Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to take and share photos on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.
Windows Movie Maker is the basic video application included with Windows XP. Learn how to use Windows Movie Maker to create a movie with transitions, effects, background music, and voice over narration. If you have never made a podcast or simple movie before, this series is a great way to get started without needing additional software if you have a Windows XP OS.
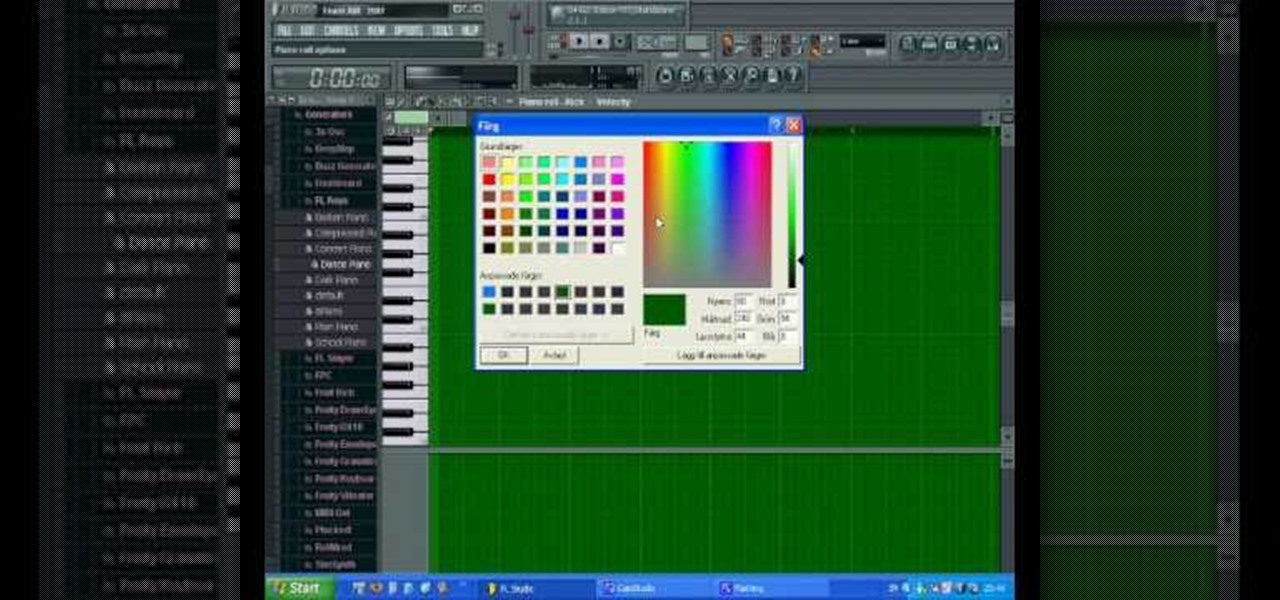
If you are tired of looking at the same old background when using Fruity Loops, go ahead and make a change! This video will show you how you can change the background color on FL studio. Personalize your FL studio!
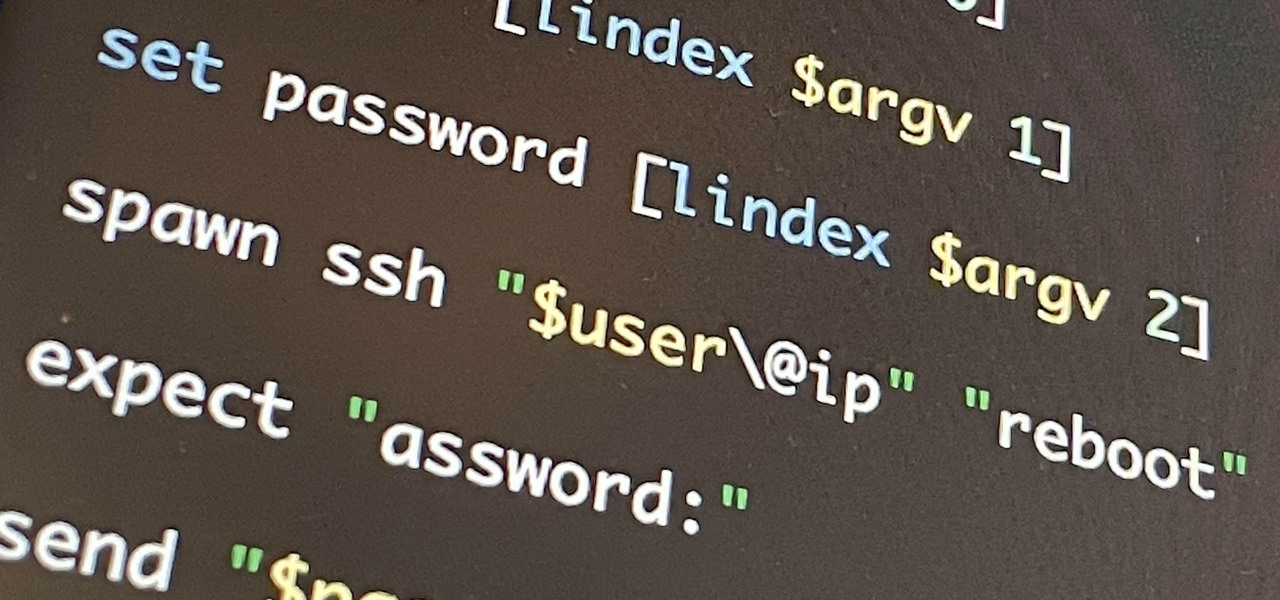
If you're getting into automation, Bash scripting is usually the way to go. However, there are a couple of limitations, and one of them is logging into another device like a Raspberry Pi and running a script automatically. To help in those situations, we're going to automate delivering an SSH payload with an "expect" script.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Apple added "Announce Messages with Siri" with the release of iOS 13.2, and it came as a welcome surprise for me; I missed the feature from its initial run during iOS 13 beta testing. However, while users online gleefully showed off their newfound Announce Messages with Siri capabilities, I was frustrated to see that I didn't have the setting, even though I just updated my iPhone to 13.2. So, what's the fix?

Apple first added the "Do Not Track" option to Safari in iOS 7, which sent a request to site owners and advertisers to not track your browsing activity. By tracking your activity, those third-parties could tailor content to you that you're more likely to interact with. While the feature was always opt-in, it's no longer a feature at all in iOS 12.2 on your iPhone.

In the current state of the augmented reality space, Leap Motion is the only well known name in DIY AR headset kits with its Project North Star design, which gives makers the blueprints to build their own headsets.

Designing and manufacturing waveguides for smartglasses is a complex process, but DigiLens wants us to know that they have a software solution that partially solves that problem.

The ongoing war between Apple and Samsung fans will rage on once again. With the release of the iPhone XS Max, Apple has presented a stronger adversary for the Samsung Galaxy Note 9, released earlier. Both stack up well against each other, providing two of the best experiences on their respective operating systems.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Samsung has legions of loyal fans, and for good reason — their Galaxy S lineup ticks so many boxes that it would be a downgrade to switch to any other phone. Though if you're still rocking an older model like the Galaxy S7 Edge, the all-new Galaxy S9 can tick all the same boxes plus a few more. But is it worth the money to upgrade at this point? That's actually a tougher call than you might think.

After testing a series of Android 8.0 builds, Essential hit the reset button and jumped to Android 8.1 Oreo. The beta program didn't last long, as Essential has now released the official 8.1 update to the masses. The features from the 8.0 betas are all still there, plus a few goodies specific to the updated version. We'll highlight the standouts here.

For some, going to the dentist can be a terrifying experience, but a new use of augmented reality could go a long way toward making the trip feel more like it's worth the orthodontic angst.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

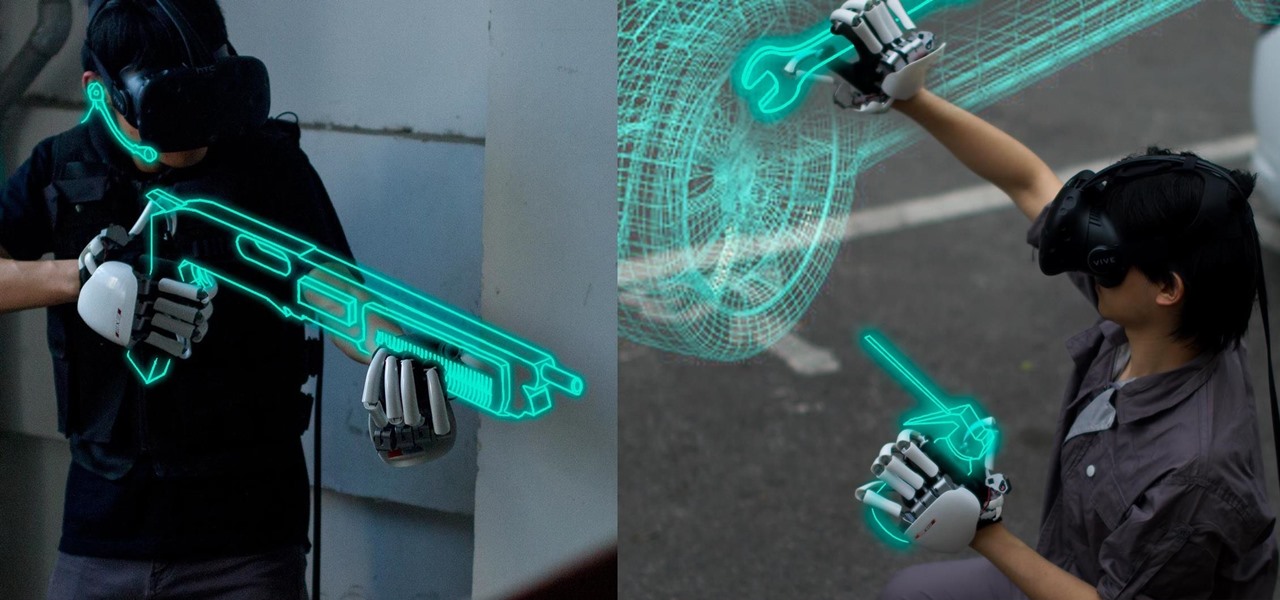
One of the disadvantages of the digital world is that you can't pick it up and touch it. While that can feel like less of a problem in virtual reality, where you're already holding controllers, mixed reality environments—like the one you'd experience in Microsoft's HoloLens—suffer from a lack of physical connection with the digital objects that appear in your real world. Dexmo aims to solve that problem with a relatively intimidating new controller that encompasses your hands.

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

We used to view homemade dressings as something whose variables of flavor and texture outweighed our desire to make them up on the fly. We often found ourselves nervous that they'd come out too runny or too tart or even too thick.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

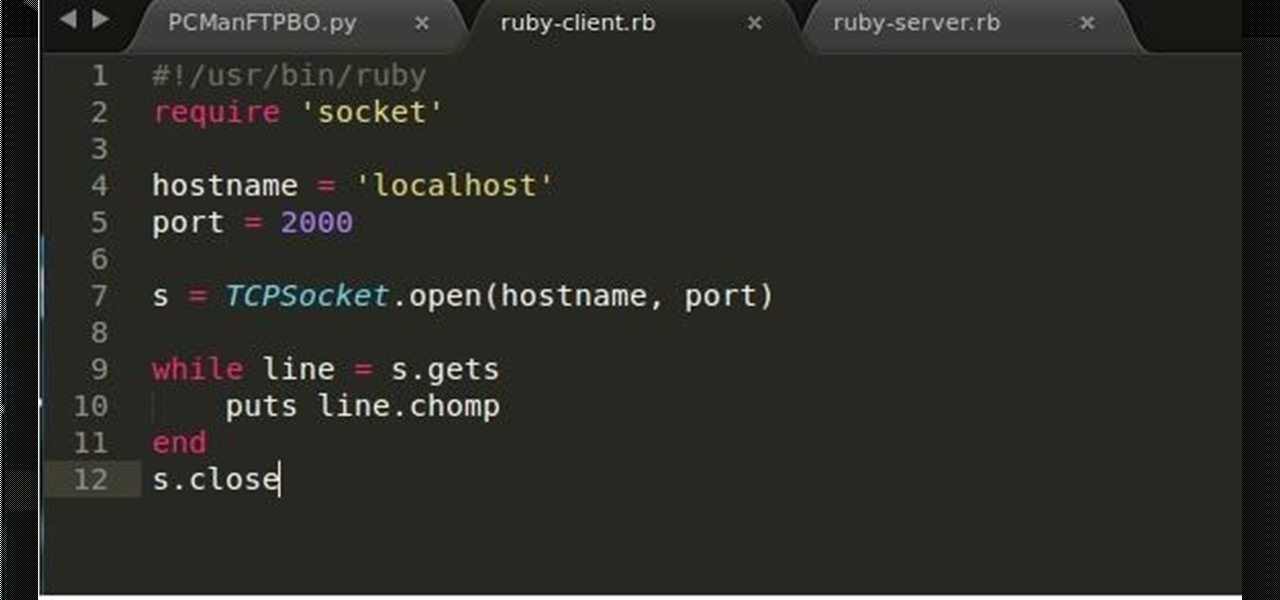
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Got a Samsung Galaxy Note 2 phablet? Sure, it has its problems like any other mobile device, but it's still one of the hottest phablets on the market right now, because, well... it's awesome, right?

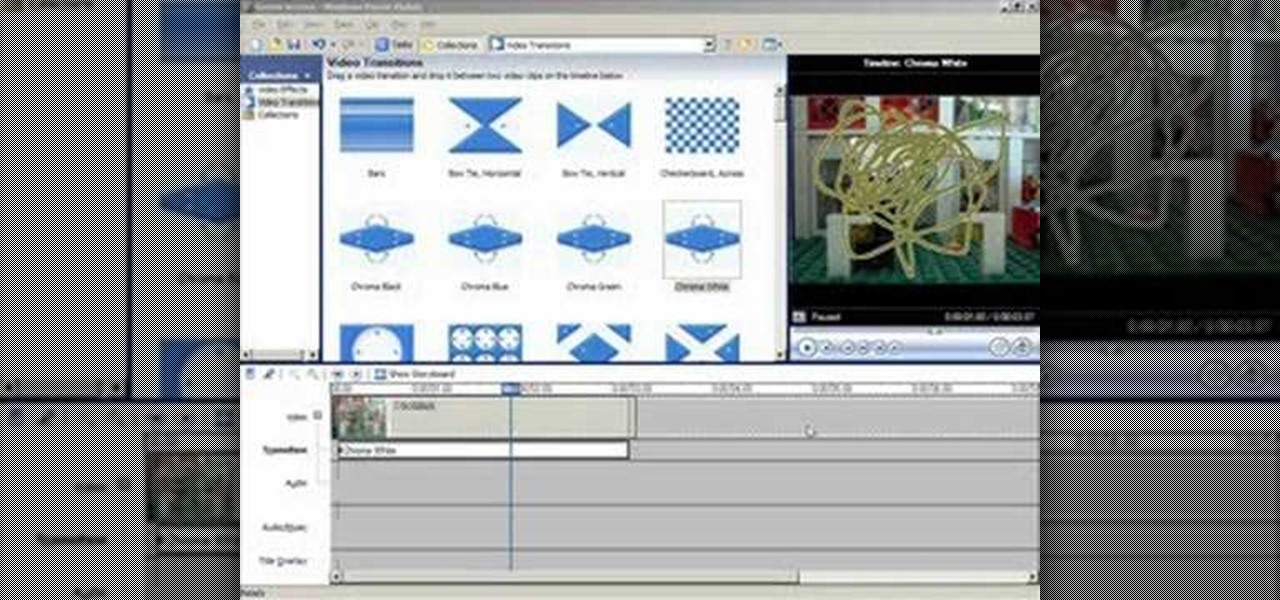
Open windows movie maker and take any video which has the background of same color. Drag and drop the video on to the time line. Then go to tools > video transitions and take the chroma key and drop it between the two videos. The chroma color should correspond to the background color of the video. After this, save the movie file. To pick the right color for the background, download Debug mode wax. This will help in creating some home videos with special effects.

This video teaches you how Laphroaig whiskey is made and also how to properly taste it. It gives background on the Laphroaig brewing company, explaining the process Laphroaig whiskey goes through and how to properly drink the completed whiskey. The video is a great tutorial on the background of whiskey making.