Being in sales is hard work. After all, the only thing more painful than trying to sell a hand cream or knife set to a stubborn client is perhaps pulling out teeth - without novacaine. And God knows how many times we've hung up on telemarketers because, well, they're a little too persistant.

This 4 part video series is a gift from me to all the other singers out there who have shown me such great love and support. It contains a full vocal warmup that will improve tone, expand range, and increase control. This is pretty much the kind of warmup that I might do with a private client, but it's for you guys - free of charge.

There are at least 24,000 different Android devices, and they all have varying hardware components. This is why many developers publish several unique variants of their apps, which, among other things, helps accommodate all of the different display sizes and resolutions on Android phones and tablets.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

If you're looking for a new Reddit client on your iPhone, look no further than Apollo. Launched with iOS in mind, Apollo is a free app that offers an exceptional Reddit experience, but some of its excellent features — as well as some necessary ones — are hidden behind its "Pro" paywall. Are these extras worth your money?

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

Video: . How to Stop Shrinkage with Shea Butter & the Banding Method!

The video shows you how to calculate capital budgeting with a Texas Instruments BA2+ financial calculator. Capital budgeting will help you determine cash flows for given investments for a certain number of years in the future, thus helping you determine if the investment is worthwhile. The buttons you will use are the CF (cashflows) button, the NPV (net present value) button, and the IRR (internal rate of return) button. The video uses the example of a $10,000 investment that will return $5,0...

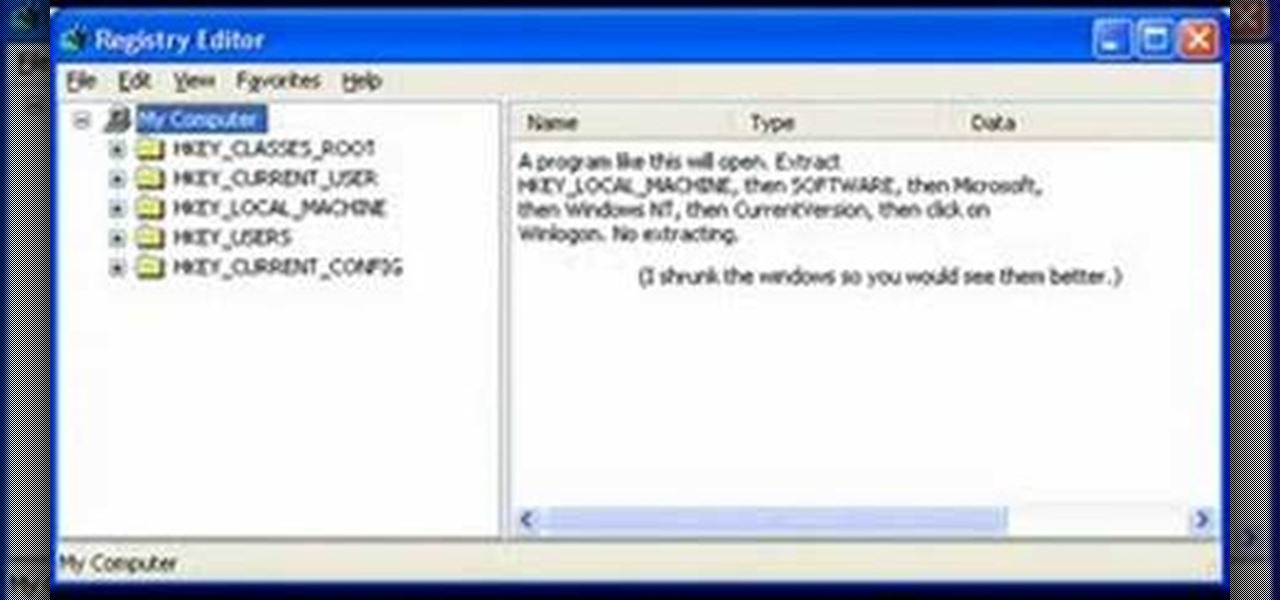
Start by clicking start and type regedit in the search box. Hit enter and when the screen opens go under hkey current user and click on control panel and then desktop. Under desktop go to menushowdelay. Under menushowdelay right click and then click modify. In the box that pops up set the value to zero and click ok. Then close the registry editor. Next you will want to download ram booster 2. 0. Once you have downloaded and installed the ram booster program you will want to edit your options....

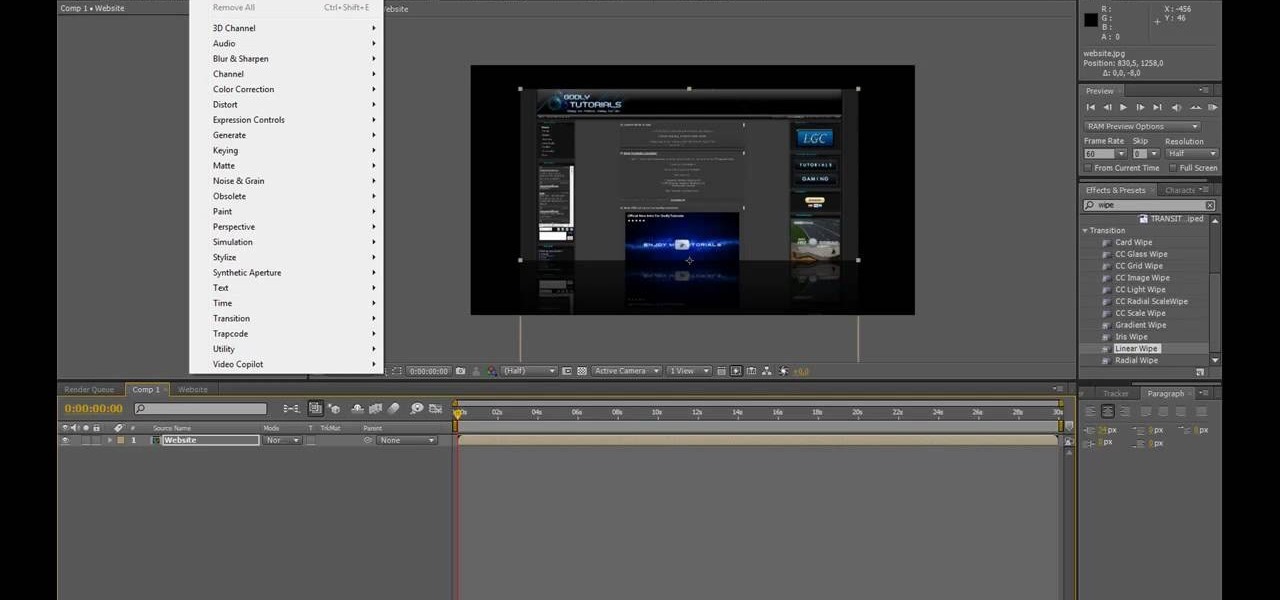
Open After Effects. Create a new composition by selecting "Composition" and "New" from main menu. Use default NTSC DV preset. Keep 30-sec default duration unless you need more time for the video scene to edit. Import several video clips by selecting "File," then "Import" from menu. Navigate to video files you want. Import at least 3 different video files using Import File dialog box. Double click on 1st video file you want to add to your timeline. The file will now open in a video monitor win...

Need to lighten or darken up a digital picture? You can make most of your lightening and darkening adjustments, even before you learn more complex Photoshop features like curves and levels; It's easy. Here's how.

Thinking of selling your car on the internet? Make sure you don’t get taken for a ride. You Will Need

How to install Java JDK (Java Development Kit) Go to the Oracle Java SE Download Page and click "Download".

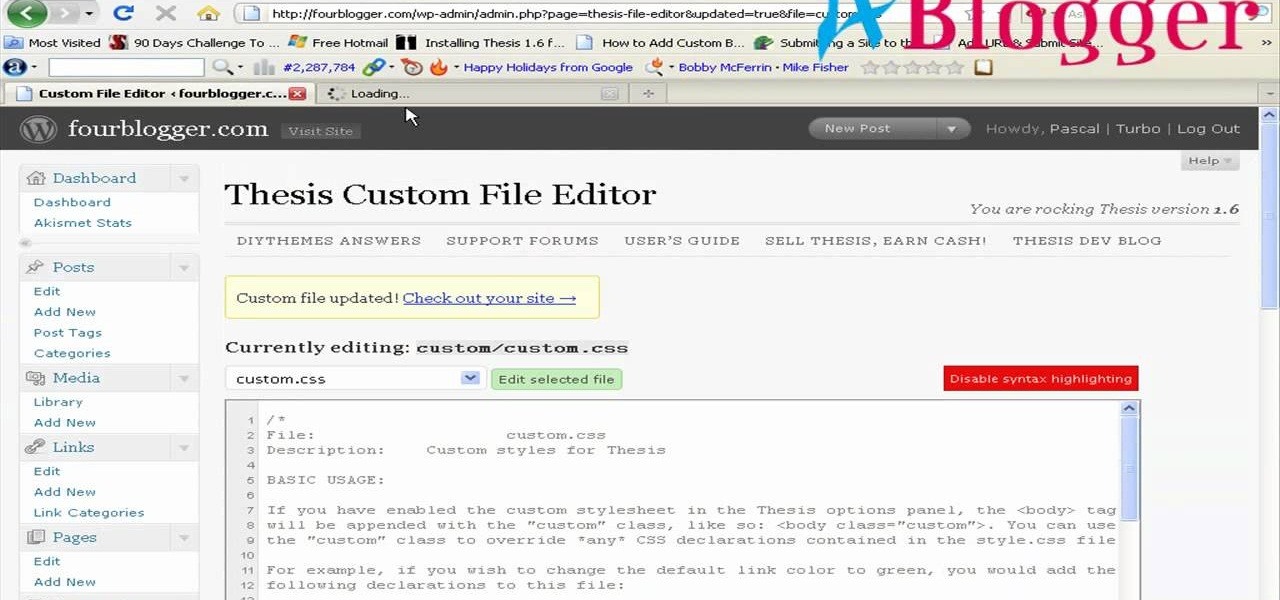
First you need to go to your site and click any post you want and see the simple heading and now you want to change the background. To do this, first you need to go to your word press admin and then click custom file editor in thesis options it will open your code window and here you will have to paste the code which is showing in the video. you will have to paste it in custom.css. After pasting the code you have to click the green save button.

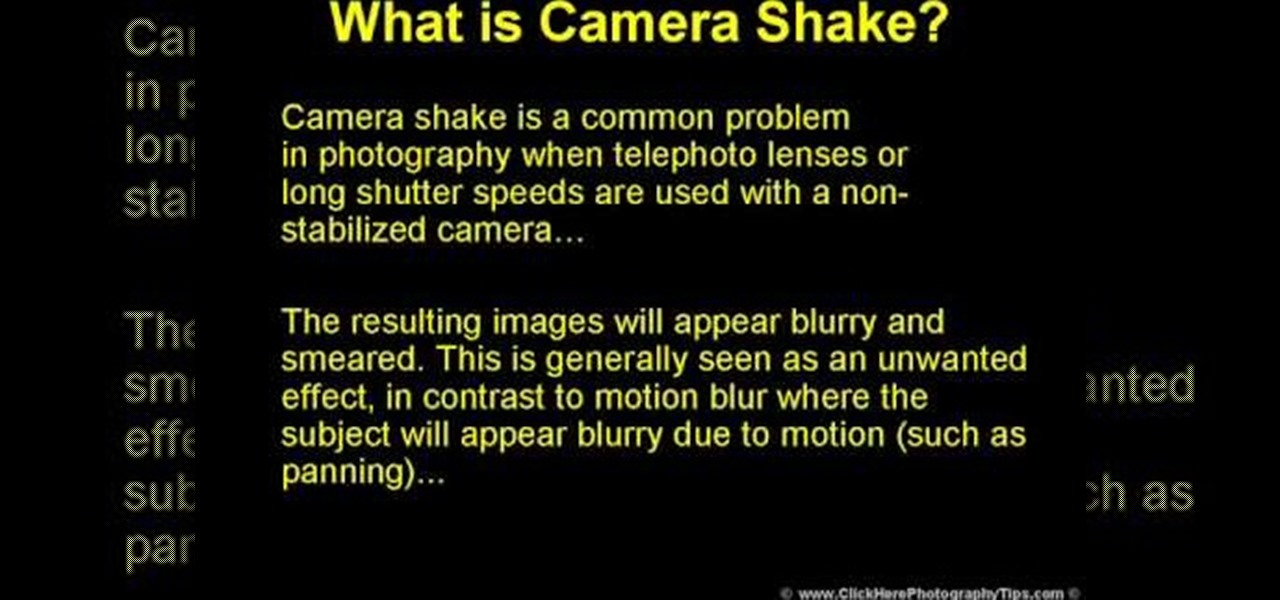
Camera shake is often an unwanted effect in photography, when a telephoto lens or long shutter speed has been used for a camera that hasn't been stabilized. The images subject to camera shake appear blurry and smeared, which is often considered an error - though some photographers find artistic value in camera shake and purposefully try to cause the effect in their art.

In this video tutorial, viewers learn how to speed up the Windows XP Start menu. Begin by clicking on the Start menu and select the Run program. Then type in "regedit" and click on OK. Now select H KEY_CURRENT_USER, go to Control Panel and click on Desktop. On the right side of the window, scroll down the list to find Menu Show Delay. Double-click on it, change the value to 0 and click OK. This video will benefit those viewers who use a Windows computer, and would like to learn how to speed u...

In order to make a smoothie that will give you healthy and glowing skin, you should begin by considering the nutritional value and restorative nature of certain fruits. To make a smoothie that will support your collagen, elasticity, and your complexion, combine the following fruit in a smoothie: blueberries, oranges, strawberries, mango, bananas, and water. These will also provide beta keratin and antioxidants.

In this how-to video, you will learn how to change your start menu text. You will need resource hacker and regedit in order to perform this. First, open resource hacker. Click file and open. Go to 37, and click on 1033. Change 578 to whatever you want the text on the start menu to be. Press compile script. Next, save this file. Now, open regedit and go to software. Go to shell and click modify. Change the value data to the name of your .exe file, which should be saved in the windows folder. N...

Ubuntu and Windows may have trouble syncing time because when they are dual booted, they both assume that your hardware clock is set to a different time setting. Ubuntu assumes that your clock is set to UTC and Windows assumes that your clock is set to local time. Answers Launchpad has solutions to fix the syncing issues. To correct the issue, configure Ubuntu to be set to local time. Launch your terminal window and click on the description box. In the code string change the UTC default value...

In this video the instructor shows you the diameter, radius and also how to find the circumference of a circle using a cookie as an example. When you draw a line against the cookie passing through its center and touching its boundaries, it is a diameter of the circle. Radius of a circle is half the diameter of the circle. The length of the circle along the border of the circle is called circumference of the circle. The formula to compute the circumference of a circle is 2 * Pi * r, where r is...

ITStaff teaches you how to design casino chips in Adobe Photoshop. You start off with a white or grey circle which will be the chip itself. You need to start decorating this so you create five trapezoids and space them equally from one another. Give them a dark red color. Next you create a red circle in the middle, touching the bases of those trapezoids. Add a crown or a symbol created or from the Custom Shapes menu. You also need to create a value so type in a number and add the dollar sign ...

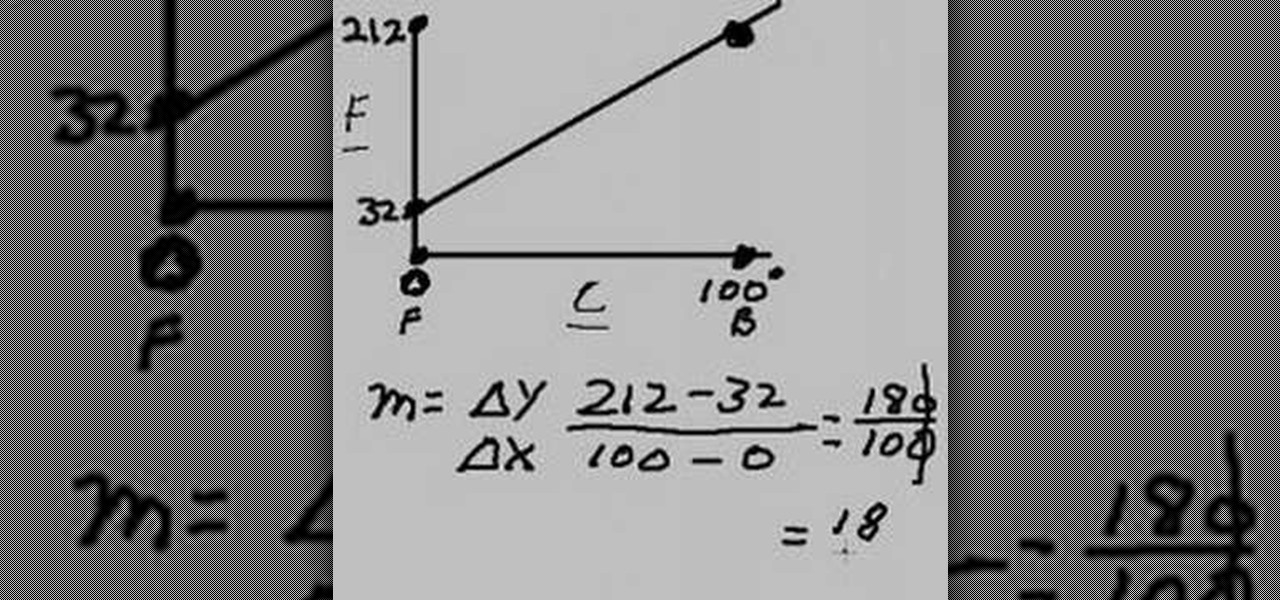
The video teaches how to convert degrees Celsius to degrees Fahrenheit. First the boiling points of 32 degrees Fahrenheit and 100 degrees Celsius are plotted on the Y and X axis. Then a line is drawn to join them both. The value m is delta Y (boiling point minus freezing point, i.e., 212-32)/ delta X (boiling point minus freezing point, i.e., 100-0). So m works out to 180/100 or 1.8. Then the formula y=mx+b (intercept of y = 32) is used, substituting X with Celsius and y with Fahrenheit, to c...

In these PHP basics video the tutor shows how to do form processing. Handling forms in PHP is basically the main functionality of PHP. The forms in HTML take the values of a from and send them to the PHP in real time to do the form processing. In this video the tutor shows how to make a HTML form from the scratch inserting a form into it with some fields and buttons. Now he makes the form post a method to a PHP page when you submit it. Now he shows how to make a PHP file from the scratch by w...

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough, you'll always be looking for more...

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough, you'll always be looking for more...

Your ability to control exposure in the Camera app is much better in iOS 14. Instead of setting the exposure for a single shot, you can also lock an exposure compensation value for an entire session while you take photos and videos. A session ends as soon as you exit the app, but you can also remind your iPhone to use your last used ECV the next time you open Camera.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

It's a good sign for any emerging technology when one of the leaders of an industry adopts it. So when Mastercard, a brand so recognizable that it dropped its name from its logo at CES last year, decides to develop a mobile augmented reality app, the moment is a milestone for the AR industry.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Great news if you're looking to upgrade to either the S10e, S10, or S10+. Samsung has a trade-in program that's offering potentially massive discounts of up to $550 if you preorder one of their flagships right now — but only for certain phones.

If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

With all the recent activity around augmented reality, the possibilities involving immersive computing and commerce are quickly becoming obvious, and digital payments giant PayPal has no plans to sit on the sidelines

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.