Welcome! Today I would like to share a few hints about picking the right color. So, if you do not know what color your today's outfit should be or your or which color you should choose for your room walls, please follow my suggestions.

Fencing is a fun sport and a great activity for kids to be involved in. It teaches critical thinking and improves reaction time, and this video will give you an introduction to the world of fencing, learning about the épée, foil or sabre sword and even the rapier.

This fast tutorial will show viewers the basics of how to use Facebook for those who are new to using the website. After creating an account and logging into Facebook, you will see your homepage, which has most of the new information regarding your friends and their recent activity. Clicking on the links at the top of the page will allow you to access pages such as your own profile, where you can display information about yourself, such as where you work or your date of birth. After watching ...

Learn how to use the future perfect tense in English with this ESL tutorial. The future perfect is the perfect tense for setting goals with deadlines. A deadline is a date that you must complete an activity or job. For example, by this time next year, what will you have achieved/done/accomplished in your life? You should say, "I will have ____" In the underlined part, put a past participle, such as "I will have found a new job by this time next year." Watch this how to video and you'll be spe...

Want to scare your friends with some paranormal activity? Learn how to make this illusion with through your cell phone camera and make ghosts appear with the help of this how-to video. This should convince your friends ghosts exist. All you need is your camera phone and a piece of clear plastic with a black smudge on it. Watch this instructional video and learn how to make a fake ghost appear on your cell phone.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Before you go ahead and delete your Facebook — don't lie, you've been thinking about it — consider this. Facebook offers users a wide variety of privacy options to mess with, which can help you find a little control over your information. We're not saying this solves Facebook's privacy crisis, but it might be a more reasonable option than throwing in the towel entirely.

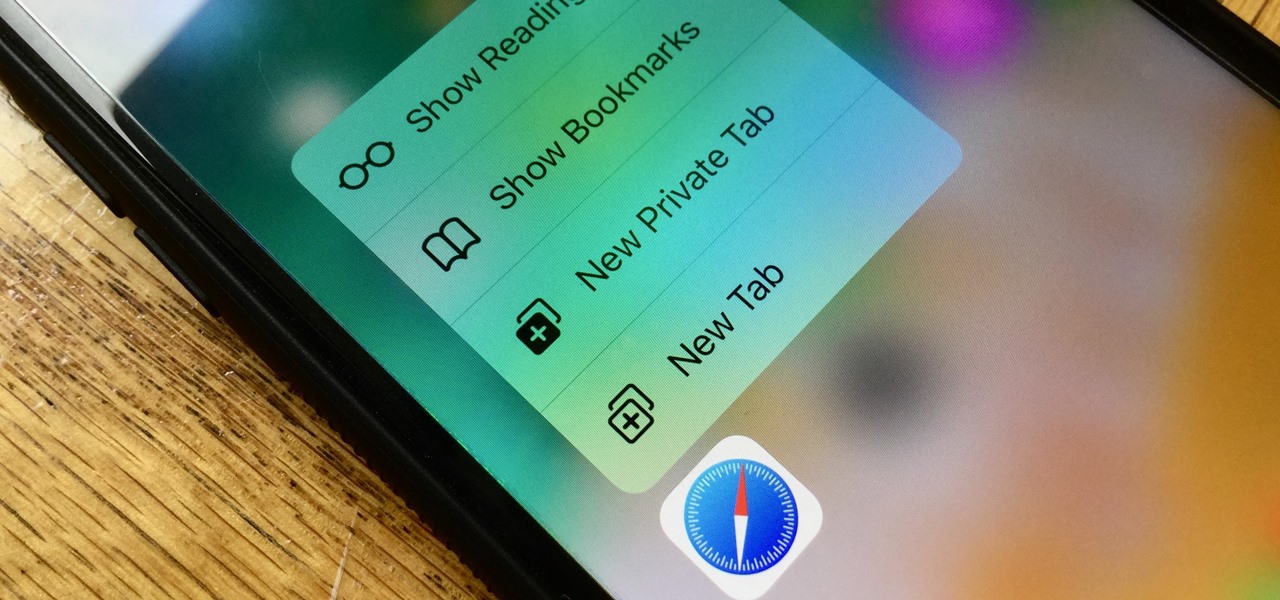
Introduced on the iPhone 6s, 3D Touch is just about the closest thing to a "right-click" that we have on iOS. Apple and app developers utilize this feature to give us helpful options that might otherwise clutter the overall app experience, as well as opportunities to "peek" into an action without committing to it. Safari on iPhone is no exception.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

See how to hack Pet Society from Playfish! Pet Society is the popular online game where you can design and take care of virtual pets. Check out this video tutorial to learn how to cheat Pet Society: Coin hack (11/15/09).

This how to video shows you the step by step process of making a baby beaded frog. This is easy and fun activity to do with your kids. Beading is a great way to introduce your children to the creativity of arts and crafts. This is a good project for older children because it does involve small beads that can be swallowed. With this how to video you will be able to teach your children how to make a beaded frog.

Braiding, cutting, binding and piercing are all activities that are necessary for quilting. Learn more about how to create your own quilt in this free video series.

With Apple's newest iOS software update, you can turn your iPhone into a smart display that's always on when you're not actively using it. So your iPhone can quickly transform into a bedside clock, digital photo frame, miniature HomePod, Live Activities tracker, widget-monitoring screen, and more.

Apple released the newest update for iPhone, iOS 14.5.1, today, Monday, May 3. The update (build number 18E212) is the first since iOS 14.5, which Apple made available one week earlier on Monday, April 26.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

With stay-at-home orders for most of us in the US because of the new coronavirus, many of you are likely struggling to be productive and efficient when working from home. Unless you've worked from home before, it can be challenging to separate work from personal life throughout the "workday." But your iPhone can help make the transition easier and more successful.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

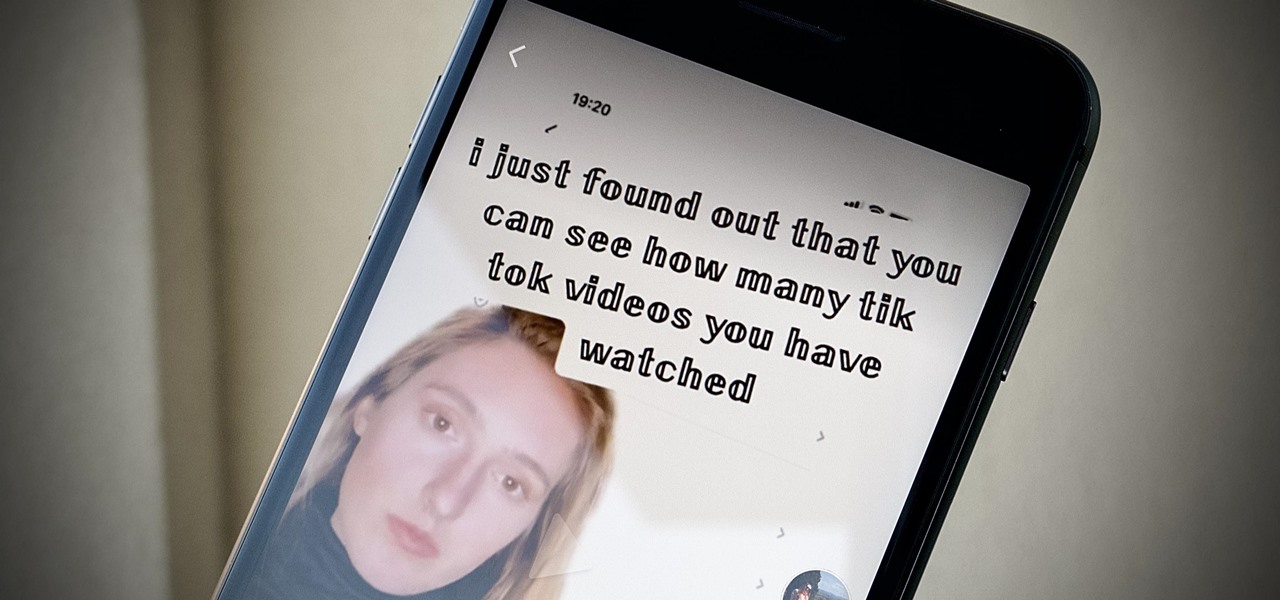
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

Google's push for your safety gained some much-needed attention when it released the Pixel 4 smartphone. It has an app called "Personal Safety," which uses the array of built-in sensors on your phone to detect if you've been in a car crash. The futuristic safety feature was exclusive to the Pixel 4 initially but is now available to all Pixel owners as well.

If you thought the news coming from China about the coronavirus might not affect your daily life in Europe and in the Americas, think again.

After three rounds of beta testing, Apple finally released iOS 13.3.1 today, Jan. 28. It's the latest update to iOS 13, coming exactly seven weeks after the release of iOS 13.3. So, what's new?

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.

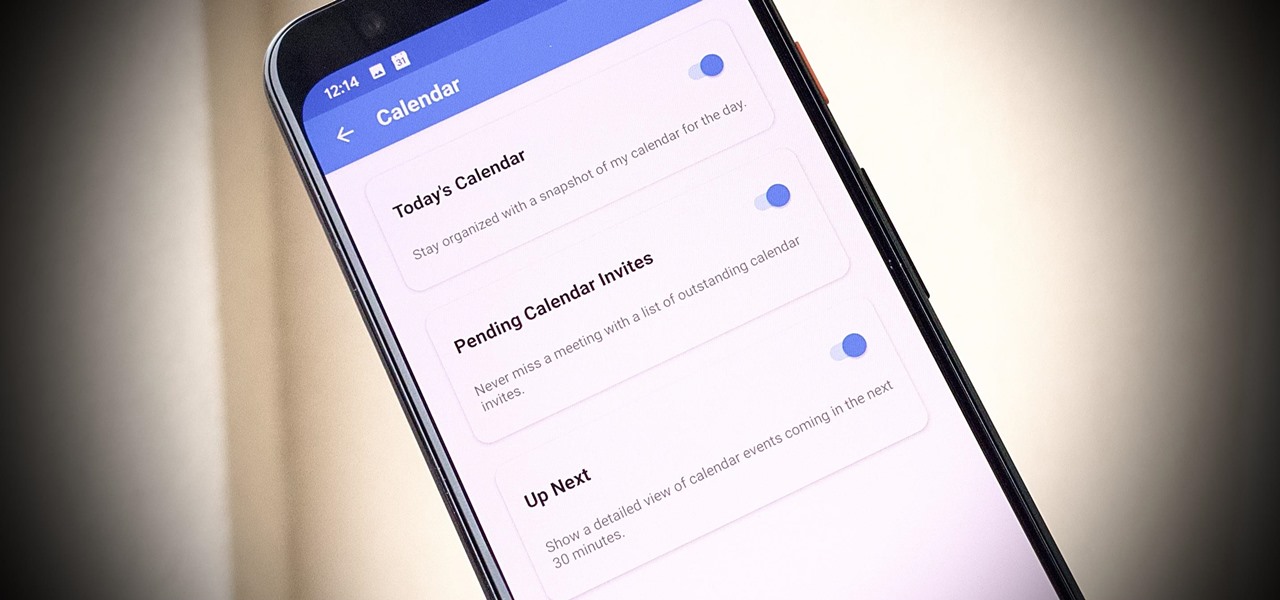
One of our favorite email apps, Edison Mail, just got even better. In versions 1.17.0 (iOS) and 1.12.0 (Android), the app introduced a new Assistant, a powerful tool that makes organizing travel, packages, entertainment, bills, calendar, and more a breeze over email. The best part? You can customize it to your liking, so the Assistant works precisely as you need it to.

In iOS 13, Apple introduced HomeKit Secure Video, which allows smart home devices with cameras to give iPhone users a private and secure way to store recorded videos. Plus, it has benefits such as object detection and activity notifications. Logitech is the first to add support for HomeKit Secure Video with its Circle 2 cameras, and all it takes is a quick firmware update to get started.

The wait is finally over. Apple just released iOS 13.2 for iPhone, the latest update to this year's iOS 13 release. The update contains a slew of exciting new features, such as Deep Fusion for 2019 iPhones, a suite of new emojis, the long-awaited Announce Messages with Siri, among many, many others.

Best known for its mobile phones and television sets, South Korea's LG has had a quieter presence in the US compared to the country's homegrown efforts.

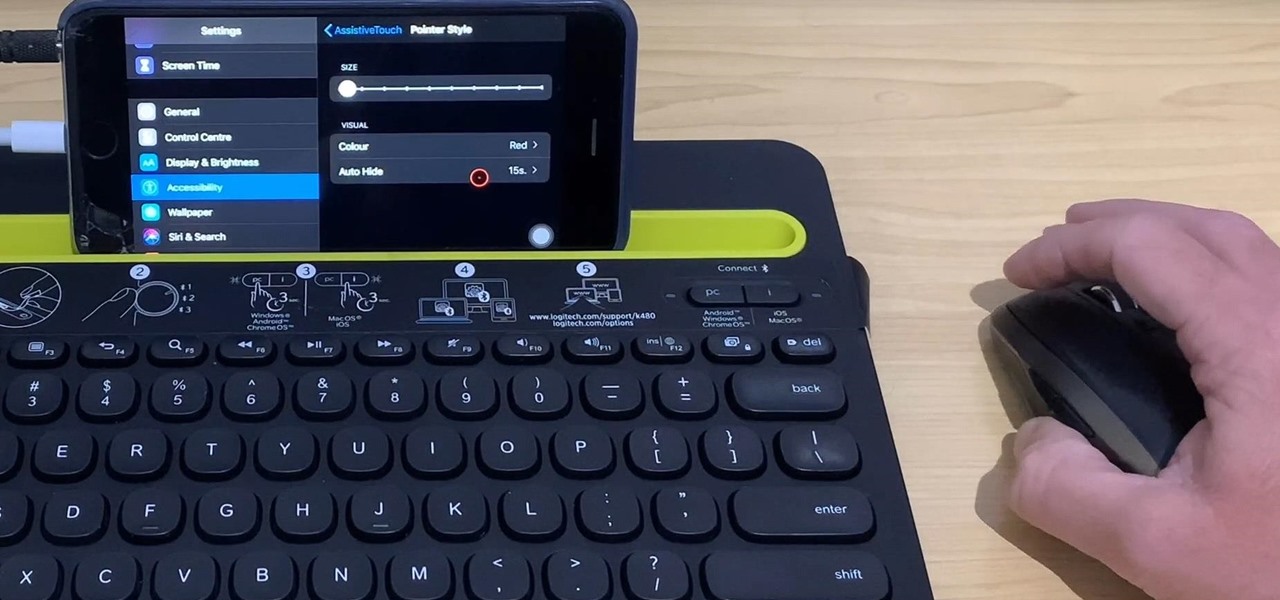
True home automation doesn't require interaction from the user. But let's be real, no system is going to be 100% autonomous. You'll always need a manual override for situations programming can't account for. So what's the best manual override system? I'll tell you right now, it doesn't involve yelling at Alexa or Google.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

The photos and videos you take with your iPhone contain bits of information, known as metadata, including the location where they were taken. This metadata makes it easier for Photos to organize your media, but put these photos and videos in the wrong hands and anyone can find out where you live or work. Luckily, iOS 13 makes it easy to wipe the geotag from images and videos before sharing.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Over the years, TV has become more of a solo activity than ever before. It is exponentially more difficult to discuss the latest shows with friends since platforms like Netflix just release all episodes at once. Luckily, Snapchat makes it easy to keep your pals in the loop on what you're watching, so they can pick up the remote and do the same.

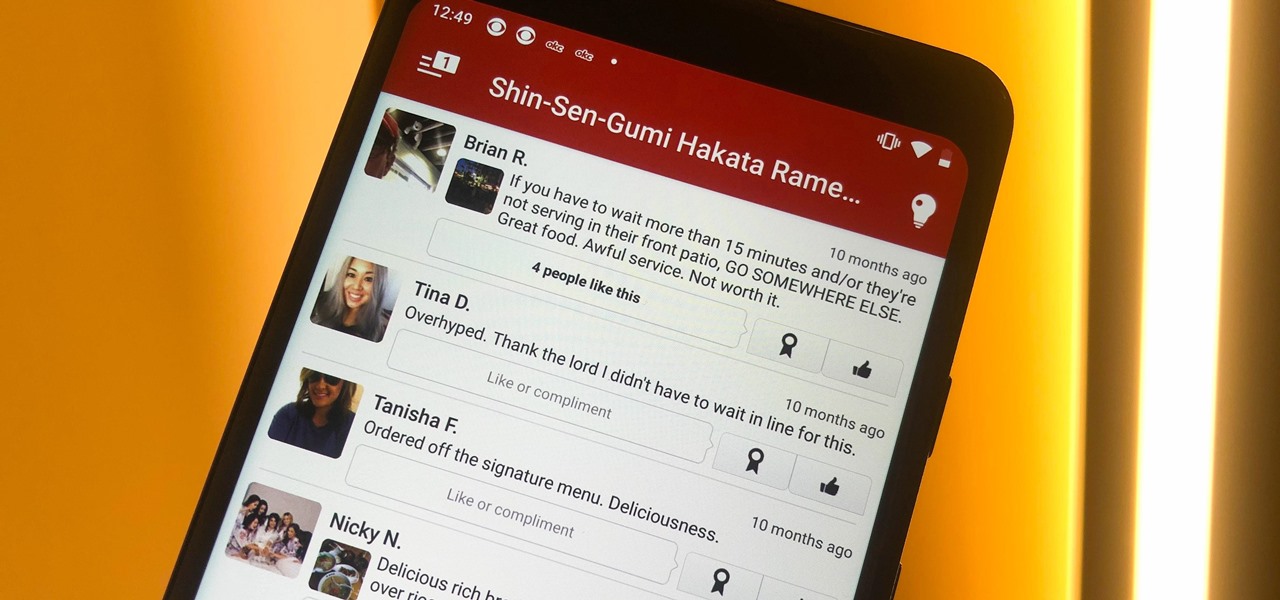
Yelp reviews are great for getting a feel for how a business operates, but they can't always be trusted, and they don't always get to the point fast enough. That's where "Tips" come in, and you can view and make them whether you're on an iPhone or Android phone.

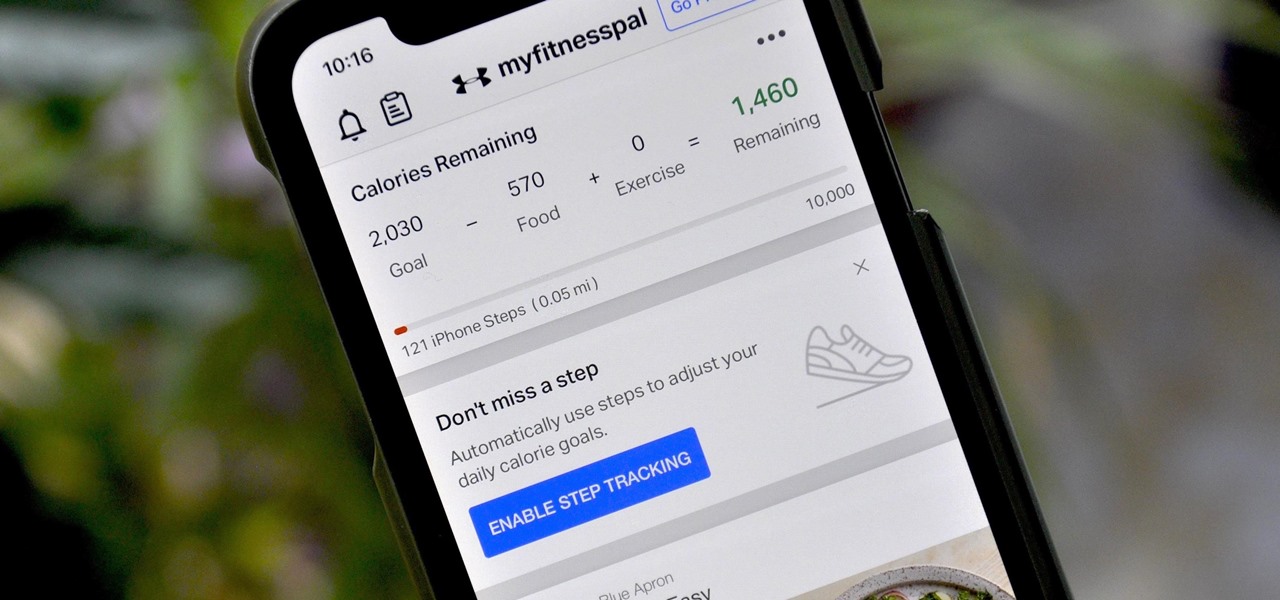
If you're new to MyFitnessPal, it might seem daunting. The app is way more than just a calorie counter, but that's because getting fit is just as much about changing your lifestyle as it is about watching what you eat. So don't let it overwhelm you — there are just a handful of tips you should know to hit the ground running.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.