Multi-touch input has been spreading throughout a huge variety of devices, from phones to all-in-one PCs. However, most multitouch (table) displays that can function with your computer tend to be fairly expensive, so with this project we're going to make our own display, that can run on any operating system, and reuses some useless everyday materials.

This instructional video teaches how to draw a variety of basic cartoon faces. Learn how to make simple changes to sketch different comic characters.

Make a classic Margarita with Trago top shelf tequila! Explore the silver, reposado and the anejo varieties of tequila. This margarita is shaken, not stirred or frozen.

Andrew Price of Dyad Bushcraft demonstates a variety of signals that can be used in a surivival situation. Techniques include signals using whistles, mirrors, and flares.

If the only cheeses you've known are American, Swiss, and pepperjack, then you've really been living under a rock when it comes to the wonderful world of cheeses.

Usually when you think of jellies or jams you think of the sweet variety, usually prepared with strawberries or grapes. But jellies come in a more savory variety too, and make excellent bread spreads.

There are thousands of different types of sooji, also known as semolina, to work with when cooking, but who has enough pantry space to keep all these varieties in stock at once? The trick to always having the sooji you need is to purchase a coarse variety and then grind it down to the consistency you want for the recipe.

In this tutorial, we learn how to draw a variety of prom dresses. First, you will need to start out by drawing the dresses on different body shapes. Make dresses that are long, short, and knee-length. After this, use a marker to draw the outline of the body and the dress, then start to add in the pleats and the dress details. Add on scarves and other items to the different types of dresses, then continue doing this for the different types of dresses and body shapes. When you are done, draw in...

If you have a shady yard, you can still have a colorful garden. You just need to pick the right plants that do well in the shade. Caladium is a leafy plant with bright colored red, pink and green leaves. They do not tolerate cold weather and should be brought in over winter. Impatiens are popular annual flowers that grow in the shade. They look nice planted around the base of a tree or in containers. The flowers come in shades of pink, coral, white and red. Fuchsia is a beautiful flowering pl...

Chef Billy Parisi from Fix My Recipe responds to a request sent by one of his viewers, to "fix" a barbecue chicken skewers meal.

Randy, from The Simple Chef, demonstrates the simple method of how to cook buttercup squash. Randy is looking for something particularly simple to make, as he has promised dinner to a special girl, however it is obvious that he has recently been injured in an accident. He begins by quartering the squash, and hollowing it. He suggests scoring the remaining inside to allow the ingredients to get deeper into the squash. This technique of cooking squash can be used for any of the hard shelled win...

David Epstein shows a simple and yet creative way to add contrast to any garden with bare or no interest areas. To add a little extra winter color, David introduces three varieties of the "Small leaf Rhododendron" including; "Midnight Ruby", "Westons Mayflower" and "Dora Ainateis". Although these smaller leafed varieties require a little more sunlight, they do however produce flowers in Spring and hold their leaves all winter long. So, for a continuation of color throughout winter, be sure to...

When you head to your neighborhood gardening center to find a shade tree for your garden, the variety of choices can be pretty overwhelming. There are so many kinds of trees, and each of those trees has its own varieties. In this clip, Dave Epstein from Growing Wisdom will help find the best shade tree for you.

Lentils are sold in many varieties and colors: split, whole, brown, green, black, red, white, French. For the most tender, toothsome lentil, one that won’t fall apart in soup, stick with the brown, green, or French (also called “puy”) variety. Watch this howcast video to learn how to make a delicious lentil soup.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Want to share Internet connectivity between two computers without a wireless network but have an extra CAT5 ethernet cable? You're in luck. This home networking how-to will show you what to do to get your machines talking not only to one another but the web at large.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

In order to make two different varieties of cold smoke sausage, you will need the following: pork butts, a grinder, a mixer, a scale, scissors, hog ring, cooking string, non-iodized salt, rubbed sage, crushed red pepper, course black pepper, and casings.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

HipHop for PHP is a source code transformer that allows you to optimize your PHP code easily, which will allow you website to run faster on less server space. This video is a record of a seminar on using HipHop done by a Facebook employee who had a hand in it's development. If you make websites using PHP, this will be very good stuff for you to learn.

Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play the basics in Evony online. See exactly what the game Evony is!

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

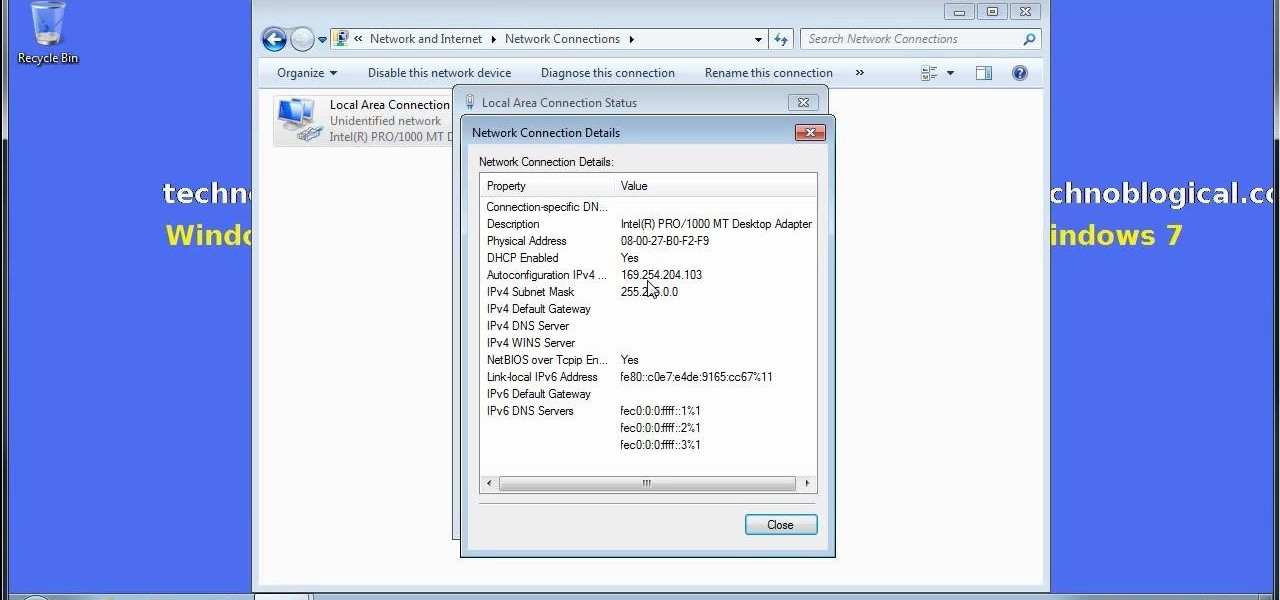
In this clip, you'll learn how to speed up the Internet connection on a PC running the Microsoft Windows 7 operating system by using custom external DNS servers. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

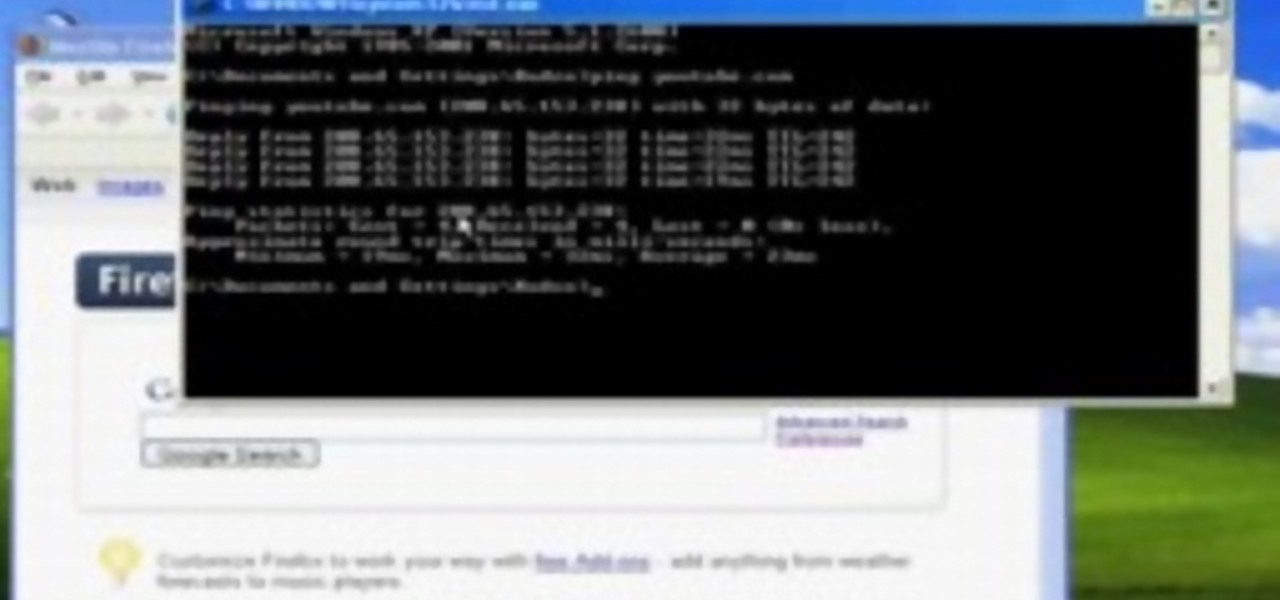
Get past your school's web filter without having to use a proxy server. Through the Start Menu, run the 'cmd' program. Then type in 'ping' plus the name of the site you want to visit. This will give you the IP address, which you can then use to get directly to the site you want to visit.

This video shows you how to install language packs on Windows 7. It can be a bit tricky to figure out where to download these language packs, but this video does a great job explaining where to go. The invitation key needed to access the downloads section on Microsoft's site is Win7-3HQW-RF74. This also allows you to download Windows Server R2 2008 and Windows 7 Home Premium

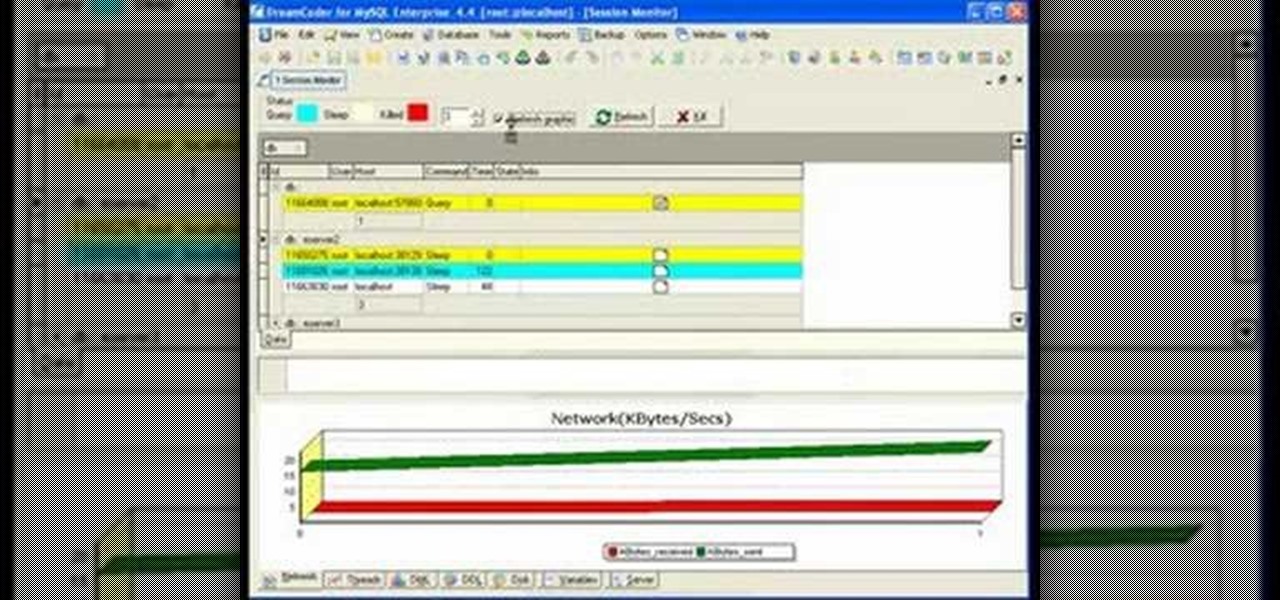
If you're new to DreamCoder for MySQL, one of the first things you may want to know how to do is to monitor a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to monitor a given MySQL database remotely via DreamCoder for MySQL, take a look!

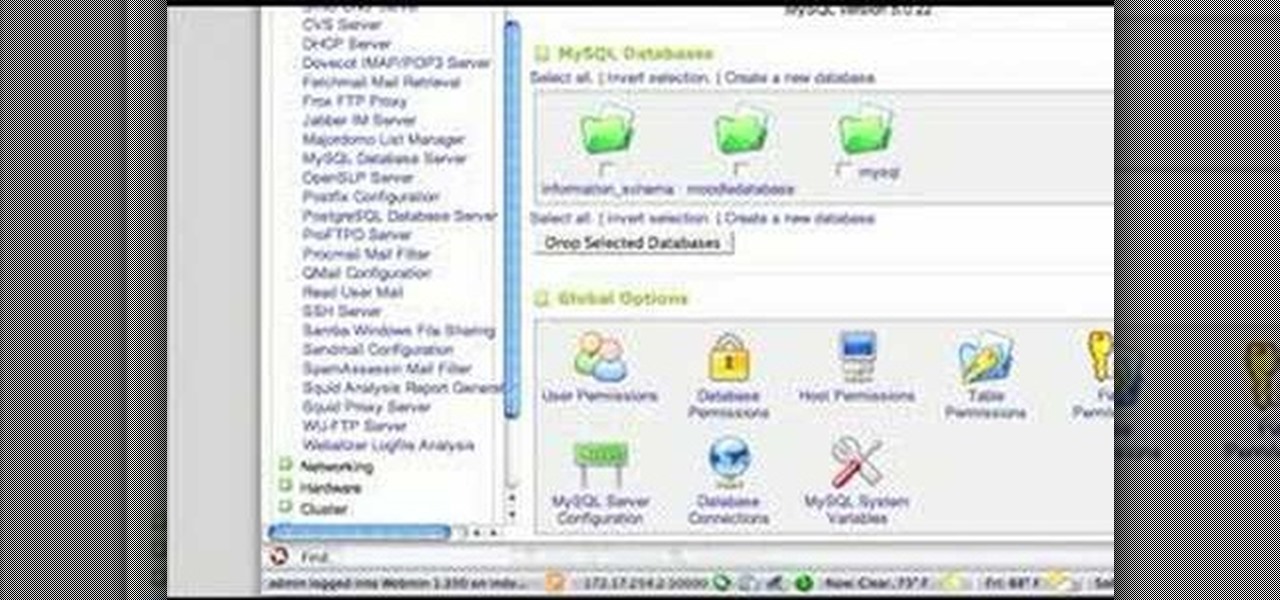
Interested in teaching an online course using your own server but can't quite figure out how to install everything you'll need? This video demonstrates how to setup a MySQL database for use with Moodle, the free, open source course management utility, which requires a MySQL database to run. For step-by-step instructions, take a look.

USB flash drives are great for moving files on and off of a linux server, but how do you do it? This quick tutorial shows you how easy it is!

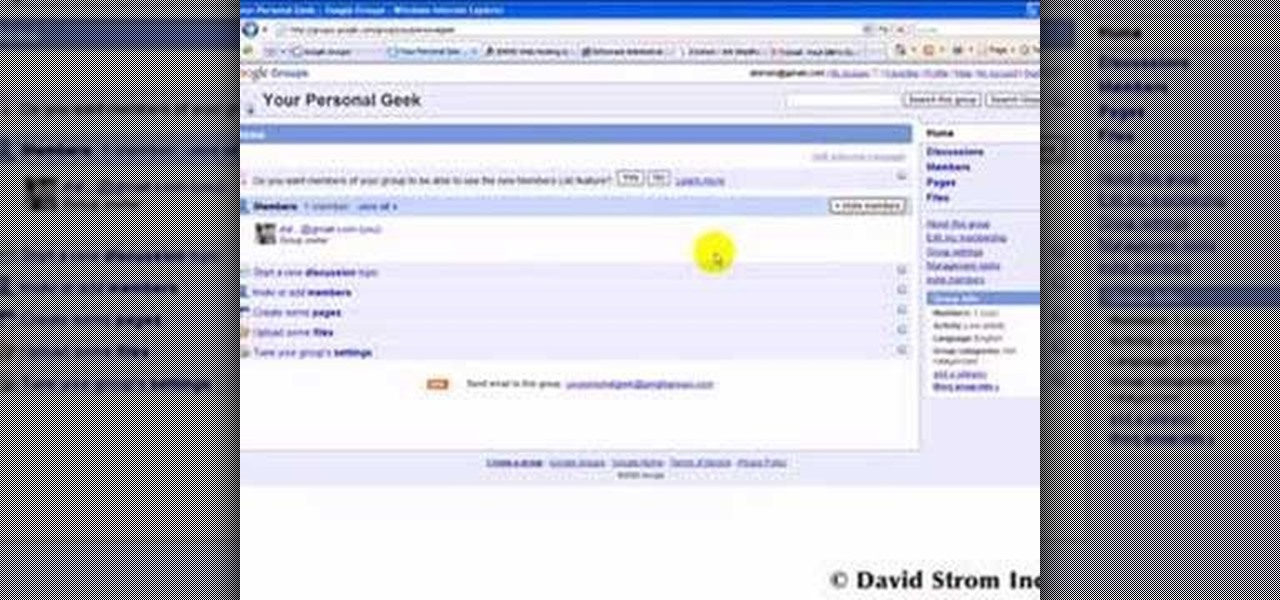
David Strom shows you how to pick from aong Google Groups, Mailman hosted by EMWD.com, and iContact and how to get started with your own mailing list

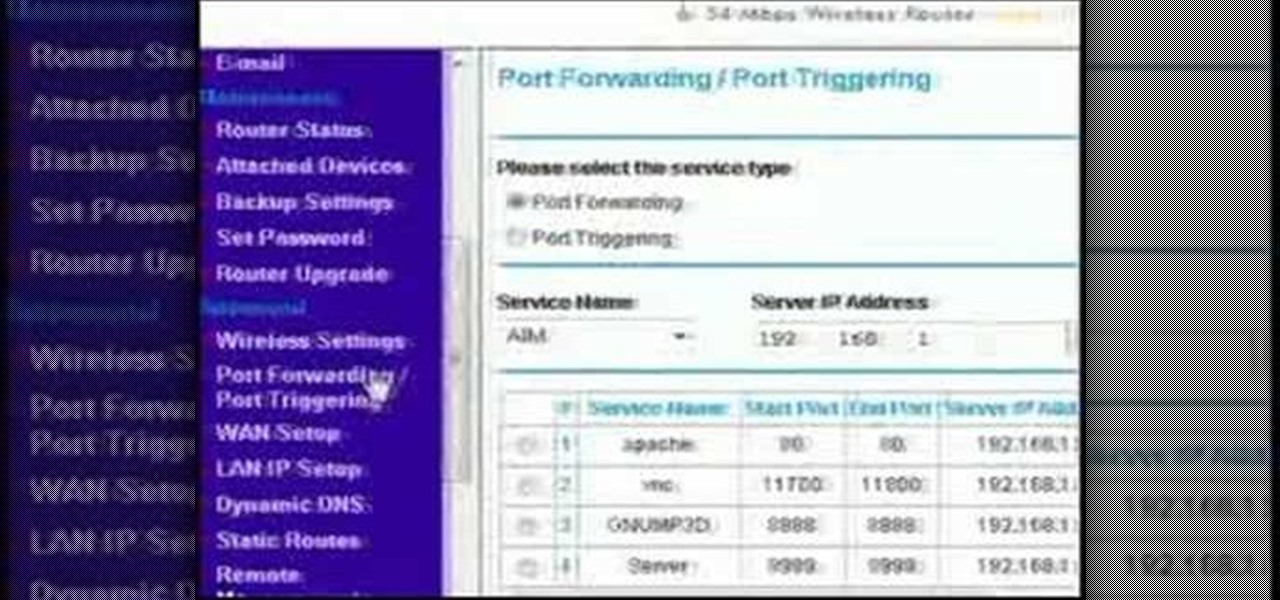
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.