
News: US Military Shows Off Modified HoloLens 2 Augmented Reality System
New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.


New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

In the business world, it's sometimes said that "where there's smoke, there's fire." At Snapchat parent company Snap, Inc., it appears the equivalent of smoke is executive turnover.

Mobile augmented reality pioneer Blippar has now completed its fall from hopeful AR startup to the immersive computing history books.

Any real Star Wars fan knows that fear is a path to the dark side, as it leads to anger, and then suffering. For players of Star Wars Jedi Challenges, though, access to the antagonistic side of the Force is now available through their mobile apps.
No matter how good a display is, the idea of perfect color calibration is subjective — some prefer warmer more saturated colors, while others prefer the calmer cooler side of the color spectrum. It is almost impossible to create a single color calibration that everyone can agree on out of the box. The display on the Pixel 2 XL was specifically calibrated with a more realistic color profile in mind.

Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film).

Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal.
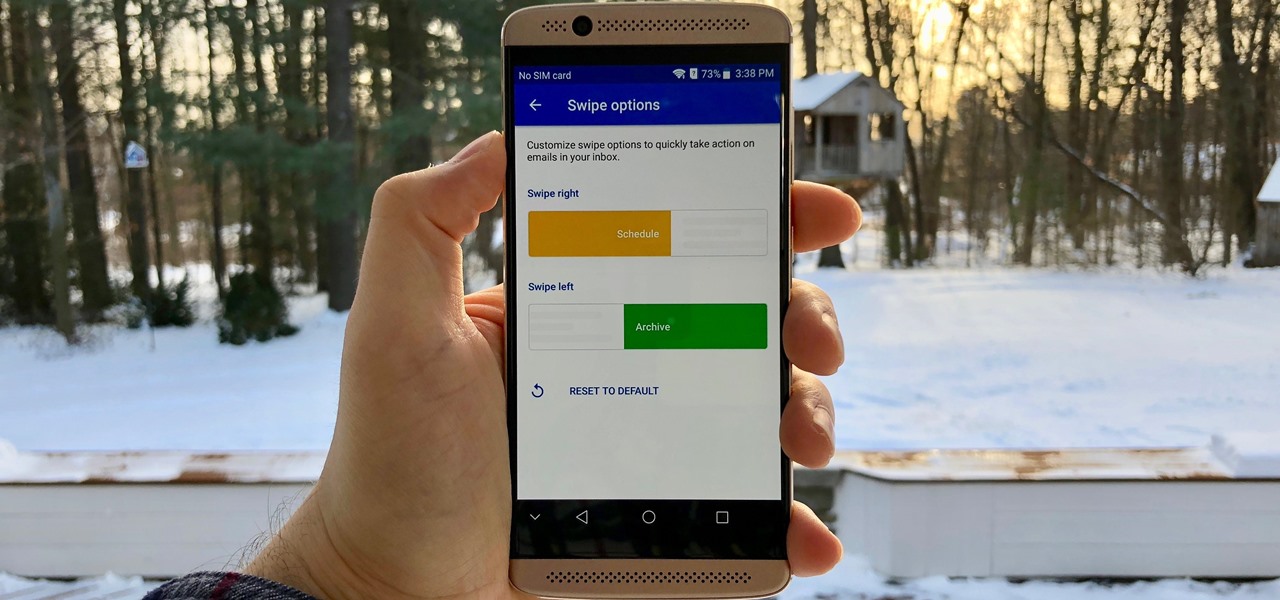
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.

Hitman Sniper topped our roundup for the best premium shooting games, and it's easy to see why. Straightforward yet intense story. Awesome visuals. Stealthy action. Strategic gameplay. Hitman Sniper is easily the best sniper game available for your smartphone, and it's currently free on Android for a limited time, as well as discounted for iPhone.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

After Ford's CEO Mark Fields' three-year tenure failed to keep up with the driverless industry and resulted in a 40% drop in shares since Field's took over in 2014, Ford is going in a new direction. Jim Hackett, who was previously chairman of Ford's self-driving division, has succeeded Fields as the company's new CEO.

If you've been longing since the '90s for the total Clueless experience of virtually trying on clothes, you missed out by not attending London Fashion Week earlier this year.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.
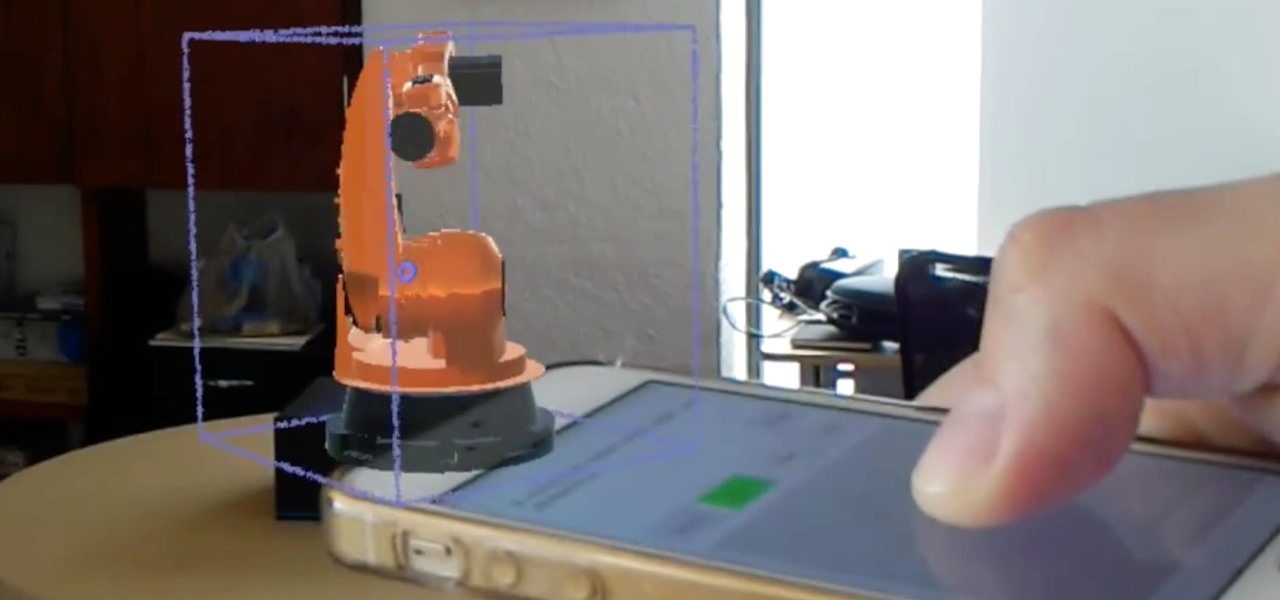
We've highlighted the projects of Wavelength Studios a few times over recent months for their work in the augmented and mixed reality space. Since receiving their HoloLens headsets, they've been hard at work on both development community projects as well as efforts for clients. This brings us to their latest work—a way to control holograms on the HoloLens with our pocket-based modern miracles, also know as smartphones.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Back for the second part,
For those times when you can't get something done by clicking a few buttons with your mouse, the Windows command prompt has always been an indispensable tool. But as much as advanced users have relied on this useful utility, it hasn't seen a significant update since the Windows 95 days.
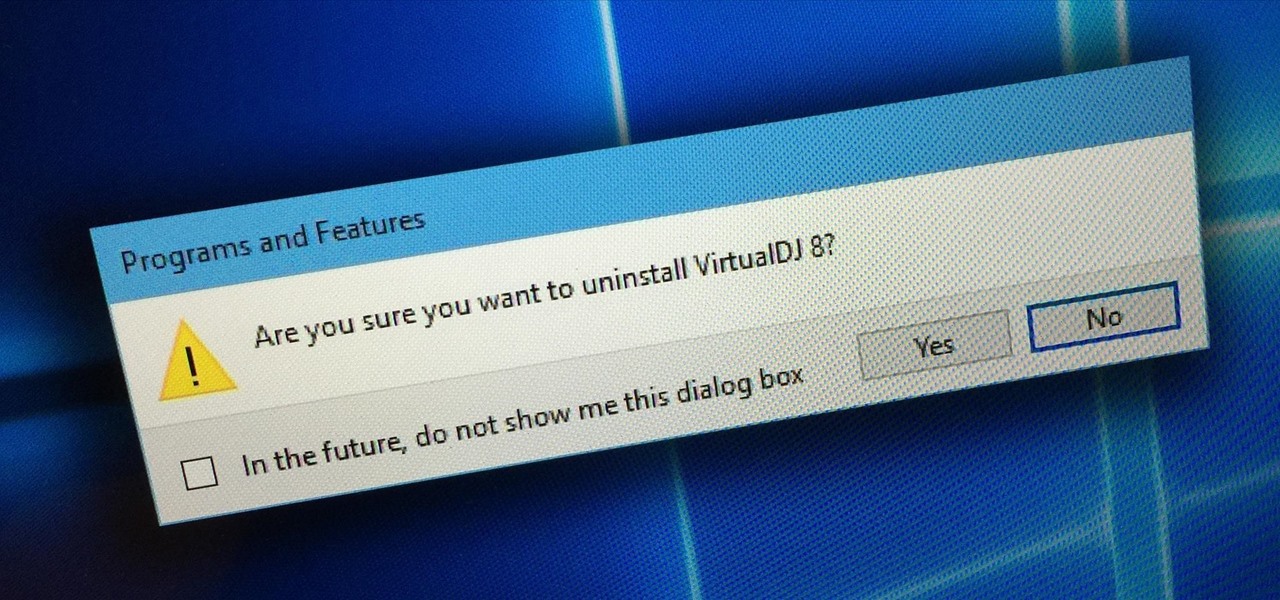
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.
For every contact photo you add, Android keeps two copies. The first is stored at a 720p resolution, and this is used for high-definition imagery when you're looking at a full-sized contact card. But the second image is only 96 pixels by 96 pixels, and this is used for all thumbnails throughout the operating system.

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.
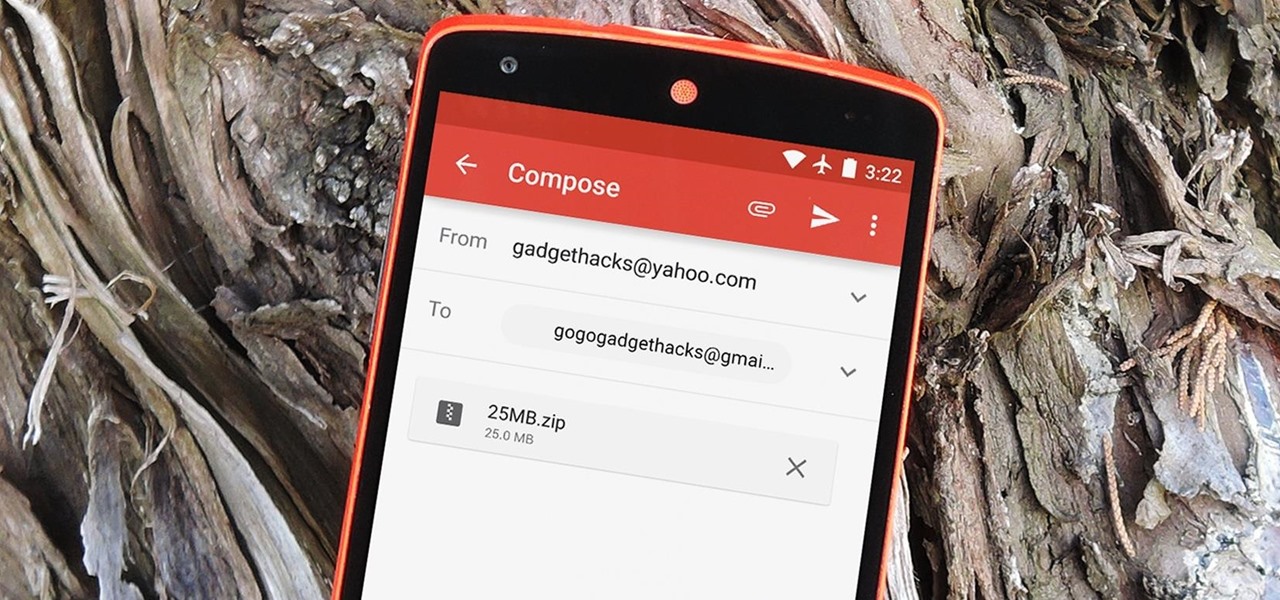
The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

Android's auto brightness feature was recently updated, and as of version 5.0, a new "Adaptive brightness" feature was added. This allows users to set a preferred overall brightness level, but still have the ambient light sensor adjust the backlight accordingly.

If you're the de facto tech support person in your family or circle of friends, you know how frustrating it can be to have to hold someone's hand and walk them through every troubleshooting step. Luckily, several options now exist for you to remotely access a Mac or Windows PC, which effectively skips the middle man and lets you get straight to fixing the issue yourself.

One of the most rewarding things about jailbreaking is theming. Unlike Android, iOS doesn't allow you to make small changes to certain aspects like the icons or the lock screen, so jailbreaking facilitates the ability to make some of these desired changes happen.

Back in iOS 7, Apple decided that it was actually a good thing to make the volume controls HUD translucent. This, of course, means that whatever you're watching on your screen will be obstructed temporarily whenever you adjust the volume.
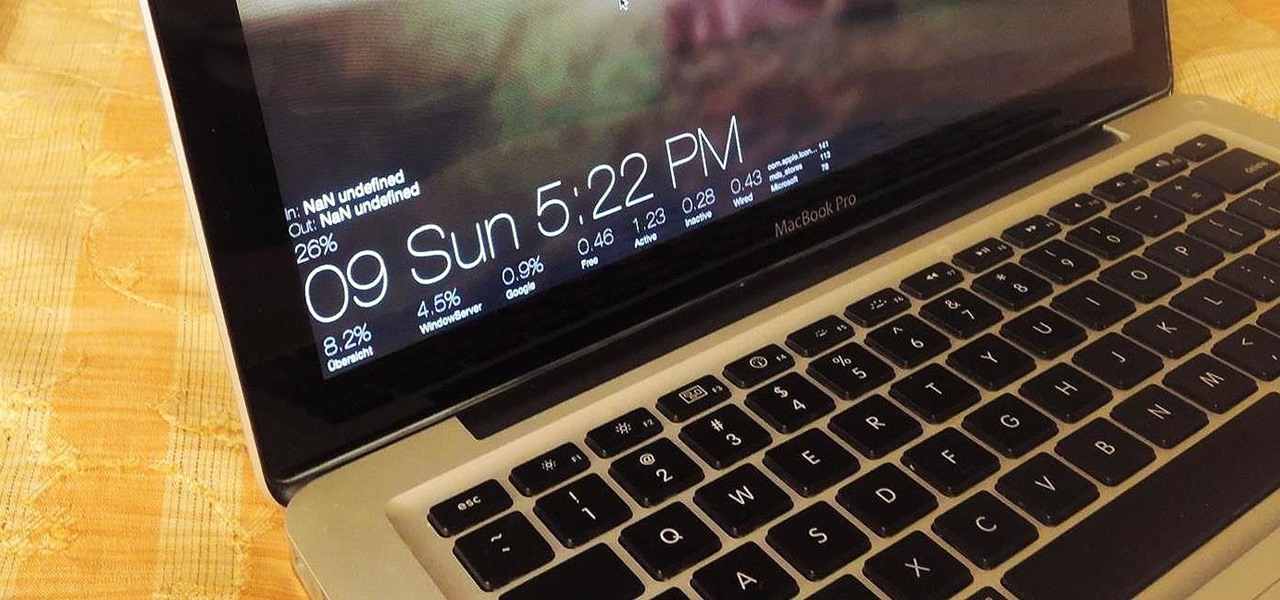
Apple hasn't been the most avid supporter of widgets over the years. Yes, they added them to the Notification Center in Yosemite, but that requires a drawer to be opened and closed whenever you want to check them. In my search for a better solution, I came across Ubersicht by developer Felix Hageloh.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Since the release of the Galaxy S5 back in April, the process of converting older models, like the Galaxy S4, to replicate the look and feel of the newest S-family member was inevitable. Galaxy users didn't want to be left out, and for good reason. The revamped interface of the S5 introduced a new color palette that was a definite improvement from the flat boring colors on older models.
Though they share the same name, the HTC One and OnePlus One have completely different sound quality. HTC had put a lot of time and effort into fine-tuning their BoomSound technology, while OnePlus is still fairly new to the game, with brand recognition being a much greater objective than awesome speakers.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

When theming Android, it's the little touches that complete the look, making your device yours. If you're rooted, you probably know by now that there's virtually nothing you can't change the look of on Android.
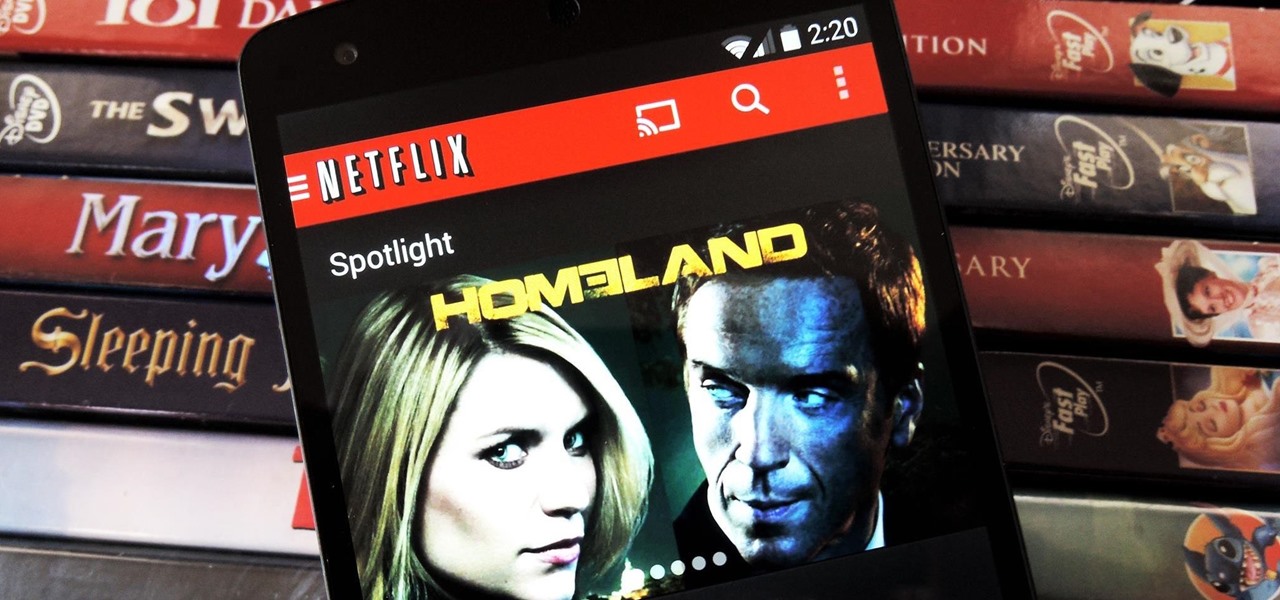
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Have you ever heard the expression "Dress for Success" or "Clothes Make the Man"? When you're wearing a perfectly fitted designer shirt, something inside just shouts, "I look good" and when you genuinely think that, those feeling are radiated outward to all your come in contact with. That said, what kind of designer shirt are you interested in, a bargain basement discount, or one tailored made, outlining your best features?