrong hands. There are lots of encryption software available to encrypt the data. But to use them first you need to install then and this can take lot of time. You can also use Windows built in compression client to encrypt information. To use this feature you need not install any software and it is a fairly simple process. So select a file that you want to encrypt, right click on it ...

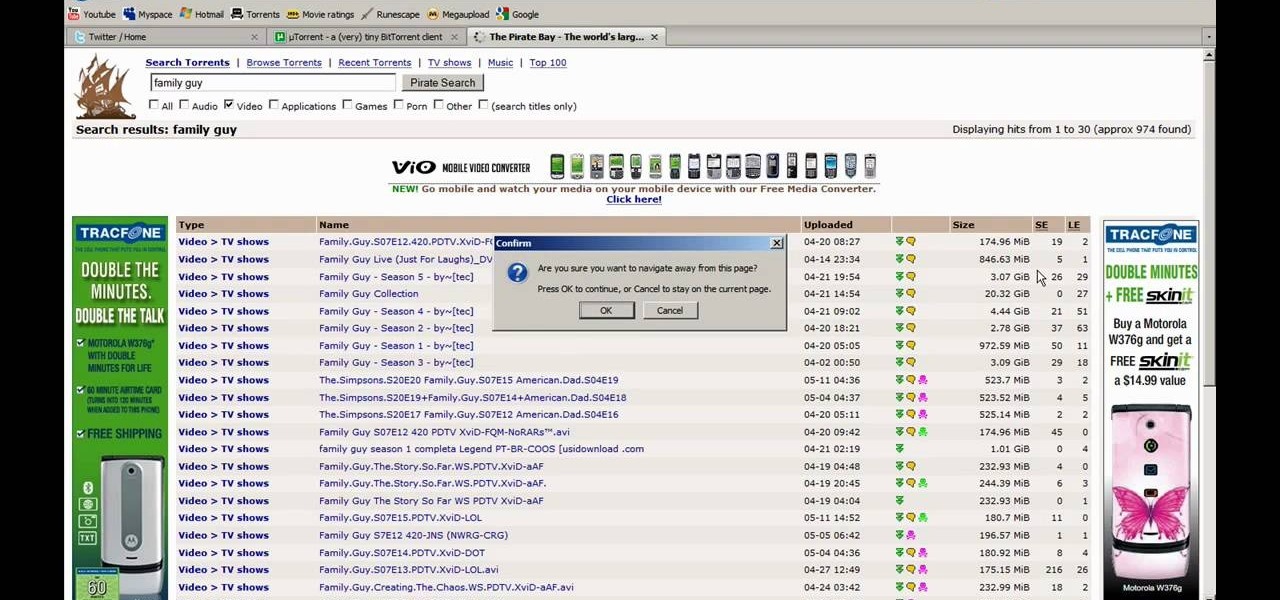
This video tutorial from JdudeTutorials presents how to download a torrent for the first time.To start, open your Internet browser. Browse to utorrent web page.Download and install uTorrent client version, suitable for your operating system (MacOS or Windows).Once you've installed application, browse to The Pirate Bay.This is the largest torrent source in the world.Check Video option under the search bar and type family guy (as an example).Click Enter. A list of torrents connected to family g...

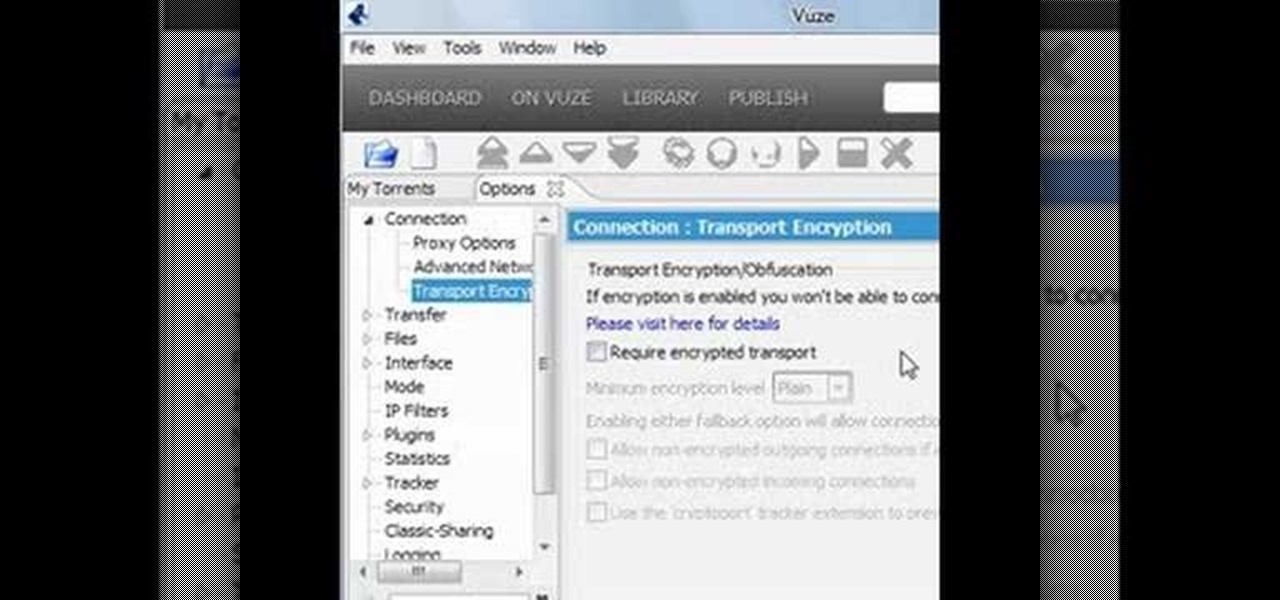
Torrents are a wonderful technology to share your files over the internet. If the data that you are sharing is confidential you may need to encrypt these files before sharing. To encrypt torrents in Azereus, go to tools and select options. From the left hand side menu select the connection option. Select the 'Transport Encryption' option from the connection sub menu. This section is intended for intermediate mode or higher and it is not available in beginner mode. So go to mode and select the...

Enabling Telnet in Windows Vista is a little bit more difficult than its predecessors but it still can be done. This video will demonstrate exactly how to enable Telnet in Windows 7 and Vista.

This is a presentation of how to face toughest interview questions. During most of the job interview, the interviewer is trying to find out your capabilities if the job. They want the client to explore why they want to be working here. They know that you want a job. But more specifically they need to know why you want to work in their firm and also your capabilities. So, you must be prepared to answer for this common question for most of the interviews. First of all you should understand why ...