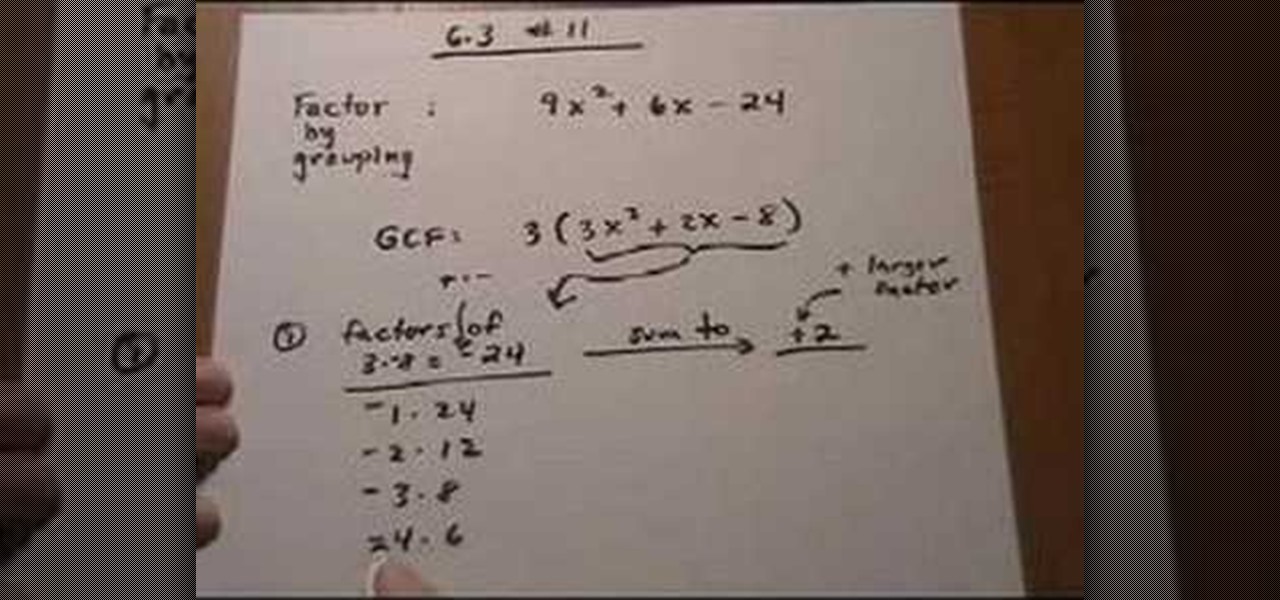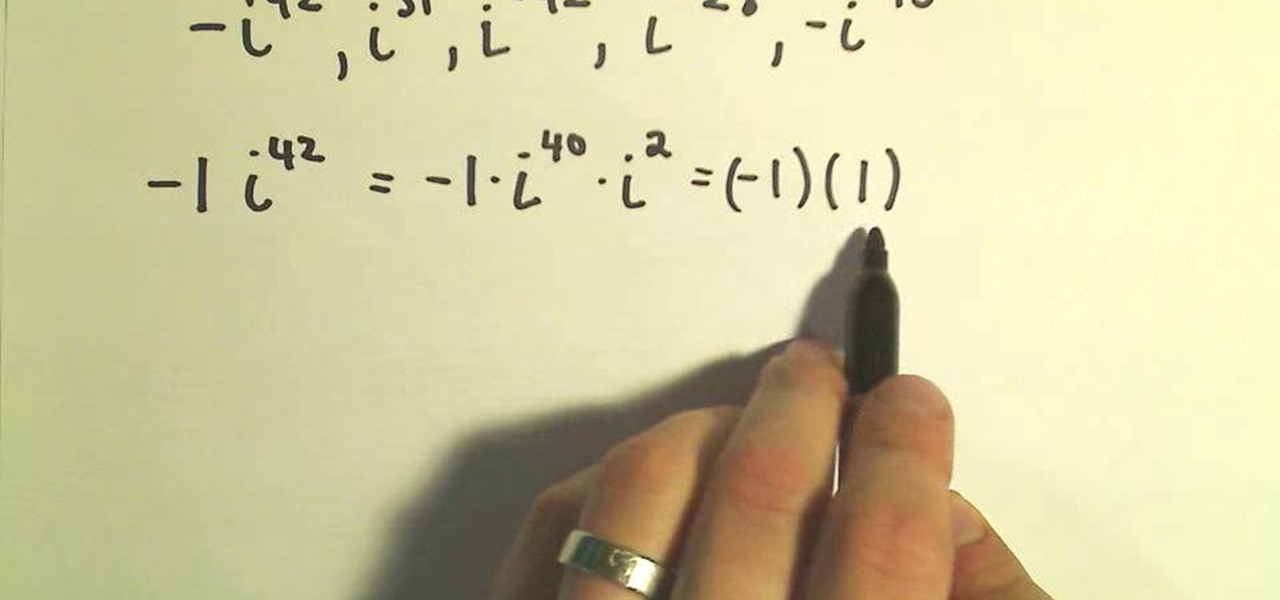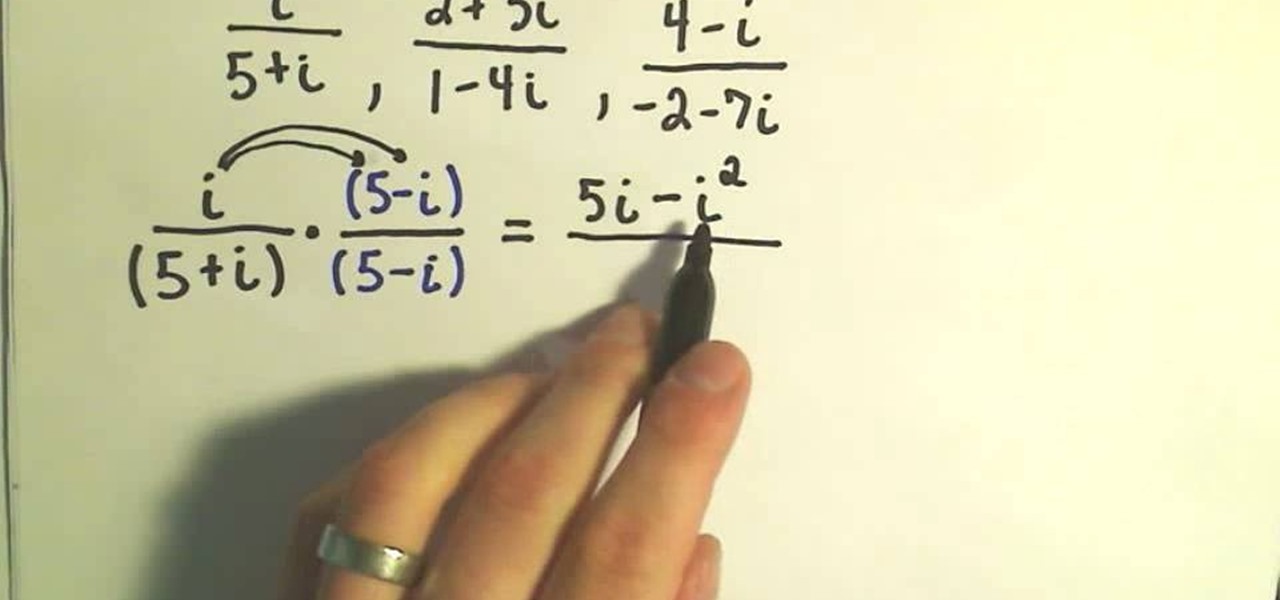Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!
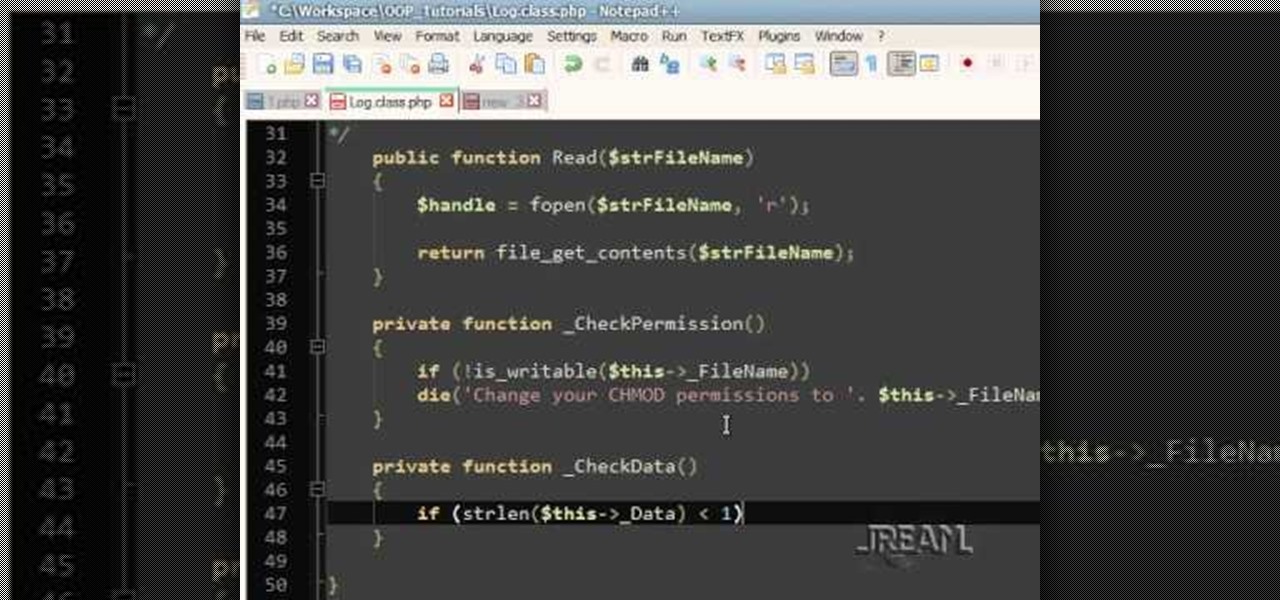
In this tutorial, learn to setup private properties(variables) and private methods(functions) with your PHP OOP programming. This tutorial will have the file logger run through some private methods. Check it out and open the door to the world of PHP programming.

Need help reducing radical expressions without perfect square or cube roots? Take heart: this free math lesson will ensure that you know everything you need to know for that next big test. Examples include square roots, cube roots, and 4th roots. You'll also learn a technique to simplify n-root expressions as well as how to simplify variables in radical expressions.

The leaf pattern is a variable shape in crocheting projects. Learn how to crochet a leaf pattern by watching this video handicraft tutorial.

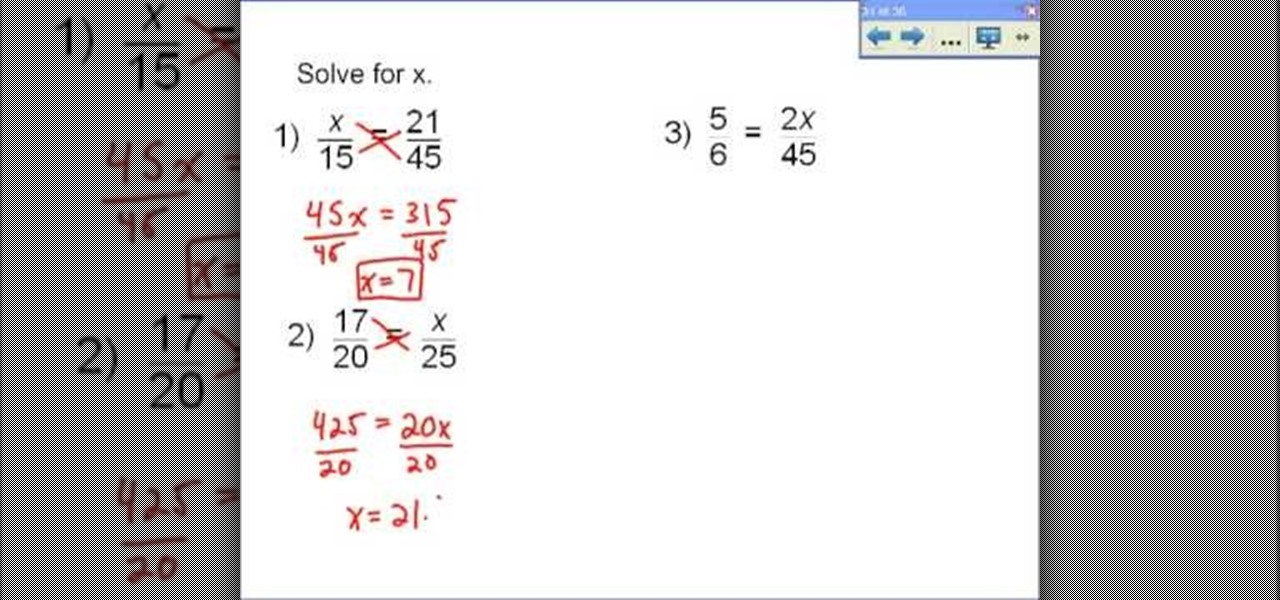
To solve a proportion for a variable you should employ cross multiplication. The basis of cross multiplication is the property which states that the product of the numerator of one fraction and the denominator of what it is set equal to is equal to the product of the remaining denominator and numerator. For example if you have x/15=21/45 you simply need to multiply x by 45 and 15 by 21 then set them equal to each other. The result of this is 45x=315. To solve this new problem for x, divide bo...

This video shows the method to solve word problems using proportions. In the given problem, we have to find the time taken by a person to type 390 words if the person takes 1 minute to type 30 words. This can be solved using proportions. We take two fractions which are equal. We type '30 words' in the numerator of the first fraction and 1 minute in its denominator. This fraction must be proportional to the second fraction. The second fraction has '390 words' in the numerator and the variable ...

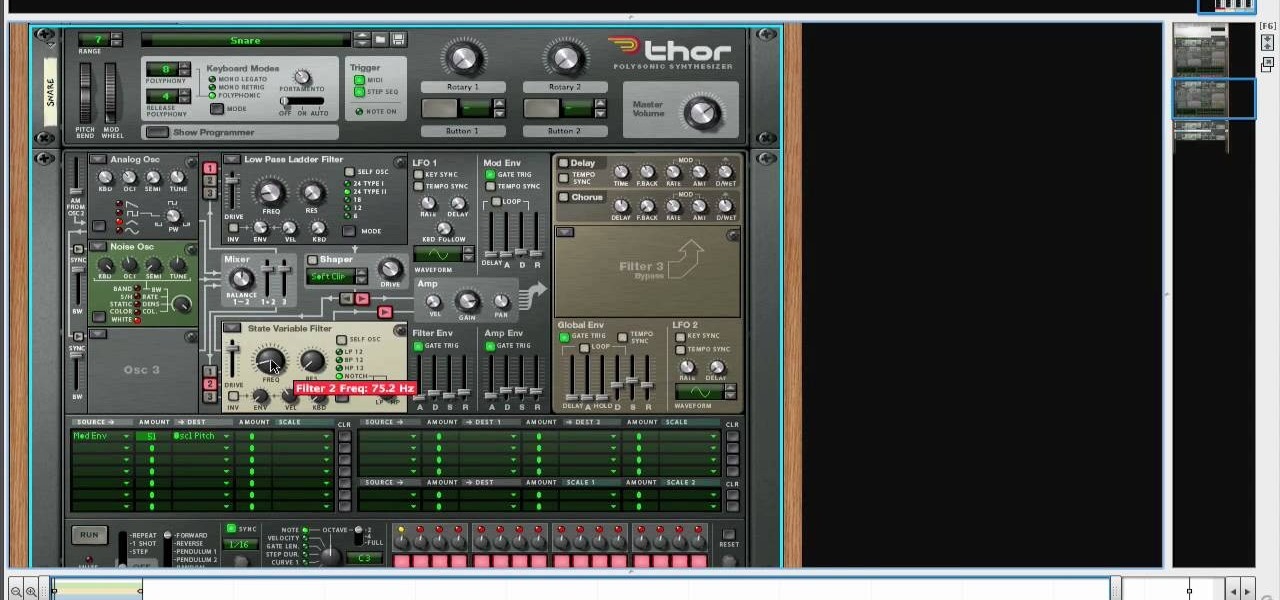
Create drums sounds using Reason's Thor synthesizerYou can use the Thor synthesizer to make a kick, snare, hat and clap sound.Kick:Use the analog oscillator with triple wave form octave3. Set the source to mod envelope 45 destination oscillator 1.Use a very short attack to K and release time. You get the short effect of pitch. Try different oscillator types to get different textures.Snare: Use the same basic patch that we created for the kick. We will keep it as the basis for most patches for...

What's up guys! It's time to discuss strings in more detail. Review

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

In this tutorial you are shown exactly how to do algebraic long division when terms are missing in the polynomial. Follow these steps and you can divide whatever you'd like:

This lesson describes the method to find the factors of a trinomial, which consists of three terms, by grouping. First of all, factor out the greatest common factor (GCF), and write the reduced trinomial in parentheses. Let the terms of the trinomial be written in order of exponent of the variable. For example, 3(3X2+2X-8) trinomial is written in the order of variable, with 3(GCF) factored out. Now identify the coefficient of the first and last terms, for example in this case, it is 3 and 8. ...

This video will show you how to drill a clean hole in ceramic, porcelain, clay, glass or tile. Materials needed for this project are: carbide tile bit, normal variable speed drill (not a hammer drill), air tool oil, plumbers putty, MDF board or a scrap piece of wood.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

The S9 and S9+ are both fantastic phones. However, there's no getting around the fact that the S9+ has its advantages. In fact, it's an objectively better smartphone than its smaller counterpart — Samsung has given the S9+ features not found in the S9, meaning you'll be missing out if you choose the 5.8" Galaxy over the 6.2".

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

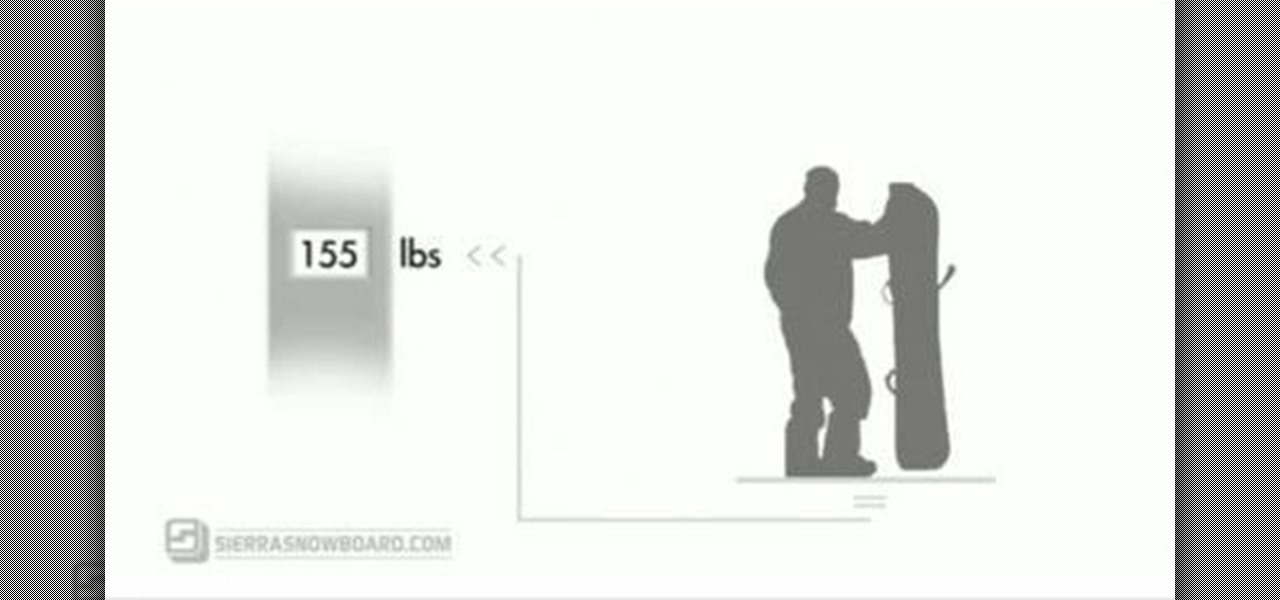
In this video, Sierra Snowboard gives us some tips on how to select the snowboard that's right for you. Each board comes in a number of different sizes, and most boards come with a size chart specific for that board. These charts can be vague, but are good starting points for selecting your size. One thing to consider is your bossy type. The weight of the rider is the primary factor in selecting the size of a snowboard. You'll notice that the height of a rider is not listed on a size chart. I...

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

I'm back! We're learning Java WhileLoops today.

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.

Want to learn how to do quick scoping in BO? It's easy: use the variable scope and zoom in to the second or third level of magnification. Voilà. No more two-second delay when shooting. For a complete walkthrough of how to quick scope, watch this gamer's guide.

The powers of the complex number "i" run their course in a cyclical nature, like annual seasons of "American Idol." Simplify your life - or at least your math class life - by learning how to rewrite the powers of "i" into simple, single variable expressions.

This series on complex numbers will help you solve equations with the cute variable "i" with ease by multiplying by the conjugate.

Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to store variables in an array index when writing code in the Java programming language. For more information, including detailed, step-by-step instructions, watch this helpful programmer's guide.

The Wedge ROP is a render output driver, which can be used to change variables on the fly while rendering. This can be very useful when simulating, in that you can test out different parameters to see the different results. It's a relatively new feature in Houdini 9.5.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

This video teaches the basics of Ohm's law, which is an important equation in electrical engineering. The three variables which are used in this equation are V, which stands for voltage, I for current, and R for resistance. The equation for the law itself is I=V/R. This law defines the relationship between these three very important electrical properties. The host of the video further explains what voltage, current, and resistance are and how they work in relation to an electrical current. Gi...

Looking for instructions on how to solve linear equations with multiple variables and constant terms? Look no further. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free ma...