These days, using Reddit on your iPhone is just as good, if not better, than Redditing on a desktop browser. While there's an official Reddit app for iOS, there are plenty of third-party clients that have similar features as well as custom perks to enhance the experience. But figuring out which Reddit client is best for your daily use can be a lot of work — work that we can make easier on you.

There are more than a few subscription-based movie streaming apps available for Android and iPhone, each with different benefits and varying pricing plans. Needless to say, it can get expensive fast if you sign up for multiple services because you can't decide on what's best. Hopefully, we can help you out with choosing the right video-on-demand app to spend your hard-earned dollars on.

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Being able to sleep deeply and fully is one of the foundations for real health. When you go without it, you feel subhuman and incapable of dealing with the world—just ask a student who's had to pull an all-nighter or the parents of a newborn. In fact, many studies have shown that lack of sleep or irregular sleep is linked to acne, weight gain, and depression.

Hello there, people. Today, I am going to show you how to extract the essence from a useful plant, using either alcohol or olive oil. This is how you take a plant and turn it into a useful (and preservable) medicine. For those of you who know nothing about herbal medicine, let me explain it for you in a nutshell...

So, the in-person conversations between you and your friends has slowed down to a near halt, thanks to everyone's obsession with texting, Facebook, and over-uploading pics to Instagram—socializing at its best. It could also be that you're just not interesting enough anymore in person.

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

From poison oak to allergies, irritants can cause an irritated area that can itch for hours. Itching is annoying and distracting, but you don't have to go to the store to find relief. You can make a topical cream to alleviate itching with things you have at home.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

If you're an AirPods user, things are a lot better with iOS 18 and iPadOS 18. If you're not, it may finally be time to grab yourself a set of AirPods, especially if you're into privacy and gaming.

Emoji have taken over the world, so there's a good chance you regularly use (or overuse) emoji on your iPhone's keyboard just like everyone else. But before emoji were popular, there were emoticons, short for "emotion icons" — and iOS has a secret emoticon keyboard just waiting for you to unlock.

Is the emoji you're using really the one you think it is? While you can use any emoji that looks like it fits what you have to say, it may have been created for a different purpose. On an iPhone, it's easy to find that purpose by retrieving the actual name of the emoji in Apple's operating system.

Google has a few hidden tools you might not have discovered yet, and they work in Google Search, in the Google app, and with Google Assistant — on both iPhone and Android phones.

The latest iPhone update introduces big features like Live Activities and Clean Energy Charging, but those aren't the only things you'll notice different on iOS 16.1. If you build your own shortcuts in the Shortcuts app, there are a few things you'll definitely want to know about the new software. It's not a massive feature drop as with iOS 16.0, but they are important changes.

When you see foreign words on a sign, unfamiliar currencies on a dinner menu, or a recipe using a different measurement system, there's a good chance you google it for a translation or conversion. Your iPhone's Translate app comes in handy for real-world language translations, and Siri's pretty good at converting measurements, but there's an app on everyone's lock screen that can do both: Camera.

If you can't curb your TikTok obsession, at least make it more efficient by taking your hands out of the equation. So when you're eating breakfast, working on your computer, or using your hands for another non-TikTok task, you don't even have to touch your iPhone or iPad to scroll through all of those videos in your feed. Instead, you can just tell it what to do, and it'll listen.

Your Pixel's Now Playing song discovery tool received a few updates in Android 12, and the feature is finally comparable to other music recognition services.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!

The Nintendo Switch and Switch Lite are console gaming on the go — with zero regards for modern audio features. Headphone jack? Check. Bluetooth connectivity? Not so much. While Nintendo seems to think we're all happy to live like it's 2015, there's a way to use your AirPods with your Switch or Switch Lite for wireless and convenient entertainment.

I won't mince words: the Notes widget in iOS 14 is bad. But you're not stuck with it if you want sticky notes on your home screen.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

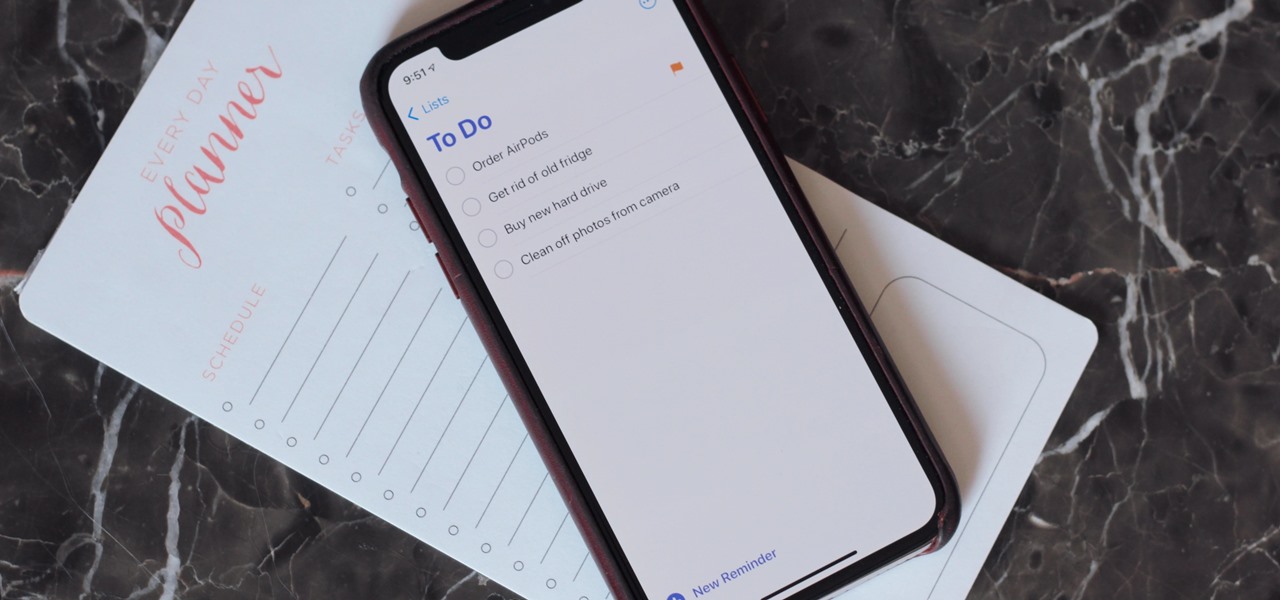
The iPhone's built-in Reminders app got an overhaul last year with iOS 13, giving us a more modern design and plenty of new features, and iOS 14 doesn't mess with a good thing. Instead, iOS 14 brings lots of small tweaks all over the app to smooth out the experience and make Reminders more powerful and more customizable than ever.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

Whether you're using your iPhone to add graphics to a document, edit a photo, or sketch an idea, color plays a vital role in making your work look great. Apple's iOS 14 update introduces a system-wide color picker that lets you pick the exact color you want, save it to your favorite colors, and use it across a variety of apps to add that special touch to your work.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus and firewall software is installed.

TWRP has been the king of custom recovery on Android for years now, thanks to device compatibility and core features. But there's a new player in town — at least, for OnePlus devices — and it's got a lot of useful features that might finally get you to ditch TWRP.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.