When iOS 17 first came out, the iPhone's Clock app received a giant new feature, one that lets you set multiple timers and keep track of them on the Lock Screen, Notification Center, and Dynamic Island. Now, the iOS 18 software update gives us something just as exciting for the stopwatch.
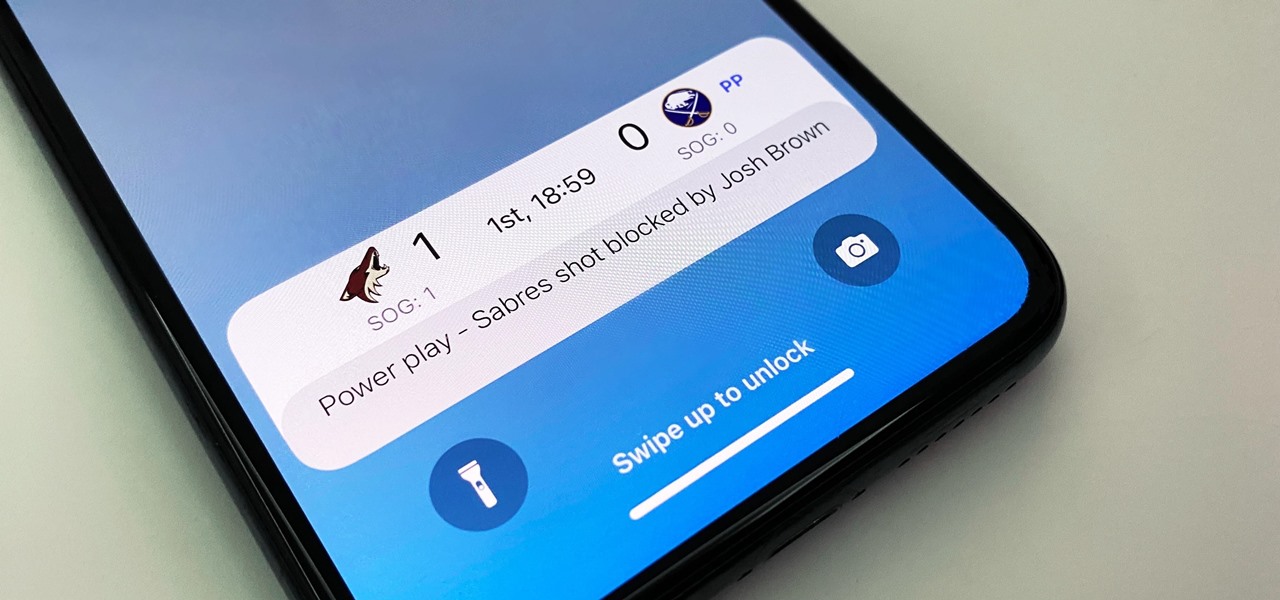
Live Activities is Apple's hottest new feature for iPhone, but it's not always straightforward. Sometimes you'll trigger one without realizing it, but it may seem frustratingly impossible to start one when you really want it.

In this tutorial, we learn how to find your recovery heart rate. First, get your heart rate up by doing some sort of activity that you enjoy doing. After you have your heart rate up, figure out how many beats you have in fifteen seconds. After you have counted this, multiply it by four. Now, sit back and relax for two minutes exactly. Next, time another fifteen seconds with your stop watch and count how many beats your heart has. Multiply this number by four, then subtract the two numbers. Af...
If you're sick and tired of you laptop dying all the time, then the answer may be right in front of you— power management. In Windows 7, it's easy to control your power settings to help you laptop's battery last longer. Watch and learn from none other than Microsoft.

Keith Ferrazzi teaches you how to be outgoing. Although it is difficult to talk to people you don`t know, you might miss out on opportunities if you don`t. Only by reaching out to people, you will meet them and they may get to know you enough to perhaps be of help to you in your carreer. You have to learn how to speak up. One way is to pick a role model in your social circle who is outgoing and watch how they behave and listen to what they say. Joining a Toastmasters group is also recommended...
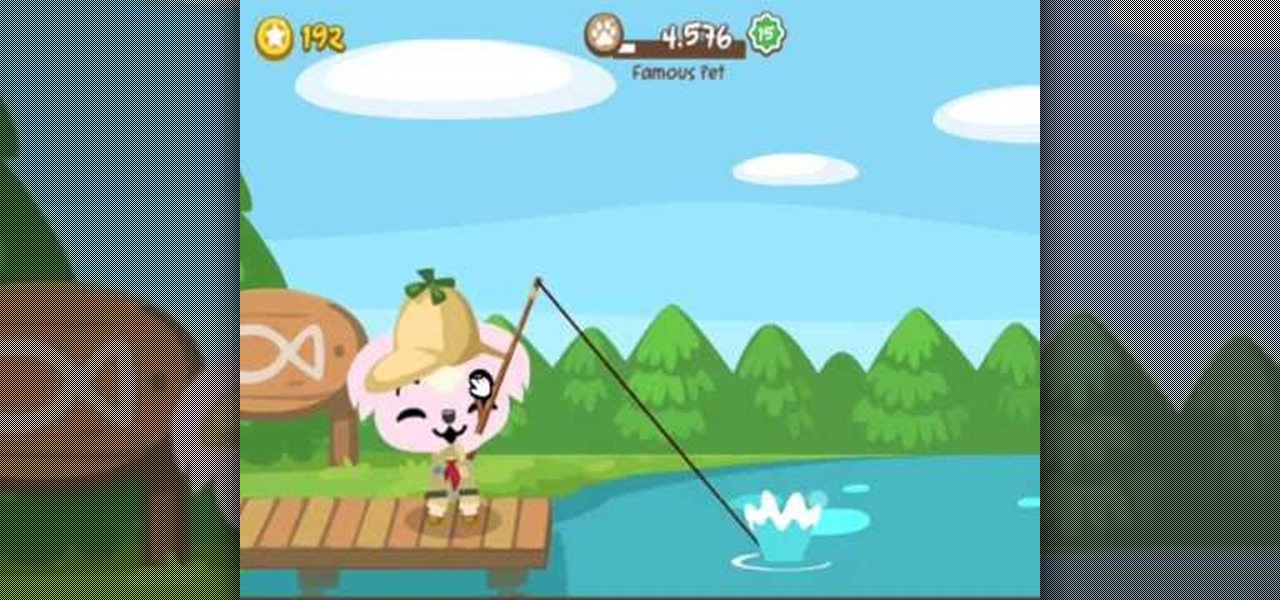
See how to hack Pet Society from Playfish! Pet Society is the popular online game where you can design and take care of virtual pets. Check out this video tutorial to learn how to fish in Pet Society (11/15/09).

d-CON is here to help identify and remedy rodent problems in your dining room. Watch this video tutorial on how to use d-CON Quick Kill Glue Traps to kill mice in the dining room. Signs of a mouse in the dining room include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your bedroom. Watch this video tutorial on how to use d-CON Ultra Set Traps to kill mice in the bedroom. Signs of a mouse in the bedroom include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your home. Watch this video tutorial on how to use d-CON Ready Mixed Baitbits to kill mice in the home. Signs of a mouse in the home include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your bathroom. Watch this video tutorial on how to use d-CON Bait Wedges to kill mice in the bathroom. Signs of a mouse in the bathroom include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your living room. Watch this video tutorial on how to use d-CON No View No Touch Traps to kill mice in the living room. Signs of a mouse in the living room include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

d-CON is here to help identify and remedy rodent problems in your kitchen. Watch this video tutorial on how to use d-CON Bait Paste Pouches to kill mice in the kitchen. Signs of a mouse in the kitchen include droppings, footprints, gnawing, rubmarks, unusual pet activities, strange sounds, and burrows or nests.

The hamstring is a large muscle in the back of the thigh. A hamstring injury is a partial tear of the muscle. Learn how to diagnose and treat a hamstring injury in this medical how to video.

Let's face it: Church is one of the most boring activities a kid attends during the week, so try to make the drudgery at least bearable by getting your kids to do some hands-on religious crafts. This video teaches you how to weave a palm cross out of palm leaves. You must soak the leaves in water overnight, then tear them into 1/2 inch X 18 inch strips for easy, pliable weaving the next day.

In this episode of In the Kitchen with Matt, I will teach you how to make Amazing Yummy Chocolate Lego figures. These little chocolate lego men are super easy to make, all you need is the chocolate and some lego molds. All you really need to do is melt the chocolate and then place it in the molds and let the chocolate set, and then you will have chocolate lego figures! I used chocolate candy melts, but you can use whatever chocolate that you want. They taste yummy, anyone can make them. It is...

We recently showed you the Misfit Shine, a no-charge, app-oriented fitness tracker that you can grab for a hundred bucks. Sony has also decided to get in on the action with their Smartband SWR10—but this thing is so much more than a fitness tracker...the Smartband wants to "log your day, every day".

Is your kid's desk all cluttered? Help them stay organize by making an easy desk desk set for your child's school supplies. Watch this how to video tutorial as our host shows you how to make a pencil holder using a can, paper and some glue. Have your children help you with this fun activity.

Making Velcro-ball dartboards is a fun activity and good way to spend a day with the kids. Learn how to make a children's crafts Velcro-ball dartboard with expert tips in this free arts and crafts video series.

Since Apple launched iOS 13, we've seen four major updates for iPhone, each of which added some cool new features. Between iOS 13.1, 13.2, 13.3, 13.4, and all the minor updates in between, there's never been a better time to be on iOS. And now, we've got even more positive changes with the iOS 13.5 update.

Apple just released the first developer beta for iOS 13.4.5 on Tuesday, March 31. The update follows the previous week's stable release of iOS 13.4.

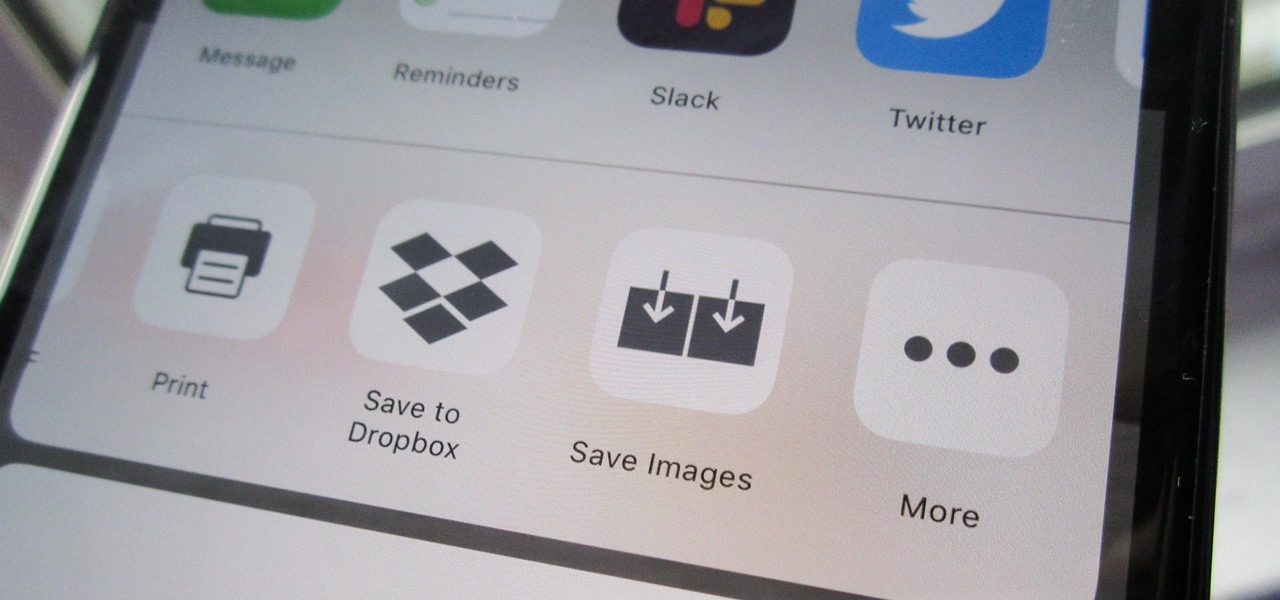
Some websites block image downloads on their webpages so you can't save them for reuse. That means long-pressing or force-pressing on protected images in Safari on your iPhone will not do anything or will omit the "Save Image" option. Taking a screenshot is the obvious solution to bypass restrictions, but you won't get the best quality. Thankfully, there's another way.

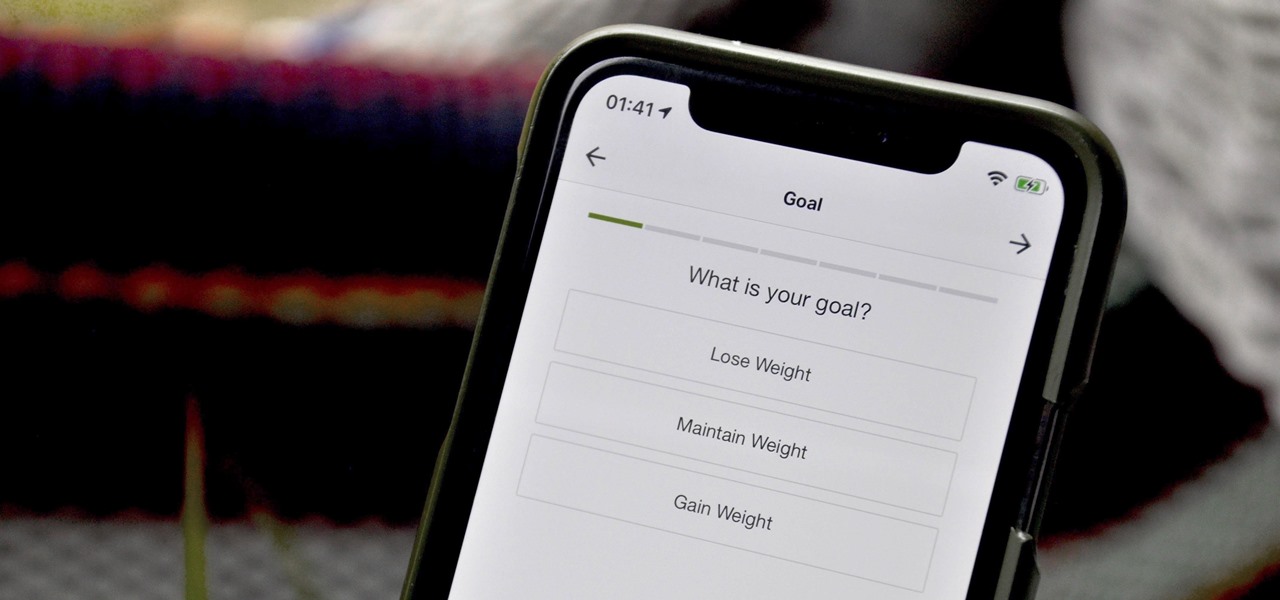
When you set up your MyFitnessPal account for the first time, it asks for a checklist of personal info to create nutrition and fitness goals for you. Whatever you decide then, it's important to know that the goals provided to you are not fixed. If your doctor or nutritionist recommends a new plan, or you simply want to change up your routine, you can customize your weekly and daily goals.

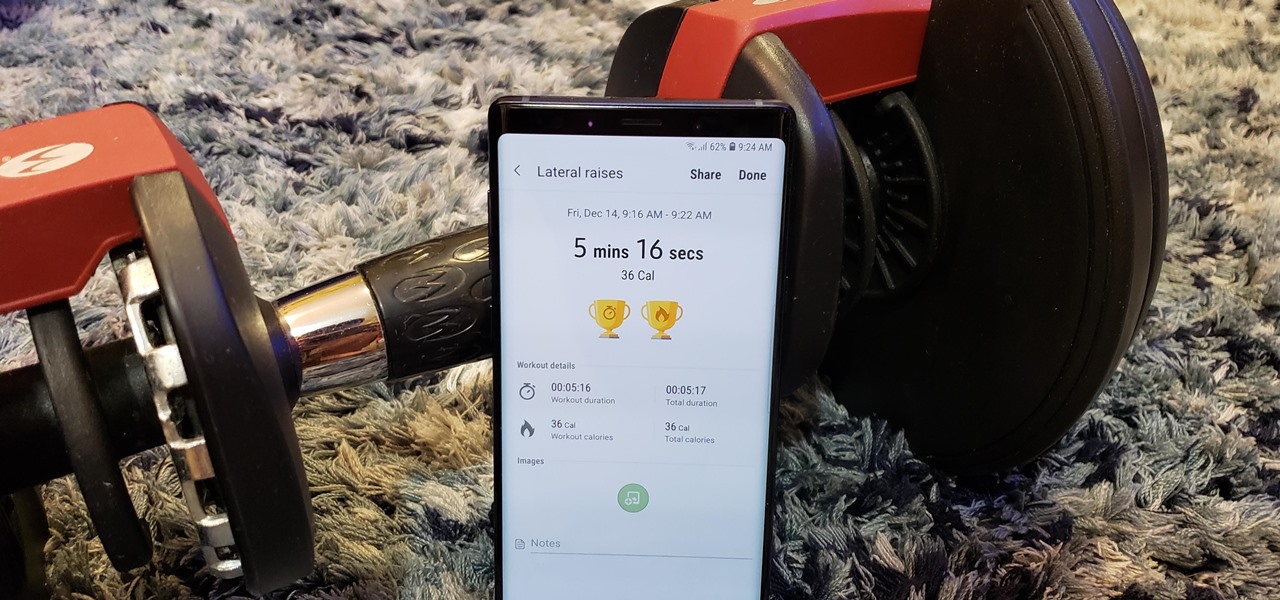
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

With iOS 12, your iPhone's Messages app has more features than ever to enhance iMessage and FaceTime. Included in these changes are the new camera effects, which allow users to add fun and unique customizations to their photos and videos with the in-app camera in Messages. Stickers, Memoji, and more await the photos you take and send in Messages. ...

Among iOS 11's many criticisms, one of the more surprising complaints came from parents worried that Apple wasn't doing enough to monitor and control their children's iPhone usage. Apple seems to have taken these issues to heart, as iOS 12 introduces new and improved parental controls to help encourage healthier mobile habits for kids.

Your dog is doing something charming, and you need to take a quick photo, but you don't have time to search in your app drawer for the camera app. The moment would have long passed by the time you find it. What if instead you could you open the camera or any other app simply by sliding your finger down on the home screen? Well with Nova Launcher and gestures, this is easy to accomplish.

The Galaxy S8 and S8+ might not have made it into the hands of the public yet, but we sure have come across a lot of the stock apps from Samsung's latest flagship phones. First, there was the new launcher, then Hello Bixby, and now, the extremely elusive Record Screen feature has been leaked.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

Having websites coded for mobile browsing is great for small screens, but if you have a Plus model iPhone or even the iPhone X, desktop versions of websites might show you more of what you want. Plus, there's the case of poorly designed mobile websites, where the desktop view is clearly the better option with more functionality and features. Luckily, asking for desktop sites in Safari is simple.

There are many, many home remedies out there for relieving itchy mosquito bites. Everything from mud to banana peels and basil leaves to Alka-Seltzer tablets can help curb the itch. But before you even have to resort to any of those methods, you should be thinking about prevention. Wearing white clothing can help to keep mosquitoes aways from your skin, and there are many plants that will help mask your mosquito-attracting smell. But there's even more ways to keep those bloodsucking bugs away.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the communities.

Last week, we rolled out a major site-wide update on WonderHowTo, making it even easier to follow the subjects you're passionate about—and easier to share your creations with people who'll give you the kudos you deserve!

It may sound like deja vu, but neural interface startup CTRL-labs has closed a $28 million funding round led by GV, Google's funding arm, for technology that reads user's nerve signals to interpret hand gestures.

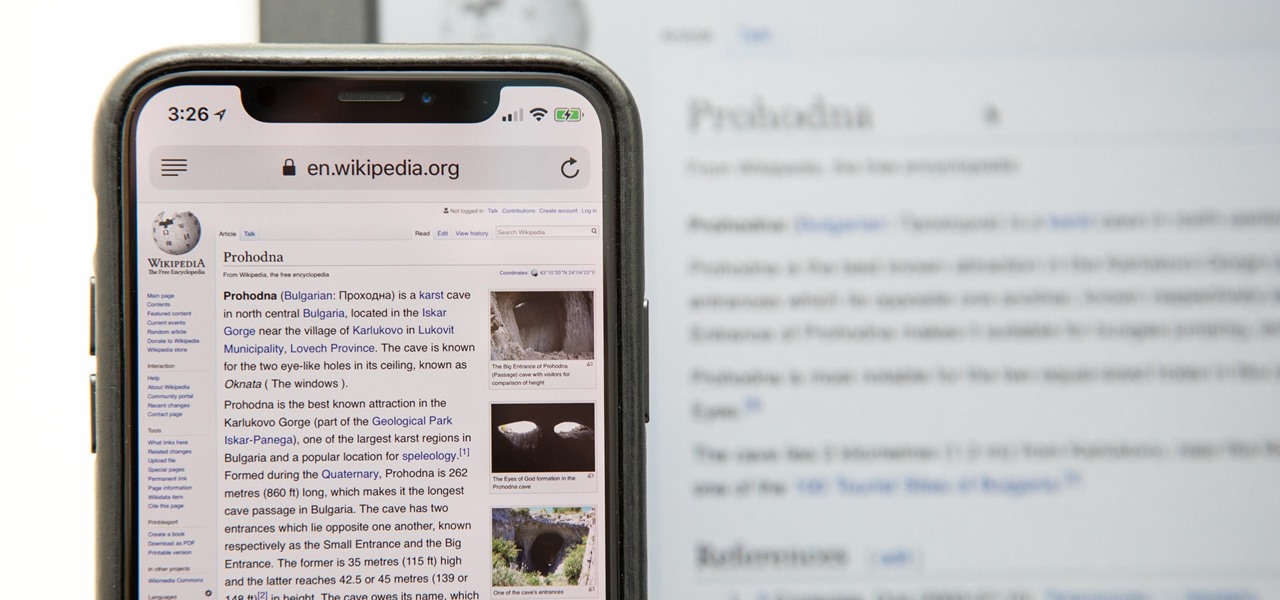
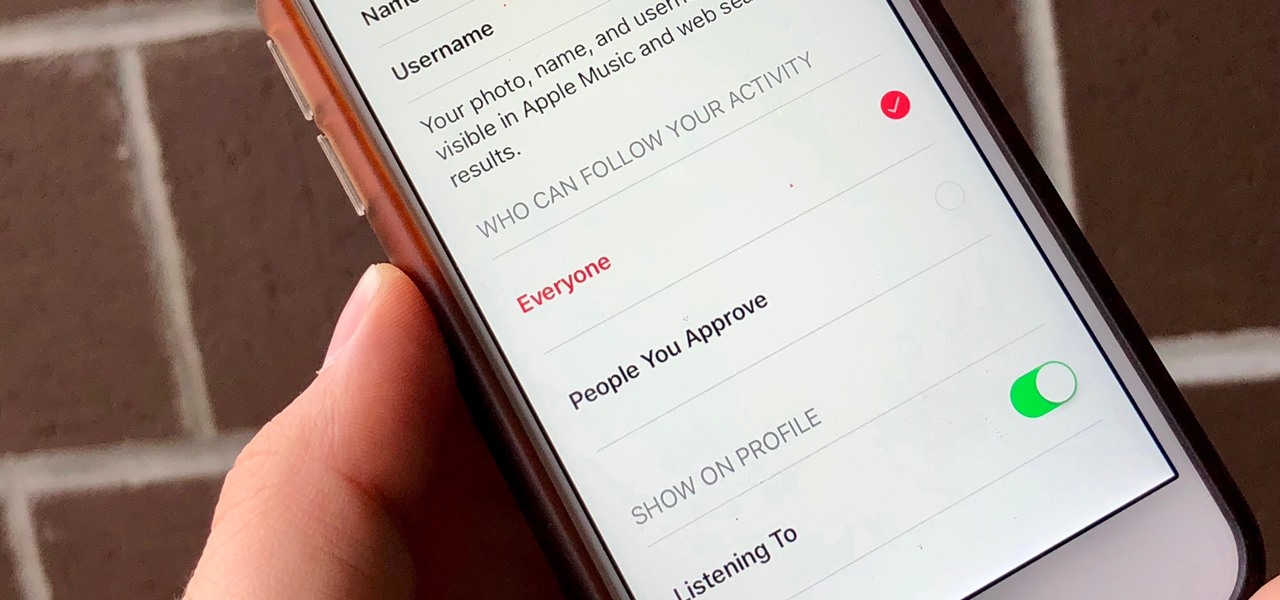
Apple Music, Apple's answer to Spotify, has many interesting features packed in to make that $9.99/month price tag as attractive as possible. One of those features is geared towards social listeners — those who want to follow other Apple Music users and who want to be followed back. But here's the thing: how do you know if your account is public or private?

As promised earlier this year, Neurable has introduced limited beta of a Unity-compatible software developer's kit (SDK) for its brain control interface (BCI) for augmented and virtual reality.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

Most augmented/mixed reality hardware still exists in the development stage, whether that's one of the more robust headsets or a high-powered smartphone. Most everything else isn't widely used or monetized. Snapchat, however, snuck in under the radar and created the foundation for the first social network to focus on augmented reality.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.