
Valued Clients Search Results


How to Hack Wi-Fi: Selecting a Good Wi-Fi Hacking Strategy
Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Social Engineering: The Most Powerful Hack
Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

How To: 6 Tweaks You Should Be Using on Your Mac Right Now
All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

How To: Writing 64-Bit Shellcode - Part 1 (Beginner Assembly)
In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

How To: Use the SOS Feature on Your Samsung Galaxy Phone in Case of an Emergency
Samsung included an "SOS" feature for its phones since the Galaxy S6 that could literally be a lifesaver should you ever find yourself in an emergency situation. It's one of those things that we hope to never have to use but will be very thankful for if a need ever arises.

How To: Install the Sling TV App on Your Nexus Player
UPDATE 5/21/15

Hack Like a Pro: Python Scripting for the Aspiring Hacker, Part 1
Welcome back, my greenhorn hackers!

The Sony Hack: Thoughts & Observations from a Real Hacker
By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...
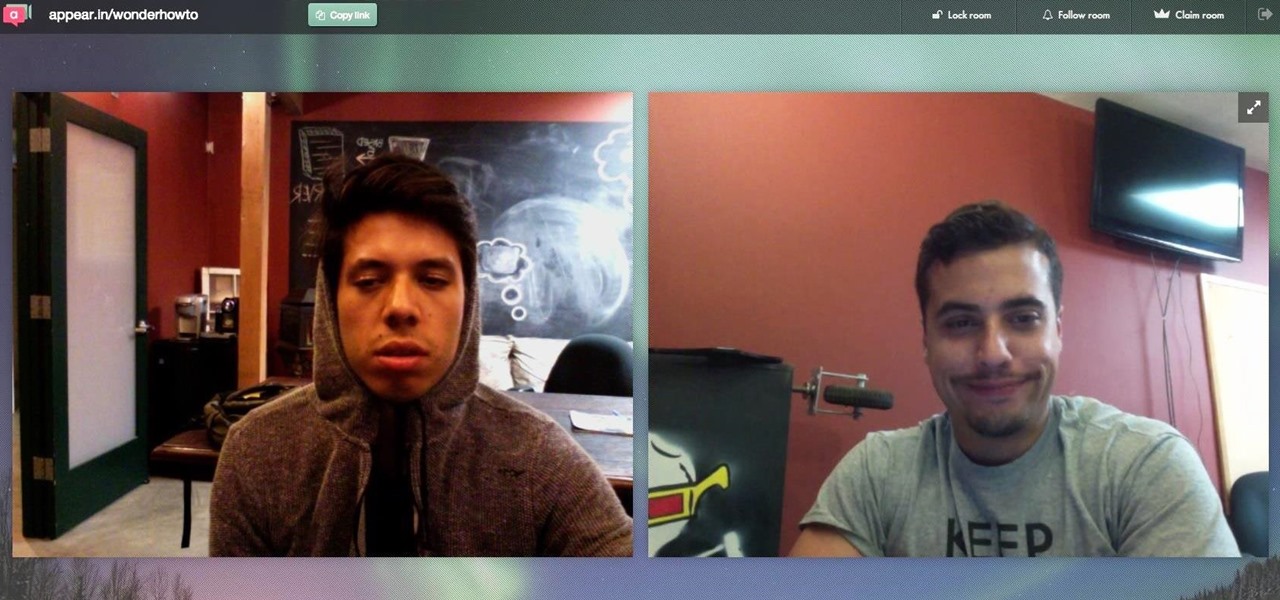
How To: Appear.in Makes Video Chatting Easy with No Logins or Downloads
These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.

Hack Like a Pro: How to Hack the Shellshock Vulnerability
Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.
How To: Get Text Messages in Facebook-Style "Chathead" Bubbles
When Android 4.4 was released, the massive changelog led to some awesome new features getting lost in the virtually endless list of new tweaks. One such change was the ability to set a default text messaging app, which streamlined the existing process of installing a third-party SMS client.

How To: Make Google Now Obey Custom Voice Commands—Even Without Root
It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.

Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 1 (Primer & Overview)
Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

How To: Save Hundreds of Wasted Hours with Gmail's "Canned Responses" Tool
Time is money, and if your job requires sending out hundreds of generic emails—think "Thank You" notes and sales pitches—you could save days of work by creating templates stored within your Gmail called "canned responses."

How To: An Introduction to Steganography & Its Uses
It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

How To: Get People to Trust You with Their Secrets
Prying into people's lives without them putting up their guard can be difficult, unless you can convince them that you already know them very well. Most people don't have many friends they can be honest with, and this can be exploited. Once they're convinced you already know their secrets, they'll start to fill you in on the little details.

How To: Get OpenVas Working Properly in Kali
A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

How To: Sync Your Entire iTunes Library to Spotify's New "My Music" Section
Included in Spotify's new darker, slimmed down redesign is a much needed My Music section, which consolidates all of your starred music, local files, and playlists into a personal collection of songs, albums, and artists, similar to how iTunes organizes your music. This makes me wonder...

How To: Access & Control Your Computer Remotely with Your Nexus 5
With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

How To: You Can't Stop Gmail from Scanning Your Emails—But You Can Limit Their Ad Targeting
Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

News: Google Tells Samsung to Get with Its Program
Fresh off the heels of their latest agreement, Google and Samsung may soon be further aligned in their mobile technology outlook. The two tech giants signed a cross-licensing patent agreement, but that doesn't mean that Samsung was just going to start putting out stock Android devices. Quite the opposite really, as we saw from leaks of its new Magazine UX. The new user interface was shown during Samsung's presentation of it's latest Galaxy tablet at this years CES, and as reported to Re/code,...

How To: Make "Fight Club" Soap Out of Bacon & Drain Cleaner
To make soap, you need fat, and if you've seen Fight Club, you're probably well aware of where soapmaker Tyler Durden got his fat from. Liposuction clinics. If you're not willing to go that far for a perfect bar of homemade soap, you can just use some drain cleaner and America's favorite food instead—bacon!

How To: Turn All of Your Email Accounts into Unlimited Free Cloud Storage!
The majority of our documents and music are digital, which is great for convenience, but it presents a problem for those with a lot of stuff—where do you store it all? There are tons of sites that offer cloud storage, like Dropbox, SkyDrive, and even Flickr, but most of them have limits unless you want to pay, and no way to connect them all.

How To: Turn Your Samsung Galaxy S3 into a Functional Keyboard & Mouse for Your Computer
These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

How To: Block Your Phone Number from Appearing on Any Caller ID
Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

How To: Cloak Your Private Email Address into an Anonymous, Disposable One with Gliph
Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

How To: Learn to Code with a Bundle That Fits Your Schedule
It can feel hard to find time for just about anything these days. But if you really sit down and think about it, you likely have a little more free time in your day than you might actually imagine. The average person has about 4.5 hours of total leisure time over the course of a week.

News: Apple's iOS 13.5 Public Beta 3 for iPhone Introduces Updated COVID-19 Exposure Logging Settings
Apple released the third public beta for iOS 13.5 today, Wednesday, May 6. This latest public beta update comes exactly one week after Apple released iOS 13.5 public beta 2, which, among other things, introduced Apple and Google's joint COVID-19 exposure notification API. Public beta 3 updates that settings page to show a more detailed "Exposure Logging" option instead.
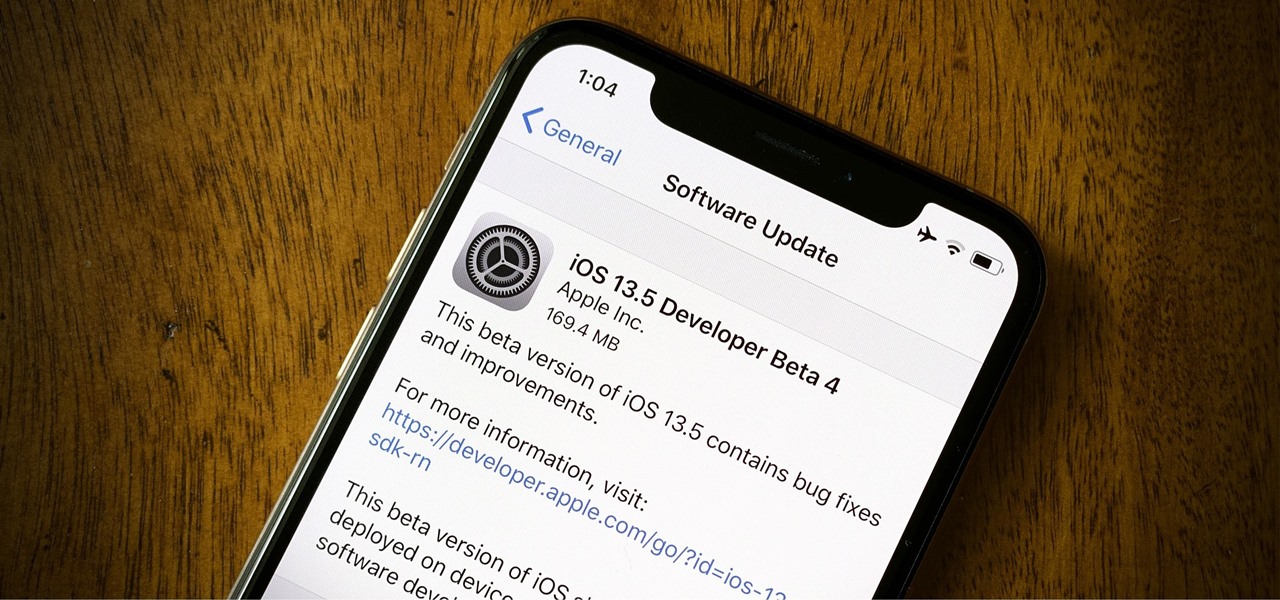
News: Apple's iOS 13.5 Developer Beta 4 Gives Us Updated COVID-19 Exposure Logging Settings
Apple released the fourth developer beta for iOS 13.5 today, Wednesday, May 6. This update comes one week after the release of iOS 13.5 dev beta 3, which introduced Apple and Google's joint COVID-19 exposure notification API to iOS for the first time. Apple updated that settings page to now include an "Exposure Logging" setting instead.

How To: Open 2 Apps at the Same Time on Any Phone with Android's Split-Screen Mode
As phones' screens get closer to seven inches, now is the perfect time to take advantage of Android's split-screen mode. This feature has available since Android 7.0 Nougat and allows you to divide the screen into two halves, with a different app on each side.
News: The Math Says You Should Stop Buying Current Flagship Android Phones
We're all feeling the impact of the economic recession underway due to the coronavirus. With millions of Americans filing for unemployment benefits, now more than ever should we focus on the best deal rather than the best model. And in no industry is that more evident than smartphones.

News: 10 Remote Collaboration Apps for HoloLens, Magic Leap, & Mobile That Can Substitute for in-Person Meetings
For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.
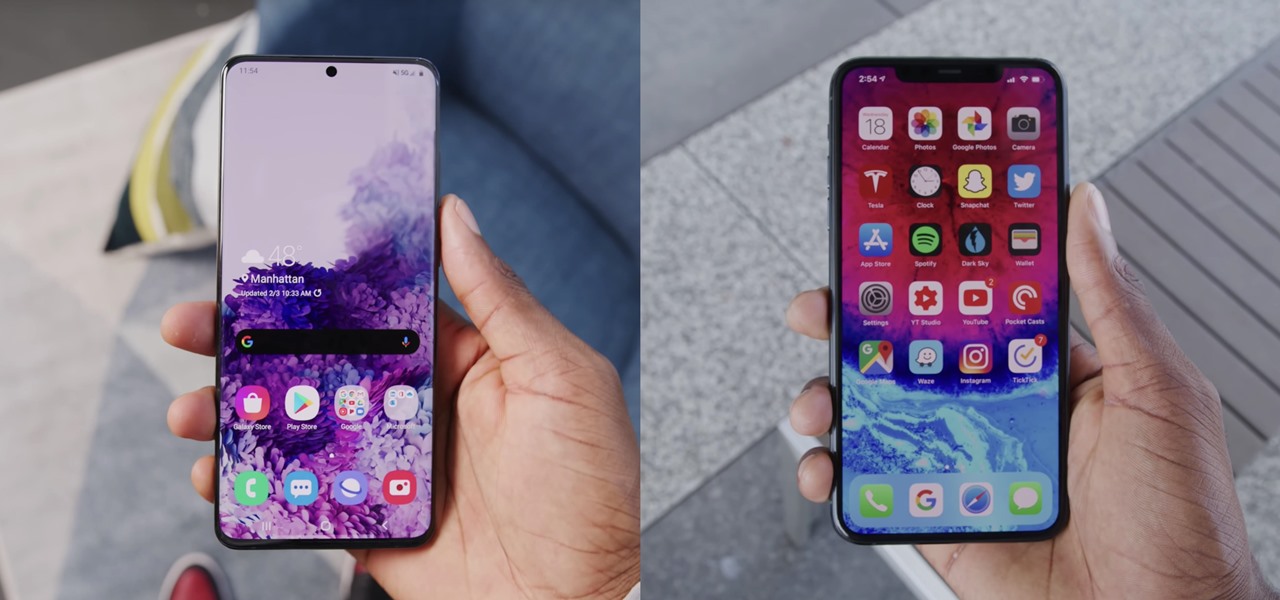
News: Galaxy S20 Ultra vs. iPhone 11 Pro Max: Full Spec Comparison of Samsung & Apple's Best Phones
The time to wait for an absolutely killer phone from Samsung is over. They've released a giant of a phone known as the S20 Ultra, and at least on paper, it's a grand slam. But only a few months ago, Apple released its first "Pro" iPhone, and it was giant in its own right. So which is better?

How To: Enable 20x Zoom on Your OnePlus Camera App
OnePlus has always pushed the boundaries with specs. They give their phones the premium treatment, which, yes, includes the camera nowadays as well. But even though they have become pretty solid in the photography department, it could always be better.

News: Marina Abramovic's Volumetric Art Piece Heads for Christie's Auction Block After Debut in Magic Leap
Some people believe that art makes artists immortal, and now one of the best known performance artists on the planet is working on taking that immortality into the realm of augmented reality.

News: Nreal Forms Alliance with Wireless Giant China Unicom to Demo Smartglasses in Retail Stores
Suddenly, Magic Leap's lawsuit against Nreal, as well as its barrier to entry in the Chinese market, appears to be as insurmountable as The Great Wall itself.

News: Startup GWD's HiiDii Blink-Activated Wearable Offers Alternative Way to Control Your Devices
We have seen Kickstarter-launched wearables before, but this one is particularly unique and may even have you blinking a bit in wonder when you see how it functions.

News: Judge Issues Permanent Injunction Against Meta Company & Founder in Patent Lawsuit, Prevents Sales of Meta 2 AR Headset
It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.
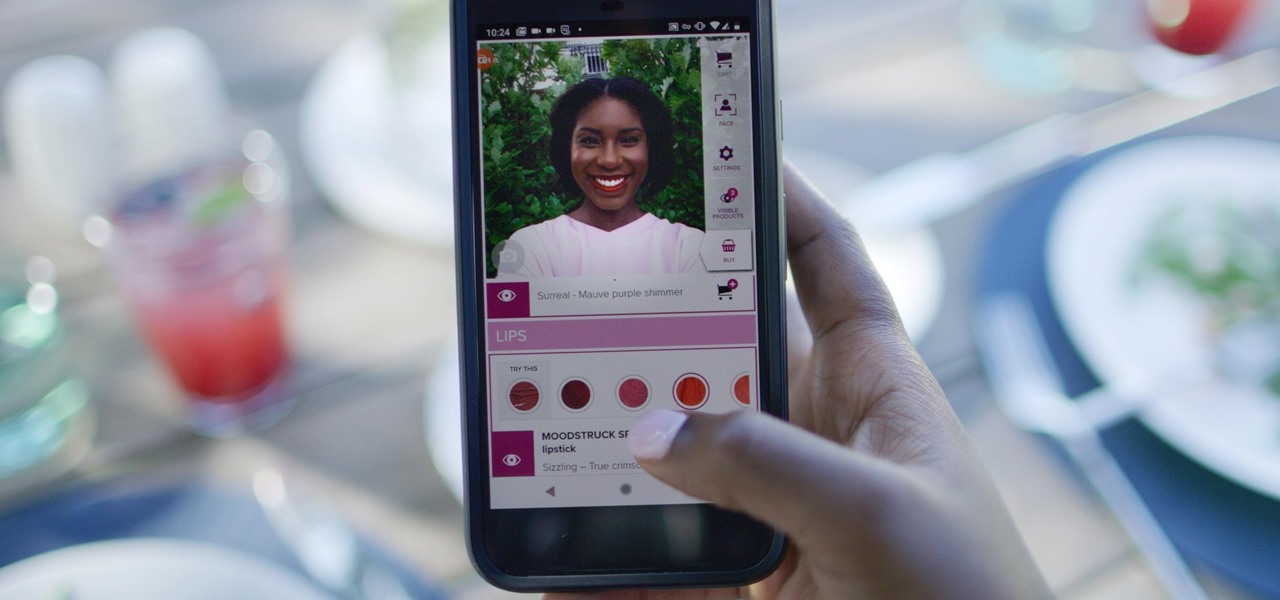
News: Younique Joins Growing AR Makeup Try-On Market by Launching Web-Based App
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

