Our hands aren't necessarily getting any bigger, but smartphones still seem to be getting larger and larger. With average cell phone display sizes nearly doubling since 2007 (leading to new terminology like "phablet"), reaching all corners of a screen can become nearly impossible with one hand. Granted, most larger devices like the Samsung Galaxy Note 3 and Galaxy Note 4 come with a one-handed option to make navigating easier, but other popular devices like the Nexus 6 don't. While it may see...

CyanogenMod has been building upon open-source AOSP apps for many years now. They've made improvements to apps like the stock SMS client, the stock Audio Mixer, and a whole slew of others.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

In a long-awaited move, the popular messaging platform WhatsApp has finally made its official web debut. Desktop and laptop owners will be happy to know that they can now message their favorite contacts directly from their computers, without the need to install additional apps.
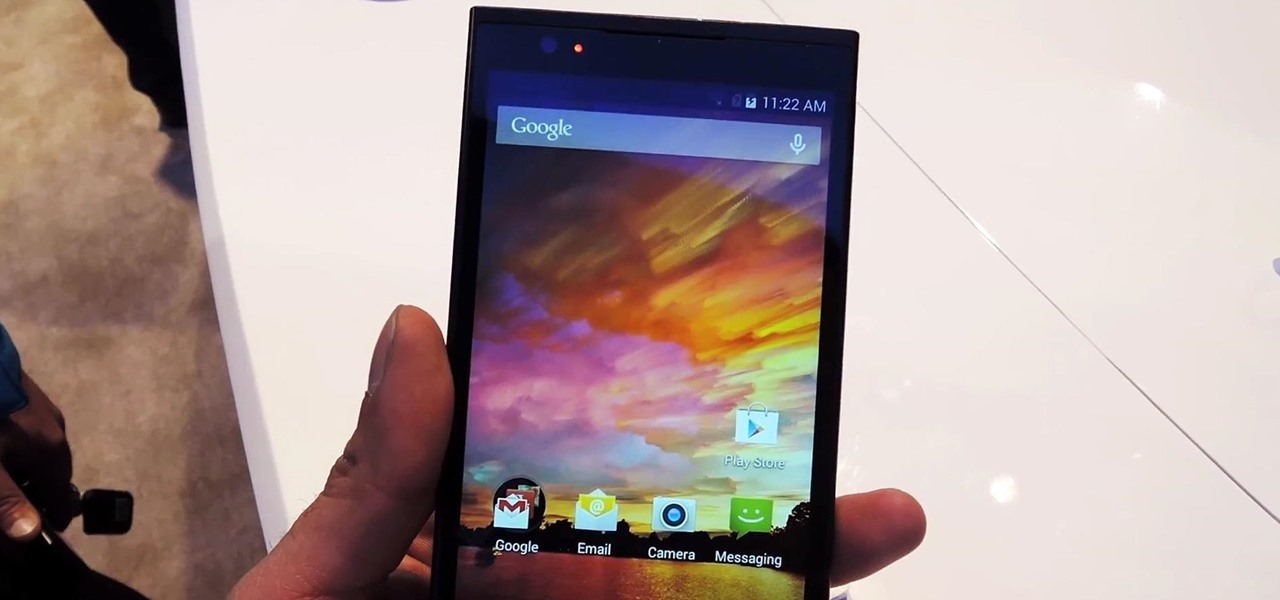
Sometimes specs aren't everything, especially if you prefer value over the bleeding-edge. Enter the ZTE ZMAX, an Android phone that you can get right now for less than $200—cheaper than even the Nexus 5 or OnePlus One. If you're looking for a cheap high-end phone, it's hard to go wrong with one that sports a 5.7-inch display, expandable storage, and a massive 3400mAh battery that'll easily get you through a full day of use.

Just in time for the holiday festivities, iOS developer Tristan Kennedy has created a snowy HTML widget for your jailbroken iPhone's home screen called SnowScreen. Simply apply the widget and you'll have a falling snow animation layered over whatever wallpaper you already have. Without further adieu, let's show you how to apply this tweak.

Sense 6 came with a ton of new features for the HTC One, but for some reason, HTC decided to keep one of them hidden to all non-Harman Kardon editions.

BoomSound has spoiled me when listening to music on my HTC One M8, but when someone comes into my room, it can be a hassle trying to quickly pause or mute my music.

Your shiny new HTC One M8 is a pretty stellar device. From controlling your entertainment center to lock screen gestures and camera shortcuts to being pretty damn indestructible, this device has a lot going for it.

Numbers are everywhere in life, and some are better at doing the math than others. Unless you're Gert Mittring, it's safe to say you use the calculator app on your tablet just as much as I do, and it's often disrupting your other tasks.

If you're a user of Google Play Music, but not a fan of being relegated to a browser tab, I've got you covered. Developer Sajid Anwar has created a desktop client for Google's music service, but since he made no attempt to hide logos and trademarks, it may not be long before the app vanishes completely. So get it while it's hot...and before Google takes it down.

Locking up your iPhone with a passcode prevents mischievous friends from looking at your pics and emails, and makes it harder for thieves to access your data before you get around to wiping it. For even more security, there's the password option, which gives you more than just 4 lonely digits.

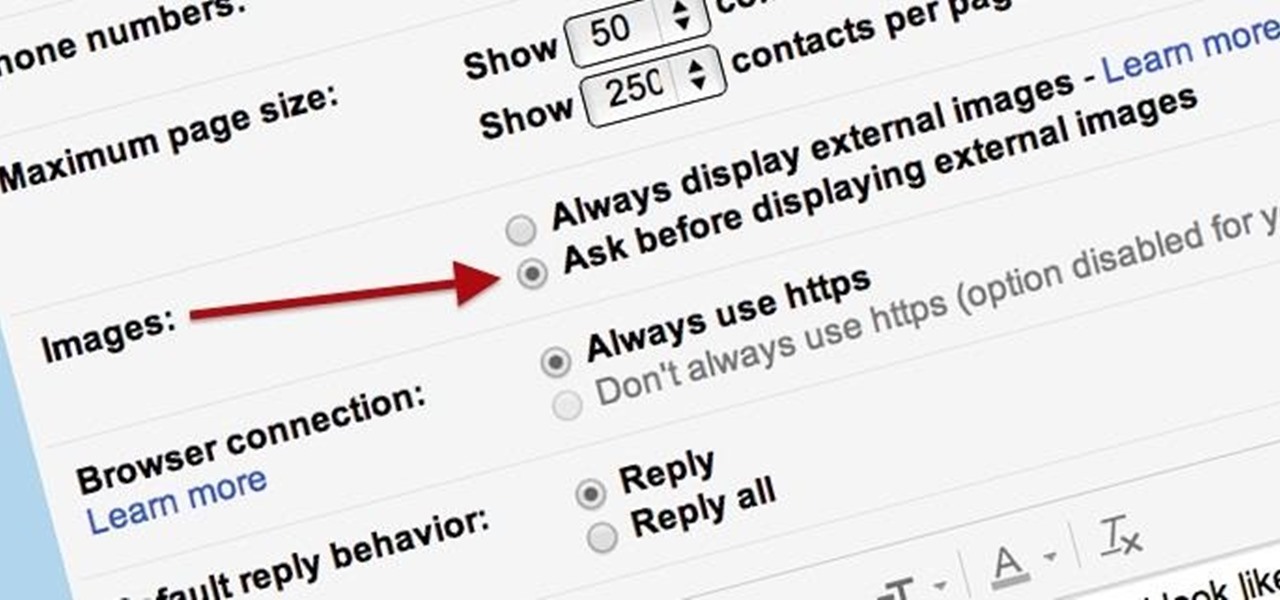
Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

In this Video Tutorial I show you a profitable and fun way to Earn Linden Dollar in Second Life. Linden Dollars is the Money in Second Life and you need it for almost everything you do (actually it is just like in First Life).

Having your phone ring loudly in a quiet environment could be potentially embarrassing for you, but also quite annoying for everyone else that didn't forget to put their smartphone on silent. Whether it's in class, at work during a meeting, at the library, or a movie screening—you can bet that someone's phone is going to ring loudly, pissing some people off. You don't really want to be that douchebag that interrupts a movie or the middle of a lecture with their annoying ringtone just because ...

Facebook has been revamping its Messenger apps these past few months, trying to lure in more users. Competing in an already crowded market of third-party messaging applications, Facebook Messenger just upped the ante, by introducing voice messaging.

As enjoyable as Facebook can be at times, it can also be a great distraction and even better deterrent of getting work done. A quick "Oh, let me check my notifications" can turn into hours and hours of Facebooking, and before you know it, you're already on your 7th Wikipedia page, all thanks to that status your friend posted. The reason I mention this is because Firefox's new 17.0 update includes many features, but the one that's been making the rounds online is the integration of Facebook Me...

An isomorphic (or self-transposing) keyboard is "a musical device where a grid of notes is displayed to the user and the interval change between notes in constant for any given direction." For those of you who didn't grow up playing the piano like I did, that basically means that it lets you move between keys easily without having to learn new patterns because the keys are laid out so that a chord is the same pattern in every musical key.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

We all expect a little something on our birthdays, so why should those expectations drop when we are talking about our gaming systems? Microsoft has started handing out birthday gifts to its Xbox LIVE Gold members with their new MyAchievements rewards program. Those eligible for the gift will automatically receive the offer on their dashboard. To be eligible for the free gift, you must be:

If you've ever found yourself wandering about a room, holding your phone up to the sky searching for a signal, this is just the trick for you. Edward from Redmond Pie found a great way to configure the readout with just a simple phone call, making your iPhone display its exact signal strength in decibels (dBm). Step 1: Put Your iPhone into Field Test Mode

In this tutorial, we learn how to resize thumbnails in Windows XP. First, close all the windows on your computer, then go to your start menu. Next, type in "regedit" under "run" and then click "enter". Now you will see a registry editor, find your current user path when you get to this page. Now, go under the software folder, then the Microsoft folder, and then the Windows folder. Next, go under "explorer" and create a new "DWORD" value called "thumbnailsize" and set a value between 32-256. A...

In this math lesson we will learn how to solve a proportion word problem. Watch the video to learn how to set up a proportion, solve it, and interpret the answer.

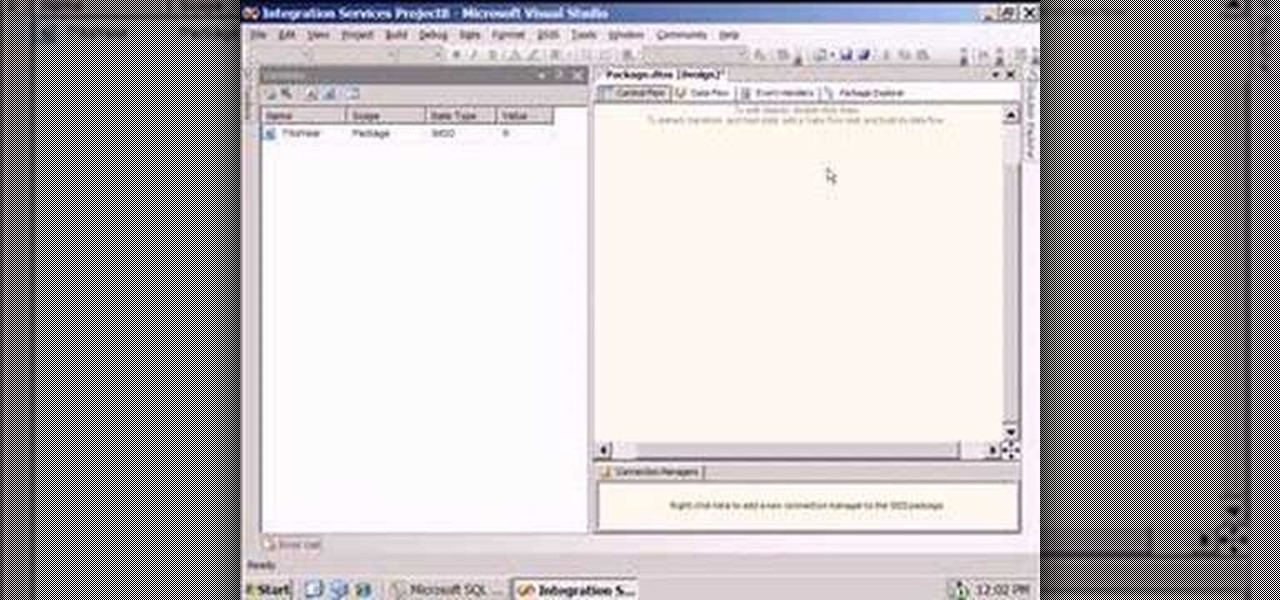
Expressions are new in SSIS (meaning that they were not in DTS) but they allow you to create extremely flexible packages. Expressions can be used to assign values to variables, help you determine whether to execute a task, and to assign properties. If you ever found yourself writing ActiveX code (VBScript) in DTS to determine which task to execute based on a variable's value, then you probably can forego the scripting all together in favor of expressions! They are very powerful in SSIS and yo...

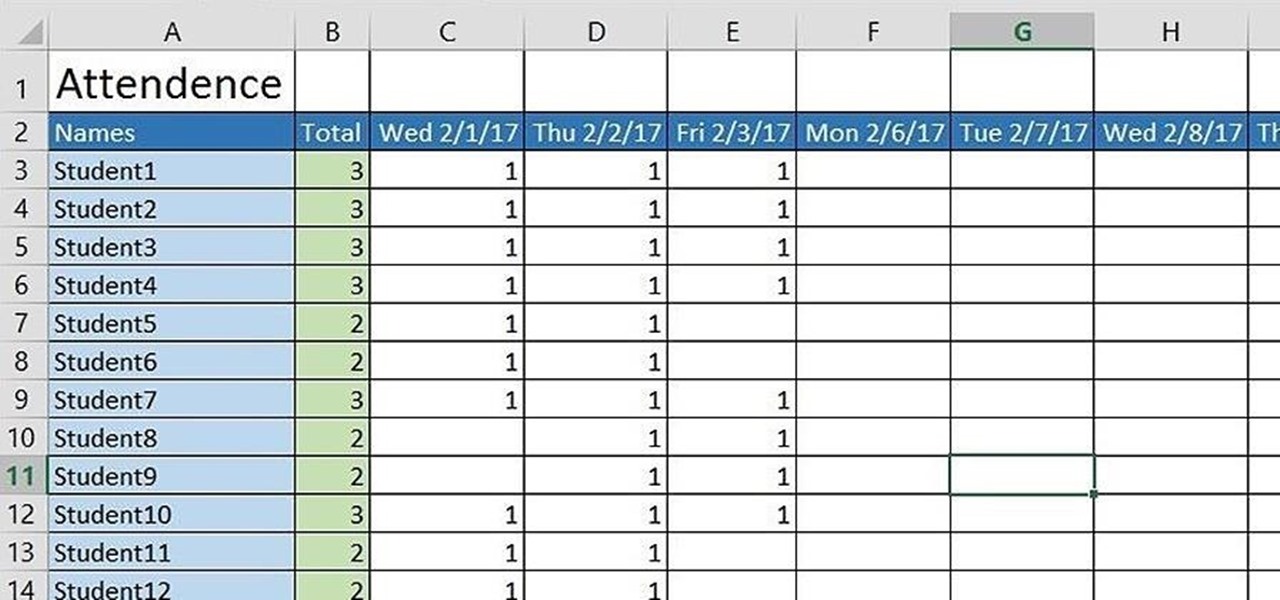
If you're a teacher in any type of school, whether it's high school, college, or middle school, it's imperative that you keep an attendance sheet. The paper and pen route can get pretty messy, and very disorganized, and that's where Microsoft Excel comes in. With this software, you can create a simple yet functional attendance sheet to keep track of your students.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

SyncVue announced at NAB that they would be offering a new version of their remote collaboration software for editors and producers. Well the long awaited update is finally here and all existing SyncVue users will definitely want to grab it. The functionality is improved and the new features are killer. So check out this quick little video tutorial on setting up and using the new version of the software, This walks you through the newest features and how to basically get around.

So now that we know what the iPhone 13 and iPhone 13 Pro and their respective mini and Max versions are all about, you've probably made your decision on whether or not to upgrade (or swap over from Android) during this cycle.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

This week's Market Reality covers a variety of business news from acquisitions and partnerships to competitive and technology assessments to quarterly financial results.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Part 1: What is Popcorn Time? Part 2: What is a torrent?

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.