robichaudd teaches you how to simplify square roots. When you're dealing with variables, even powers and you want to find out the square root of it, you follow the process. Divide the power by the root, which is two, because it's a square root, that gives you what comes out. If we have square root of x squared, the result would be x. So the square root of x to the 6 is x cubed. You simply divide the power by two, since we are dealing with square root. Then square root of 36 times x square is ...

In this video you can learn how to solve linear inequalities. Understand the basics of inequalities and linear equations. In an inequality, we say that that one number is greater than (>) another number or less than (<) another. On occasion we say that something is greater than or equal to, or less than or equal to. In a basic linear equation, we solve for the variable of x by subtracting the value from the opposite side or the = sign. Start by writing your equation on a sheet of paper. It wi...

Want to impress some friends? This magic trick requires no sleight of hand, just a bit of setup. Using the Magicard application, you can make your iPhone mysteriously identify the card placed against it.

If you want to maximize your work output, follow these simple steps. You Will Need

It's super easy to add filters, adjust levels, and crop images using the default photo editor on your smartphone, but there's rarely any built-in tool for removing the background in a photo. A third-party app can help isolate people and objects in your pictures, and we've found a free one that's easy to use, works with high-resolution images, and is available for Android, iOS, iPadOS, and the web.
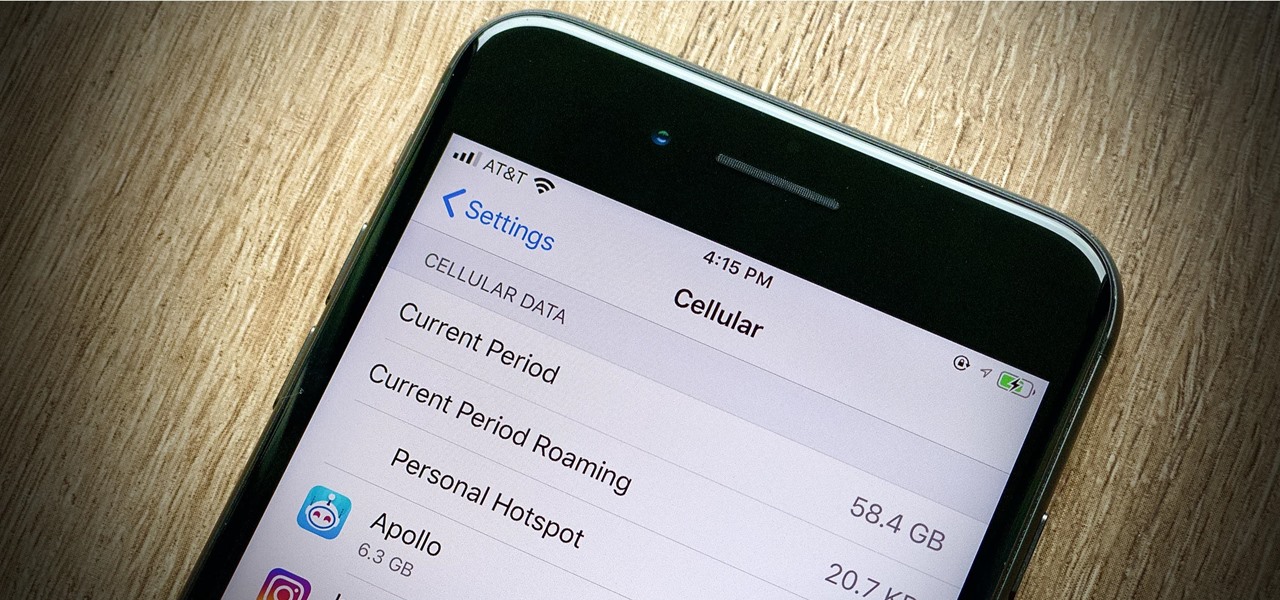
While mobile data caps are larger than they used to be, many of us still have limits to contend with. If you find yourself up against that ceiling month after month, your iPhone itself might be to blame. Luckily, there's an easy fix to stop your iOS device from burning through data in the background.

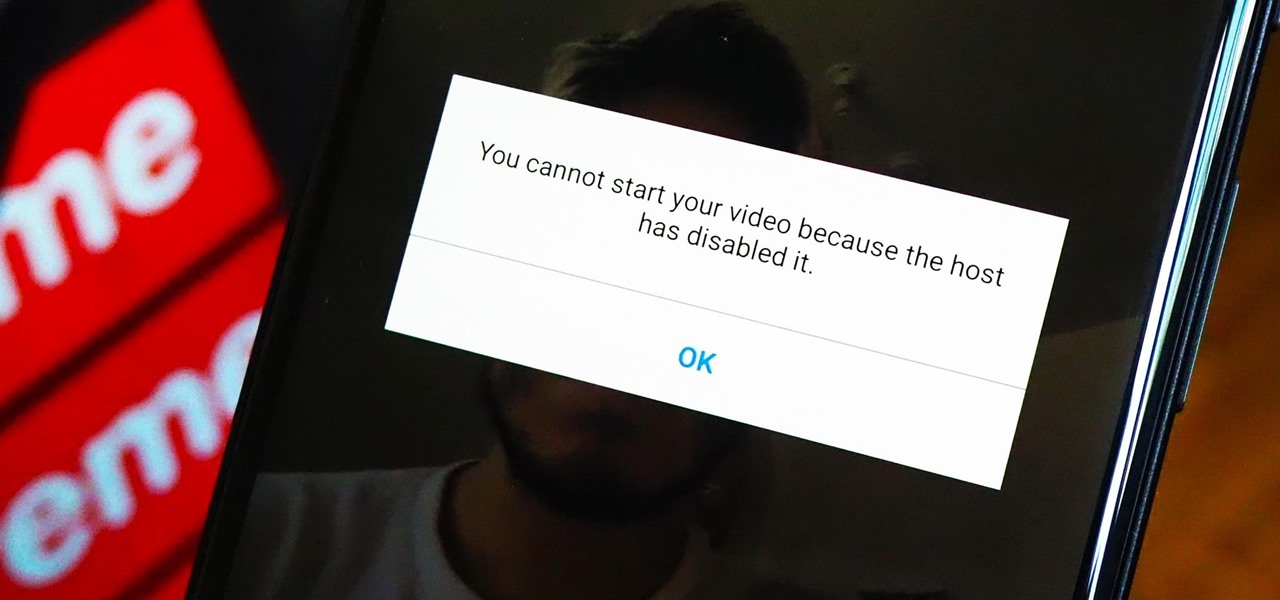
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

So you're listening to Spotify on your Note 10+ and you pause it for a second to talk to someone. A minute or so passes, and you press the play button on your wireless headphones ... but nothing happens. That's because Samsung already killed the Spotify app. Here's how you can prevent this.

When Google finally gave us a dark theme for YouTube, it was a bit disappointing. They didn't use a pure black background, reducing some of the battery savings you'd get with an OLED panel. But with the help of another app, we can fix this, and not only get a real dark mode, but other colors as well.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

While I love Spotify, I don't like it devouring my data plan when streaming music away from a Wi-Fi network. If you have the foresight or time to download Spotify tracks for offline playback later, great. For those of you who like to listen to your music more randomly like I do, based on your current mood, streaming is the only way to go, and there are settings you can tweak to use up less data.

Samsung hopes to make a splash with the new Galaxy Note 9 to make up for the underwhelming sales of its signature Galaxy S9 series. This flagship is a radical departure from its predecessors — it's now optimized for gaming and paired with the most advanced S Pen stylus to date. Here's everything you need to know.

Unless you're experienced using the Linux terminal, running ADB and Fastboot commands can get confusing very fast. The problems often stem from having to hunt for various files — usually IMG or ZIP files that you need to mod your Android phone — and then move them to your platform-tools folder, which, depending on how you installed ADB in the first place, could be anywhere.

Google worked with design agency B-Reel to create some unique wallpapers for its Pixel and Pixel XL flagships, and the end result is quite stunning. These "Live Earth" wallpapers, as they're called, combine Google Earth's high-def satellite imagery with a 3D parallax effect that changes perspective as you move between screens.

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Nostalgia sometimes gets the best of us—hence the reason we geek-out when we see emulators for SNES on Apple devices or N64 on Android.

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

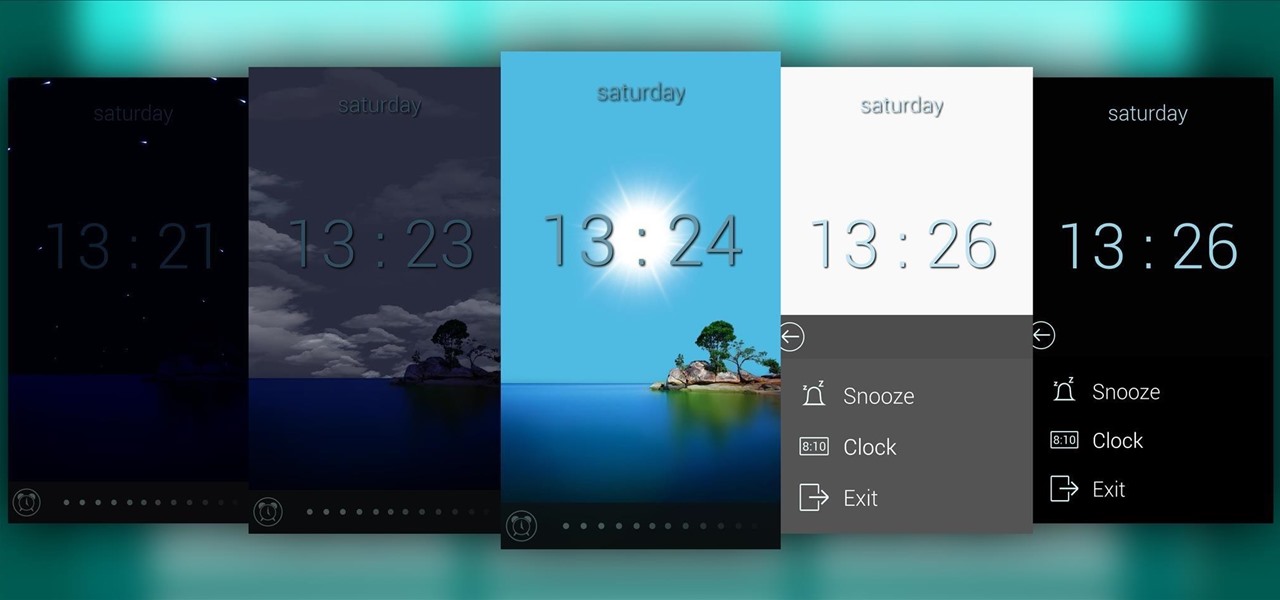
Most alarms just make noise to wake you up, and it can be a bit jarring coming off of a deep sleep to suddenly being woken up by a blaring sound. On the flip side, if you're a heavy sleeper, this might not even be enough stimuli to snap you out of your 8-hour coma.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

There were some pretty amazing things included in the Android 4.4 KitKat update, but unfortunately, most of them were left inactive on our Nexus 7 tablets. Some, like full-screen immersive mode and the hidden battery percentage status bar icon, could be enabled on rooted devices, but not everyone wants to root.

Texting something as simple as "What up, bruh?" can be transformed into something way more baller by adding emojis, emoticons, GIFs, and textspeak. Some people would even argue that texting is a form of art, similar to Shakespearean sonnets, but it still has a ways to go if you ask me.

Many people are bored of the typical square-ish icons arranged in a uniform grid on their Android homescreen. I dislike looking at grids of buttons and sometimes I would like to have some really HUGE buttons for the applications that matter the most at any given time.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

If you're anything like me, you'd like the ability to fully exit your iPhone apps to help free up memory, improve battery life, stop background processes, and fix unresponsive apps. The thing is, you can, with the help of the app switcher. Force-closing apps also helps keep your app switch clean and organized.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

Why ever would you want to throw a cowboy-themed party for your little cowboy? Two words: John Wayne. The epitome of wild West cool and the exemplar of the "strong and silent" type, John Wayne made the cowboy badass. So give your boy the coolest party in the world by creating a cowboy theme.

You know how you can personalize your computer desktop by pinning any picture you want as the background? You can do the same thing with phones - well, iPhones. Since nowadays it seems everyone and their mother has an iPhone or iPod Touch, make sure your iGadget looks different than everybody else's by installing a theme.