To much of the United States, Zika seems like a tropical disease that causes horrible problems in other countries but is nothing to be worried about stateside. It may make you rethink your beach vacation abroad, but not much more than that. However, if you live in Florida or Texas, the possibility of getting a Zika infection where you live is real — and local outbreaks are more and more a possibility.
When it comes to note-taking, Google Keep is one of the most diverse and functional applications on the Android platform. Sure, there are a plethora of other note-taking apps to choose from, such as ever popular OneNote and Evernote, but Google Keep differentiates itself from the crowd with its user-friendly interface and Google Now integration.

With certain apps and games, it's all about the settings. In order to get your money's worth with one of these, you simply have to take the time to tweak and adjust various options, which is something a lot of users don't necessarily want to do.

In recent weeks, some people have been shunned from the Null Byte community because they expressed "black hat" aspirations. This is because Null Byte is the "white hat" hacker training/playground. Although most of us think we know what that means, it does beg the question; "Who and what is a white hat hacker?"

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

When a migraine strikes, it can be crippling. Intense and sharp pain not only at the temples, but radiating throughout the entire head; feelings of nausea and digestive discontent; an unbearable aversion to light, sound, and even the smallest of movements.

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

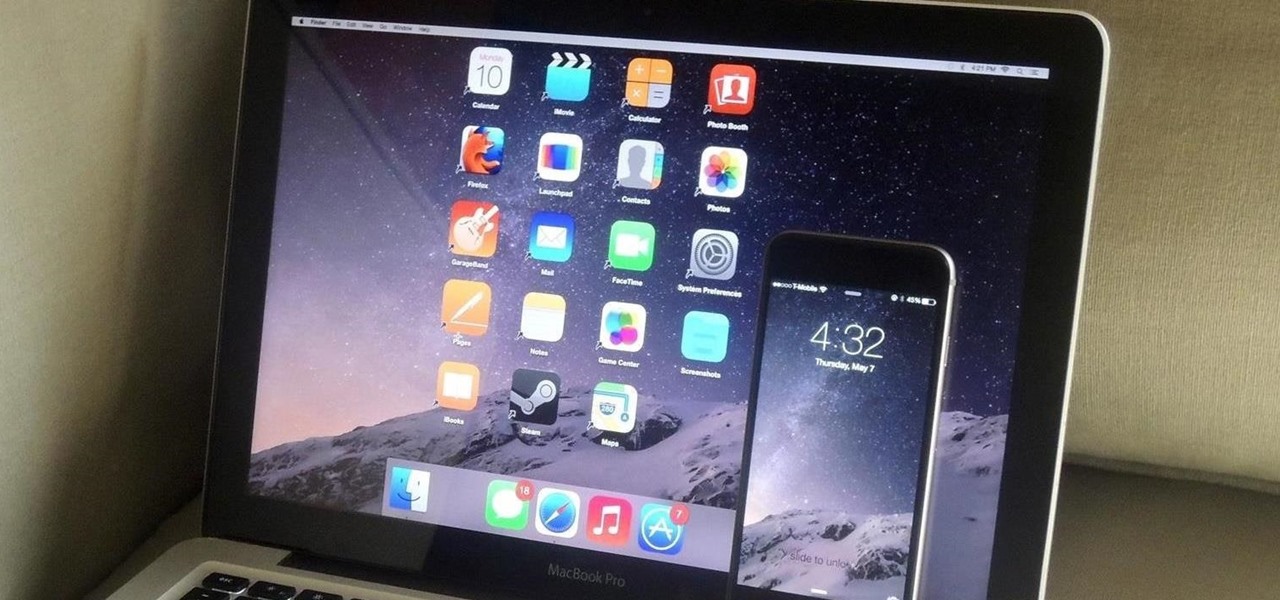
Is your Mac starting to feel messy and sluggish after using iOS 8 on your iPhone every day? Even with all of the iOS-friendly features built in to Mac OS X Yosemite, your Mac can still feel kind of "old" in comparison to an iOS device—but it doesn't have to. Using the tips and tricks below, you can easily make your Mac desktop or laptop look and feel like iOS 8 in no time.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

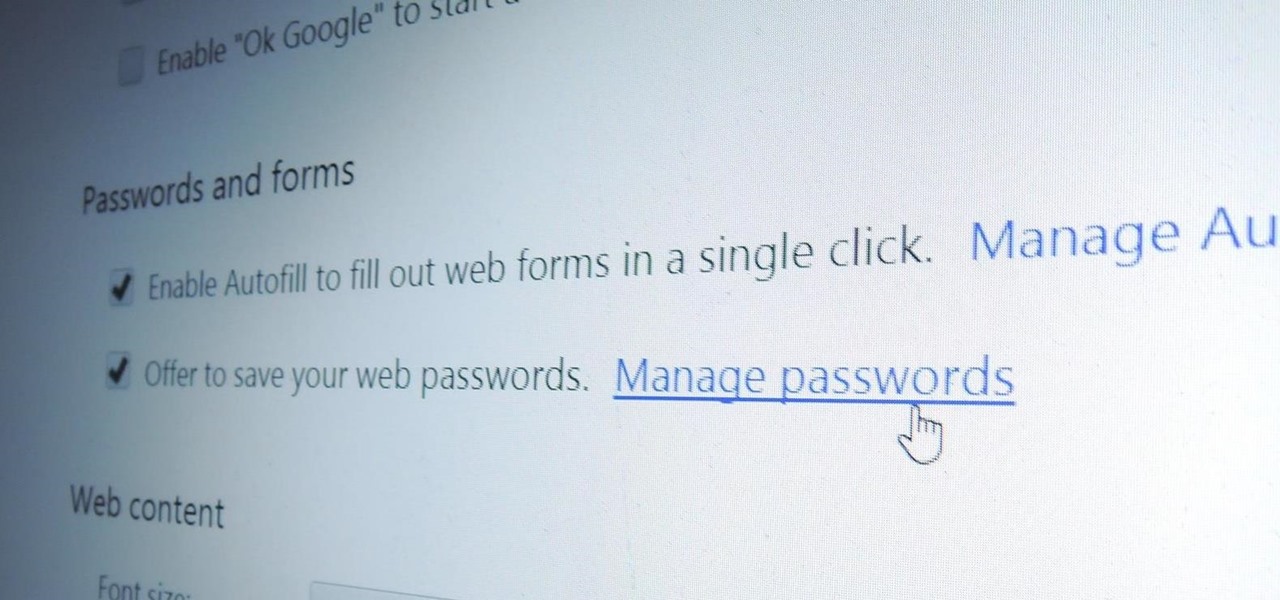
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

What separates the work habits of the ultra-productive from us mere mortals struggling to check items off our never ending to-do lists? While the answer to that question is by no means simple, one undeniable factor in their success is a clearly defined, highly organized workflow.

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Deep in the crevasses of the Songshan mountain range, an Indian dhyana master established the first Shaolin Monastery in 477 AD, seeking to spread the relatively new teachings of Buddha at the time. This monastery then bred the Shaolin monks, who are now popular for their incredible feats with Chinese martial arts, particularly with Shaolin Kung Fu.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Shorts, learning from your audience and the fundamental plausibility of being hustled in the desert Mike Clattenburg, creator of Trailer Park Boys and Afghan Luke, was kind enough to talk to us from Nova Scotia, where he was hard at work in preproduction, about Crackin’ Down Hard, his short that screens Monday and Tuesday as part of TIFF’s Short Cuts Canada Programme. We picked his brain about realism versus surrealism in comedy, the virtue of shorts, and the virtue of turning negative skinny...

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

Apple's built-in search on iPhone is an incredibly valuable tool you shouldn't ignore or underutilize, and we're here to show you why. So, buckle in because this list covers hidden and lesser-known Spotlight features that will leave you wondering how you ever lived without Spotlight Search on iOS.

Not everyone stickers, but that's going to change with Apple's new sticker options on iOS 17, iPadOS 17, and even macOS Sonoma. Before you know it, people everywhere will be adding stickers to messages and emails — including you.

If you're sick of seeing some of your contacts' faces in the sharing menu every time you share photos, apps, webpages, or other content on your iPhone, or if you want to keep nearby eyes from sneaking a peek at the people you frequently share things with, you can make some or all of them disappear.

While the iPhone came before the first Android smartphone, every new iOS version seems to include a wealth of features already existing on Android, and iOS 17 is no exception.

There's more than one way to get free credits and discounts in the Google Play Store for apps, games, books, movies, in-app items, and other Play Store content. You may know a few of them — but some of these may surprise you.

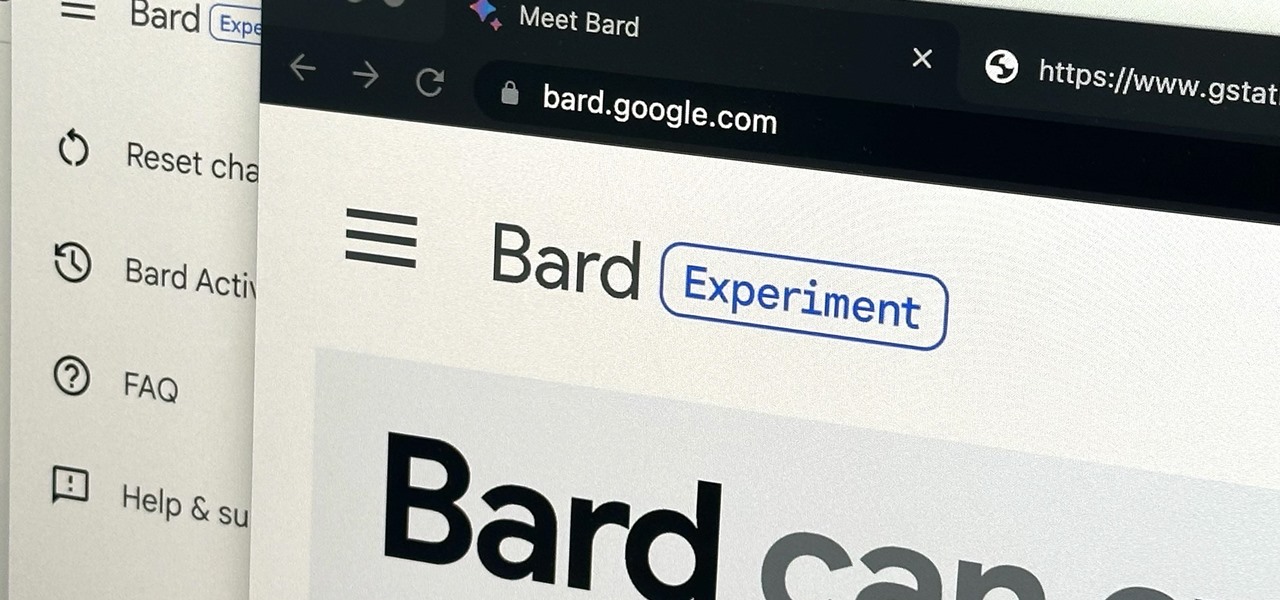
Generative artificial intelligence has taken the tech world by storm, and Google's AI chatbot will give you a taste of what it offers.

With the prestige appeal of its original programming and relatively low subscription price, Apple TV+ is one of the more appealing streaming options out there — and you don't need an Apple device to subscribe and watch movies, TV shows, sports, and other Apple TV+ content.

The close of the second quarter of 2021 brought about a flurry of merger and acquisition and financing activity in the augmented reality industry, headlined by the acquisition of Ubiquity6 and JigSpace's new multimillion-dollar funding round.

Apple released the first public beta for iOS 14.5 on Thursday, Feb. 4. This update is proving to be the most significant in some time, offering new features and changes like support for PS5 DualSense and Xbox Series X controllers, the ability to unlock your iPhone using your Apple Watch, AirPlay 2 support for Fitness+, Reminders sorting and printing options, 5G support when using dual-SIM, and more.

Buckle up, iPhone users, because it's update time! Apple just released its latest iPhone OS to the public, iOS 14.4. This new edition isn't the company's most ground-breaking, but it doesn't come up short, either — you'll find support for smaller QR codes in Camera, a new "Device Type" setting in Bluetooth, support for a new Apple Watch face, and a major privacy feature, among other new changes.

Users on Android could customize their app icons for some time, but it's a relatively new addition to the iPhone. You could change icons since iOS 12, but it really took off in iOS 14 and got even better in iOS 14.3. Still, it's not as easy as on Android, and you'll see a notification every time you open an app with your custom icon. However, there is a workaround to stop those annoying notifications.

Instagram isn't as link-friendly as other social media platforms like Twitter and Facebook. Still, when you do find and open a link, whether it's for a petition or a product, you may want to find it again later. That's why Instagram keeps track of every link you've ever opened. That way, if you ever need to revisit a webpage, you don't have to find the original post or account from last time.

Instagram is addicting — and that's done on purpose. To stop your Instagram habits, your smartphone likely has a built-in feature to curb the daily usage of a particular app, like Apple's Screen Time for iOS and Google's Digital Wellbeing for Android. But you don't need to mess with those complicated settings when Instagram itself can help you get some of your life back.

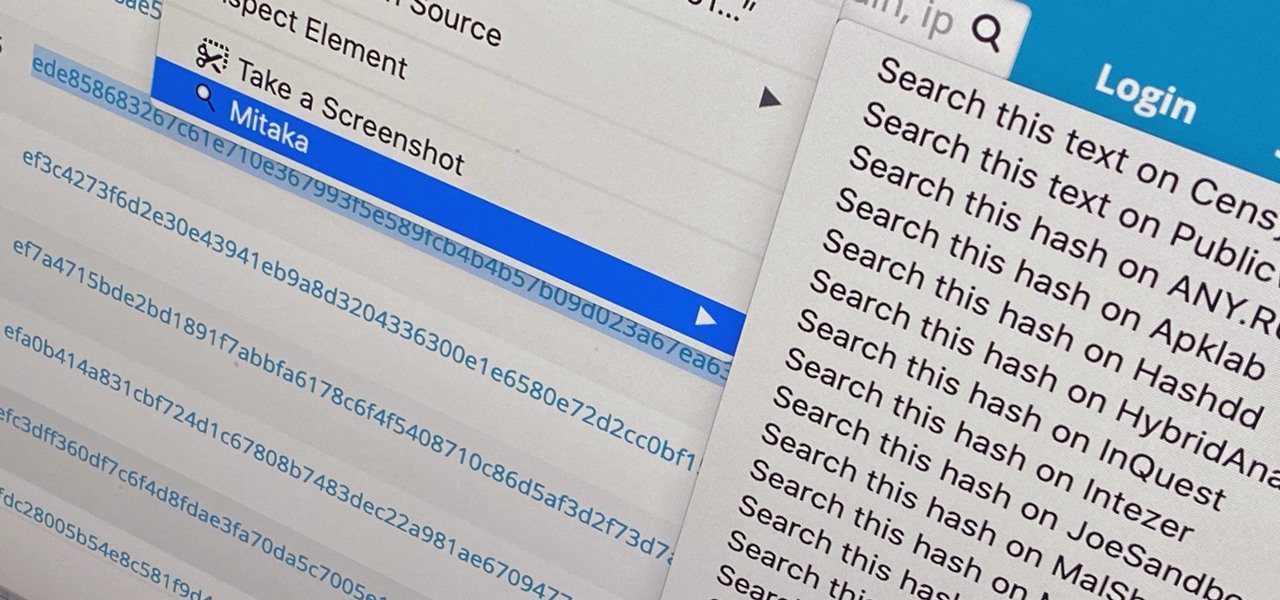
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.