Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

While still extremely awesome, the Samsung Galaxy Gear smartwatch is limited as to what you can download on to it, especially apps. It also doesn't have its own internet access (only Bluetooth), so apps like Instagram, Facebook, and Vine have yet to make their way to the Gear Store.

Nerds get a bad rap most of the time, but on Halloween, everyone wants to be one. However, not everyone knows how to geek it out without going too far. There is a limit, even for nerds, and these eight Halloween costumes are nerdy times pi.
We've all been there. Your phone's either dead or barely hanging on with a few minutes of life left, and you only have a small window of time to charge it before you need to head out. Sure, you can charge it for the few minutes you have, but what's the point if your device is going to die again in several minutes?

Particles, such as electrons, have a property called spin which can be measured at any angle, but when measured always results in one of two answers—up or down.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

Java is one of the world's leading programming languages thanks to its virtually endless array of applications. Since Java's initial release in 1998, this Open Source platform has become beloved by coders for its speed, flexibility, and dependability.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

Even if your cat drives you a little nuts, don't worry, because a new study says that cats pose no risk to your mental health.

With the height of the flu season ahead, there are some good reasons to keep a flu vaccination in mind.

Apple just unveiled the new iPhone 7 and 7 Plus at their September event, which means we're inching closer to traffic jams, parking lot fights, and day-long lines at Apple Stores, as well as those inevitable, dreaded words: "sold out."

Caramel is delicious, but it can be a tricky flavor to incorporate into baking. Traditionally, caramel is a liquid, and that doesn't always suit dessert preparation since adding extra liquid to baked goods can ruin them. So how do you get that buttery, toffee-like flavor?

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

Almost every bread recipe will tell you to look for a golden brown crust or to tap on the bottom of your loaf and listen for a hollow sound. That visual and sound technique will work most of the time, but it can still come up short, leaving you with a soft and gooey spot in the middle of your loaf.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Hi everyone! In the previous part of this series we introduced remote code arbitrary execution via buffer overflows using all of our past experiences.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

It's a small but very real frustration: you want a chilled drink, but you open the freezer only to see nothing but empty ice trays. Fortunately, there's a simple way to make ice cubes quickly—use hot water. Yup, you read that correctly. Hot water freezes more rapidly than cold.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

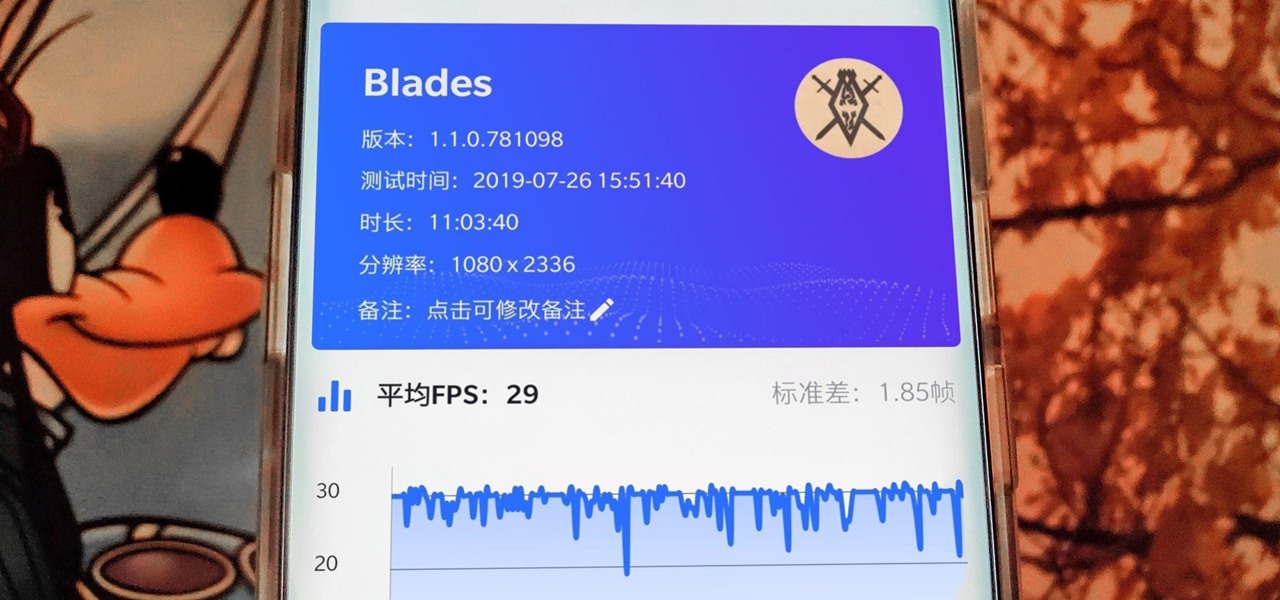
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Before, the only way to really tell how your iPhone's lithium-ion battery was performing was to use tools such as Geekbench and Battery Life, but now Apple has included some quick battery health checks right into iOS 11.

So after setting everything up, creating the system, working with focus and gaze, creating our bounding box and UI elements, unlocking the menu movement, as well as jumping through hoops refactoring a few parts of the system itself, we have finally made it to the point in our series on dynamic user interfaces for HoloLens where we get some real interaction.

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.