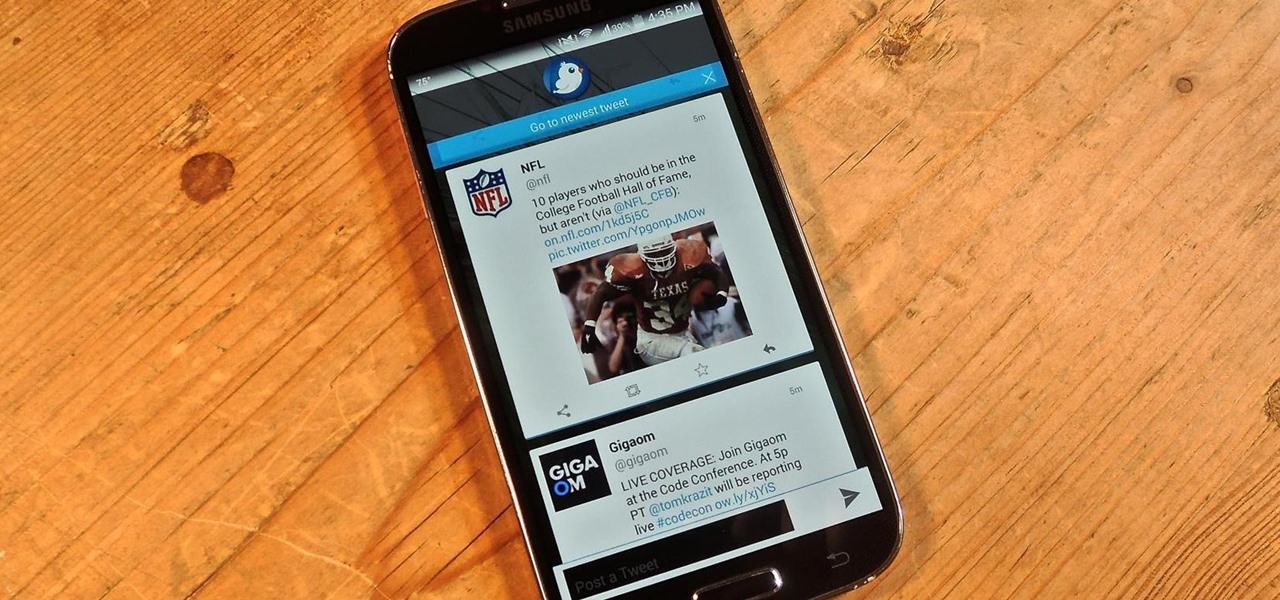
Fact: we live in a world where social media dictates our behaviors and shapes our perceptions. Maybe some of us are addicted more than others, but most of society uses some type of social media, whether it's Twitter, Instagram, Facebook, Snapchat , or something new that I've never heard of.

With the introduction of the Control Center in iOS 7, we finally had a way to access common system toggles like Wi-Fi, Airplane Mode, and best of all, Flashlight. Of course, there were plenty of adequate flashlight apps in the iOS App Store, but none that made it available straight from the lock screen.

With the the general computer users understanding of Information security rising (at least to the point of not clicking on unknown links), and operating system security getting better by default. We need to look for new and creative ways to gain a foothold in a system.
If you're new to Android phones, one of the first things you've probably noticed is how notification alerts differs from Apple devices, especially in regards to getting a text message.
For the most part, Xbox Live is amazing, but there is one thing that has been annoying for pretty much everyone, to say the least. Microsoft Points.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

For the most part, keyboard shortcuts are great. They save you some time and make it easier to do everything right from the push of a button. But like most things in life, there is always a caveat, and in this case, for me—it's a huge one.

The new Call of Duty: Black Ops 2 is the hottest game on the market right now, and there's no doubt it'll end up being the most unwrapped gaming gift come Christmas morning. The first-person shooter hopes to carry on the tradition of its many predecessors in bringing the most action-packed gaming modes, along with a high-replay value, to its legions of fans.

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...
Converting Movies To Psp Format. Hey again, this is a real quick guide for anyone interested to get a movie onto there PSP without all the fluff i have seen elsewhere. I just watched Africa the Serengeti on my PSP and heres is the lowdown.

It's no secret that most people who got an iPhone 5 (or upgraded their old iPhone to iOS 6) have been sorely disappointed with Apple Maps. We may all miss Google Maps, but the Google says they aren't even working on an app for iOS 6 yet. Even worse, Google exec Eric Schmidt says they're waiting on an invitation from Apple, and if we know Apple, that could be a while. Users who didn't get an iPhone 5 have had an even worse time of things—Apple disabled 3D maps and turn-by-turn directions on ol...

The iPhone 5 will be here in no time. Pre-orders started at 12:01AM PST this morning and it's expected to start shipping in about two weeks. Verizon, AT&T, and Sprint are all handling unlimited data plans differently, so if you currently have an unlimited plan and are going to get the iPhone 5, you'll want to know what your carrier is doing before you upgrade so you don't end up with a very unpleasant surprise on your next phone bill. Verizon

I should start off by saying that this technique is of no real practical value, because this process is far more time-consuming than simply just manually trimming trees to meet your specifications. That said, it's an awful lot of fun to play with!

Doorbells are a great idea. They let you know when someone who's not a burglar is trying to enter your house, apartment, or squat. They eliminate the need for lots of noisy yelling and startling door pounding.

Drawing is easy for some, harder for others, but drawing letters is pretty simple for both the pro and novice artist. There's all kind of text styles you could conjure up, and they don't have to be boring fonts. Fire up your imagination to create different styles for drawing numbers and letters of the alphabet, adding individuality and pizzazz to names, messages, greeting cards and decorated items.

Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack your way to level 14 on MyBrute (08/18/09).

In order to work a quadratic equation, you should, first, try to simplify it. Try to move your variable to one side of the equation and the numerical values to the other. For example, in the equation 3n + 5n 2 = 0, you should try to move the 2 to the other side, by adding a positive two to both sides. Then, you should add together the like variables. This will give you 8n = 2. Then, you will need to divide both sides by 8. The answer will be n = 2/8. The quadratic formula is ax2 + bx + c = 0....

In this Diet & Health video tutorial you will learn how to check your own blood pressure. Checking blood pressure is a very important part of your personal health routine. Using machines that are widely available, you can easily and quickly check your blood pressure. The target figure will be 140 over 90. The other parameter is the pulse rate. If you are higher than these figures, you need to take a second opinion and consult your GP. Wrap the arm band around the upper arm above the elbow. Pl...

In this video tutorial, viewers learn how to solve for the circumference and area of a circle. The circumference is the distance around a closed curve. The formula for circumference is C= pi x d. The diameter is two times the radius (d= 2r or r= d/2). The value of pi is approximately 3.14. The formula for the area of a circle is A= Pi x r^2. This video provides examples and demonstrations on how to use and solve with both the formulas. This video will benefit those viewers who are struggling ...

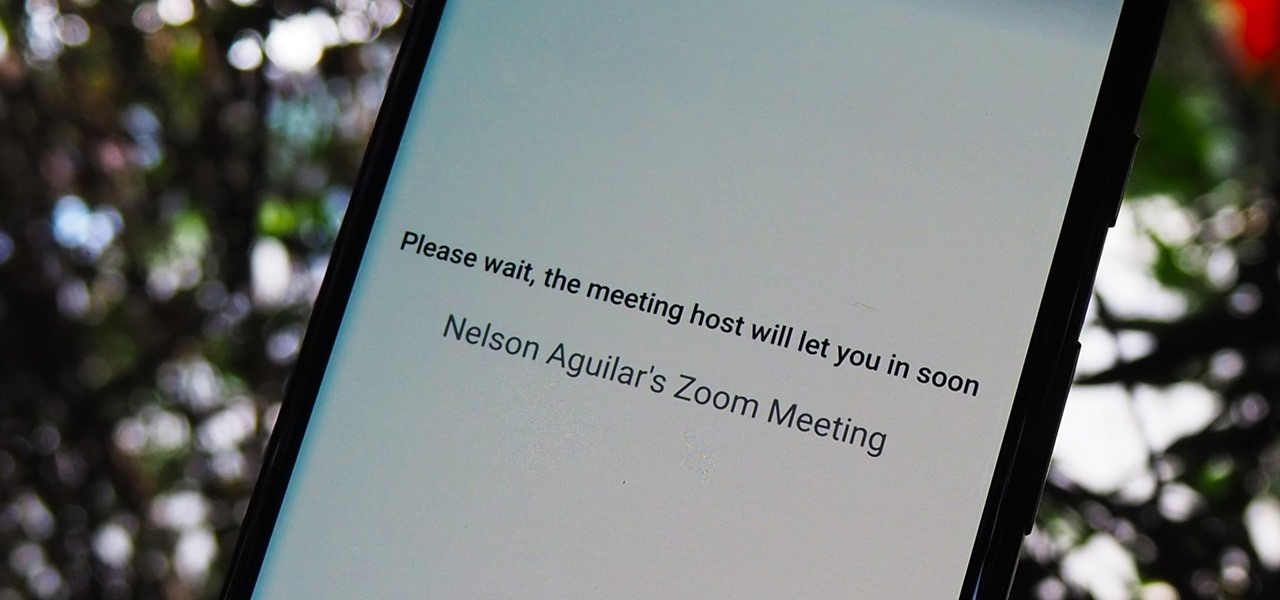
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

When you think about your Apple Watch, what comes to mind? Fitness tracking? Replying to texts? There are a lot of things Apple Watch is good for, but social media doesn't appear to be one of them based on the App Store. If that's your perception, however, it's time for a reality check because you can start browsing Twitter and Reddit on your Apple Watch right now.

The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.

We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

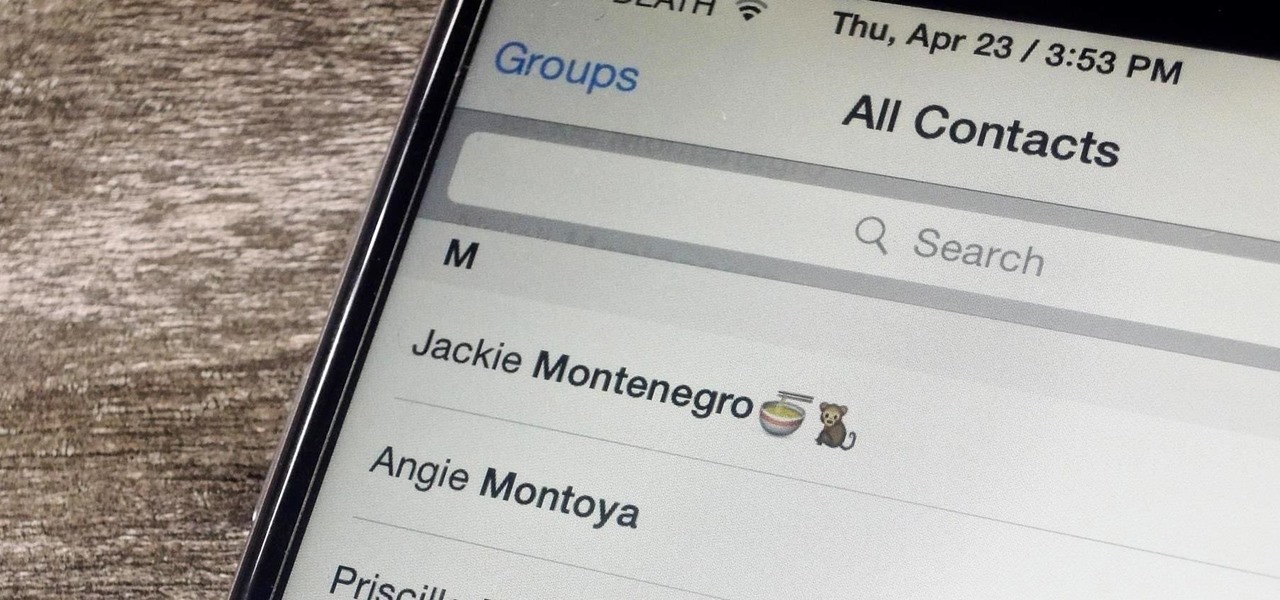
Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

SQLite is a small C library that implements a self-contained, embeddable, zero-configuration SQL database engine. SQLite implements a large subset of SQL-92 and stores a complete database in a single disk file. The library footprint is less than 250 KB making is suitable for use in embedded devices and applications where memory space is scarce.

This video focuses on how to do long division. She starts by dividing 1548 by 26, going incrementally between each value. She first take 26 into the first three numbers of 1548 (154) and gets 5, then takes the remainder of 24 (154-130) and brings down the 8 to get 248. She then divides 248 by 26 to get 9 with a remainder of 14. She then goes into some detail as to how to extract the decimal from the remainder by continuing the long division and adding zeros to the end of the divisor. At the e...

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough, you'll always be looking for more...

This is a how to video on downloading free Movies, Video games, TV Shows, and Programs using BitComet Bittorrent client.