When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

Transition animations are an essential element of any mobile operating system. They give the user a sense of what's happening on the screen, where the apps are coming from, and where they're going.

Have you ever fallen victim to a clever Jedi mind trick? Don't worry. It happens. There are evolutionary reasons as to why our brains sometimes give into the oldest tricks in the book. Fortunately, the more you understand the tricks of a salesman, the easier it is to avoid their gripping psychological influence. Clue #1: Too Much Specificity

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"

If you want to tool around in the user interface of Star Trek Online and modify your client, this video shows you how. Do note that Cryptic doesn't support modding, and it could break your system. But if you want to alter the mouse pointer or your camera point of view, here's how!

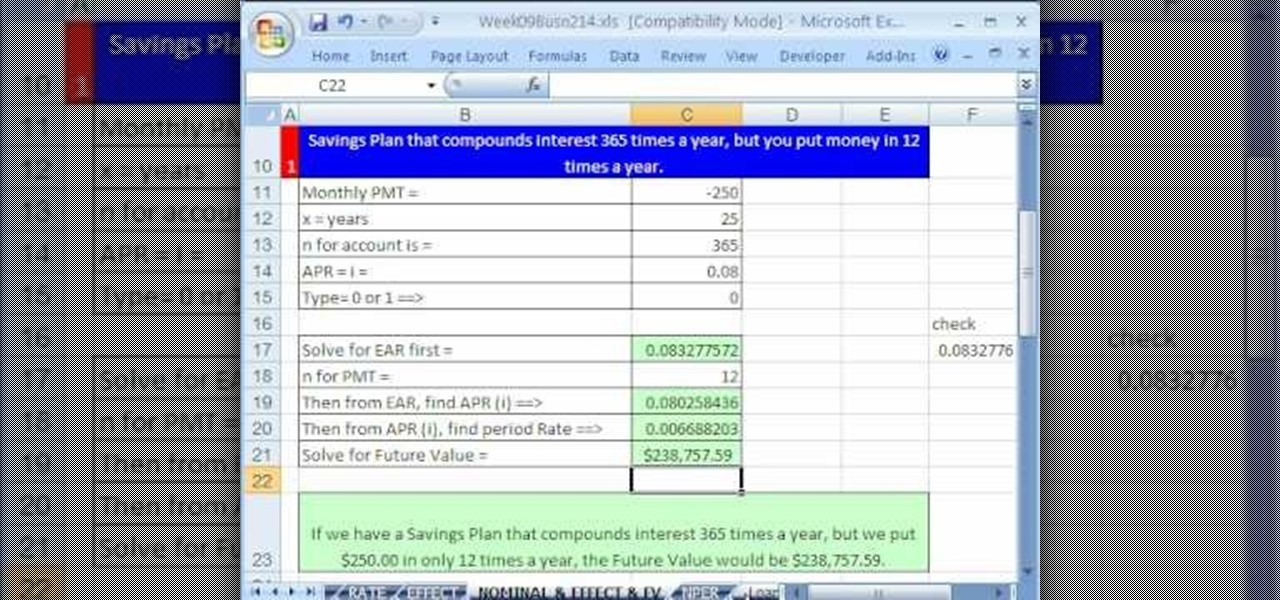
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 48th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to use the RATE, EFFECT, NOMINAL and NPER Excel functions to solve the following problems:

What's the quickest way to get to an application on your Android phone? It's a shortcut icon, much like on your Windows and Mac computers that take you to the application quick without having to dig in your applications folder. So how do you add a shortcut on your phone? Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up shortcuts on your Android enabled cell phone.

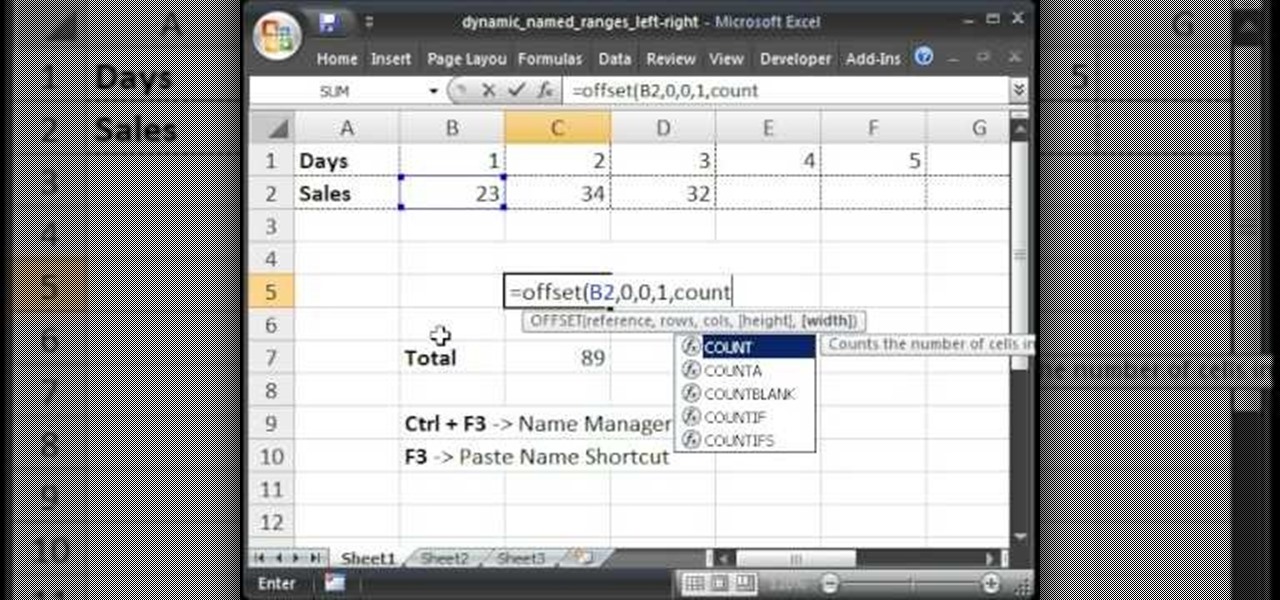
Teach Excel describes how to create a dynamically updating named range that goes from left to right using Excel. First, you define the named range by highlighting the cells containing numbers in a certain row. In the name box to the left of the formula bar, type the name of the data. In this example, the numbers correspond to sales, so type "sales." To check if the named range works, click on an empty cell and enter =sum(sales). That should return the sum of the highlighted cells. However, as...

This video teaches viewers on how to inspect a motorcycle for damage after an accident as well as documenting it. The most important thing you need to do after an accident is to document all parts of the damage by taking photos of the damaged parts. Start by verifying the VIN number or Vehicle Identification Number and take a picture of it, take a photo of it. After that, get a photograph of the mileage on the dash area of the motorcycle. If there is other important information that needs to ...

Ron Watson of Positive Vibe dog training studio in western Michigan with Frisbee Foundations and Dog mantic Dog Training TV explains how to do vault, stall, and rebound discrimination dog training. First, add value to a barrel by using eye contact. When the dog goes to where the reinforcement happens, feed it treats. Then order the dog off the barrel. When the dog jumps up by its own volition, then you know the technique is working. Then, set a linear vault by saying, top, and tossing the tre...

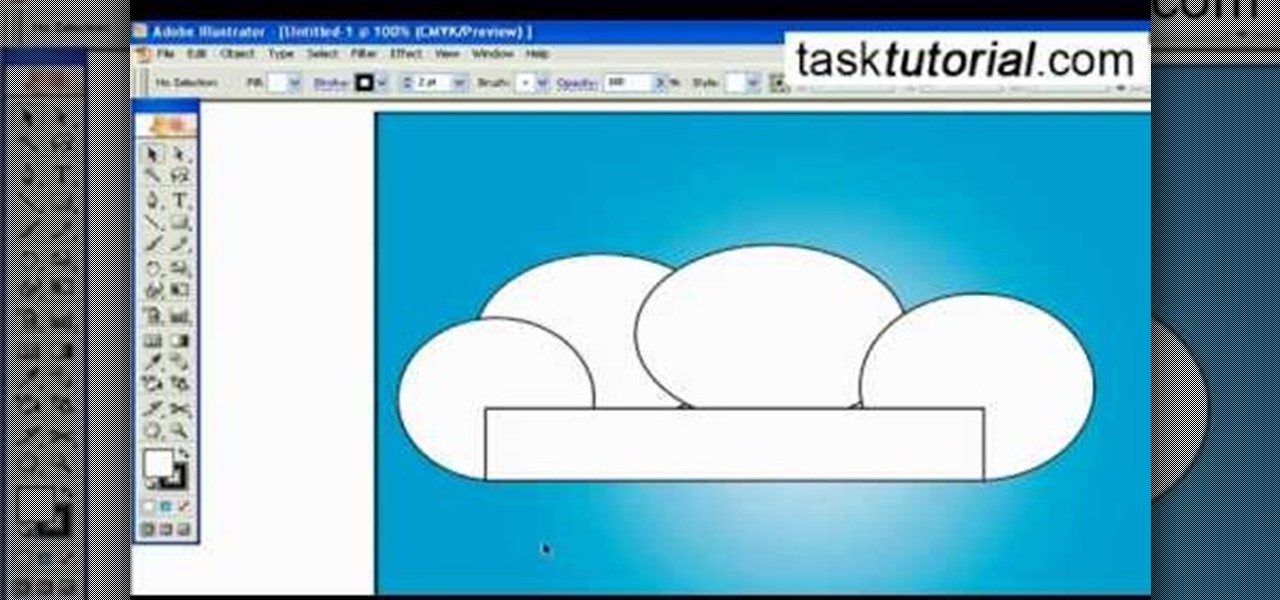
A great free video training from tasktutorial on how to create a cartoon cloud in Adobe Illustrator. All the project files are available to download for free at the Adobe website. First create a background: select the rectangle tool then create a new layer and draw a rectangle across the canvas. Now select the path, go to gradient and edit the it a bit until it's a shade of blue. Lock the gradient and create a new layer. Select white fill color and 2 point black stroke and draw a few oval sha...

In this six-part video tutorial, learn how to create an access database. The following six parts go over the following:

Souls have their value in the Xbox 360 game Darksiders. Learn all you need to know about the Crossroads level Charred Council. War finds himself before the Charred Council who accuse him or disobeying the laws of the Seven Seals. War feels that he was in the right to intervene and pleads to be sent back to earth to discover how the Destroyer invaded earth without breaking the Seven Seals. Being that War has been stripped of all his powers, the council sees it as a death sentence which is a wo...

What? Cheating Bloons Tower Defense 4 without Cheat Engine? Unheard of! Guess it only takes a glitch though to throw the whole game off balance.

This is hacking for Bloons Tower Defense 4. Newly released, this game can't stand resistant to hacks and cheats. There's no way you can loose at Bloons!

Bejeweled Blitz is a Facebook game. Learn how to hack Bejeweled Blitz with tricks, cheats, hacks. Watch this video tutorial to learn how to cheat on facebook's Bejeweled Blitz (07/27/09).

Check out this episode of Brian Brushwood's Scam School from Revision3 to find out how to pull the best cons, bar scams and magic tricks. It's rare to find a trick that you can actually fool yourself with...and that's exactly what you get with this episode!

Check out this bar trick of super sonic hearing. It is the trick that fooled Einstein by Brian Brushwood and Revision3's Scam School. Watch Brian scam Olympic gold medalist Jonny Moseley with a few coins, and some algebra!

Second Class Boy Scouts work on building their outdoor survival and camping skills. Compass work, nature observation, camp tools, and swimming are areas where new skills are mastered and demonstrated. A second class scout, having completed all the requirements, should be able to lead a hike, care for his own equipment, set up a campsite, and perform basic first aid.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

Increase arm strength with side dumbbell lateral raises. Learn how to work out with dumbbell exercises in this training video. Take action: begin with moderate weight, keep shoulders back and chest high with abs tight, doing slow and controlled movements. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifti...

Work out and getting in shape with dips. Learn how dip exercises can increase your strength and fitness in this training video. Take action: do not lock elbows, upper arms stay parallel to floor, and no partial reps, use full range of motion! Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she en...

Strengthen the arms and the core with seated laterals. Learn how lateral exercises and weightlifting can keep you fit in this video. Take action: begin with a moderate weight, use slow and controlled movements, but do not keep hands above elbows. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and sh...

Keep arms stiff for lateral pull downs. Learn exercises for the lats in this training video. Take action: this is a great exercise for swimmers or surfers, keep shoulders back and arms straight, but do not curl shoulders. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training aspirin...

Increase strength in the triceps with triceps kick backs. Learn about muscle growth with arm exercises in this fitness video. Take action: keep head in line with spine, only movement should be with lower arm, and keep core tight. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training...

Strengthen the triceps with triceps push ups. Learn how to increase arm strength with triceps exercises in this training video. Take action: position hands in diamond shape under chest,so that the elbows move straight back, and maintain plank position. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting ...

Add deep squats to your workout to really strengthen your legs. Learn how exercising with squats can strengthen the legs in this fitness video. Take action: feet wider than shoulder-width, toes pointed out, keeping abs tight and chest high, squeeze quads at top of movement. Michelle, the instructor in this how-to video, is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specia...