In this video, Justin Seeley shows how to use a Wacom tablet to create photo collages in Photoshop CS3 Extended. He shows how to blend photographs together using the Wacom pen to create a print ad type image. He shows how to increase the size of the brush, change the opacity, blend the image, and lightly paint into the image to control the amount of the fade.

Corinne Bradd shows Kristy Clark how to use the bead roller, a nifty gadget that can create perfect beads of equal size from polymer clay, quickly and effectively. Once they have been shaped and baked, these little beauties can be used for all sorts of projects, from jewelery to decorating picture frames and much more.
Find the biggest files on your computer ordered by size. Learn to order folder by filesize so you can find the ones harboring the most diskspace terrorists. Learn to clear up your private data automatically and wipe it clean from being undeleted.

If you ever run out of cd cases, or those plastic baggie. Have no fear because this tutorial teaches you how to make a CD cover using only A4 size paper in less than a minute.

This tutorial shows you how to use the vanishing point filter to easily move images around and automatically have them adjust to the proper size and angle.

The blood knot is used to join to fishing lines of similar size together. The blood knot is also used frequently by fly fishermen tying there own leaders.

This Photoshop CS2 tutorial walks you through one way to turn a horizontal or vertical shape bar/line of text into a repeating frame. The example involves creation of a footprint frame. It is roughly 16 megs in size; it may take a few minutes to load.

Now this is cool: Turn those custom frame and border shapes into reflective ribbons, frames and bows! You have to watch this one to believe it. This video is roughly 22 megabytes in size; it may take a few minutes to load.

Ever wonder which side of the plate to put a fork? This video will show you piece-by-piece how to create a formal place setting for two different meal sizes. This is useful if you are hosting a fancy dinner, or are just having friends over for a nice meal. Some people even enjoy having a formal setting on their dining room table all the time.

In this math lesson you will learn how to solve systems of equations. Systems of equations usually have 2 equations and two variables. You can solve a system of equations by using one of the following methods.

Wow! No longer do you have to buy those huge marble machine roller coaster toys — you can DIY one! This video covers the materials, tools and techniques used to make a homemade rolling ball marble machine. If you haven't seen this rolling ball marble machine toy in action yet, WATCH IT. It's a looping rolling marble machine made with wood, rebar tie wire and polyurethane tubing, featuring a magnetic elevator.

Learn how to origami a crane with this demonstration by a Japanese surgeon. Watch as he makes origami with the DaVinci robot, a surgical tool powered by state-of-the-art robotic technology. The surgeon’s hand movements are scaled, filtered and seamlessly translated into precise movements of the EndoWrist Instruments. Making origami will never be more interesting. Check out the size of the origami paper crane!! Amazing!

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Open another canvas. It doesn't matter what size you make it, as long as it is the same size or bigger than the area you want it to cover on the image. Open a new canvas by going to "File" and clicking "New." Select your dimensions and click "Okay."

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

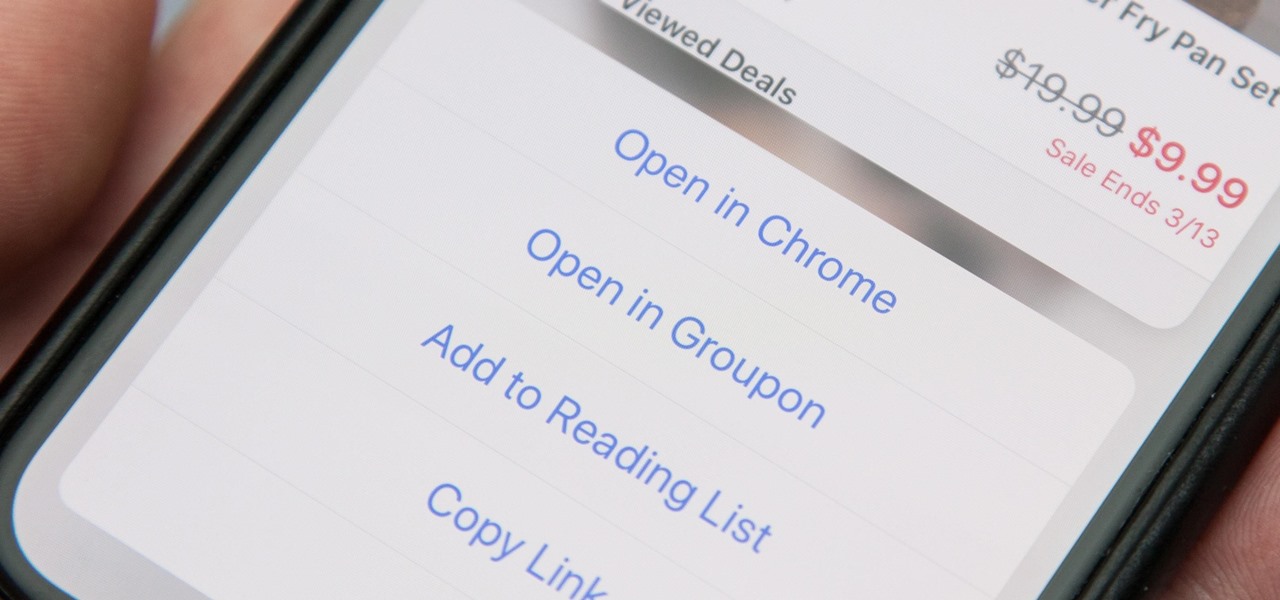
When you tap on a URL link in a text, email, or wherever, your iPhone's default reaction will be to open it up in Safari, and there's no way to change this in the settings. However, there is a way you can work around this to open up links in Chrome instead. Even if you accidentally open a link in Safari, there's a quick way to jump the tab right into Chrome.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.

Google's Material Design guidelines have finally brought some consistency to the look and feel of Android apps, bringing most of the user experience on par with what you would see on iOS. However, some developers are still using non-compliant home screen icons, even though Material Design calls for specific padding, size, and layouts.

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman)

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Homemade ice cream is so good and you can make it with just a few ingredients and no special equipment. Most cookbooks and magazine recipes expect you to have an ice cream maker at home, but you can imitate the churning effect of an ice cream maker by shaking or tossing around the ingredients inside a tightly sealed ziplock bag.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Macs, like pretty much all Apple products, are notorious for not having a highly customizable UI. They do this to keep a consistent look and feel across all of their devices, but I've grown bored of it over the years.

The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks.

Out of the box, your Android device can be customized in many different ways, and a ton more with root access, but adjusting the actual interface of the system is a little bit more challenging. Changing the status bar size, icon width/length, and positioning of toast notifications are things that require a little bit more know-how—until now.

The new Google Now Launcher has hotword detection and one-swipe access to Google Now, but personally, it's not enough to convert me away from other launchers like Apex or Nova. Just because it's Google's official launcher for stock Android doesn't make it better than all the rest.

3D video capture isn't just for the Hollywood film makers, but it does take a bit of knowledge to set-up and configure. In this two part video series, the guide provides you with tips and information that will help you learn how to use your 3D camera rig and correctly adjust your parameters.

Little girls are always in a rush to look just like their mommies. Just think pint-sized fashionistas like Suri Cruz and Courtney Cox's daughter Coco, who was recently caught by the paps wearing the same ruby lipstick as her mommy on a stroll. While we don't think that wearing makeup is all that age appropriate for a five year old, beautiful, youthful hairstyles are.

There's no shortage of ice cream recipes out there, but one ice cream shop in London has found a unique recipe to sell to its customers, and of course it's controversial—breast milk ice cream.

If you're using Adobe Illustrator CS4, you know that cropping an image can be less than a simple task. This how-to walks you through the steps, not only showing how to place and move the image, but also how to crop it to the desired sized. Unlike Photoshop which allows you to work directly with pixels, Illustrator treats all images as whole objects. SO, watch this video and end the frustration that Adobe Illustrator can bring when you're cropping an image.