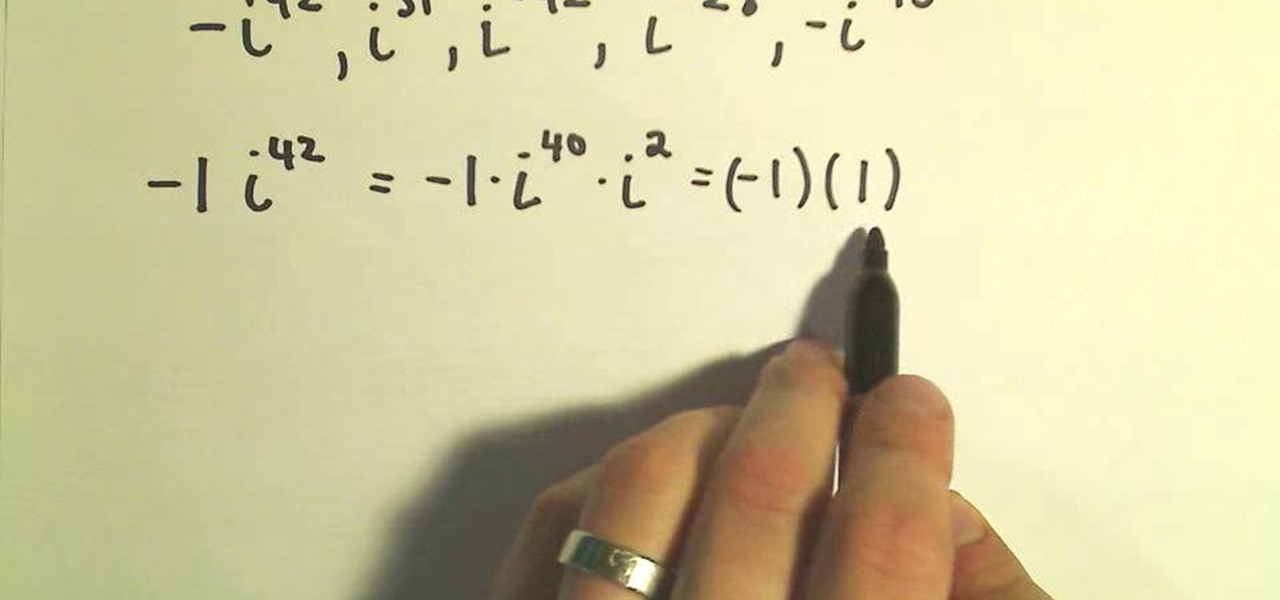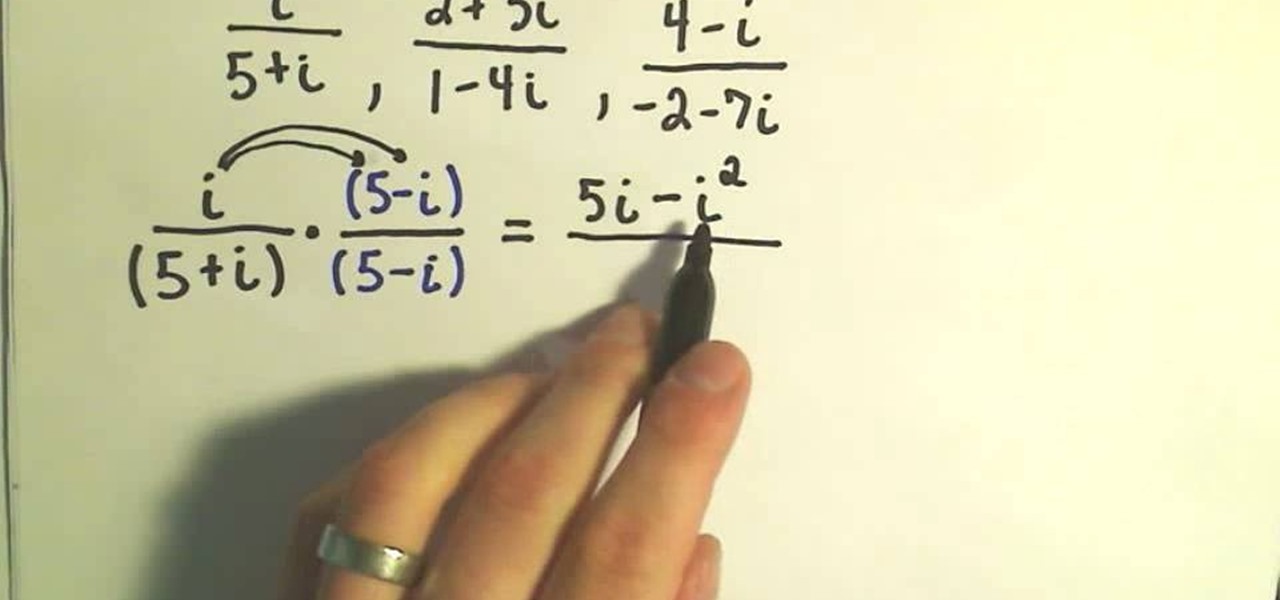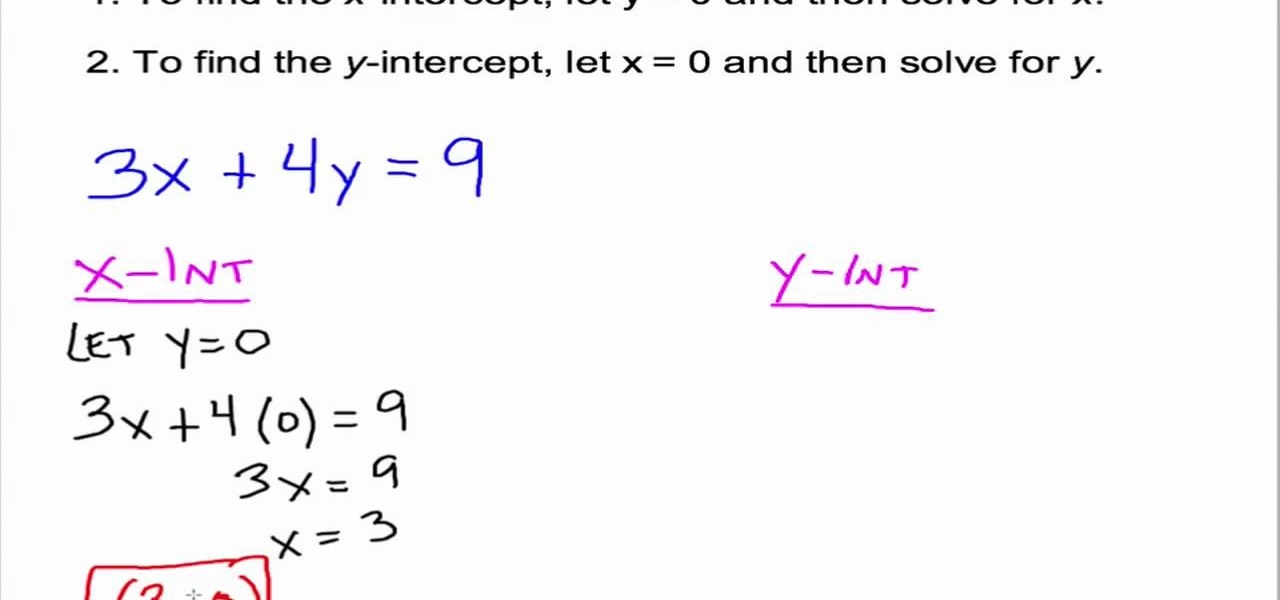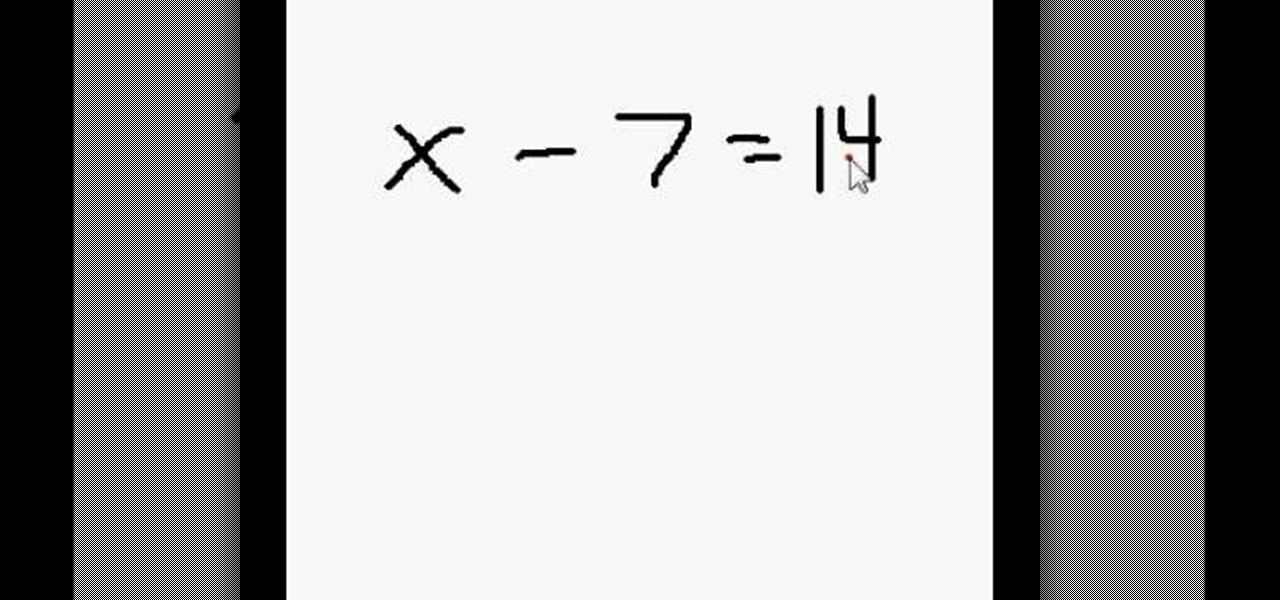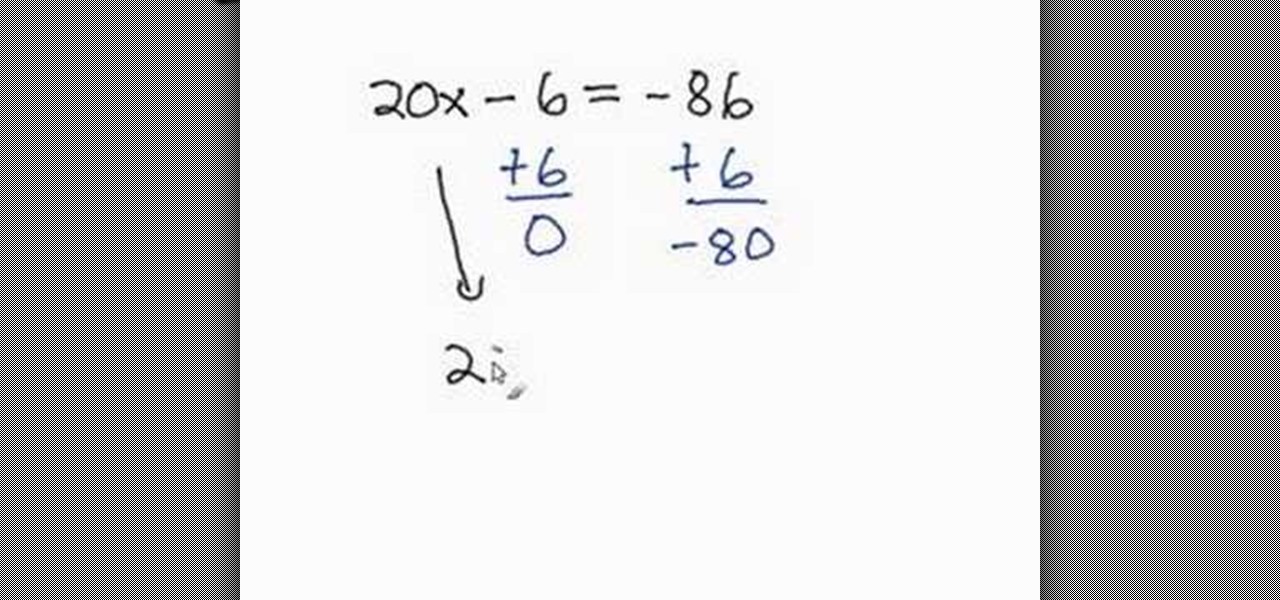A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost!

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.
And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

Open another canvas. It doesn't matter what size you make it, as long as it is the same size or bigger than the area you want it to cover on the image. Open a new canvas by going to "File" and clicking "New." Select your dimensions and click "Okay."

Want to learn how to do quick scoping in BO? It's easy: use the variable scope and zoom in to the second or third level of magnification. Voilà. No more two-second delay when shooting. For a complete walkthrough of how to quick scope, watch this gamer's guide.

The powers of the complex number "i" run their course in a cyclical nature, like annual seasons of "American Idol." Simplify your life - or at least your math class life - by learning how to rewrite the powers of "i" into simple, single variable expressions.

This series on complex numbers will help you solve equations with the cute variable "i" with ease by multiplying by the conjugate.

Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to store variables in an array index when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

The Wedge ROP is a render output driver, which can be used to change variables on the fly while rendering. This can be very useful when simulating, in that you can test out different parameters to see the different results. It's a relatively new feature in Houdini 9.5.

Check out this informative video tutorial from Apple on how to remove backgrounds with Instant Alpha in Keynote '09.

Get all of the info on Thesis themes for you WordPress blog. Watch this video tutorial from 4Blogger to learn how to add a background box and color in a Thesis sidebar.

Want Gary the Gadget Guy's background for Club Penguin? Well, there are just a few simple steps to getting the background on CP.

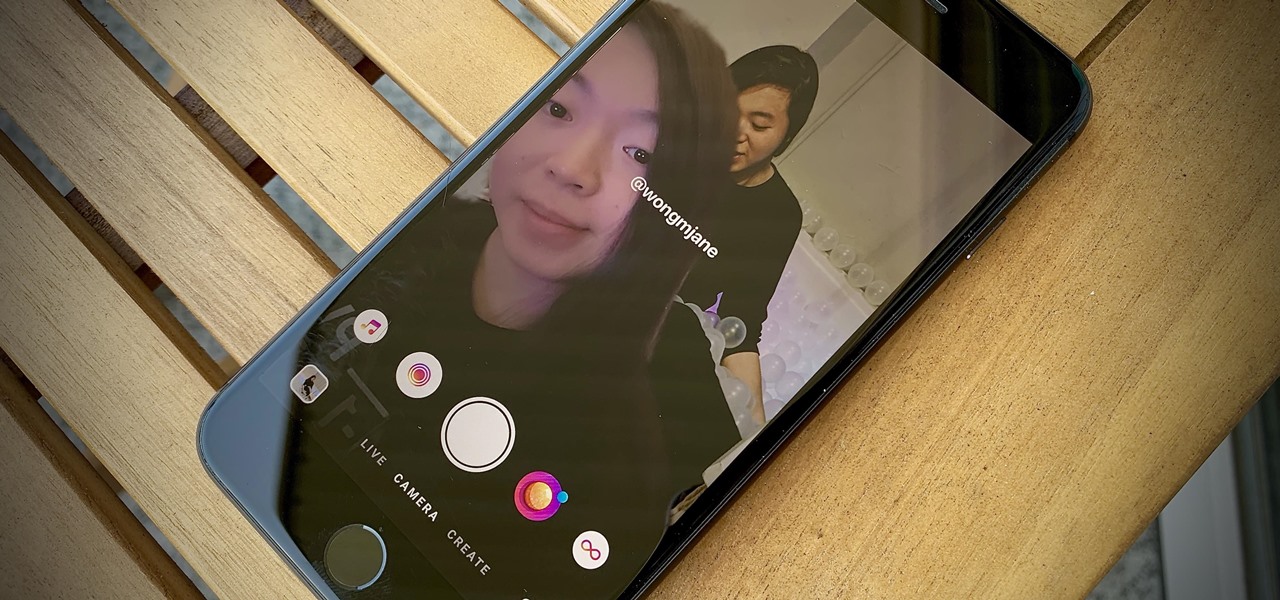
Remember Photo Booth on Mac and iOS? It still exists, but there was a of time where everyone was using it. And why not? It was so cool to take photos with any background imaginable. Underwater? Check. On the moon? Of course. Now, Instagram wants to bring back the fun by introducing AR backgrounds for stories.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

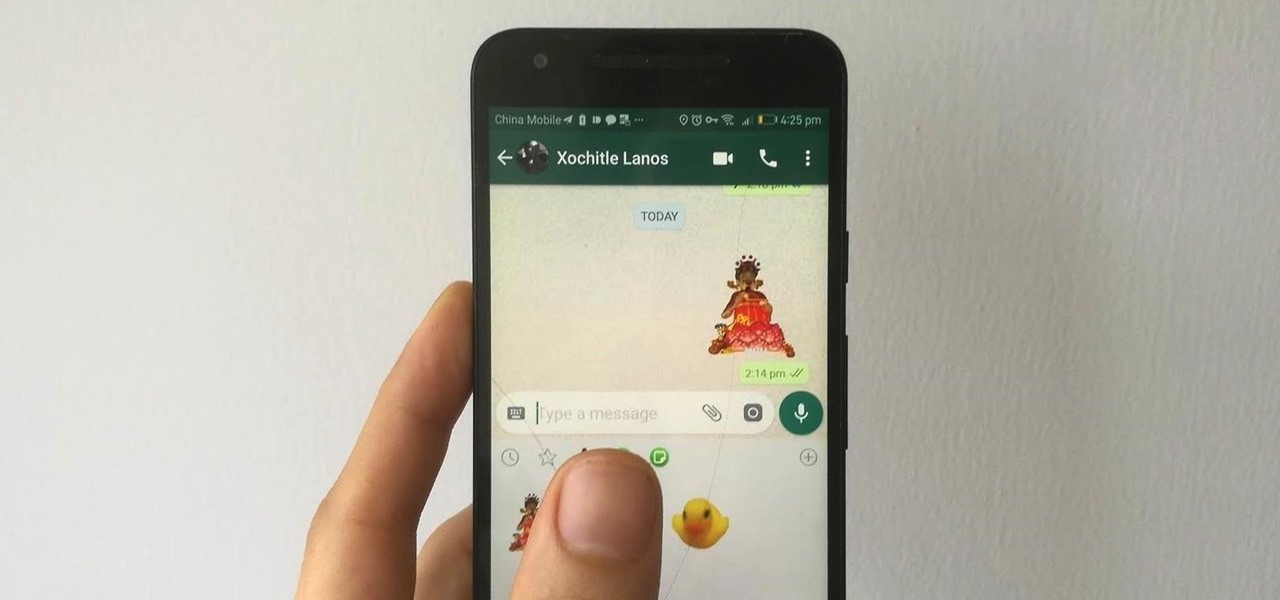
WhatsApp stickers can make your chat more fun. The stickers that come with WhatsApp are fine, but they're standard and accessible to everyone. What if you wanted to show off unique stickers that your friends haven't seen? To take things to the next level, you can create your own WhatsApp Stickers.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

I'm back! We're learning Java WhileLoops today.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

Macs, like pretty much all Apple products, are notorious for not having a highly customizable UI. They do this to keep a consistent look and feel across all of their devices, but I've grown bored of it over the years.

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.

This video teaches the basics of Ohm's law, which is an important equation in electrical engineering. The three variables which are used in this equation are V, which stands for voltage, I for current, and R for resistance. The equation for the law itself is I=V/R. This law defines the relationship between these three very important electrical properties. The host of the video further explains what voltage, current, and resistance are and how they work in relation to an electrical current. Gi...

First double click on the image in layer window then name it and click on OK. Now if you use magic tool on the image and delete the background, it will also delete some of the image part. So to fix it you need to find that kind of places of the image and use brush tool to fill up that space. Now you can delete the background by selecting it with magic tool.

Looking for instructions on how to solve linear equations with multiple variables and constant terms? Look no further. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free ma...

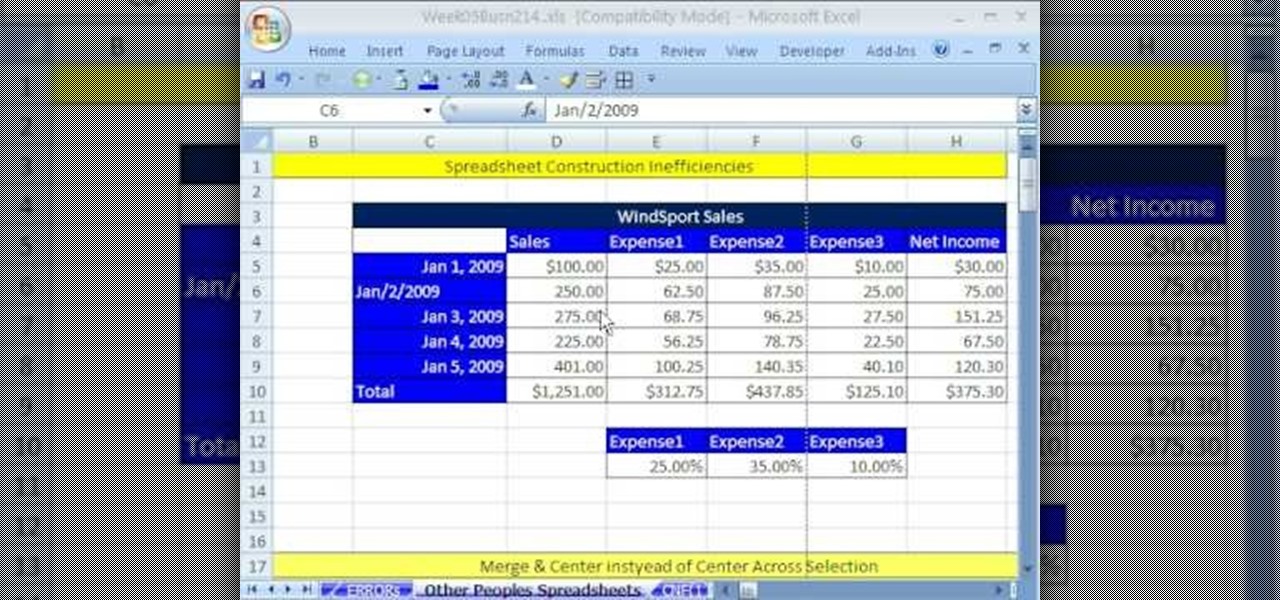
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 26th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to use spreadsheet construction guidelines to fix common problems:

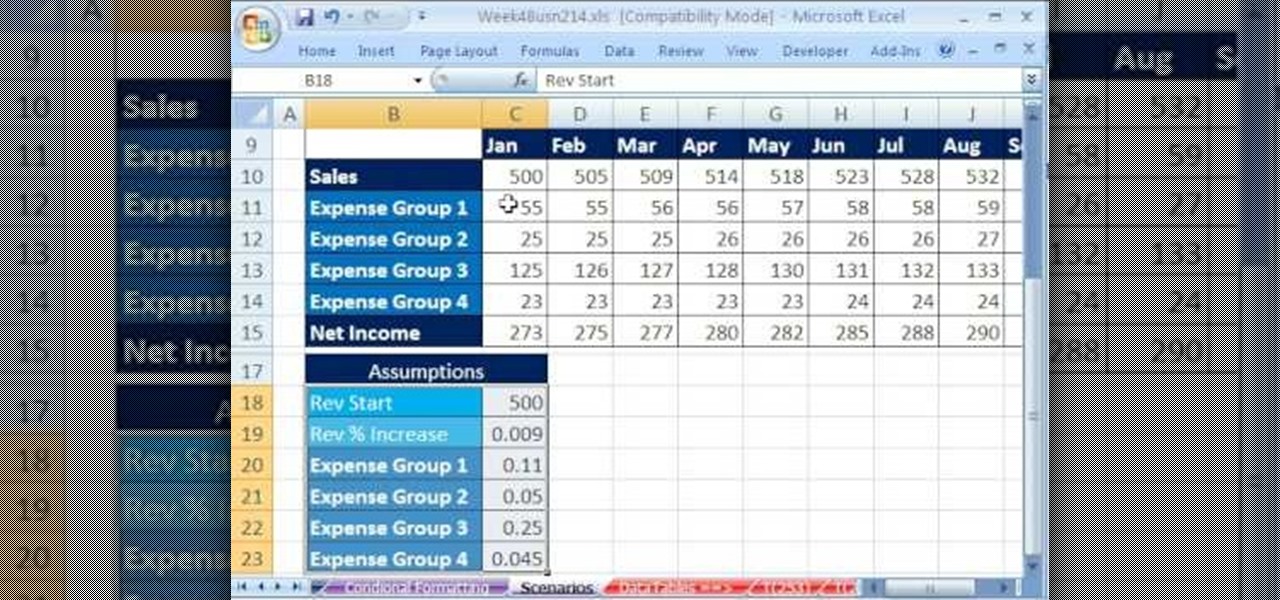
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 22nd installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to create a budget with formula inputs in an assumption area and formulas. Then do what-if analysis by saving and showing scenarios. Also see how to save variables...

A straight line can be represented in the form of a liner equation containing two variables x and y. When the equation is graphed on a pair of coordinate axes, the line passes cut through the axes in two points. The point where the line cuts the x-axes is called as its x coordinate and the point where the line cuts the y-axes is called as its y coordinate. In this way a line has x-intercept and y-intercept. The x-intercept of a line lies on x axes and is in the form (a,0). Similarly the y-int...

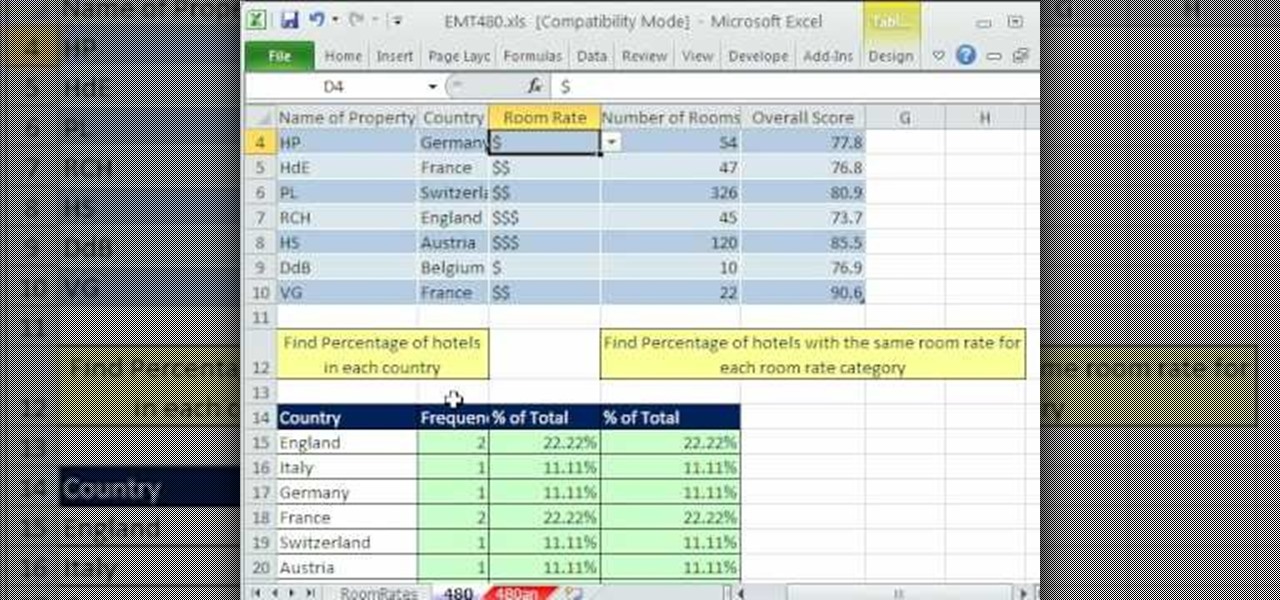
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 480th installment in their series of digital spreadsheet magic tricks, you'll learn how to calculate a percentage of total from a database data set when the variable of interest is text (word). This is accomplished with recourse to the COUNTIF, SUM & COUNTA functions.

This feature also comes with Windows 7. Right click on desktop then click "Personalize". You can see the numbers of themes for example choose Nature theme and click "Desktop Background". You can see the some pictures and a tick mark on the corner of the pictures which tells these pictures are the part of my slide show. Also you can set the time for new pictures to come.

Advance Photoshop shows viewers how to make the Photoshop CS3 icon in Photoshop. First in Photoshop go to File and then click New. Make a new blank at 500 x 500 pixels. Go to your layer button and create a new layer. Next, go to your rectangular marquee tool, hold down shift, and make the rectangle slightly smaller than the canvas itself. Set it from foreground to background and change the background color to a dark blue, enter 15396F for the color. Click on foreground color and enter 3070CA ...

This is a video about "How to Hack: Demolition City 2" by Travis. This is a flash game. To begin hacking, go to the game and enter the first level. At this point, you do not have any cash. Specify that you are using Mozilla in the cheat engine. After you have completed the first level, write "double" variable in value type and then type the value for the first level, and you can easily notice the game appearance seems to be changed, because the second level of the game consists of first level...

The first operations you will need to know when learning to use algebra to solve for an unknown variable “x” will be using addition and subtraction. You can check you work by checking the balance of the equation when you are done.

This video is a detailed step by step explanation as how to solve a two step equation. The video provides an example of how to go about a two step equation problem and the steps necessary in order to solve for the value of one of the variables. This video uses very simple mathematical terminologies, therefore, most people should be able to understand and learn the concept easily. The video is very helpful and recommended to anyone who plans on taking algebra in the near future.

In this tutorial the author shows how to find out the missing part of a triangle that is similar to another triangle. He explains the concept of similar triangle diagrammatically by showing that similar triangles have similar angles and parallel sides. Now he labels sides of similar triangles and marks the value of unknown side as variable x. Now in similar triangles as the lengths of sides of proportionate he shows how to write a equation of proportion and solves it finding the missing part ...