For any comedian, aspiring or professional, this video series is a must see. Actually for anyone at all, the value of these clips to help with social interaction is also astounding. There is more to improv than just games. We improvise on a daily basis in every situation. Improv is only a reaction to something.

Watch these series of antique collecting videos to find out just what qualities make these oil lamps valuable. Our antiquing expert discusses the rarity of different patterns and chimneys and how to determine the ways condition affects their value. She also tells you how to use your prize lamp safely and even the best way to display them. You may not get your three wishes, but you can still have a satisfying collection of lamps.

In this video series, learn all about collecting those treasured Christmas tree ornaments. These unique objects remind us of some of the best times we have all year; and they come in so many colors, shapes, and sizes that they offer a world of collecting potential to the ornament connoisseur. Our expert will show you how to get your collection started, and she’ll talk about a few things you need to know when choosing pieces, including determining value, age, how to display, and how to store y...

In this video clip series our fashion and cosmetology expert Casey Christensen will show you not only how to get some cool styles for men when cutting their hair but also how to use a razor for a messier, more party style look. She walks you through each step, cross checking again and again remembering that she's not done until the client is happy. Don't let today's fashions pass you by or one day you might be wearing the mullet of tomorrow. Ouch!

There are many ways to calculate basic math problems and solve algebraic equations, geometric expressions, and trigonometric functions on your iPhone, but Apple just came out with one that will blow you away.

Important emails can slip through the cracks in any email client, especially sent emails you were expecting responses to but never received — and ultimately forgot about. Apple has an easy solution for this problem, helping you get answers in Mail for all your pending questions.

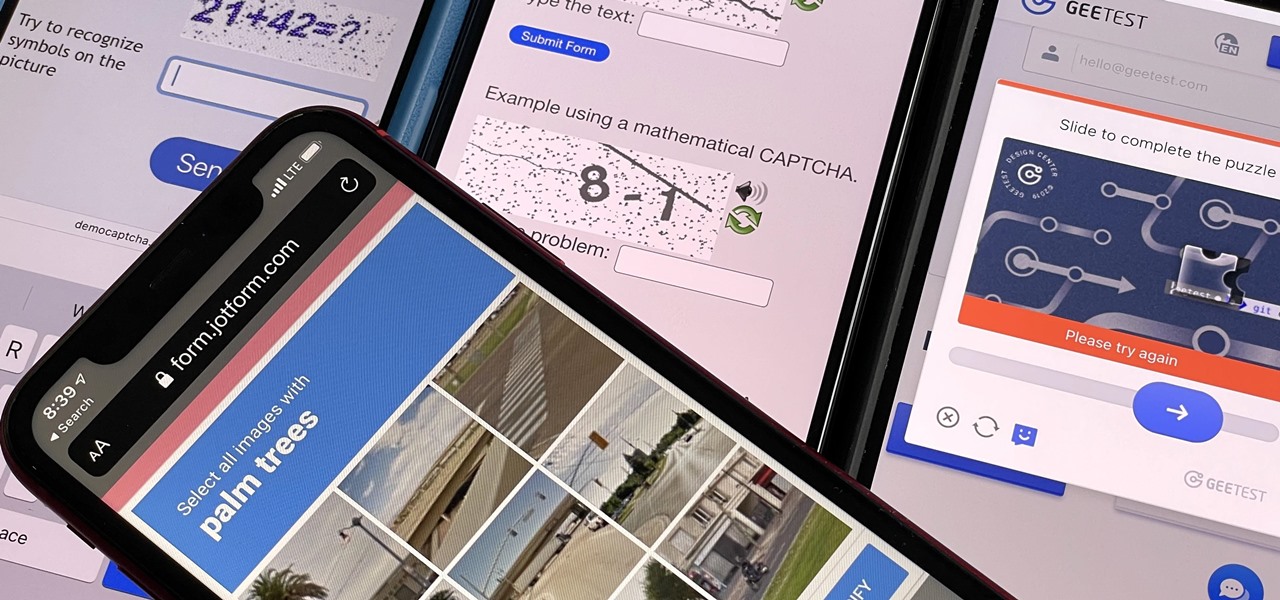
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.

I'm always looking for solutions to problems people are having with their smartphones. This means I spend a lot of time browsing forums and release sites looking for new apps. In doing so, I find a lot of apps that don't quite solve a major problem, but are nonetheless pretty cool. I came across four of those this week.

With its emphasis on well-rounded audible entertainment, Deezer gives all music and podcast fans the best of both worlds. As great as the app is, it's inconvenient to constantly tell Siri to play your music and podcasts through Deezer so that it doesn't default to Apple Music or Apple Podcasts instead. But as of iOS 14.5, you can set Deezer as your iPhone's "default" music player for Siri.

If there is one constant in currently available AR headsets, it's that, for a quality experience, they'll carry a high price tag. Price is one of the reasons these devices are mostly marketed towards enterprise customers for now.

Python is commonly touted as one of the best programming languages for beginners to learn, and its straightforward syntax and functionality makes that hard to argue with. But a lot of tutorials still use Python 2, which is outdated now. Python 3 introduces many new features, and it's important to be aware of them going forward, as well as the key differences between Python 3 and its predecessor.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan — so root nation is an important demographic that deserves being catered to.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds.

A few months ago, iOS 12.1 came out with a handful of useful new features, and iOS 12.2 goes even further. While some of iOS 12.2's new features for iPhone are much welcomed, there are some that we'd be better without.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

You no longer have to resort to a third-party email client on your iPhone to schedule messages to send whenever you want. Apple built the scheduling functionality into its Mail app, and it works with any email service you use in Mail, whether that's iCloud, Gmail, Yahoo, Outlook, or another service.

One of Apple's most prominent iOS 16 features lets you unsend iMessages, but those aren't the only things you can take back. Your iPhone's Mail app also has the Undo Send feature, and unlike the Messages app, you can even customize the amount of time you have to stop an email before it's too late.

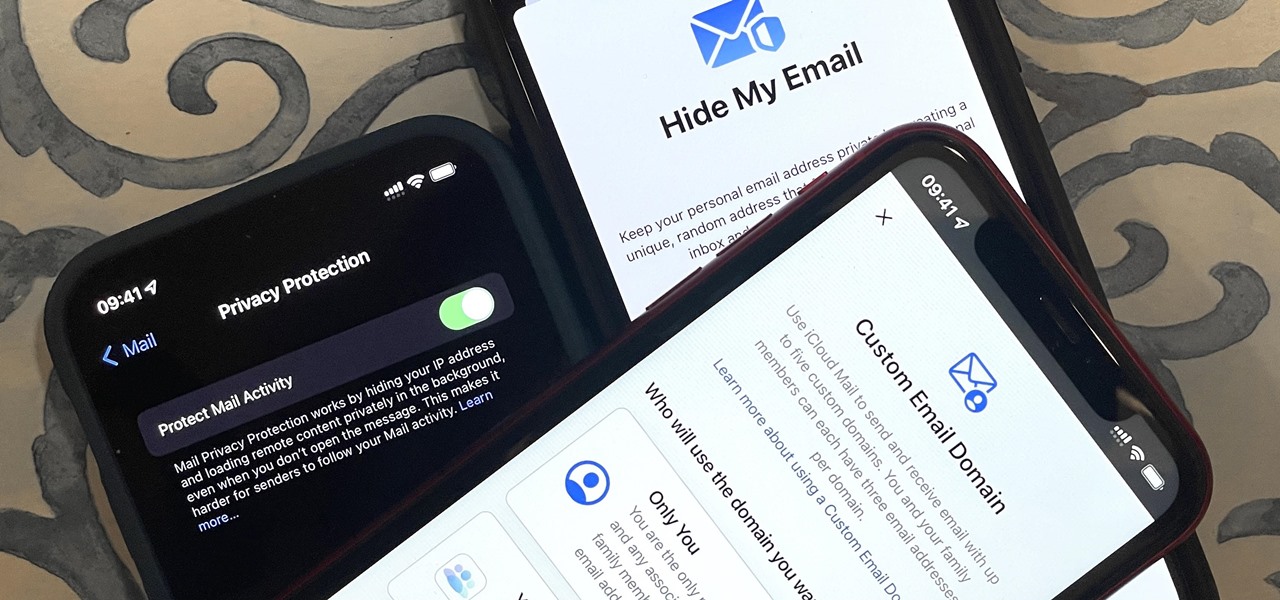
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

Wireless charging is pretty much ubiquitous among modern iPhones and Android smartphones, but the technology has brought a lot of clutter with it.

With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion.

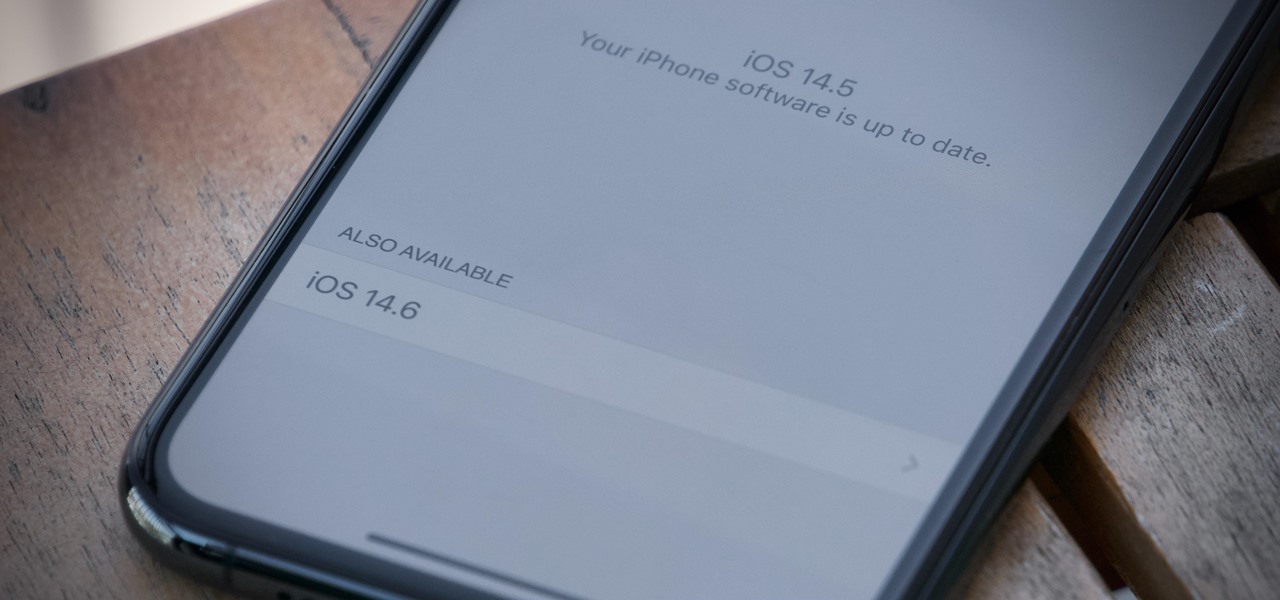
Apple released the first public beta for iOS 14.6 today, Friday, April 23, one day after the company seeded iOS developers 14.6 beta 1. The update introduces an easy way for testers to update from an iOS RC (release candidate) to the latest beta, via a simple option in Software Update.

Apple released the first beta for iOS 14.6 today, Thursday, April 22. The new beta (build number 18F5046e) comes just two days after Apple's spring event, as well as the iOS 14.5 RC, and features an easy way for beta testers to update to the latest beta software when running an RC.

Throughout the COVID-19 pandemic, Facebook enjoyed a boost in sales of Portal, its smart video cameras with AR effects, as social distancing became the norm.

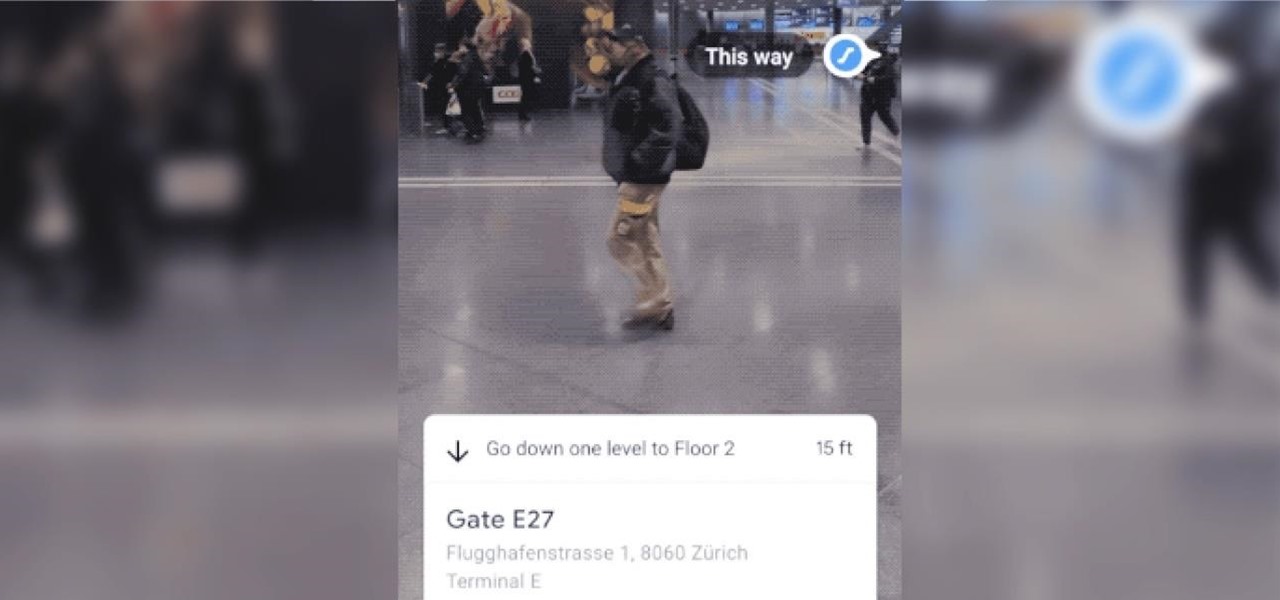
The AR walking navigation feature in Google Maps, which is arguably one of the most useful mobile augmented reality to available to consumers, is about to get even more indispensable for travelers.

Ever since the US Army awarded Microsoft's HoloLens a $480 million contract, the battle for enterprise augmented reality has heated up in earnest.